Powerpoint Templates and Google slides for Secure Data Implementing
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
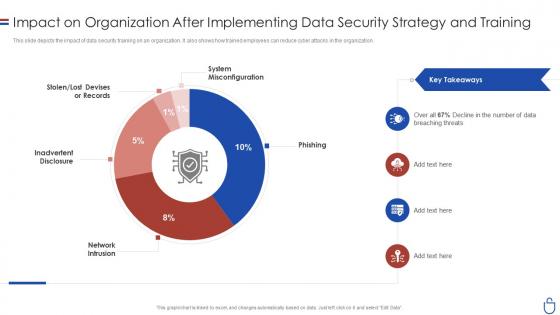 Data security it impact on organization after implementing data security strategy
Data security it impact on organization after implementing data security strategyThis slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver an outstanding presentation on the topic using this Data Security IT Impact On Organization After Implementing Data Security Strategy. Dispense information and present a thorough explanation of Phishing, Network Intrusion, Inadvertent Disclosure, System Misconfiguration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Contracts Implementation Plan Statistical Data Of Security Breach Incident
Smart Contracts Implementation Plan Statistical Data Of Security Breach IncidentThis slide summarizes the security breach incident across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. Present the topic in a bit more detail with this Smart Contracts Implementation Plan Statistical Data Of Security Breach Incident. Use it as a tool for discussion and navigation on Statistical Data, Security Breach Incident, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
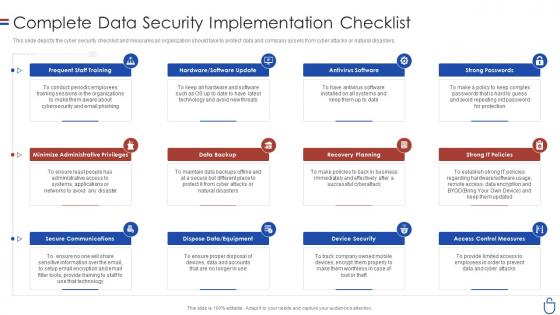 Data security it complete data security implementation checklist
Data security it complete data security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Data Security IT Complete Data Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Antivirus Software, Strong Passwords, Minimize Administrative Privileges, Data Backup, Recovery Planning, Strong IT Policies, Secure Communications, Device Security, using this template. Grab it now to reap its full benefits.
-
 Data security it implementation of strong password policy
Data security it implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Data Security IT Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Special Characters, Employees, Protected Accounts, using this template. Grab it now to reap its full benefits.
-
 Data security it timeline for the implementation of data security
Data security it timeline for the implementation of data securityThis slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Data Security IT Timeline For The Implementation Of Data Security. Use it as a tool for discussion and navigation on Phishing Exercise, Risk Assessments, Security Documentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
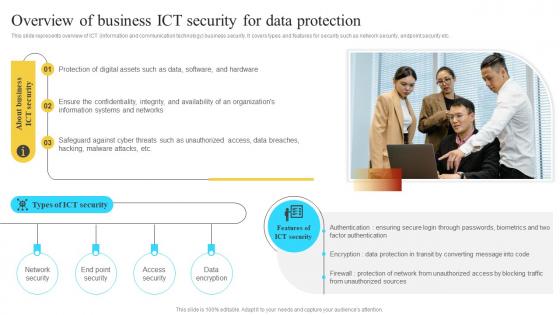 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
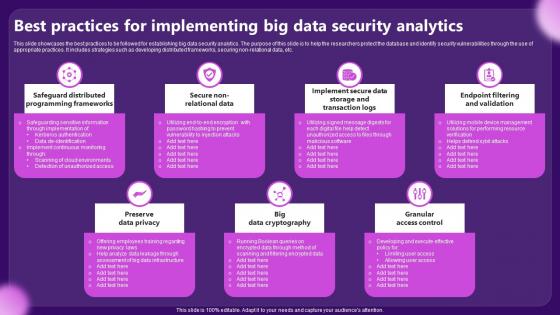 Best Practices For Implementing Big Data Security Analytics
Best Practices For Implementing Big Data Security AnalyticsThis slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non relational data, etc. Presenting our set of slides with Best Practices For Implementing Big Data Security Analytics. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preserve Data Privacy, Granular Access Control.
-
 Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption
Impact Of Encryption Implementation On Cloud Security Cloud Data EncryptionThis slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Cloud Data Security Implementation Cloud Data Encryption
Timeline For Cloud Data Security Implementation Cloud Data EncryptionThis slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Introducing Timeline For Cloud Data Security Implementation Cloud Data Encryption to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Test Encryption Solutions, Implement Encryptions Solution, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Data Security Concerns Faced By Company
Encryption Implementation Strategies Data Security Concerns Faced By CompanyThis slide discusses the security issues faced by the organization due to a lack of encryption and data protection technologies. These concerns are unauthorized access, data breaches, insider threats, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Security Concerns Faced By Company. Dispense information and present a thorough explanation of Data Security Concerns, Phishing Attacks, Data Protection Technologies, Compliance And Regulations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest
Encryption Implementation Strategies Encryption Technologies To Secure Data At RestThis slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Full Disk Encryption, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use
Encryption Implementation Strategies Overview Of Encryption For Securing Data In UseThe purpose of this slide is to outline the different possible ways of protecting data in use. The methods include IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use. Dispense information and present a thorough explanation of Information Rights Management, Encryption For Securing Data, Role Based Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies
Encryption Technologies To Secure Data In Transit Encryption Implementation StrategiesThis slide compares different data in transit protection methods, including their working and associated cost. These methods are email encryption, Managed File Transfer MFT, Data Leak Prevention DLP, Cloud Access Security Brokers CASB, etc. Deliver an outstanding presentation on the topic using this Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Managed File Transfer, Cloud Access Security Brokers, Email Encryption, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies
Overview Of Encryption For Securing Data At Rest Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data at rest. The storage methods include file servers, network shares, document management systems, external storage, databases, endpoint devices, mobile devices, cloud storage, etc. Present the topic in a bit more detail with this Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies. Use it as a tool for discussion and navigation on Database Encryption, Information Rights Management, Data Leak Prevention, Mobile Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies
Overview Of Encryption For Securing Data In Transit Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data in transit. The methods include email encryption, MFT Managed File Transfer, IRM Information Rights Management, CASB Cloud Access Security Brokers, and DLP Data Leak Prevention. Deliver an outstanding presentation on the topic using this Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Data Breach Security Response Plan
Checklist To Implement Data Breach Security Response PlanThis slide depicts the checklist to execute response plans during data security breaches. The purpose of this checklist is to help the business ensure all suitable actions are implemented in order to prevent data leaks. It includes elements such as activity status, person responsible, etc. Presenting our well structured Checklist To Implement Data Breach Security Response Plan. The topics discussed in this slide are Isolate Affected Systems, Notify Appropriate Stakeholders, Identify The Nature. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SS
Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SSThis slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile. Deliver an outstanding presentation on the topic using this Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SS Dispense information and present a thorough explanation of Customer Trust, Sensitive Information, Balancing Personalization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process
Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management ProcessThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Increase audience engagement and knowledge by dispensing information using Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process. This template helps you present information on five stages. You can also present information on Malware Infection, Systems With Passwords, Employees Feels, Allow Official Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Response Plan Implementation Secure Operations
Data Breach Response Plan Implementation Secure OperationsThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Implementation Secure Operations. Use it as a tool for discussion and navigation on Secure Physical Areas, Assemble Expert Team, Consult With Legal Counsel, Secure Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats
Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates various methods to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Deliver an outstanding presentation on the topic using this Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Network Attached Storage, Cloud Storage Services, Flat Backup System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats
Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Increase audience engagement and knowledge by dispensing information using Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Time Consuming Process, Speedy Process, Incremental Backup using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness Among
Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness AmongThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Introducing Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness Among to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Email Attachments, Systems, Employees using this template. Grab it now to reap its full benefits.
-
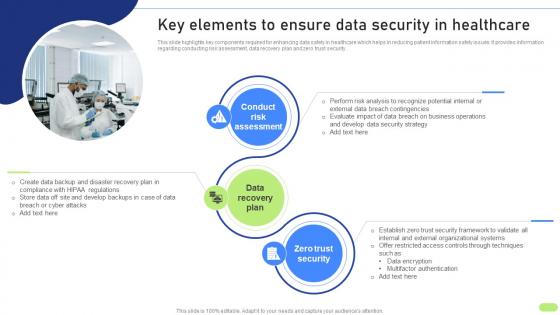 Key Elements To Ensure Data Security Definitive Guide To Implement Data Analytics SS
Key Elements To Ensure Data Security Definitive Guide To Implement Data Analytics SSThis slide highlights key components required for enhancing data safety in healthcare which helps in reducing patient information safety issues. It provides information regarding conducting risk assessment, data recovery plan and zero trust security. Introducing Key Elements To Ensure Data Security Definitive Guide To Implement Data Analytics SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Risk Assessment, Data Recovery Plan, Zero Trust Security, using this template. Grab it now to reap its full benefits.
-
 Implement Robust Security Measures Icon For Big Data Platforms
Implement Robust Security Measures Icon For Big Data PlatformsIntroducing our Implement Robust Security Measures Icon For Big Data Platforms set of slides. The topics discussed in these slides are Implement Robust Security Measures, Icon For Big Data Platforms. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Tokenization Working Process For Data Security Implementing Effective Tokenization
Tokenization Working Process For Data Security Implementing Effective TokenizationThis slide represents the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Deliver an outstanding presentation on the topic using this Tokenization Working Process For Data Security Implementing Effective Tokenization. Dispense information and present a thorough explanation of Tokenization Working Process, Data Security, Mobile Payment Application, Generating Tokens using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization
Tokenization For Improved Data Security 30 60 90 Days Plan To Implement TokenizationThis slide depicts the 30 60 90 days plan for implementing tokenization. The plan includes the activities and goals such as assessment, planning, selecting tokenization solutions, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization. Dispense information and present a thorough explanation of Assessment And Planning, Select Tokenization Solution, Test Tokenization Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security
Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data SecurityThis slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security. Dispense information and present a thorough explanation of Compliance With Regulations, Reduced Insider Threats, Exposure Of Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business
Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In BusinessThis slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business. Use it as a tool for discussion and navigation on Tokenization Solution, Integration And Customization, Infrastructure And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In Ds
Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In DsThis slide highlights the disadvantages of carrying out tokenization. The purpose of this slide is to showcase the drawbacks and its implications which include increased IT complexity, limited adoption, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In Ds. Use it as a tool for discussion and navigation on Critical Challenges, Tokenization Implementation, Alters Transaction Process, Compatibility Concerns. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds
Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In DsThis slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds. This template helps you present information on six stages. You can also present information on Mathematically Reversible, Cryptographic Function, Producing Tokens using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data Security
Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data SecurityThis slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Roadmap To Implement Tokenization For Data Security. This template helps you present information on five stages. You can also present information on Identify Sensitive Data, Implement Access Controls, Configure The Tokenization System, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data Security
Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data SecurityThis slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Timeline To Implementation Tokenization In Data Security. This template helps you present information on six stages. You can also present information on Tokenization Key Management, Monitoring And Auditing, Tokenization Methods, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Implement Ethics In Data Cyber Security
Best Practices To Implement Ethics In Data Cyber SecurityThis slide represents various best practices that assist companies to implement ethics to enhance their data cybersecurity. It include various best practices such as ethical code of conduct, ethical hacking and testing, third-party ethics. Introducing our Best Practices To Implement Ethics In Data Cyber Security set of slides. The topics discussed in these slides are Best Practices, Details, Impact. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS
Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing secure multi party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Increase audience engagement and knowledge by dispensing information using Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Increase Security Against Attacks, Boost Data Confidentiality, Input Sharing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Implement Encryption Trends In Data Security
Strategies To Implement Encryption Trends In Data SecurityThe purpose of this slide is to guide and inform on effective strategies for implementing encryption trends in data security. It provides actionable insights to enhance data protection and address evolving cyber threats. Introducing our Strategies To Implement Encryption Trends In Data Security set of slides. The topics discussed in these slides are Biometric Authentication, Multi-Factor Authentication, Cloud Encryption, Blockchain Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides Image
Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides ImageThis slide illustrates the issues that trigger poor relationship with customers which includes no real time support, no innovative product launched, bad after sale service and lack of engagement. Present the topic in a bit more detail with this Sales CRM Cloud Implementation Poor Relationship With Customers Ppt Slides Picture. Use it as a tool for discussion and navigation on Weak Relationship Building, Poor Customer Service, Product Launched. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Our Data With Crm Crm Software Implementation Ppt Slides Demonstration
Securing Our Data With Crm Crm Software Implementation Ppt Slides DemonstrationThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an outstanding presentation on the topic using this Securing Our Data With Crm Crm Software Implementation Ppt Slides Demonstration. Dispense information and present a thorough explanation of Data Storage And Failover, Communication Protection, Data Backup using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security
Consequences Of Data Breaches Faced By Organization Development And Implementation Of SecurityThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security. Dispense information and present a thorough explanation of Payment Card Fraud, Physical Loss, Insider Leak using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace enabling data security risk management action plan
Implementing advanced analytics system at workplace enabling data security risk management action planThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Enabling Data Security Risk Management Action Plan. Dispense information and present a thorough explanation of Management, Resources, Enabling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 6 step process to implement data availability security
6 step process to implement data availability securityThis slide represents 6 step process to implement data availability security illustrating simplified recording, on-site maintenance and online security, training, record disposal and plan. Presenting our set of slides with 6 Step Process To Implement Data Availability Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Implement, Organization.
-
 Planning And Implementation Of Crm Software Securing Our Data With Crm
Planning And Implementation Of Crm Software Securing Our Data With CrmThis slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. Deliver an outstanding presentation on the topic using this Planning And Implementation Of Crm Software Securing Our Data With Crm. Dispense information and present a thorough explanation of User Role Based Security, Profile Based Security, Record Sharing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Our Data With Crm Planning And Implementation Of Crm Software
Securing Our Data With Crm Planning And Implementation Of Crm SoftwareThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Present the topic in a bit more detail with this Securing Our Data With Crm Planning And Implementation Of Crm Software. Use it as a tool for discussion and navigation on Securing Our Data With CRM. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Steps Enable Data Security Crm Software Deployment Guide
Implementation Steps Enable Data Security Crm Software Deployment GuideThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm Software Deployment Guide. Use it as a tool for discussion and navigation on Implementation, Authentication, Restrictions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Steps Enable Data Security Crm Platform Implementation Plan
Implementation Steps Enable Data Security Crm Platform Implementation PlanThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an outstanding presentation on the topic using this Implementation Steps Enable Data Security Crm Platform Implementation Plan. Dispense information and present a thorough explanation of Authentication, Implementation, Security Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Customer Relationship Management System Implementation Steps Enable Data Security
Customer Relationship Management System Implementation Steps Enable Data SecurityThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an outstanding presentation on the topic using this Customer Relationship Management System Implementation Steps Enable Data Security. Dispense information and present a thorough explanation of Implementation, Authentication, Restrictions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Crm Implementation Process Implementation Steps Enable Data Security
Crm Implementation Process Implementation Steps Enable Data SecurityThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Crm Implementation Process Implementation Steps Enable Data Security. Use it as a tool for discussion and navigation on Implementation, Authentication, Restrictions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Implement Cloud Security In Business Cloud Data Protection
Checklist To Implement Cloud Security In Business Cloud Data ProtectionThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Checklist To Implement Cloud Security In Business Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Logging And Monitoring, Networking, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Roadmap Of Cloud Security Implementation Cloud Data Protection
Roadmap Of Cloud Security Implementation Cloud Data ProtectionThis slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Introducing Roadmap Of Cloud Security Implementation Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services Monitoring, Services Management, Database Security Measures, Network Security, using this template. Grab it now to reap its full benefits.
-
 Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses
Implementation Steps Enable Data Security Crm System Implementation Guide For BusinessesThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses. Use it as a tool for discussion and navigation on Implementation, Compliance, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 In House Training Schedule We Will Implement Preventing Data Breaches Through Cyber Security
In House Training Schedule We Will Implement Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto jacking and IoT Based attack. Present the topic in a bit more detail with this In House Training Schedule We Will Implement Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Compromise, Training. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security
Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Increase audience engagement and knowledge by dispensing information using Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Gamification, Personalization, High Quality Content using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS
Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SSThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc.Present the topic in a bit more detail with this Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Factor Authentication, Organizations Information, Ensure Confidentiality. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda implementing security management plan reduce threats protect sensitive company data
Agenda implementing security management plan reduce threats protect sensitive company dataIncrease audience engagement and knowledge by dispensing information using Agenda Implementing Security Management Plan Reduce Threats Protect Sensitive Company Data. This template helps you present information on six stages. You can also present information on Management, Security, Plan, Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing security management plan reduce threats protect sensitive company data icons slide
Implementing security management plan reduce threats protect sensitive company data icons slidePresenting our well crafted Implementing Security Management Plan Reduce Threats Protect Sensitive Company Data Icons Slide set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.




