Powerpoint Templates and Google slides for Secure Cryptography
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cryptography In Cyber Security Powerpoint Ppt Template Bundles
Cryptography In Cyber Security Powerpoint Ppt Template BundlesEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cryptography In Cyber Security Powerpoint Ppt Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Cryptographic Cloud Security Solution Providers Cloud Cryptography
Cryptographic Cloud Security Solution Providers Cloud CryptographyThis slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Present the topic in a bit more detail with this Cryptographic Cloud Security Solution Providers Cloud Cryptography. Use it as a tool for discussion and navigation on Cryptographic, Solution Providers, Management Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Enhancement Using Hashing Cloud Cryptography
Cloud Security Enhancement Using Hashing Cloud CryptographyThis slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Increase audience engagement and knowledge by dispensing information using Cloud Security Enhancement Using Hashing Cloud Cryptography. This template helps you present information on four stages. You can also present information on Data Integrity, Digital Signatures, Password Storage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cryptographic Algorithms Used In Data Security Cloud Cryptography
Cryptographic Algorithms Used In Data Security Cloud CryptographyThis slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Deliver an outstanding presentation on the topic using this Cryptographic Algorithms Used In Data Security Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Algorithms, Data Encryption Standard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security In Cloud Computing Architecture Cloud Cryptography
Data Security In Cloud Computing Architecture Cloud CryptographyThis slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Present the topic in a bit more detail with this Data Security In Cloud Computing Architecture Cloud Cryptography. Use it as a tool for discussion and navigation on Architecture, Cryptographic, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Types Of Cryptographic Security Techniques Cloud Cryptography
Different Types Of Cryptographic Security Techniques Cloud CryptographyThis slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc. Deliver an outstanding presentation on the topic using this Different Types Of Cryptographic Security Techniques Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Techniques, Quantum Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Emerging Trends In Cryptographic Cloud Security Cloud Cryptography
Emerging Trends In Cryptographic Cloud Security Cloud CryptographyThis slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Deliver an outstanding presentation on the topic using this Emerging Trends In Cryptographic Cloud Security Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Homomorphic Encryption, Quantum Safe Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Factors Responsible For Cloud Security Failures Cloud Cryptography
Factors Responsible For Cloud Security Failures Cloud CryptographyThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Present the topic in a bit more detail with this Factors Responsible For Cloud Security Failures Cloud Cryptography. Use it as a tool for discussion and navigation on Information, Businesses, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Uses And Applications Of Cryptographic Security Cloud Cryptography
Key Uses And Applications Of Cryptographic Security Cloud CryptographyThis slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Increase audience engagement and knowledge by dispensing information using Key Uses And Applications Of Cryptographic Security Cloud Cryptography. This template helps you present information on nine stages. You can also present information on Computer Security, Digital Currencies, Web Surfing Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud Cryptography
Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud CryptographyThis slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Introducing Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud Cryptography to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Digital Signatures, using this template. Grab it now to reap its full benefits.
-
 Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud Cryptography
Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud CryptographyThis slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Increase audience engagement and knowledge by dispensing information using Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud Cryptography. This template helps you present information on four stages. You can also present information on Encryption, Access Control, Key Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Cryptographic Cloud Security Cloud Cryptography
Steps To Implement Cryptographic Cloud Security Cloud CryptographyThe purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Increase audience engagement and knowledge by dispensing information using Steps To Implement Cryptographic Cloud Security Cloud Cryptography. This template helps you present information on eight stages. You can also present information on Cryptographic, Appropriate, Implement Access Controls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Training Program For Cryptographic Cloud Security Cloud Cryptography
Training Program For Cryptographic Cloud Security Cloud CryptographyThis slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Deliver an outstanding presentation on the topic using this Training Program For Cryptographic Cloud Security Cloud Cryptography. Dispense information and present a thorough explanation of Cryptography Fundamentals, Introduction To Cryptography, Cloud Computing And Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Leverage Cryptography To Boost Privacy And Confidentiality Hands On Blockchain Security Risk BCT SS V
Leverage Cryptography To Boost Privacy And Confidentiality Hands On Blockchain Security Risk BCT SS VThe following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Introducing Leverage Cryptography To Boost Privacy And Confidentiality Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Confidentiality, Data Integrity, Digital Signatures, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets About Cryptography Overview And Key Features
Secure Your Digital Assets About Cryptography Overview And Key FeaturesThis slide discusses cryptography and its key features. The purpose of this slide is to highlight the overview of cryptography as it is the technology for protecting data and some features such as confidentiality, integrity, non- repudiation, etc. Introducing Secure Your Digital Assets About Cryptography Overview And Key Features to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Non Repudiation, Authentication, Encrypt Data And Communications, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Understanding Applications And Use Cases Of Cryptography
Secure Your Digital Assets Understanding Applications And Use Cases Of CryptographyThis slide represents the application of cryptography in the market. The purpose of this slide is to outline the implements such as computer passwords, digital currencies, secure web browsing, electronic signatures, authentications, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Understanding Applications And Use Cases Of Cryptography. This template helps you present information on six stages. You can also present information on Computer Passwords, Digital Currencies, Secure Web Browsing, Electronic Signatures, Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
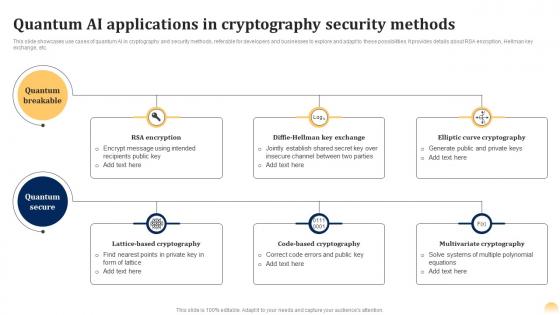 Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SS
Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SSThis slide showcases use cases of quantum AI in cryptography and security methods, referable for developers and businesses to explore and adapt to these possibilities. It provides details about RSA encryption, Hellman key exchange, etc. Present the topic in a bit more detail with this Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SS. Use it as a tool for discussion and navigation on Elliptic Curve Cryptography, Code Based Cryptography, Multivariate Cryptography. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Crypto Wallets Types And Applications Key Security Benefits Of Cryptography
Crypto Wallets Types And Applications Key Security Benefits Of CryptographyThis slide aims to highlight the advantages of cryptography in the market. This slide represents some benefits of crypto, such as access control, secure communication, protection against attacks, compliance with legal requirements, etc. Introducing Crypto Wallets Types And Applications Key Security Benefits Of Cryptography to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Protection Against Attacks, Compliance With Legal Requirements, Secure Communication, using this template. Grab it now to reap its full benefits.
-
 Leverage Cryptography Boost Securing Blockchain Transactions A Beginners Guide BCT SS V
Leverage Cryptography Boost Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Increase audience engagement and knowledge by dispensing information using Leverage Cryptography Boost Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on four stages. You can also present information on Data Confidentiality, Digital Signatures, Consensus Mechanisms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Advantages Of Quantum Cryptography To Secure Data Encryption For Data Privacy In Digital Age It
Advantages Of Quantum Cryptography To Secure Data Encryption For Data Privacy In Digital Age ItThis slide demonstrates the benefits of quantum encryption technique. The advantages discussed in this slide are provides secure communication, detects eavesdropping, several methods for security, provides perfect secrecy and future proof. Present the topic in a bit more detail with this Advantages Of Quantum Cryptography To Secure Data Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Quantum, Cryptography, Data Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It
Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age ItThis slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Introducing Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Quantum Safe Cryptography, Secure Multi Party Computation, using this template. Grab it now to reap its full benefits.
-
 Applications Of Cryptography In Cyber Security
Applications Of Cryptography In Cyber SecurityThis slide covers various of applications and provides details about how the company secures data for users. It includes elements such as computer passwords, digital currencies, etc. Presenting our set of slides with Applications Of Cryptography In Cyber Security. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Computer Passwords, Secure Web Browsing, Authentication.
-
 Checklist For Cryptography In Cyber Security
Checklist For Cryptography In Cyber SecurityThis slide covers a checklist for cryptography and provides details about the work of company to prioritize risk for systems. It includes elements such as patch management, system monitoring, etc. Introducing our Checklist For Cryptography In Cyber Security set of slides. The topics discussed in these slides are System Monitoring, Backup Monitoring, Vulnerability Scans . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cryptography In Cyber Security Tools
Cryptography In Cyber Security ToolsThis slide covers various tools in cybersecurity and provides details about software that determines cryptography in organizations. It includes elements such as docker Introducing our premium set of slides with Cryptography In Cyber Security Tools. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication Token, Authentication Using Key, Java Cryptography Architecture. So download instantly and tailor it with your information.
-
 Major Techniques Of Cryptography In Cyber Security
Major Techniques Of Cryptography In Cyber SecurityThis slide elaborates on various approaches in cyber security and provides details about cryptography techniques to optimize security. It includes elements such as hashing, simple codes, etc. Introducing our premium set of slides with Major Techniques Of Cryptography In Cyber Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Steganography, Simple Codes, Symmetric Encryption. So download instantly and tailor it with your information.
-
 Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS
Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of cryptographic network protocols for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about secure connectivity, updates, etc. Increase audience engagement and knowledge by dispensing information using Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Secure Connectivity, Network Protocols Usage, Continuous Updates, Cryptographic Network Protocols using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS
Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SSThis slide showcases homomorphic cryptography deployment which can help employees increase data privacy and outsourcing security. It provides details about private key, plaintext, decryption, etc. Introducing Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Classified Plaintext, Decrypted Results, Data Owner Organization, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS
Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS. Use it as a tool for discussion and navigation on Potential Impact, Increased Speed, Improved User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Wireless LAN Cryptographic Security Algorithms Wireless LAN Controller
Wireless LAN Cryptographic Security Algorithms Wireless LAN ControllerThe purpose of this slide is to highlight the various wireless LAN cryptographic algorithm such as wired equivalent privacy, temporal key integrity proposal, etc. Increase audience engagement and knowledge by dispensing information using Wireless LAN Cryptographic Security Algorithms Wireless LAN Controller. This template helps you present information on two stages. You can also present information on Equivalent Privacy, Security Methods, Security Algorithms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Different types security services cryptography ppt powerpoint presentation icon maker cpb
Different types security services cryptography ppt powerpoint presentation icon maker cpbPresenting our Different Types Security Services Cryptography Ppt Powerpoint Presentation Icon Maker Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Different Types Security Services Cryptography. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Is Blockchain Technology Secure Cryptographic Ledger
Is Blockchain Technology Secure Cryptographic LedgerThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain.Introducing Is Blockchain Technology Secure Cryptographic Ledger to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Bitcoins Blockchain, Blockchain Technology, Weaknesses In Blockchain, using this template. Grab it now to reap its full benefits.
-
 Cryptography Used Secure Data Ppt PowerPoint Presentation Infographic Cpb
Cryptography Used Secure Data Ppt PowerPoint Presentation Infographic CpbPresenting our Cryptography Used Secure Data Ppt PowerPoint Presentation Infographic Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cryptography Used Secure Data. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Business Governance Model For Cryptographically Secured Services
Business Governance Model For Cryptographically Secured ServicesThis slide signifies the organisation governance model for cryptographically secured services. It includes steps like generic value network, analysis, canvas analysis and plan. Presenting our well structured Business Governance Model For Cryptographically Secured Services. The topics discussed in this slide are Cloud Services, Value Network, Business Model Canvas. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Security Icon For Blockchain Cryptography
Data Security Icon For Blockchain CryptographyPresenting our well structured Data Security Icon For Blockchain Cryptography. The topics discussed in this slide are Data Security Blockchain Cryptography.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Is Blockchain Technology Secure Cryptographic Ledger IT
Is Blockchain Technology Secure Cryptographic Ledger ITThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain.Present the topic in a bit more detail with this Is Blockchain Technology Secure Cryptographic Ledger IT. Use it as a tool for discussion and navigation on Generated Math Algorithms, Weaknesses Blockchain, Networks Nevertheless. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Cryptography Security Encryption Illustration
Cloud Cryptography Security Encryption IllustrationThis colourful PowerPoint Illustration is perfect for illustrating the concept of cloud cryptography. It features a cloud with a lock and key, demonstrating the secure encryption of data stored in the cloud. Its a great way to visually explain the power of cloud cryptography.
-
 Cryptography Techniques For Framing Phone Security Policy
Cryptography Techniques For Framing Phone Security PolicyThis slide shows cryptography techniques for phone oriented business data. The purpose of this slide is to highlight main techniques for building phone security policy. It include techniques such as simple codes, symmetric encryption and hashing, etc. Presenting our set of slides with Cryptography Techniques For Framing Phone Security Policy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Simple Codes, Symmetric Encryption.
-
 Cryptographic security ppt powerpoint presentation portfolio graphic tips cpb
Cryptographic security ppt powerpoint presentation portfolio graphic tips cpbPresenting this set of slides with name Cryptographic Security Ppt Powerpoint Presentation Portfolio Graphic Tips Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cryptographic Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cryptography information security ppt powerpoint presentation portfolio show cpb
Cryptography information security ppt powerpoint presentation portfolio show cpbWith Stage - Presenting our Cryptography Information Security Ppt Powerpoint Presentation Portfolio Show Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cryptography Information Security This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.



