Powerpoint Templates and Google slides for Secure Computer
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Computing Security And Privacy Icon
Cloud Computing Security And Privacy IconPresenting our set of slides with name Cloud Computing Security And Privacy Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Computing, Security And Privacy Icon.
-
 Cloud Architecture And Security Multi Cloud Computing Stack For Applications Need A Highly Scalable
Cloud Architecture And Security Multi Cloud Computing Stack For Applications Need A Highly ScalableThis slide covers the reasons to choose SaaS infrastructure when business grows as all applications would need a highly scalable platform. Present the topic in a bit more detail with this Cloud Architecture And Security Multi Cloud Computing Stack For Applications Need A Highly Scalable. Use it as a tool for discussion and navigation on Multi Cloud, Computing Stack, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cps Security And Privacy Life Cycle Next Generation Computing Systems Ppt Show Graphics Design
Cps Security And Privacy Life Cycle Next Generation Computing Systems Ppt Show Graphics DesignThis slide depicts the cyber-physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Present the topic in a bit more detail with this Cps Security And Privacy Life Cycle Next Generation Computing Systems Ppt Show Graphics Design. Use it as a tool for discussion and navigation on Performance, Operational, Capability . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
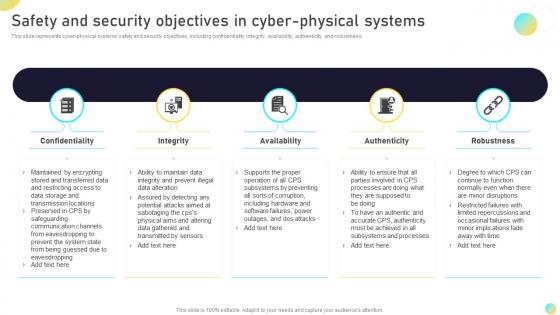 Safety And Security Objectives In Cyber Physical Systems Next Generation Computing Systems
Safety And Security Objectives In Cyber Physical Systems Next Generation Computing SystemsThis slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present the topic in a bit more detail with this Safety And Security Objectives In Cyber Physical Systems Next Generation Computing Systems. Use it as a tool for discussion and navigation on Confidentiality, Availability, Authenticity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Strategic Planning Process For Cps Next Generation Computing Systems
Security Strategic Planning Process For Cps Next Generation Computing SystemsThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Present the topic in a bit more detail with this Security Strategic Planning Process For Cps Next Generation Computing Systems. Use it as a tool for discussion and navigation on Strategic, Planning, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps For Cps Security Strategy Plan Next Generation Computing Systems Ppt Show Design Inspiration
Steps For Cps Security Strategy Plan Next Generation Computing Systems Ppt Show Design InspirationThis slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Present the topic in a bit more detail with this Steps For Cps Security Strategy Plan Next Generation Computing Systems Ppt Show Design Inspiration. Use it as a tool for discussion and navigation on Communicate, Implementation, Continuous Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Strategy Icon Depicting Computer Protection
Cyber Security Strategy Icon Depicting Computer ProtectionIntroducing our premium set of slides with name Cyber Security Strategy Icon Depicting Computer Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Strategy Icon, Depicting Computer, Protection. So download instantly and tailor it with your information.
-
 Applications Of Confidential Computing Security Technology
Applications Of Confidential Computing Security TechnologyThe following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting our set of slides with name Applications Of Confidential Computing Security Technology. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Guard Business Process, Collaboration, Customer Satisfaction.
-
 Cloud Computing Security Technology Framework
Cloud Computing Security Technology FrameworkThis slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Introducing our premium set of slides with Cloud Computing Security Technology Framework. Elucidate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security, Network Security, Others, Monitoring, Governance. So download instantly and tailor it with your information.
-
 Five Elements Of Cloud Computing Security
Five Elements Of Cloud Computing SecurityThis slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting our set of slides with Five Elements Of Cloud Computing Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Compliance, Monitor Visibility, Authentication.
-
 Cloud Computing Security Of Cloud Storage Ppt Powerpoint Summary
Cloud Computing Security Of Cloud Storage Ppt Powerpoint SummaryThis slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Of Cloud Storage Ppt Powerpoint Summary. This template helps you present information on five stages. You can also present information on Technology Failures, Cloud Storage, Data Redundancy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Strategies For Cloud Computing Security
Various Strategies For Cloud Computing SecurityThis slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Introducing our Various Strategies For Cloud Computing Security set of slides. The topics discussed in these slides are Secure Data Transfers, Local Data Backups, Vulnerability Assessments. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Peer Computer Network In Powerpoint And Google Slides Cpb
Security Peer Computer Network In Powerpoint And Google Slides CpbPresenting our Security Peer Computer Network In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Peer Computer Network This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Introduction To Grid Computing Security Model Ppt Powerpoint Presentation Slides Design
Introduction To Grid Computing Security Model Ppt Powerpoint Presentation Slides DesignThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Present the topic in a bit more detail with this Introduction To Grid Computing Security Model Ppt Powerpoint Presentation Slides Design. Use it as a tool for discussion and navigation on Grid Security Model, Policy Expression And Exchange, Binding Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Grid Computing Security Ppt Powerpoint Presentation Icon Graphics Pictures
Key Components Of Grid Computing Security Ppt Powerpoint Presentation Icon Graphics PicturesThis slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Introducing Key Components Of Grid Computing Security Ppt Powerpoint Presentation Icon Graphics Pictures to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Grid Security Infrastructure, Grid Network Communicate, Authorization Processes, using this template. Grab it now to reap its full benefits.
-
 Confidential Edge Computing IoT Security Strategy
Confidential Edge Computing IoT Security StrategyThe following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction.Introducing our premium set of slides with Confidential Edge Computing IoT Security Strategy. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Guard Business, Process Customer Satisfaction. So download instantly and tailor it with your information.
-
 IoT Edge Computing Security Technology Icon
IoT Edge Computing Security Technology IconPresenting our well structured IoT Edge Computing Security Technology Icon. The topics discussed in this slide are Iot Edge Computing, Security Technology Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IoT Edge Computing Security Technology Image
IoT Edge Computing Security Technology ImagePresenting our set of slides with IoT Edge Computing Security Technology Image. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Iot Edge Computing, Security Technology Image.
-
 Computer Device Digital Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Device Digital Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for illustrating digital security topics. It features a padlock in a vibrant blue colour, making it an eye-catching addition to any presentation. It is easy to use and can be resized to fit any project.
-
 Computer Device Digital Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Device Digital Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for presentations on digital security. It features a padlock icon, representing the importance of keeping data secure. Its simple and easy to understand, making it an ideal choice for any digital security presentation.
-
 F1541 Confidential Computing Market Driven By Cloud And Security Initiatives Confidential Cloud Computing
F1541 Confidential Computing Market Driven By Cloud And Security Initiatives Confidential Cloud ComputingThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this F1541 Confidential Computing Market Driven By Cloud And Security Initiatives Confidential Cloud Computing. Dispense information and present a thorough explanation of Initiatives, Confidential, Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Serverless Computing Best Practices For Improving Serverless Application Security
Serverless Computing Best Practices For Improving Serverless Application SecurityThe purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties. Increase audience engagement and knowledge by dispensing information using Serverless Computing Best Practices For Improving Serverless Application Security. This template helps you present information on four stages. You can also present information on Safeguard Critical Data, Appropriate Security Logging, Dependence On External Parties, Serverless Application Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Serverless Computing Serverless Computing Security Problems And Risks
Serverless Computing Serverless Computing Security Problems And RisksThe purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc. Present the topic in a bit more detail with this Serverless Computing Serverless Computing Security Problems And Risks. Use it as a tool for discussion and navigation on Serverless Computing, Security Problems And Risks, Insufficient Function, Recording And Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Computer Data Access Icon
Secure Computer Data Access IconIntroducing our premium set of slides with name Secure Computer Data Access Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Computer, Data Access Icon. So download instantly and tailor it with your information.
-
 Secure Data Access Methods For Cloud Computing
Secure Data Access Methods For Cloud ComputingThis slide describes the various methods to access the data stored in a cloud environment securely. The purpose of this slide is to represent secure data access for cloud computing users. The methods include cloud based access through a relational database management system, cloud based data warehousing and a cloud data lake. Introducing our Secure Data Access Methods For Cloud Computing set of slides. The topics discussed in these slides are Data Storage Updates, Encrypted Data, Data Access Request. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Computer Password Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Password Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is a great visual aid for representing computer passwords. It features a key with a lock, indicating security and access control. The bright, vibrant colours make it easy to spot and identify in presentations.
-
 Computer Password Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Password Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is a great way to visually represent the importance of computer passwords. It is a simple yet powerful image that will help your presentation stand out.
-
 Secured Computer Password Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Secured Computer Password Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is a great visual aid for representing computer passwords. It features a key with a lock, indicating security and access control. The bright, vibrant colours make it easy to spot and identify in presentations.
-
 Secured Computer Password Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Secured Computer Password Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is a great way to visually represent the importance of computer passwords. It is a simple yet powerful image that will help your presentation stand out.
-
 Computer Website Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Website Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for representing website security. It features a padlock and a shield, both in bright, vibrant colours, to symbolise the importance of keeping your website safe and secure. Its the ideal way to show your customers that you take website security seriously.
-
 Computer Website Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Website Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for any presentation on website security. It features a modern, minimalist design and is sure to add a professional touch to your slides. Its the perfect way to illustrate the importance of website security in a visually appealing way.
-
 Best Home Computer Security Software In Powerpoint And Google Slides Cpb
Best Home Computer Security Software In Powerpoint And Google Slides CpbPresenting Best Home Computer Security Software In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Best Home Computer Security Software. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secure Computer Folder Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Computer Folder Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is an ideal visual aid to represent documents security. It is bright and eye-catching, making it perfect for presentations and other materials. Its simple design ensures that it is easy to understand and will be remembered by viewers.
-
 Secure Computer Folder Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Computer Folder Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon is the perfect visual representation of Documents Security. It is a simple, yet powerful image that will help you communicate the importance of protecting confidential information in an effective and visually appealing way.
-
 Security Architecture Review Of A Cloud Cloud Computing Software Opportunities And Innovation
Security Architecture Review Of A Cloud Cloud Computing Software Opportunities And InnovationThis slide covers the current situation of cloud computing and software covering new opportunities and innovation for those willing to implement the change. Introducing Security Architecture Review Of A Cloud Cloud Computing Software Opportunities And Innovation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Computing, Software Opportunities, Innovation, using this template. Grab it now to reap its full benefits.
-
 Benefits Reaped Through Cloud Computing Security
Benefits Reaped Through Cloud Computing SecurityThe slide showcases benefits of cloud security that continuously help monitor, identify, analyze and mitigate attacks. The elements are optimize security cost, automated security, response time , centralize security with easy management , reliability with easy access . Presenting our set of slides with Benefits Reaped Through Cloud Computing Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Optimize Security Cost, Response Time, Future Considerations.
-
 Cloud Computing Security Architecture And Boundaries
Cloud Computing Security Architecture And BoundariesThe slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Introducing our Cloud Computing Security Architecture And Boundaries set of slides. The topics discussed in these slides are Presentation Mobility, Presentation Platform, Boundaries This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Computing Security Threats And Solutions
Cloud Computing Security Threats And SolutionsThe slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting our well structured Cloud Computing Security Threats And Solutions. The topics discussed in this slide are Account Hijacking, Weak Control Plane, Threats This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Computing Security Tools And Package
Cloud Computing Security Tools And PackageThe slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Introducing our Cloud Computing Security Tools And Package set of slides. The topics discussed in these slides are Cloud, Computing, Tools This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Computing Security Training Programs Timeline
Cloud Computing Security Training Programs TimelineThe slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package. Presenting our well structured Cloud Computing Security Training Programs Timeline. The topics discussed in this slide are Computing, Cloud, Training This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Digital Cloud Computing Cyber Security Icon
Digital Cloud Computing Cyber Security IconIntroducing our premium set of slides with Digital Cloud Computing Cyber Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Digital Cloud Computing, Cyber Security Icon So download instantly and tailor it with your information.
-
 Key Cloud Computing Security Challenges
Key Cloud Computing Security ChallengesThe slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures. Presenting our set of slides with Key Cloud Computing Security Challenges. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Breaches, Data Loss, Security
-
 Levels Of Security Concerns In Cloud Computing
Levels Of Security Concerns In Cloud ComputingThe slide showcases levels of security concerns that measure user and device authentication. The elements are virtual machine security , network security , interface security , privacy concerns etc. Introducing our premium set of slides with Levels Of Security Concerns In Cloud Computing. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Virtual Machine Security, Interface Security, Network Security So download instantly and tailor it with your information.
-
 Network Cloud Computing Security Analysis Icon
Network Cloud Computing Security Analysis IconPresenting our set of slides with Network Cloud Computing Security Analysis Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Cloud Computing, Security Analysis Icon
-
 Shared Responsibility For Cloud Computing Security
Shared Responsibility For Cloud Computing SecurityThe slide represents shared responsibilities that dictate security obligations ensuring accountability of both the cloud computing provider and its users. The elements are responsibilities such a data classification, client and end point protection, identity and access management etc. Introducing our Shared Responsibility For Cloud Computing Security set of slides. The topics discussed in these slides are Management, Data Classification, Host Infrastructure This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Factors For Cloud Computing Security Audit
Factors For Cloud Computing Security AuditThe slide highlights the factors to be considered while auditing the cloud services for data protection. Various factors considered are transparency, encryption and colocation. Introducing our premium set of slides with factors for Factors For Cloud Computing Security Audit. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Transparency, Encryption, Colocation . So download instantly and tailor it with your information.
-
 Agenda Deploying Computer Security Incident Management
Agenda Deploying Computer Security Incident ManagementIntroducing Agenda Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Agenda, using this template. Grab it now to reap its full benefits.
-
 B98 Table Of Contents For Deploying Computer Security Incident Management
B98 Table Of Contents For Deploying Computer Security Incident ManagementPresent the topic in a bit more detail with this B98 Table Of Contents For Deploying Computer Security Incident Management . Use it as a tool for discussion and navigation on Best Practices, Cyber Security, Incident Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Implementing Web Application Firewall Deploying Computer Security Incident
Benefits Of Implementing Web Application Firewall Deploying Computer Security IncidentThis slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc.Present the topic in a bit more detail with this Benefits Of Implementing Web Application Firewall Deploying Computer Security Incident. Use it as a tool for discussion and navigation on Provides Signature, Protects Against, Fights Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Cybersecurity Incident Management Deploying Computer Security Incident
Best Practices For Cybersecurity Incident Management Deploying Computer Security IncidentThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc.Increase audience engagement and knowledge by dispensing information using Best Practices For Cybersecurity Incident Management Deploying Computer Security Incident. This template helps you present information on five stages. You can also present information on Incident Management, Management Process, Responsibilities Members using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Common Sources Of Precursors And Indicators Deploying Computer Security Incident Management
Common Sources Of Precursors And Indicators Deploying Computer Security Incident ManagementThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc.Present the topic in a bit more detail with this Common Sources Of Precursors And Indicators Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Antivirus Software, Based Guarantee, Operating System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident Management
Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident ManagementThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery.Present the topic in a bit more detail with this Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Business Continuity, Incident Response, Review Recovery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Event And Incident Flow Diagram Deploying Computer Security Incident Management
Cyber Security Event And Incident Flow Diagram Deploying Computer Security Incident ManagementThis slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation.Present the topic in a bit more detail with this Cyber Security Event And Incident Flow Diagram Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Information Collection, Confirmed Security Incident, Categorize Incidents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management
Cyber Security Incident Communication Strategy Deploying Computer Security Incident ManagementThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders.Introducing Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Impacted Business, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handler Contact Information Deploying Computer Security Incident Management
Cyber Security Incident Handler Contact Information Deploying Computer Security Incident ManagementThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler.Present the topic in a bit more detail with this Cyber Security Incident Handler Contact Information Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Incident Response Management, Forensic Expert, Law Enforcement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Handling Checklist Deploying Computer Security Incident Management
Cyber Security Incident Handling Checklist Deploying Computer Security Incident ManagementThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handling Checklist Deploying Computer Security Incident Management. This template helps you present information on one stage. You can also present information on Containment Eradication, Acquisition Preservation, Incident Containment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist After An Incident Deploying Computer Security
Cyber Security Incident Management Checklist After An Incident Deploying Computer SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident.Introducing Cyber Security Incident Management Checklist After An Incident Deploying Computer Security to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Reporting Requirements, Quantify Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Team Structure Deploying Computer Security Incident Management
Cyber Security Incident Management Team Structure Deploying Computer Security Incident ManagementThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure Deploying Computer Security Incident Management. This template helps you present information on five stages. You can also present information on Systems Analyst, Network Analyst, Firewall Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management
Cyber Security Incident Response Lifecycle Deploying Computer Security Incident ManagementThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc.Introducing Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Eradication Recovery, Post Incident Activity, Remove Malwares, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Plan Timeline Deploying Computer Security Incident Management
Cyber Security Incident Response Plan Timeline Deploying Computer Security Incident ManagementThis slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow.Present the topic in a bit more detail with this Cyber Security Incident Response Plan Timeline Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Cyber Incident, Verification Incident, Dispatch Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.





