Powerpoint Templates and Google slides for Secure Computation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Methods For Enhancing Computer Server Security
Methods For Enhancing Computer Server SecurityFollowing slide showcases enhancing computer server security through different methods, also including elements such as firewalls, antivirus software, encryption, secure communications, etc. Presenting our set of slides with Methods For Enhancing Computer Server Security. This exhibits information on sevenstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Intrusion Detection Systems, Antivirus Software, Secure Communications.
-
 Server Security And Computer Networking System Icon
Server Security And Computer Networking System IconPresenting our set of slides with Server Security And Computer Networking System Icon. This exhibits information on threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Server Security, Computer Networking System.
-
 Incorporating Secure Multi-Party Computation To Boost Data Ai Driven Digital Transformation Planning DT SS
Incorporating Secure Multi-Party Computation To Boost Data Ai Driven Digital Transformation Planning DT SSThis slide provides glimpse about utilizing secure multi-party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Present the topic in a bit more detail with this Incorporating Secure Multi-Party Computation To Boost Data Ai Driven Digital Transformation Planning DT SS. Use it as a tool for discussion and navigation on Secure Computation, Output Reconstruction, Input Sharing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incorporating Secure Multi Party Computation To Boost Complete Guide Of Digital Transformation DT SS V
Incorporating Secure Multi Party Computation To Boost Complete Guide Of Digital Transformation DT SS VThis slide provides glimpse about utilizing secure multi-party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Present the topic in a bit more detail with this Incorporating Secure Multi Party Computation To Boost Complete Guide Of Digital Transformation DT SS V. Use it as a tool for discussion and navigation on Benefits, Secure Computation, Output Reconstruction, Input Sharing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitoring Computer Safety Lock Icon For Cyber Security
Monitoring Computer Safety Lock Icon For Cyber SecurityPresenting our set of slides with Monitoring Computer Safety Lock Icon For Cyber Security This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring Computer Safety, Cyber Security.
-
 Monitoring Cyber Risk Icon For Computer Security
Monitoring Cyber Risk Icon For Computer SecurityIntroducing our premium set of slides with Monitoring Cyber Risk Icon For Computer Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitoring Cyber Risk, Computer Security. So download instantly and tailor it with your information.
-
 Improving Security By Green Computing Technology Carbon Free Computing
Improving Security By Green Computing Technology Carbon Free ComputingThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Present the topic in a bit more detail with this Improving Security By Green Computing Technology Carbon Free Computing. Use it as a tool for discussion and navigation on Green Computing Technology, Computers And Networks, Security Concerns And Solution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ATP Computer Cyber Security Flow Icon
ATP Computer Cyber Security Flow IconPresenting our set of slides with name ATP Computer Cyber Security Flow Icon. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on ATP Computer, Cyber Security Flow Icon.
-
 Key Elements Of Computer Network Media Security
Key Elements Of Computer Network Media SecurityThis slide showcases major elements of network media security to minimize risk of unauthorized entry and protecting sensitive information from attackers. It involves elements such as firewalls, encryption, network segmentation etc. Introducing our premium set of slides with Key Elements Of Computer Network Media Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Prevention System, Network Segmentation, Network Access Control. So download instantly and tailor it with your information.
-
 Types Of Computer Network Security Software
Types Of Computer Network Security SoftwareThis slide covers categories of computer network security such as access control, antivirus, cloud security, firewall, and sandbox to safeguard digital assets and sensitive information by detecting, preventing, and mitigating cybersecurity threats. Introducing our premium set of slides with Types Of Computer Network Security Software. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Cloud Security, Security Software. So download instantly and tailor it with your information.
-
 Computer Security Icon For Cyber Risk Management
Computer Security Icon For Cyber Risk ManagementPresenting our set of slides with Computer Security Icon For Cyber Risk Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Computer Security Icon, Cyber Risk Management.
-
 Computer Safety Through Hids Cyber Security Icon
Computer Safety Through Hids Cyber Security IconPresenting our set of slides with Computer Safety Through Hids Cyber Security Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Icon, Computer.
-
 Computing Malware Virus Icon For Security Vulnerability
Computing Malware Virus Icon For Security VulnerabilityIntroducing our premium set of slides with Computing Malware Virus Icon For Security Vulnerability Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Computing Malware Virus, Security Vulnerability So download instantly and tailor it with your information.
-
 Ai Network Security Icon With Cloud Computing
Ai Network Security Icon With Cloud ComputingIntroducing our Ai Network Security Icon With Cloud Computing set of slides. The topics discussed in these slides are AI Network Security, Cloud Computing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS
Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Increase audience engagement and knowledge by dispensing information using Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Privacy Preservation, Secure Cloud Computing, Model Owner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS
Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing secure multi party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Increase audience engagement and knowledge by dispensing information using Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Increase Security Against Attacks, Boost Data Confidentiality, Input Sharing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your SEO and web security with our eye-catching PowerPoint icon. Featuring vibrant colours and a sleek design, this icon represents the importance of managing cyber security while optimizing your website for search engines. Perfect for presentations and training materials, its a must-have for any business or individual focused on online success.
-
 Computer Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is a must-have for any presentation on SEO and web cyber security management. With a sleek and professional design, it conveys the importance of protecting your online presence. Use it to enhance your slides and emphasize the crucial role of security in todays digital landscape.
-
 Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on cyber risk management with our vibrant Computer Security PowerPoint icon. This eye-catching icon features a lock symbol in bold colors, representing the importance of safeguarding your data and systems. Perfect for showcasing the importance of cyber security in todays digital age.
-
 Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the importance of computer security in cyber risk management. It is a visual representation of the need for safeguarding sensitive information and protecting against potential cyber threats. Use this icon to enhance presentations on cyber security and emphasize the significance of risk management in the digital world.
-
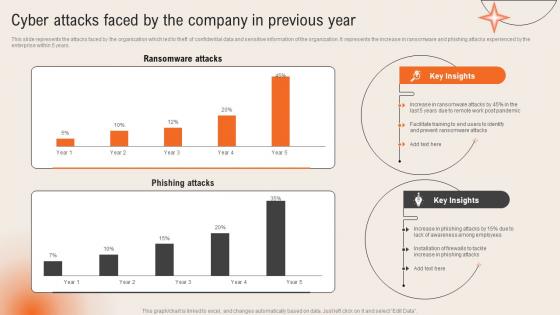 Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident Management
Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident ManagementThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years.Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks, Awareness Among Employees. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Analytics Dashboard Slide For Computer Security Infographic Template
Business Analytics Dashboard Slide For Computer Security Infographic TemplateThis is our Business Analytics Dashboard Slide For Computer Security Infographic Template designed in PowerPoint, however, you can also access it in Google Slides. It comes in two aspect ratios standard and widescreen, with fully-editable visual content.
-
 Cloud Computing Security Architecture Of Cloud Security Cont
Cloud Computing Security Architecture Of Cloud Security ContThis slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an outstanding presentation on the topic using this Cloud Computing Security Architecture Of Cloud Security Cont. Dispense information and present a thorough explanation of Providers Responsibility, End User Security And Monitoring, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Computing Security How To Manage Security In Cloud Cont Ppt Professional
Cloud Computing Security How To Manage Security In Cloud Cont Ppt ProfessionalThis slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How To Manage Security In Cloud Cont Ppt Professional. This template helps you present information on four stages. You can also present information on Firewalls, Access Controls, Data Masking, Data Recovery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Cloud Computing Security Cont Ppt Formates
Table Of Contents For Cloud Computing Security Cont Ppt FormatesIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Cloud Computing Security Cont Ppt Formates. This template helps you present information on six stages. You can also present information on Cloud Security Management, Working Of Cloud Security, Cloud Security Solutions, Cloud Security Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Budget Allocation For Cyber Incident Management Training Deploying Computer Security
Budget Allocation For Cyber Incident Management Training Deploying Computer SecurityThis slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc.Present the topic in a bit more detail with this Budget Allocation For Cyber Incident Management Training Deploying Computer Security. Use it as a tool for discussion and navigation on Training Budget, Supply Chain, Operational. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
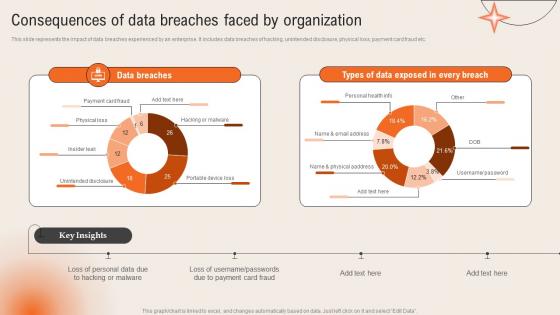 Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management
Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident ManagementThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc.Present the topic in a bit more detail with this Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Unintended Disclosure, Portable Device, Hacking Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
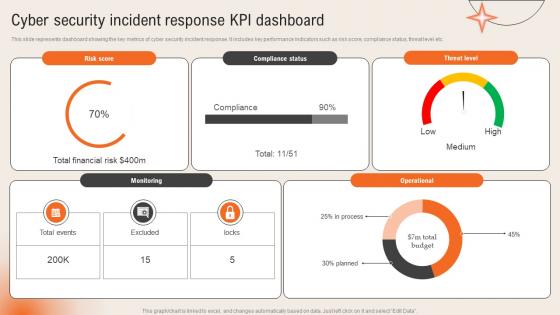 Cyber Security Incident Response Kpi Dashboard Deploying Computer Security Incident Management
Cyber Security Incident Response Kpi Dashboard Deploying Computer Security Incident ManagementThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc.Present the topic in a bit more detail with this Cyber Security Incident Response Kpi Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Compliance Status, Threat Level, Operational. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident
Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security IncidentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident. Use it as a tool for discussion and navigation on Expiring Password, Accessible Directories, Directories Direct Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
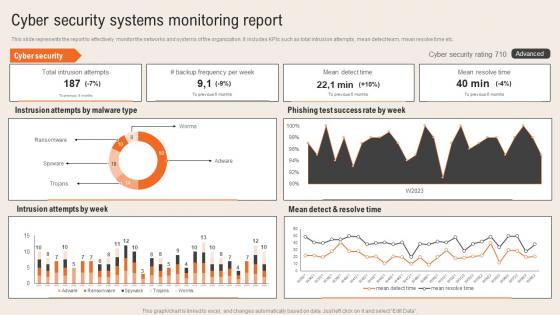 Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management
Cyber Security Systems Monitoring Report Deploying Computer Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc.Present the topic in a bit more detail with this Cyber Security Systems Monitoring Report Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Intrusion Attempts, Ransomware, Phishing Test Success. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management
Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc.Present the topic in a bit more detail with this Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Resource Security Hygiene, Subscription Coverage, Resource Health Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
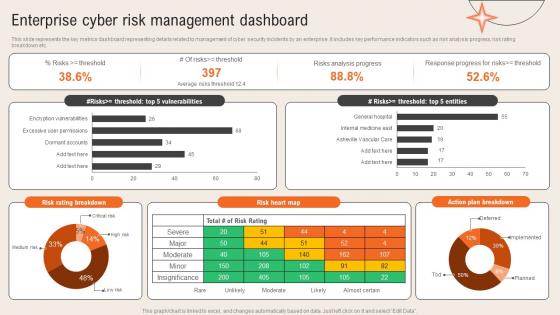 Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management
Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc.Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Risks Analysis Progress, Response Progress, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Driven By Cloud And Security Initiatives Ppt Slides Summary
Confidential Computing Market Driven By Cloud And Security Initiatives Ppt Slides SummaryThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Driven By Cloud And Security Initiatives Ppt Slides Summary. Dispense information and present a thorough explanation of Confidential Computing TAM, Growth Drivers, Key Takeaways using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Wireless security camera connected with computer system
Wireless security camera connected with computer systemIntroducing our premium set of slides with Wireless Security Camera Connected With Computer System. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Wireless Security Camera Connected With Computer System. So download instantly and tailor it with your information.
-
 Computer security incident ppt powerpoint presentation professional tips cpb
Computer security incident ppt powerpoint presentation professional tips cpbPresenting Computer Security Incident Ppt Powerpoint Presentation Professional Tips Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Computer Security Incident. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security considerations cloud computing ppt powerpoint presentation show mockup cpb
Security considerations cloud computing ppt powerpoint presentation show mockup cpbPresenting Security Considerations Cloud Computing Ppt Powerpoint Presentation Show Mockup Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Considerations Cloud Computing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Electronic information security framework in cloud computing
Electronic information security framework in cloud computingThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Introducing Electronic Information Security Framework In Cloud Computing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Recover, Respond, Identify, Protect, Detect, using this template. Grab it now to reap its full benefits.
-
 Computer crime security survey ppt powerpoint presentation infographics graphics cpb
Computer crime security survey ppt powerpoint presentation infographics graphics cpbPresenting Computer Crime Security Survey Ppt Powerpoint Presentation Infographics Graphics Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Analysis Interpretation. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computer network security audit ppt powerpoint presentation example cpb
Computer network security audit ppt powerpoint presentation example cpbPresenting Computer Network Security Audit Ppt Powerpoint Presentation Example Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Computer Network Security Audit. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Icon Of Computer Security Program For Protection
Icon Of Computer Security Program For ProtectionIntroducing our premium set of slides with Icon Of Computer Security Program For Protection. Elucidate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Computer Security Program For Protection. So download instantly and tailor it with your information.
-
 Secure data storage cloud computings ppt powerpoint presentation example cpb
Secure data storage cloud computings ppt powerpoint presentation example cpbPresenting Secure Data Storage Cloud Computings Ppt Powerpoint Presentation Example Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Data Storage Cloud Computings. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computer Security Small Business Ppt Powerpoint Presentation Pictures Guide Cpb
Computer Security Small Business Ppt Powerpoint Presentation Pictures Guide CpbPresenting our Computer Security Small Business Ppt Powerpoint Presentation Pictures Guide Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Computer Security Small Business. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Framework In Cloud Computing Information Security
Security Framework In Cloud Computing Information SecurityThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Introducing Security Framework In Cloud Computing Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Protect, Respond, using this template. Grab it now to reap its full benefits.
-
 Difference Computer Security Information Security Ppt Powerpoint Presentation Deck Cpb
Difference Computer Security Information Security Ppt Powerpoint Presentation Deck CpbPresenting Difference Computer Security Information Security Ppt Powerpoint Presentation Deck Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Difference Computer Security Information Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Network Security Security Framework In Cloud Computing
Network Security Security Framework In Cloud ComputingThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Introducing Network Security Security Framework In Cloud Computing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Business, Requirements, Technology, Processes, Strategy, using this template. Grab it now to reap its full benefits.
-
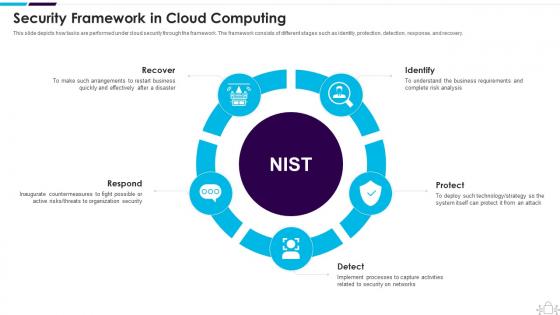 Security Framework In Cloud Computing Information Technology Security
Security Framework In Cloud Computing Information Technology SecurityThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Increase audience engagement and knowledge by dispensing information using Security Framework In Cloud Computing Information Technology Security. This template helps you present information on five stages. You can also present information on Recover, Respond, Identify using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer Security Technical Assessment Process
Computer Security Technical Assessment ProcessThis slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Introducing our premium set of slides with Computer Security Technical Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Analyse, Prioritize, Monitoring. So download instantly and tailor it with your information.
-
 Distributed computing security of data and networks in distributed computing
Distributed computing security of data and networks in distributed computingThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Present the topic in a bit more detail with this Distributed Computing Security Of Data And Networks In Distributed Computing. Use it as a tool for discussion and navigation on Element, Computing, Protection, System, Network, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Of Data And Networks In Edge Computing Distributed Information Technology
Security Of Data And Networks In Edge Computing Distributed Information TechnologyThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Deliver an outstanding presentation on the topic using this Security Of Data And Networks In Edge Computing Distributed Information Technology. Dispense information and present a thorough explanation of Security Of Data And Networks In Edge Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Ways To Secure Cloud Infrastructure From Security Threats Optimization Of Cloud Computing
Key Ways To Secure Cloud Infrastructure From Security Threats Optimization Of Cloud ComputingMentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Introducing Key Ways To Secure Cloud Infrastructure From Security Threats Optimization Of Cloud Computing to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Key Takeaways, Hardware Maintenance, Improvement In Service using this template. Grab it now to reap its full benefits.
-
 Computer Cyber Security Framework Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Cyber Security Framework Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Computer cyber security framework colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Computer Cyber Security Framework Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Cyber Security Framework Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Computer cyber security framework monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Agenda For Cloud Computing Security Ppt Infographics Information
Agenda For Cloud Computing Security Ppt Infographics InformationIntroducing Agenda For Cloud Computing Security Ppt Infographics Information to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Service Providers, Cloud Security, Organizations Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In Business
Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In BusinessThis slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In Business. This template helps you present information on three stages. You can also present information on Monitor Data Activities, User Behavior, Cloud Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security Checklist To Implement Cloud Security In Business
Cloud Computing Security Checklist To Implement Cloud Security In BusinessThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Cloud Computing Security Checklist To Implement Cloud Security In Business to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Logging And Monitoring, Data Encryption, Backup And Data Recovery, Policies And Procedures, Networking, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT Solutions
Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT SolutionsThis slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Difference Between Cloud Security Solutions And Traditional IT Solutions. This template helps you present information on two stages. You can also present information on Cloud Security, Traditional It Security, Low Efficiency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security Enterprise Cloud Security Solutions Ppt Sample
Cloud Computing Security Enterprise Cloud Security Solutions Ppt SampleThis slide describes the enterprise cloud security solutions, including multi factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost benefits of hybrid cloud. Present the topic in a bit more detail with this Cloud Computing Security Enterprise Cloud Security Solutions Ppt Sample. Use it as a tool for discussion and navigation on Multi Factor Authentication, Business Operation, Company Networks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Computing Security Essential Pillars Of Cloud Security Ppt Pictures
Cloud Computing Security Essential Pillars Of Cloud Security Ppt PicturesThis slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security. Introducing Cloud Computing Security Essential Pillars Of Cloud Security Ppt Pictures to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Visibility And Consistency, Process Based Security, Network Security, Identity Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security How Does Cloud Security Work Data Retention And Business
Cloud Computing Security How Does Cloud Security Work Data Retention And BusinessThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Data Retention And Business. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Testing And Maintenance, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Data Security
Cloud Computing Security How Does Cloud Security Work Data SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Introducing Cloud Computing Security How Does Cloud Security Work Data Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Application Security, Physical Security, Internet Security, Endpoint Security, using this template. Grab it now to reap its full benefits.





