Powerpoint Templates and Google slides for Protection Computer
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Computer Security Significance Organization Information Protection Verification System
Computer Security Significance Organization Information Protection Verification SystemThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Computer Security Significance Organization Information Protection Verification System and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Antivirus Icon Exclamation Protection Computer Monitor
Antivirus Icon Exclamation Protection Computer MonitorThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Antivirus Icon Exclamation Protection Computer Monitor and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Cloud Security Icon Security Computing Data Protection Digital Access
Cloud Security Icon Security Computing Data Protection Digital AccessKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Computer virus protection symbol analysis process scanning gear
Computer virus protection symbol analysis process scanning gearIt covers all the important concepts and has relevant templates which cater to your business needs. This complete deck has PPT slides on Computer Virus Protection Symbol Analysis Process Scanning Gear with well suited graphics and subject driven content. This deck consists of total of eleven slides. All templates are completely editable for your convenience. You can change the colour, text and font size of these slides. You can add or delete the content as per your requirement. Get access to this professionally designed complete deck presentation by clicking the download button below.
-
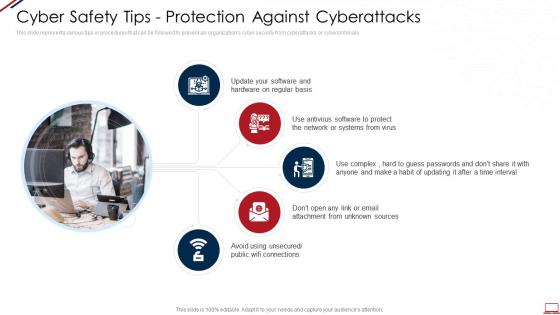 Cyber safety tips protection against cyberattacks computer system security
Cyber safety tips protection against cyberattacks computer system securityThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Cyber Safety Tips Protection Against Cyberattacks Computer System Security. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Market Technologies Used To Protect Data In Use
Confidential Computing Market Technologies Used To Protect Data In UseThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present the topic in a bit more detail with this Confidential Computing Market Technologies Used To Protect Data In Use. Use it as a tool for discussion and navigation on Technologies, Demonstrates, Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Technologies Used To Protect Data In Use
Confidential Computing Hardware Technologies Used To Protect Data In UseThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present the topic in a bit more detail with this Confidential Computing Hardware Technologies Used To Protect Data In Use. Use it as a tool for discussion and navigation on Protect The Information In Processing, Security And Scalability, Homomorphic Encryption, Multi Party Computation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium Technologies Used To Protect Data In Use
Confidential Computing Consortium Technologies Used To Protect Data In UseThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Technologies Used To Protect Data In Use. Dispense information and present a thorough explanation of Protecting Technologies, Security And Scalability, Technologies Homomorphic Encryption, Multi Party Computation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technologies Used To Protect Data In Use Confidential Computing System Technology
Technologies Used To Protect Data In Use Confidential Computing System TechnologyThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Deliver an outstanding presentation on the topic using this Technologies Used To Protect Data In Use Confidential Computing System Technology. Dispense information and present a thorough explanation of Technologies, Security Comparison, Scalability Comparison using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Content Protection Mechanisms In Mobile Comprehensive Guide To Mobile Cloud Computing
Content Protection Mechanisms In Mobile Comprehensive Guide To Mobile Cloud ComputingThe purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc. Deliver an outstanding presentation on the topic using this Content Protection Mechanisms In Mobile Comprehensive Guide To Mobile Cloud Computing. Dispense information and present a thorough explanation of Protection, Mechanisms, Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Protection Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Protection Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of secure computer. It is a modern, vibrant and eye catching icon that will help to create an impactful presentation. It is a great way to emphasize the importance of data security and safety.
-
 Firewall Protection Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Protection Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on secure computer systems. It features a black and white design depicting a computer with a padlock, symbolizing the safety of your data. Use this icon to emphasize the importance of secure computing.
-
 Confidential Computing V2 Technologies Used To Protect Data In Use
Confidential Computing V2 Technologies Used To Protect Data In UseThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present the topic in a bit more detail with this Confidential Computing V2 Technologies Used To Protect Data In Use. Use it as a tool for discussion and navigation on Homomorphic Encryption, Trusted Execution Environments, Privacy Preserving Computation, Protecting Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer Protection And Data Encryption Icon
Computer Protection And Data Encryption IconIntroducing our premium set of slides with name Computer Protection And Data Encryption Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Computer Protection, Data Encryption, Icon. So download instantly and tailor it with your information.
-
 Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on cyber risk management with our vibrant Computer Security PowerPoint icon. This eye-catching icon features a lock symbol in bold colors, representing the importance of safeguarding your data and systems. Perfect for showcasing the importance of cyber security in todays digital age.
-
 Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the importance of computer security in cyber risk management. It is a visual representation of the need for safeguarding sensitive information and protecting against potential cyber threats. Use this icon to enhance presentations on cyber security and emphasize the significance of risk management in the digital world.
-
 0914 disk to disk to tape storage replication between protected computer and tape library ppt slide
0914 disk to disk to tape storage replication between protected computer and tape library ppt slideWe are proud to present our 0914 disk to disk to tape storage replication between protected computer and tape library ppt slide. This image slide displays different methods of storage and backup. This image slide has been designed with graphic of servers with disks or tape. Use this image slide, in your presentations to express views on disk and tape storage, data protection manager and technology. This image slide will enhance the quality of your presentations.
-
 Icon Of Computer Security Program For Protection
Icon Of Computer Security Program For ProtectionIntroducing our premium set of slides with Icon Of Computer Security Program For Protection. Elucidate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Computer Security Program For Protection. So download instantly and tailor it with your information.
-
 Cloud Computing Security Phase 3 Respond To Cloud Protection Issues
Cloud Computing Security Phase 3 Respond To Cloud Protection IssuesThis slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver an outstanding presentation on the topic using this Cloud Computing Security Phase 3 Respond To Cloud Protection Issues. Dispense information and present a thorough explanation of Authentication Process, Cloud Service, Cloud Access Standards using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Automation And Multi Cloud Computing Data Protection Multi Cloud Data Encryption
Cloud Automation And Multi Cloud Computing Data Protection Multi Cloud Data EncryptionThis slide covers data protection and encryption framework in multi cloud with multi layer protection and data management. Deliver an outstanding presentation on the topic using this Cloud Automation And Multi Cloud Computing Data Protection Multi Cloud Data Encryption. Dispense information and present a thorough explanation of Data Protection, Multi Cloud, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Strategy Icon Depicting Computer Protection
Cyber Security Strategy Icon Depicting Computer ProtectionIntroducing our premium set of slides with name Cyber Security Strategy Icon Depicting Computer Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Strategy Icon, Depicting Computer, Protection. So download instantly and tailor it with your information.
-
 Computer Screen Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Screen Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is perfect for protecting your display from scratches and dust. It is made of high quality material and is easy to install. It is available in various colours and sizes to suit your needs. It provides a clear view and is highly durable.
-
 Computer Screen Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Screen Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is perfect for presentations and slideshows. It is designed to protect your display from scratches and dust, while also providing a sleek and modern look. Its lightweight and easy to install, and will keep your display looking great for years to come.
-
 Technologies Used To Protect Data In Use Confidential Cloud Computing
Technologies Used To Protect Data In Use Confidential Cloud ComputingThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Deliver an outstanding presentation on the topic using this Technologies Used To Protect Data In Use Confidential Cloud Computing. Dispense information and present a thorough explanation of Technologies, Homomorphic, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Protects Your Computer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Protects Your Computer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon features a shield protecting a computer. It is perfect for presentations related to cyber security, data protection, and online safety. It can also be used to illustrate the importance of safeguarding your digital assets.
-
 Confidential Computing It Technologies Used To Protect Data In Use Ppt Slides Styles
Confidential Computing It Technologies Used To Protect Data In Use Ppt Slides StylesThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi party computation, and so on. Introducing Confidential Computing It Technologies Used To Protect Data In Use Ppt Slides Styles to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Preserving Computation, Security Comparison, Scalability Comparison, using this template. Grab it now to reap its full benefits.
-
 Best Computer Protection Software In Powerpoint And Google Slides Cpb
Best Computer Protection Software In Powerpoint And Google Slides CpbPresenting Best Computer Protection Software In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Best Computer Protection Software. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computer kids pc outline with lock protection
Computer kids pc outline with lock protectionPresenting computer kids pc outline with lock protection. This is a computer kids pc outline with lock protection. This is a four stage process. The stages in this process are child computer, kids laptop, kids technology, computer kids.
-
 Binary codes protection error in computer ppt icons graphics
Binary codes protection error in computer ppt icons graphicsWe are proud to present our binary codes protection error in computer ppt icons graphics. This power point icon template diagram has been crafted with graphic of four technical icons. Concept of binary codes protection and error has been displayed in this power point template. Use this icon template for internet and computer technology related presentations.
-
 Computer networking hard disk gear protective shield ppt icons graphics
Computer networking hard disk gear protective shield ppt icons graphicsDownloads PPT plans with just a solitary tick. Easy to present association logo, trademark or name. Pictures depictions don't pixelate when expected on wide screen. Fully compatible with Google slides. Free of space impediments to pick titles and sub titles. Adjust design content creative style, substance, and shading and outline as displayed by your necessities. Run effectively with every one of programming's projects. Can be acceptably changed over into PDF or JPG organizes.
-
 Protect your computer document safety shield with woman protected voting ppt icons graphics
Protect your computer document safety shield with woman protected voting ppt icons graphicsPresenting protect your computer document safety shield with woman protected voting ppt icons graphics. This Power Point icons template has been crafted with graphic of computer, document and safety shield icons. This icon PPT contains the concept of document safety and protection representation. Use this icon PPT for business and technology related presentations.
-
 Computer system with firewall protection icon
Computer system with firewall protection iconPresenting this set of slides with name Computer System With Firewall Protection Icon. This is a three stage process. The stages in this process are Computer System With Firewall Protection Icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cloud computing data protection binary security codes
Cloud computing data protection binary security codesPresenting this set of slides with name Cloud Computing Data Protection Binary Security Codes. This is a three stage process. The stages in this process are Cloud Computing Data Protection Binary Security Codes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security system with shield protection verification
Computer security system with shield protection verificationPresenting this set of slides with name Computer Security System With Shield Protection Verification. This is a two stage process. The stages in this process are Computer Security System With Shield Protection Verification. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security using shield safe protection
Computer security using shield safe protectionPresenting this set of slides with name Computer Security Using Shield Safe Protection. This is a four stage process. The stages in this process are Computer Security Using Shield Safe Protection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Professional working on computer with security protection
Professional working on computer with security protectionPresenting this set of slides with name Professional Working On Computer With Security Protection. This is a three stage process. The stages in this process are Professional Working On Computer With Security Protection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer protected with information security software
Computer protected with information security softwarePresenting this set of slides with name Computer Protected With Information Security Software. This is a three stage process. The stages in this process are Computer Protected, Information Security, Software. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer virus with danger and protection symbol
Computer virus with danger and protection symbolPresenting this set of slides with name Computer Virus With Danger And Protection Symbol. This is a three stage process. The stages in this process are Computer Virus With Danger And Protection Symbol. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Protect icon displayed on computer screen
Protect icon displayed on computer screenPresenting this set of slides with name Protect Icon Displayed On Computer Screen. This is a five stage process. The stages in this process are Protect Icon Displayed On Computer Screen. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security threat with password protection reminder
Computer security threat with password protection reminderIntroducing our Computer Security Threat With Password Protection Reminder set of slides. The topics discussed in these slides are Computer Security Threat With Password Protection Reminder. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Computer protection software ppt powerpoint presentation model outfit cpb
Computer protection software ppt powerpoint presentation model outfit cpbPresenting our Computer Protection Software Ppt Powerpoint Presentation Model Outfit Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Computer Protection Software This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Compare computer virus protection ppt powerpoint inspiration template cpb
Compare computer virus protection ppt powerpoint inspiration template cpbPresenting our Compare Computer Virus Protection Ppt Powerpoint Inspiration Template Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Compare Computer Virus Protection This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Computer software protection ppt powerpoint presentation ideas clipart cpb
Computer software protection ppt powerpoint presentation ideas clipart cpbPresenting our Computer Software Protection Ppt Powerpoint Presentation Ideas Clipart Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Computer Software Protection This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Computer protection ppt powerpoint presentation gallery slide download cpb
Computer protection ppt powerpoint presentation gallery slide download cpbPresenting Computer Protection Ppt Powerpoint Presentation Gallery Slide Download Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase eight stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Computer Protection. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud data breach protection cloud computing standard architecture patterns ppt powerpoint slide
Cloud data breach protection cloud computing standard architecture patterns ppt powerpoint slideHere is a slide titled Cloud Data Breach Protection Cloud Computing Standard Architecture Patterns Ppt Powerpoint Slide. Describe cloud computing patterns and their applications using this contemporary presentation template available in standard and widescreen sizes. Topics such as Policies And Procedures, Inventory Of Data, Separation Of Duties can be discussed with the help of this PowerPoint theme. Hit the download button and instantly elevate your presentation with our customizable PPT template.
-
 Hypervisor protection cloud computing standard architecture patterns ppt presentation diagram
Hypervisor protection cloud computing standard architecture patterns ppt presentation diagramShowcase your expertise on cloud computing patterns by introducing this slide titled Hypervisor Protection Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as Operating System, Virtual Hardware, Management with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
 Permanent data loss protection cloud computing standard architecture patterns ppt powerpoint slide
Permanent data loss protection cloud computing standard architecture patterns ppt powerpoint slideShowcase your expertise on cloud computing patterns by introducing this slide titled Permanent Data Loss Protection Cloud Computing Standard Architecture Patterns Ppt Powerpoint Slide. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as Protection, Cloud Computing, Standard Architecture Patterns with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
 Cloud denial of service protection cloud computing standard architecture patterns ppt diagram
Cloud denial of service protection cloud computing standard architecture patterns ppt diagramShowcase your expertise on cloud computing patterns by introducing this slide titled Cloud Denial Of Service Protection Cloud Computing Standard Architecture Patterns Ppt Diagram. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as Misconfigured Sites, Covert Channels, Legitimate Traffic, Mitigation Service, Attack Traffic with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
 Cloud traffic hijacking protection cloud computing standard architecture patterns ppt diagram
Cloud traffic hijacking protection cloud computing standard architecture patterns ppt diagramUtilize this visually appealing slide titled Cloud Traffic Hijacking Protection Cloud Computing Standard Architecture Patterns Ppt Diagram. Elucidate the concept of cloud computing patterns using this editable PowerPoint presentation. Explain Traffic Monitor, Cloud Consumers Resource, Compromised Internet Router using this PPT theme. Instantly grab the attention of your audience by downloading this professionally designed PPT template.
-
 Computer file protection from virus and malware icon
Computer file protection from virus and malware iconIntroducing our premium set of slides with Computer File Protection From Virus And Malware Icon. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Computer File Protection From Virus And Malware Icon. So download instantly and tailor it with your information.
-
 Network security framework ensuring protection from computer virus
Network security framework ensuring protection from computer virusPresenting our set of slides with Network Security Framework Ensuring Protection From Computer Virus. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security Framework Ensuring Protection From Computer Virus.
-
 Protecting personal computer privacy from hacker
Protecting personal computer privacy from hackerIntroducing our premium set of slides with Protecting Personal Computer Privacy From Hacker. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protecting Personal Computer Privacy From Hacker. So download instantly and tailor it with your information.
-
 Internet cybersecurity protection icon for personal computer
Internet cybersecurity protection icon for personal computerPresenting our set of slides with Internet Cybersecurity Protection Icon For Personal Computer. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Internet Cybersecurity Protection Icon For Personal Computer.
-
 Computer security protection measures ppt powerpoint presentation file formats cpb
Computer security protection measures ppt powerpoint presentation file formats cpbPresenting our Computer Security Protection Measures Ppt Powerpoint Presentation File Formats Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Computer Security Protection Measures This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 User data protection cloud computing standard architecture patterns ppt presentation diagram
User data protection cloud computing standard architecture patterns ppt presentation diagramShowcase your expertise on cloud computing patterns by introducing this slide titled User Data Protection Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as User Data Protection, Cloud Computing, Standard Architecture Patterns with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
 0914 life belt around computer server for protection stock photo
0914 life belt around computer server for protection stock photoWe are proud to present our 0914 life belt around computer server for protection stock photo. This image is in .jpg format and is available in size 2000x2000. This image displays life belt around computer server. This image has been designed with graphic of black computer server with blue light and red and white life savers on white background. This image depicts workstation protection. Use this image, in your PowerPoint template to express views on client server computing and data security. This image will enhance the quality of your presentations.



