Powerpoint Templates and Google slides for Practice Protect
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
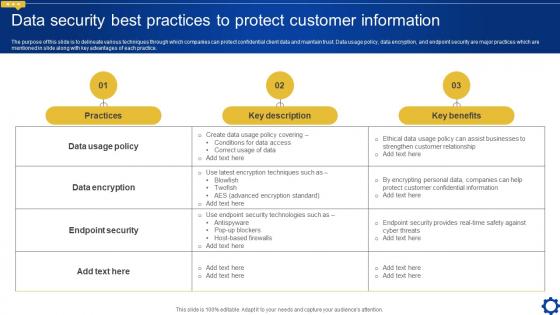 Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V
Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Present the topic in a bit more detail with this Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V. Use it as a tool for discussion and navigation on Practices, Key Description, Key Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
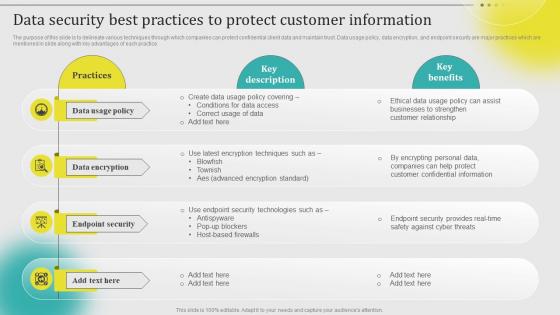 Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V
Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Data Security Best Practices To Protect Complete Introduction To Database MKT SS V
Data Security Best Practices To Protect Complete Introduction To Database MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Complete Introduction To Database MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V
Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V
Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V
Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V
Data Security Best Practices To Protect Using Customer Data To Improve MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V. Dispense information and present a thorough explanation of Policy, Data, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Protection Analytics Best Practices
Cyber Protection Analytics Best PracticesThe following slide highlights firewall protection, security software, strong password enforcement, two-factor authentication, and regular data backup to emphasize cybersecurity analytics best practices. It helps organizations fortify defenses and safeguard sensitive information from cyber threats. Introducing our premium set of slides with Cyber Protection Analytics Best Practices. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Firewall Protection, Security Software, Factor Authentication . So download instantly and tailor it with your information.
-
 Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V
Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V. Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Containerization Technology Security Best Practices To Protect Containerized Environments
Containerization Technology Security Best Practices To Protect Containerized EnvironmentsThis slide outlines the best practices for securing containerized environments. The purpose of this slide is to define the security best practices for organizations to protect containerized environments, and these are securing images, securing registries, securing deployments, and so on. Deliver an outstanding presentation on the topic using this Containerization Technology Security Best Practices To Protect Containerized Environments. Dispense information and present a thorough explanation of Securing Registries, Securing Deployment, Securing Container Runtime, Securing Kubernetes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Improve Cybersecurity In BCP For Data Protection
Best Practices To Improve Cybersecurity In BCP For Data ProtectionThis slide represents various best practices that helps businesses in improving cybersecurity against online data threats affecting business continuity. It includes practices such as using VPN, Training employees, backing up companies data, etc. Presenting our set of slides with Best Practices To Improve Cybersecurity In BCP For Data Protection This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Continuity Software, Backup Company, Train Employees
-
 Cybersecurity Best Practices To Protect Education Institutes
Cybersecurity Best Practices To Protect Education InstitutesThis slide highlights the best practices to protect education businesses. This slide aims to help the business improve its security measures by implementing practices such as regular patch applications, auditing user permissions, etc. Presenting our set of slides with Cybersecurity Best Practices To Protect Education Institutes. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Properly Configure Firewalls, Apply Patches Regularly, Audit User Permission Regularly.
-
 Best Practices To Ensure Protection Against Hacking
Best Practices To Ensure Protection Against HackingThis slide illustrates various tactics to protect organizational assets from sophisticated attacks. The purpose of this slide is to help businesses in securing their digital devices and networks by preventing unauthorized access. It covers approaches such as ensuring downloads from secure sources , installing antivirus software, using virtual private network and ensuring multi factor authentication.Presenting our set of slides with Best Practices To Ensure Protection Against Hacking This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Install Antivirus Software, Ensure Downloads, Secure Sources.
-
 Overview Of Windbreaks For Protecting Crops And Livestock Complete Guide Of Sustainable Agriculture Practices
Overview Of Windbreaks For Protecting Crops And Livestock Complete Guide Of Sustainable Agriculture PracticesThis slide provides glimpse about summary of windbreaks that can help in protecting agriculture produce and animals. It includes overview, favorable crops, benefits, etc. Present the topic in a bit more detail with this Overview Of Windbreaks For Protecting Crops And Livestock Complete Guide Of Sustainable Agriculture Practices Use it as a tool for discussion and navigation on Boost Income Generation, Benefits, Store Carbon And Sequestration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Protect Personal Guide To Use And Manage Credit Cards Effectively Fin SS
Best Practices To Protect Personal Guide To Use And Manage Credit Cards Effectively Fin SSThis slide shows multiple ways which can be used by individuals or people using credit cards to protect their personal information. These ways are secure card, PIN and passwords, be cautious and monitor. Introducing Best Practices To Protect Personal Guide To Use And Manage Credit Cards Effectively Fin SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Card, Passwords, Monitor, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Crypto Swap Attack Protection
Best Practices For Crypto Swap Attack ProtectionThis slide covers crypto swap attack protection best practices for better security such as using hardware funds, enabling 2FA, using virtual private network, etc. Presenting our set of slides with Best Practices For Crypto Swap Attack Protection This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Use Hardware Funds, Enable 2FA, Use Virtual Private Network
-
 Best Practices Involved For DOS Attack Protection
Best Practices Involved For DOS Attack ProtectionFollowing slide represents DOS attack protection involving best practices for time and cost savings. It further covers practices such as multilayered protection, avoid becoming bot, create DOS threat model and set priority buckets. Introducing our premium set of slides with name Best Practices Involved For DOS Attack Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Multilayered Protection, Avoid Becoming Bot, Set Priority Buckets. So download instantly and tailor it with your information.
-
 Email Security Best Practices Email Data Protection Overview And Features
Email Security Best Practices Email Data Protection Overview And FeaturesThe purpose of this slide is to discuss the Email Data Protection EDP solutions of email security. This slide highlights the features of Email Data Protection EDP , such as content-based email control, recipient authentication, data anonymization, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Data Protection Overview And Features. Use it as a tool for discussion and navigation on Content-Based Email Control, Recipient Authentication, Two-Factor Authentication, Data Anonymization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices Of Saas Governance For Enhancing Data Protection
Best Practices Of Saas Governance For Enhancing Data ProtectionThis slide represents various best practices that assist companies in implementing Software as a Service SaaS governance to enhance sensitive data security. It includes various practices such as information security policies, asset management, access control, etc. Introducing our Best Practices Of Saas Governance For Enhancing Data Protection set of slides. The topics discussed in these slides are Information Security Policies, Organization Of Information Security, Asset Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices To Protect Technology Systems Contd Distance Training Playbook
Best Practices To Protect Technology Systems Contd Distance Training PlaybookThis slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Introducing Best Practices To Protect Technology Systems Contd Distance Training Playbook to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Information, Compliance, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Protect Technology Systems E Learning Playbook Ppt Styles Background Designs
Best Practices To Protect Technology Systems E Learning Playbook Ppt Styles Background DesignsThis slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Increase audience engagement and knowledge by dispensing information using Best Practices To Protect Technology Systems E Learning Playbook Ppt Styles Background Designs. This template helps you present information on three stages. You can also present information on Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Protect Technology Systems Cont Online Education Playbook
Best Practices To Protect Technology Systems Cont Online Education PlaybookThis slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Present the topic in a bit more detail with this Best Practices To Protect Technology Systems Cont Online Education Playbook. Use it as a tool for discussion and navigation on Technology, Information, Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Protect Technology Systems Contd Online Training Playbook
Best Practices To Protect Technology Systems Contd Online Training PlaybookThis slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Introducing Best Practices To Protect Technology Systems Contd Online Training Playbook to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Information, Regulations, using this template. Grab it now to reap its full benefits.
-
 Technology Mediated Education Playbook Best Practices To Protect Technology Systems Contd
Technology Mediated Education Playbook Best Practices To Protect Technology Systems ContdThis slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Introducing Technology Mediated Education Playbook Best Practices To Protect Technology Systems Contd to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Device Management, Acceptable Usage Policies, Safe Usage Policies, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Protect Technology Systems Playbook For Teaching And Learning At Distance
Best Practices To Protect Technology Systems Playbook For Teaching And Learning At DistanceThis slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Introducing Best Practices To Protect Technology Systems Playbook For Teaching And Learning At Distance to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Device Management, Internet And Content Filtering, Program Requirements, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Protect Technology Systems Cont Distance Learning Playbook
Best Practices To Protect Technology Systems Cont Distance Learning PlaybookThis slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Increase audience engagement and knowledge by dispensing information using Best Practices To Protect Technology Systems Cont Distance Learning Playbook. This template helps you present information on two stages. You can also present information on Best Practices, Protect Technology, Student Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Protect Technology Digital Learning Playbook
Best Practices To Protect Technology Digital Learning PlaybookThis slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Introducing Best Practices To Protect Technology Digital Learning Playbook to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Content Filtering, Student Privacy, Regulations, Compliance, using this template. Grab it now to reap its full benefits.
-
 Digital Learning Playbook Best Practices To Protect Technology Systems
Digital Learning Playbook Best Practices To Protect Technology SystemsThis slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Increase audience engagement and knowledge by dispensing information using Digital Learning Playbook Best Practices To Protect Technology Systems. This template helps you present information on three stages. You can also present information on Device Management, Implement, Management, Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Anti Fraud Playbook Addressing The Practices To Protect
Anti Fraud Playbook Addressing The Practices To ProtectPurpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Introducing Anti Fraud Playbook Addressing The Practices To Protect to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Addressing The Practices To Protect Business Against Fraud, using this template. Grab it now to reap its full benefits.
-
 Various Practices To Protect Operational Technology System
Various Practices To Protect Operational Technology SystemMentioned slide outlines key practices that can be implemented by an organization within the premises to protect operational technology OT system. OT cybersecurity program, OT asset inventory and security awareness training are some of the major practices which will assist company to protect critical IT infrastructure. Introducing Various Practices To Protect Operational Technology System to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on OT Cybersecurity Program, OT Asset, Inventory Software, OT Security, Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Fraud Investigation And Response Playbook Addressing The Practices To Protect Business Against Fraud
Fraud Investigation And Response Playbook Addressing The Practices To Protect Business Against FraudPurpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Introducing Fraud Investigation And Response Playbook Addressing The Practices To Protect Business Against Fraud to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Business, Software, Information, using this template. Grab it now to reap its full benefits.
-
 Fraud Risk Management Guide Addressing The Practices To Protect Business Against Fraud
Fraud Risk Management Guide Addressing The Practices To Protect Business Against FraudPurpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Increase audience engagement and knowledge by dispensing information using Fraud Risk Management Guide Addressing The Practices To Protect Business Against Fraud. This template helps you present information on three stages. You can also present information on Addressing Practices, Protect Business using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Best Practices Cloud Data Protection
Cloud Security Best Practices Cloud Data ProtectionThis slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an outstanding presentation on the topic using this Cloud Security Best Practices Cloud Data Protection. Dispense information and present a thorough explanation of Cloud Protection Issues, Cloud Service, Infrastructure As A Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Fraud Prevention Playbook Addressing The Practices To Protect Business Against Fraud
Fraud Prevention Playbook Addressing The Practices To Protect Business Against FraudPurpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Introducing Fraud Prevention Playbook Addressing The Practices To Protect Business Against Fraud to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Business Email, Compromise Scams, Ransomware, using this template. Grab it now to reap its full benefits.
-
 Addressing The Practices To Protect Business Against Fraud Best Practices For Managing
Addressing The Practices To Protect Business Against Fraud Best Practices For ManagingPurpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Introducing Addressing The Practices To Protect Business Against Fraud Best Practices For Managing to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Business Email, Compromise Scams, Ransomware, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Protect Data In Cloud Infra Security
Best Practices To Protect Data In Cloud Infra SecurityThe following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users, etc. Increase audience engagement and knowledge by dispensing information using Best Practices To Protect Data In Cloud Infra Security. This template helps you present information on seven stages. You can also present information on Secure, Manage, Employee using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Evaluating Financial Practices In Firm Defense Plan To Protect Firm Assets
Evaluating Financial Practices In Firm Defense Plan To Protect Firm AssetsThe firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an outstanding presentation on the topic using this Evaluating Financial Practices In Firm Defense Plan To Protect Firm Assets. Dispense information and present a thorough explanation of Accepted Standards, Government Requirements, Understanding Of Finances using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improving Customer Engagement Data Security Best Practices To Protect Customer MKT SS V
Improving Customer Engagement Data Security Best Practices To Protect Customer MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Improving Customer Engagement Data Security Best Practices To Protect Customer MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Protect Technology Systems Cont One Pager Sample Example Document
Best Practices To Protect Technology Systems Cont One Pager Sample Example DocumentThis is a One Pager designed in Powerpoint titled Best Practices To Protect Technology Systems Cont One Pager Sample Example Document. It is crafted using high-quality visuals that can be readjusted in PowerPoint and Google Slides. This template comes in an editable format and is available in A4 size format for immediate download.
-
 Anti Fraud Playbook Addressing The Practices To Protect One Pager Sample Example Document
Anti Fraud Playbook Addressing The Practices To Protect One Pager Sample Example DocumentThis is a One Pager designed in Powerpoint titled Anti Fraud Playbook Addressing The Practices To Protect One Pager Sample Example Document. It is crafted using high-quality visuals that can be readjusted in PowerPoint and Google Slides. This template comes in an editable format and is available in A4 size format for immediate download.



