Powerpoint Templates and Google slides for Planning Vulnerability
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Vulnerability Assessment Plan Powerpoint Presentation Slides
Vulnerability Assessment Plan Powerpoint Presentation SlidesPresenting Vulnerability Assessment Plan Powerpoint Presentation Slides. Make modifications in the font color, font size, and font style of the slide as it is entirely customizable. Its compatibility with Google Slides makes it accessible at once. You can transform and save the slide in PDF and JPG formats as well. Get this high-quality slide to present it in front of thousands of people on a standard screen and widescreen.
-
 Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard
Application Security Implementation Plan Application Security Vulnerability Scanning DashboardThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard. Use it as a tool for discussion and navigation on Application Security Vulnerability, Scanning Dashboard, Monitor Vulnerabilities Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Data Breach Response Plan Fix Vulnerabilities
Data Breach Prevention And Mitigation Data Breach Response Plan Fix VulnerabilitiesThis slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Data Breach Response Plan Fix Vulnerabilities. Dispense information and present a thorough explanation of Collaborate With Forensics Experts, Review Network Segmentation, Communicate Transparently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities
Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Financial Transactions, Credentials Compromised, Cloud Network, Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks Vulnerabilities
Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cloud Network Compromised, Financial Transactions, Credentials Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Risk Register To Measure Cyber Attacks Vulnerabilities
Compressive Planning Guide Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Compressive Planning Guide Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cyber Attack Risk Vulnerabilities, Vulnerability Exploited, Occurrence And Control Recommended. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Assessing Risk And Potential Vulnerabilities In Business Data
Data Breach Response Plan Assessing Risk And Potential Vulnerabilities In Business DataThis slide discusses the risks and vulnerabilities assessment of organizational data. The different risk scenarios can be incompetent and malicious employees, catastrophic data loss, disruption of services, sensitive data exposure, reputation management, etc. Present the topic in a bit more detail with this Data Breach Response Plan Assessing Risk And Potential Vulnerabilities In Business Data. Use it as a tool for discussion and navigation on Incompetent And Malicious Employees, Catastrophic Data Loss, Reputation Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Implementation Fix Vulnerabilities
Data Breach Response Plan Implementation Fix VulnerabilitiesThis slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Implementation Fix Vulnerabilities. Dispense information and present a thorough explanation of Review Network Segmentation, Communicate Transparently, Collaborate With Forensics Experts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Responsibility Matrix For Fix Vulnerabilities Phase
Data Breach Response Plan Responsibility Matrix For Fix Vulnerabilities PhaseThis slide shows the matrix to assign multiple responsibilities to the different teams for the fix vulnerabilities phase of data breach response plan. The responsibilities include assess Service Providers access privileges, collaborate with forensic experts, etc. Present the topic in a bit more detail with this Data Breach Response Plan Responsibility Matrix For Fix Vulnerabilities Phase. Use it as a tool for discussion and navigation on Responsibilities, Customer Support Team, Review Network Segmentation, Fix Vulnerabilities Phase. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Penetration Testing Implementation Plan Vulnerability Scanning Stage Of Penetration Testing
Penetration Testing Implementation Plan Vulnerability Scanning Stage Of Penetration TestingThis slide highlights a checklist to scan vulnerabilities while doing penetration testing. The purpose of this slide is to showcase the components involved, such as finding network topology, identifying OS types of discovered hosts, and so on. Deliver an outstanding presentation on the topic using this Penetration Testing Implementation Plan Vulnerability Scanning Stage Of Penetration Testing. Dispense information and present a thorough explanation of Network Topology, Network Services, Potential Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability management system workforce diversity marketing communications planning cpb
Vulnerability management system workforce diversity marketing communications planning cpbPresenting this set of slides with name - Vulnerability Management System Workforce Diversity Marketing Communications Planning Cpb. This is an editable four stages graphic that deals with topics like Vulnerability Management System, Workforce Diversity, Marketing Communications Planning to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Vulnerability management whitepaper define and document the plan ppt styles inspiration
Vulnerability management whitepaper define and document the plan ppt styles inspirationIncrease audience engagement and knowledge by dispensing information using Vulnerability Management Whitepaper Define And Document The Plan Ppt Styles Inspiration. This template helps you present information on five stages. You can also present information on Build Vulnerability Management Team, Coordinate Risk Management, Define Standard Remediation Timelines, Define Vulnerabilities Should Documented, Define Periodic Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability management whitepaper develop a plan revision process
Vulnerability management whitepaper develop a plan revision processIncrease audience engagement and knowledge by dispensing information using Vulnerability Management Whitepaper Develop A Plan Revision Process. This template helps you present information on three stages. You can also present information on Review Changes, Update Toolset Necessary, Update Sources, Vulnerability Information, Primary Source Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Contingency plan for cyber managing critical threat vulnerabilities and security threats
Contingency plan for cyber managing critical threat vulnerabilities and security threatsThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Introducing Contingency Plan For Cyber Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Contingency Solutions, Contingency Considerations, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management develop a plan revision process
Enterprise vulnerability management develop a plan revision processIntroducing Enterprise Vulnerability Management Develop A Plan Revision Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Review The Changes, Vulnerability Information, Update Toolset If Necessary, using this template. Grab it now to reap its full benefits.
-
 Enterprise vulnerability management overview plan
Enterprise vulnerability management overview planIntroducing Enterprise Vulnerability Management Overview Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Management, Vulnerability Information, Definition Of Roles And Responsibilities, using this template. Grab it now to reap its full benefits.
-
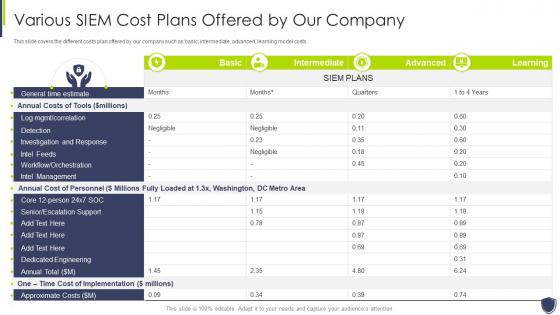 Improve it security with vulnerability management various siem cost plans offered company
Improve it security with vulnerability management various siem cost plans offered companyThis slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Present the topic in a bit more detail with this Improve It Security With Vulnerability Management Various Siem Cost Plans Offered Company. Use it as a tool for discussion and navigation on Various SIEM Cost Plans Offered By Our Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Exhaustive Contingency Plan With Impact And Vulnerabilities Project Management Bundle
Exhaustive Contingency Plan With Impact And Vulnerabilities Project Management BundleThe following slide displays the contingency plan of the organization for various risks and hazards that are associated to the project, the provided highlights the nature of hazard, the further actions and the responsible team member for plan execution. Deliver an outstanding presentation on the topic using this Exhaustive Contingency Plan With Impact And Vulnerabilities Project Management Bundle. Dispense information and present a thorough explanation of Transportation System, Raw Materials, Personnel, Facility, Utilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Management Action Plan Vulnerability Administration At Workplace
Threat Management Action Plan Vulnerability Administration At WorkplaceThe threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver an outstanding presentation on the topic using this Threat Management Action Plan Vulnerability Administration At Workplace. Dispense information and present a thorough explanation of Threat Management Action Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Contingency Plan For Cyber Threat Handling
Vulnerability Administration At Workplace Contingency Plan For Cyber Threat HandlingThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Contingency Plan For Cyber Threat Handling. Dispense information and present a thorough explanation of Contingency Plan For Cyber Threat Handling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Threat Management Action Plan
Vulnerability Administration At Workplace Threat Management Action Planthem. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Threat Management Action Plan. Use it as a tool for discussion and navigation on Threat Management Action Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise vulnerability management define and document the plan
Enterprise vulnerability management define and document the planIntroducing Enterprise Vulnerability Management Define And Document The Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Coordinate With Risk Management, Standard Remediation Timelines, Vulnerabilities Should, using this template. Grab it now to reap its full benefits.
-
 Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security
Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information SecurityThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Assessment, Vulnerability, Associated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information Security
Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information SecurityThis slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description Present the topic in a bit more detail with this Vulnerability Rating For Risk Identification Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Identification, Information, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan
Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Vulnerability Severity, Threat Source, Risk Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat
Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And ThreatThis slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat. Dispense information and present a thorough explanation of Assessment, Vulnerability, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Planning Vulnerability Management Program Icon
Planning Vulnerability Management Program IconIntroducing our premium set of slides with Planning Vulnerability Management Program Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning Vulnerability, Management Program Icon. So download instantly and tailor it with your information.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan
Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity PlanThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Risk Assessment Matrix, Vulnerability Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan
Threat Identification And Vulnerability Assessment Formulating Cybersecurity PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Vulnerability Severity, Threat Source, Likelihood. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Rating For Risk Identification Formulating Cybersecurity Plan
Vulnerability Rating For Risk Identification Formulating Cybersecurity PlanThis slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Introducing Vulnerability Rating For Risk Identification Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Score, Risk Identification, using this template. Grab it now to reap its full benefits.
-
 Backup Methods For Cyber Defense Planning Cybersecurity Incident And Vulnerability
Backup Methods For Cyber Defense Planning Cybersecurity Incident And VulnerabilityFollowing slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental. Increase audience engagement and knowledge by dispensing information using Backup Methods For Cyber Defense Planning Cybersecurity Incident And Vulnerability. This template helps you present information on three stages. You can also present information on Backup Methods, Backup Options, Incremental using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Communication Plan For Effective Incident Management Cybersecurity Incident And Vulnerability
Communication Plan For Effective Incident Management Cybersecurity Incident And VulnerabilityThis slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person. Introducing Communication Plan For Effective Incident Management Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Delivery Method, Incident Information, Team Meetings, using this template. Grab it now to reap its full benefits.
-
 Food Fraud Mitigation Plan Development To Remove Vulnerability
Food Fraud Mitigation Plan Development To Remove VulnerabilityThis slide provide information about procedure to formulate food fraud mitigation plan to remove vulnerability. It includes elements such as pre-screening, vulnerability assessment, impact assessment, overall risk assessment etc. Presenting our set of slides with Food Fraud Mitigation Plan Development To Remove Vulnerability. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Pre Screening, Vulnerability Assessment, Impact Assessment, Overall Risk Assessment.
-
 Food Fraud Vulnerability Assessment With Mitigation Plan
Food Fraud Vulnerability Assessment With Mitigation PlanThis slide illustrate food fraud vulnerability assessment mitigation plan to remove frauds occurring in food industry. It includes elements such as mitigation plan, potential vulnerability, mention trade mark etc. Introducing our Food Fraud Vulnerability Assessment With Mitigation Plan set of slides. The topics discussed in these slides are Potential Vulnerability, Mitigation Plan, Ingredient Bought. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Food Ingredient Fraud Vulnerability Mitigation Plan
Food Ingredient Fraud Vulnerability Mitigation PlanThis slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments. Presenting our well structured Food Ingredient Fraud Vulnerability Mitigation Plan. The topics discussed in this slide are Facility Security, Building Security, Security Assessments. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Vulnerability management plan discovery scan report
Vulnerability management plan discovery scan reportPresenting this set of slides with name - Vulnerability Management Plan Discovery Scan Report. This is a five stage process. The stages in this process are Vulnerability Management, Risk Management, Vulnerability Planning.
-
 Talent management marketing channels benefit plan vulnerability management cpb
Talent management marketing channels benefit plan vulnerability management cpbPresenting this set of slides with name - Talent Management Marketing Channels Benefit Plan Vulnerability Management Cpb. This is an editable five stages graphic that deals with topics like Talent Management, Marketing Channels, Benefit Plan, Vulnerability Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Arrow action plan showing review assess vulnerability risk develop implement and monitor
Arrow action plan showing review assess vulnerability risk develop implement and monitorPresenting this set of slides with name - Arrow Action Plan Showing Review Assess Vulnerability Risk Develop Implement And Monitor. This is a six stage process. The stages in this process are Road Sig Arrow Action Plan, Arrow Action Strategy, Arrow Action Approachns Powerpoint, Traffic Signs, Traffic Symbol.
-
 Succession planning backup summary simple format position vulnerability ppt presentation skills
Succession planning backup summary simple format position vulnerability ppt presentation skillsPresenting this set of slides with name Succession Planning Backup Summary Simple Format Position Vulnerability Ppt Presentation Skills. The topics discussed in these slides are Table, Business, Management, Planning, Strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Vulnerability management plan template ppt powerpoint presentation file graphics cpb
Vulnerability management plan template ppt powerpoint presentation file graphics cpbPresenting this set of slides with name Vulnerability Management Plan Template Ppt Powerpoint Presentation File Graphics Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Vulnerability Management Plan Template to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Vulnerable sectors and economies covid 19 introduction response plan economic effect landscapes
Vulnerable sectors and economies covid 19 introduction response plan economic effect landscapesThis slide provides details about various sectors and economies that are adversely impacted due to COVID 19 outbreak. Increase audience engagement and knowledge by dispensing information using Vulnerable Sectors And Economies Covid 19 Introduction Response Plan Economic Effect Landscapes. This template helps you present information on Six stages. You can also present information on Global, Social, Demand using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.



