Powerpoint Templates and Google slides for Phishing Assault
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V
Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V This template helps you present information on Three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now
-
 Triage Cyber Security Dashboard To Response Phishing Threats
Triage Cyber Security Dashboard To Response Phishing ThreatsThis slide represents triage cyber security dashboard to response phishing threats which assists to analyse and response to phishing attacks. It includes key components such as active clusters, processed reports, etc Presenting our well structured Triage Cyber Security Dashboard To Response Phishing Threats The topics discussed in this slide are Active Clusters, Categorized Reports. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS V
Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS V This template helps you present information on Seven stages. You can also present information on Steals Data From User System, Obtains Information From System using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Methods To Identify Crypto Phishing Scams BCT SS V
Cyber Threats In Blockchain Methods To Identify Crypto Phishing Scams BCT SS VThe following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Methods To Identify Crypto Phishing Scams BCT SS V This template helps you present information on Five stages. You can also present information on Copycatting, Spelling, Ambiguous Links using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS V
Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Opportunities, Fake Website, Data Breach using this template. Grab it now to reap its full benefits.
-
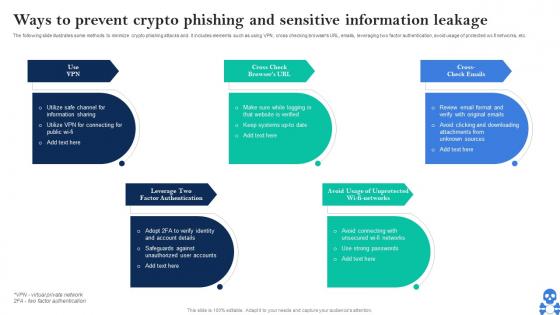 Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V
Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. it includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Use VPN, Factor Authentication, Avoid Usage Of Unprotected using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it phishing cyber terrorism tool ppt slides graphics
Cyberterrorism it phishing cyber terrorism tool ppt slides graphicsThis slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Introducing Cyberterrorism IT Phishing Cyber Terrorism Tool Ppt Slides Graphics to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Obtain Sensitive Information, Credit Card Details, Business, Consumer Confidence, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it phishing techniques misused for cyber assault
Cyberterrorism it phishing techniques misused for cyber assaultThis slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Phishing Techniques Misused For Cyber Assault. This template helps you present information on four stages. You can also present information on Spear Phishing, Smishing And Vishing, Whaling, Email Phishing Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Cyber Terrorism Tool Cyber Terrorism Attacks
Phishing Cyber Terrorism Tool Cyber Terrorism AttacksThis slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Increase audience engagement and knowledge by dispensing information using Phishing Cyber Terrorism Tool Cyber Terrorism Attacks. This template helps you present information on five stages. You can also present information on Obtain, Sensitive, Information, Trustworthy, Convinces using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Techniques Misused For Cyber Assault Cyber Terrorism Attacks
Phishing Techniques Misused For Cyber Assault Cyber Terrorism AttacksThis slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Introducing Phishing Techniques Misused For Cyber Assault Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Techniques Misused For Cyber Assault, using this template. Grab it now to reap its full benefits.
-
 Insider Threat Icon For Financial Information Phishing
Insider Threat Icon For Financial Information PhishingIntroducing our premium set of slides with Insider Threat Icon For Financial Information Phishing. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Insider Threat Icon, Financial Information Phishing. So download instantly and tailor it with your information.
-
 Cyber Security Threats Phishing In Powerpoint And Google Slides Cpb
Cyber Security Threats Phishing In Powerpoint And Google Slides CpbPresenting our Cyber Security Threats Phishing In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Threats Phishing This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Threats phishing ppt powerpoint presentation styles samples cpb
Threats phishing ppt powerpoint presentation styles samples cpbPresenting this set of slides with name Threats Phishing Ppt Powerpoint Presentation Styles Samples Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Threats Phishing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.



