Powerpoint Templates and Google slides for Networking Approaches
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Network Traffic Approaches Classification Process Through Description
Network Traffic Approaches Classification Process Through DescriptionDeliver a credible and compelling presentation by deploying this Network Traffic Approaches Classification Process Through Description. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The thirteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Network Traffic Approaches Classification Process Through Description PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Storage Area Network San Configurations Approaches For Storage Virtualization Systems
Storage Area Network San Configurations Approaches For Storage Virtualization SystemsThis Slide Outlines The Methods For Storage Virtualization System Configurations. The Purpose Of This Slide Is To Showcase The Main Configuration Approaches Of Storage Virtualization Systems, Such As The In-Band Approach And The Out-Band Approach. Deliver An Outstanding Presentation On The Topic Using This Storage Area Network San Configurations Approaches For Storage Virtualization Systems. Dispense Information And Present A Thorough Explanation Of Configurations, Approaches, Virtualization Using The Slides Given. This Template Can Be Altered And Personalized To Fit Your Needs. It Is Also Available For Immediate Download. So Grab It Now.
-
 Storage Area Network San Hardware Design Approaches In Hyper Converged Infrastructure
Storage Area Network San Hardware Design Approaches In Hyper Converged InfrastructureThis Slide Outlines The Hardware Architecture Approaches Of Hyper-Converged Infrastructure. The Purpose Of This Slide Is To Give An Overview Of Both Integrated HCI And Disaggregated HCI Approaches Used In Hardware-Based Hyper-Converged Infrastructure HCI. Present The Topic In A Bit More Detail With This Storage Area Network San Hardware Design Approaches In Hyper Converged Infrastructure. Use It As A Tool For Discussion And Navigation On Infrastructure, Approaches, Hardware. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Neural Network Approach Deployed By NLP Y Comprehensive Tutorial About AI SS V
Neural Network Approach Deployed By NLP Y Comprehensive Tutorial About AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Increase audience engagement and knowledge by dispensing information using Neural Network Approach Deployed By NLP Y Comprehensive Tutorial About AI SS V. This template helps you present information on three stages. You can also present information on Recurrent Neural Networks, Artificial Neural Networks, Convolutional Neural using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Neural Network Approach Deployed Power Of Natural Language Processing AI SS V
Neural Network Approach Deployed Power Of Natural Language Processing AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks convolutional neural networks. Introducing Neural Network Approach Deployed Power Of Natural Language Processing AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate entice your audience. Dispence information on Data Manner, Network Comprises, Organized Interconnected, using this template. Grab it now to reap its full benefits.
-
 Neural Network Approach Deployed Role Of NLP In Text Summarization And Generation AI SS V
Neural Network Approach Deployed Role Of NLP In Text Summarization And Generation AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Increase audience engagement and knowledge by dispensing information using Neural Network Approach Deployed Role Of NLP In Text Summarization And Generation AI SS V. This template helps you present information on three stages. You can also present information on Recurrent Neural Networks, Artificial Neural Networks, Convolutional Neural Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Neural Network Approach Deployed Zero To NLP Introduction To Natural Language Processing AI SS V
Neural Network Approach Deployed Zero To NLP Introduction To Natural Language Processing AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Introducing Neural Network Approach Deployed Zero To NLP Introduction To Natural Language Processing AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Recurrent Neural Networks, Artificial Neural Networks, Convolutional Neural Networks, using this template. Grab it now to reap its full benefits.
-
 Approaches To Implement Zero Trust Network Access Cloud Security Model
Approaches To Implement Zero Trust Network Access Cloud Security ModelThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenges With Traditional Network Security Approaches Cloud Security Model
Challenges With Traditional Network Security Approaches Cloud Security ModelThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Deliver an outstanding presentation on the topic using this Challenges With Traditional Network Security Approaches Cloud Security Model. Dispense information and present a thorough explanation of Approaches, Security, Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Neural Network Approach Deployed Gettings Started With Natural Language AI SS V
Neural Network Approach Deployed Gettings Started With Natural Language AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Introducing Neural Network Approach Deployed Gettings Started With Natural Language AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Networks, Artificial, Comprises, using this template. Grab it now to reap its full benefits.
-
 Sase Security Approaches To Implement Zero Trust Network Access
Sase Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Sase Security Approaches To Implement Zero Trust Network Access. Dispense information and present a thorough explanation of Approaches, Organizations, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Challenges With Traditional Network Security Approaches
Sase Security Challenges With Traditional Network Security ApproachesThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Deliver an outstanding presentation on the topic using this Sase Security Challenges With Traditional Network Security Approaches. Dispense information and present a thorough explanation of Cyberthreat Risks, Disjointed Management, Poor User Experience using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase
Approaches To Implement Zero Trust Network Access Secure Access Service Edge SaseThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Approaches, Endpoint Initiated, Service Initiated using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenges With Traditional Network Security Approaches Secure Access Service Edge Sase
Challenges With Traditional Network Security Approaches Secure Access Service Edge SaseThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present the topic in a bit more detail with this Challenges With Traditional Network Security Approaches Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Approaches, Demonstrate, Conventional. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Natural Language Processing Neural Network Approach Deployed By NLP Technology AI SS V
Natural Language Processing Neural Network Approach Deployed By NLP Technology AI SS VThis slide provides information regarding neural-network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Introducing Natural Language Processing Neural Network Approach Deployed By NLP Technology AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Recurrent Neural Networks, Artificial Neural Networks, Convolutional Neural Networks, using this template. Grab it now to reap its full benefits.
-
 Neural Network Approach Deployed By NLP Technology Decoding Natural Language AI SS V
Neural Network Approach Deployed By NLP Technology Decoding Natural Language AI SS VThis slide provides information regarding neural-network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Introducing Neural Network Approach Deployed By NLP Technology Decoding Natural Language AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Recurrent Neural Networks, Artificial Neural Networks using this template. Grab it now to reap its full benefits.
-
 Challenges With Traditional Network Security Approaches SASE Network Security
Challenges With Traditional Network Security Approaches SASE Network SecurityThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present the topic in a bit more detail with this Challenges With Traditional Network Security Approaches SASE Network Security. Use it as a tool for discussion and navigation on Security, Traditional, Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Approaches To Implement Zero Trust Network Access
SASE Network Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero trust network access. It also includes how users access business services and applications in both approaches. Increase audience engagement and knowledge by dispensing information using SASE Network Security Approaches To Implement Zero Trust Network Access. This template helps you present information on two stages. You can also present information on Program, Environment, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Three Approaches Of Network Security Risk Management
Three Approaches Of Network Security Risk ManagementThis slide showcases the three approaches of network security risk management which helps an organization to identify and assess potential emerging threats . It include details such as develop detailed network diagram, plan for attacks. Introducing our premium set of slides with Three Approaches Of Network Security Risk Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Develop Detailed Network Diagram, Analyze Network Risks, Plan Attacks. So download instantly and tailor it with your information.
-
 Neural Network Approach Deployed By NLP Technology What Is NLP And How It Works AI SS V
Neural Network Approach Deployed By NLP Technology What Is NLP And How It Works AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Present the topic in a bit more detail with this Neural Network Approach Deployed By NLP Technology What Is NLP And How It Works AI SS V Use it as a tool for discussion and navigation on Performing Calculations, Desired Outcomes, Interconnected Nodes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Neural Network Approach Deployed By Technologies And Associated With NLP AI SS
Neural Network Approach Deployed By Technologies And Associated With NLP AI SSThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Introducing Neural Network Approach Deployed By Technologies And Associated With NLP AI SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Networks, Artificial, Convolutional, using this template. Grab it now to reap its full benefits.
-
 Natural Language Neural Network Approach Deployed By NLP Technology AI SS V
Natural Language Neural Network Approach Deployed By NLP Technology AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Introducing Natural Language Processing Natural Language Neural Network Approach Deployed By NLP Technology AI SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Recurrent Neural Networks, Artificial Neural Networks, Convolutional Neural Networks, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Approaches To Implement Zero Trust Network Access
SD WAN Model Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Increase audience engagement and knowledge by dispensing information using SD WAN Model Approaches To Implement Zero Trust Network Access. This template helps you present information on one stages. You can also present information on Zero Trust Network Access, Service Initiated Approach, Business Services And Applications, Cloud Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Challenges With Traditional Network Security Approaches
SD WAN Model Challenges With Traditional Network Security ApproachesThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Challenges With Traditional Network Security Approaches. Dispense information and present a thorough explanation of Challenges With Traditional Network, Security Approaches, Including Disjoint Management, Workload, Slower Cloud Adoption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Neural Network Approach Deployed Explore Natural Language Processing NLP AI SS V
Neural Network Approach Deployed Explore Natural Language Processing NLP AI SS VThis slide provides information regarding neural network NLP methodology, in which each node manages calculations to attain desired outcomes. Various types of neural networks include recurrent neural networks, artificial neural networks and convolutional neural networks. Introducing Neural Network Approach Deployed Explore Natural Language Processing NLP AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Networks, Artificial, Convolutional, using this template. Grab it now to reap its full benefits.
-
 Sase Model Approaches To Implement Zero Trust Network Access
Sase Model Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Introducing Sase Model Approaches To Implement Zero Trust Network Access to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Service Initiated, Endpoint Initiated, using this template. Grab it now to reap its full benefits.
-
 Sase Model Challenges With Traditional Network Security Approaches
Sase Model Challenges With Traditional Network Security ApproachesThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present the topic in a bit more detail with this Sase Model Challenges With Traditional Network Security Approaches. Use it as a tool for discussion and navigation on Disjointed Management, Workload, Slower Cloud Adoption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Four Step Approach To Ensure Network Optimization
Four Step Approach To Ensure Network OptimizationThis slide shows various tactics to optimize network performance. The purpose of this slide is to help businesses in improving network processes by eliminating risks of human errors. It covers strategies such determining critical factors, ensuring regular monitoring, conducting root cause analysis, etc. Presenting our set of slides with Four Step Approach To Ensure Network Optimization. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Conduct, Network.
-
 As A Service Deployment Approach Of ZTNA Architecture Identity Defined Networking
As A Service Deployment Approach Of ZTNA Architecture Identity Defined NetworkingThis slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Present the topic in a bit more detail with this As A Service Deployment Approach Of ZTNA Architecture Identity Defined Networking Use it as a tool for discussion and navigation on Disadvantages, Service Architecture, Advantages This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Client Based Approach Of ZTNA Architecture Identity Defined Networking
Client Based Approach Of ZTNA Architecture Identity Defined NetworkingThis slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Present the topic in a bit more detail with this Client Based Approach Of ZTNA Architecture Identity Defined Networking Use it as a tool for discussion and navigation on Overview, Architecture, Connection Process This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Other ZTNA Architecture Deployment Approaches Identity Defined Networking
Other ZTNA Architecture Deployment Approaches Identity Defined NetworkingThis slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Introducing Other ZTNA Architecture Deployment Approaches Identity Defined Networking to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Enhanced Identity Governance, Micro Segmentation, Software Defined using this template. Grab it now to reap its full benefits.
-
 Pro Browser Based Approach Of ZTNA Architecture Identity Defined Networking
Pro Browser Based Approach Of ZTNA Architecture Identity Defined NetworkingThis slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Deliver an outstanding presentation on the topic using this Pro Browser Based Approach Of ZTNA Architecture Identity Defined Networking Dispense information and present a thorough explanation of Internet Browser, Unmanaged Devices, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Self Hosted Deployment Approach Of ZTNA Architecture Identity Defined Networking
Self Hosted Deployment Approach Of ZTNA Architecture Identity Defined NetworkingThis slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Deliver an outstanding presentation on the topic using this Self Hosted Deployment Approach Of ZTNA Architecture Identity Defined Networking Dispense information and present a thorough explanation of Benefits, Drawbacks, Organizations, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 List Of Private Blockchain Network Platforms Comprehensive Approach To Privacy BCT SS
List Of Private Blockchain Network Platforms Comprehensive Approach To Privacy BCT SSThis slide covers list of various private blockchain network technologies for multiple applications including platforms such as enterprise Ethereum, Hyperledger fabric, corda, ripple and quorum along with description, key components and implementation cost. Present the topic in a bit more detail with this List Of Private Blockchain Network Platforms Comprehensive Approach To Privacy BCT SS. Use it as a tool for discussion and navigation on Private Blockchain, Smart Contract Functionality, Network Architecture And Consensus Mechanism. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Private Blockchain Networks Comprehensive Approach To Privacy BCT SS
Overview Of Private Blockchain Networks Comprehensive Approach To Privacy BCT SSThis slide covers brief summary of private blockchain networks including benefits such as preventing fraud by using identity to confirm membership, higher performance due to lesser nodes, etc along with characteristics. Present the topic in a bit more detail with this Overview Of Private Blockchain Networks Comprehensive Approach To Privacy BCT SS. Use it as a tool for discussion and navigation on About Private Blockchain Networks, Benefits Of Private Blockchain Network, Characteristics Of Private Blockchain. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Private Blockchain Network Process Flow Comprehensive Approach To Privacy BCT SS
Private Blockchain Network Process Flow Comprehensive Approach To Privacy BCT SSThis slide covers parties involved and workflow of private blockchain network including steps from creating transaction or block by user, distributing and validating transaction through cryptographic hashing, etc. Deliver an outstanding presentation on the topic using this Private Blockchain Network Process Flow Comprehensive Approach To Privacy BCT SS. Dispense information and present a thorough explanation of Crypto Hashing, Distributed Databases, Trustless Peering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Use Cases Of Private Blockchain Network Comprehensive Approach To Privacy BCT SS
Use Cases Of Private Blockchain Network Comprehensive Approach To Privacy BCT SSThis slide covers applications of public blockchain network platform. It includes use cases such as insurance, banking and finance, healthcare, supply chain etc. for maintaining privacy in deploying blockchain technology. Increase audience engagement and knowledge by dispensing information using Use Cases Of Private Blockchain Network Comprehensive Approach To Privacy BCT SS. This template helps you present information on five stages. You can also present information on Insurance, Banking And Finance, Healthcare using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Penetration Testing Approaches Why Do We Perform Network Penetration Testing
Penetration Testing Approaches Why Do We Perform Network Penetration TestingThis slide represents the reasons to perform network service penetration testing. The purpose of this slide is to showcase the network-based attacks such as firewall misconfiguration and firewall bypass, router attacks, SSH attacks and so on. Present the topic in a bit more detail with this Penetration Testing Approaches Why Do We Perform Network Penetration Testing. Use it as a tool for discussion and navigation on Router Attacks, DNS Level Attacks, SSH Attacks, Proxy Server Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Approaches To Implement StyleGAN Inversion Generative Adversarial Network AI SS
Approaches To Implement StyleGAN Inversion Generative Adversarial Network AI SSThis slide provides information regarding various methods to deploy StyleGAN inversion in terms of optimization-based, learning-based or hybrid. Introducing Approaches To Implement StyleGAN Inversion Generative Adversarial Network AI SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Optimization-Based, Learning-Based, Hybrid, using this template. Grab it now to reap its full benefits.
-
 Generative Adversarial Network Variant Approach Generative Adversarial Network AI SS
Generative Adversarial Network Variant Approach Generative Adversarial Network AI SSThis slide provides information regarding StyleGAN inversion technique that helps in inverting assigned images to latent space to enable semantic editing with ease. Present the topic in a bit more detail with this Generative Adversarial Network Variant Approach Generative Adversarial Network AI SS. Use it as a tool for discussion and navigation on Reconstruction And Manipulation, Sampling And Generation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Penetration Testing Approaches And Type Of Penetration Testing Network Service
Penetration Testing Approaches And Type Of Penetration Testing Network ServiceThis slide highlights the network service penetration testing, which is the type of penetration testing. The purpose of this slide is to showcase the different components, such as the primary purpose, the scope of assessment, and proactive defence. Present the topic in a bit more detail with this Penetration Testing Approaches And Type Of Penetration Testing Network Service. Use it as a tool for discussion and navigation on Primary Purpose, Scope Of Assessment, Proactive Defence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sales Forecasting Models And Methods Approaching Sales Forecasting Using Neural Network SA SS
Sales Forecasting Models And Methods Approaching Sales Forecasting Using Neural Network SA SSPurpose of this slide is to use neural network for projecting company sales by analyzing historical data and applying trained algorithms of data science. Deliver an outstanding presentation on the topic using this Sales Forecasting Models And Methods Approaching Sales Forecasting Using Neural Network SA SS. Dispense information and present a thorough explanation of Perceptrons Determining Sales Pattern, Approaching Sales Forecasting, Neural Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Which Social Network Have Most Engaged Audience Key Approaches To Increase Client
Which Social Network Have Most Engaged Audience Key Approaches To Increase ClientThis slide shows the graphical representation of customer engagement by social media sites such as snapchat, Instagram, twitter, etc. with total minutes and percentage reach of digital population. Deliver an outstanding presentation on the topic using this Which Social Network Have Most Engaged Audience Key Approaches To Increase Client. Dispense information and present a thorough explanation of Social Media, Digital Population, Engaged Audience using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 5G Emerging As Network Of Opportunity Proactive Approach For 5G Deployment
5G Emerging As Network Of Opportunity Proactive Approach For 5G DeploymentThis slide provides details regarding 5G as next generation mobile technology and emerging as network of opportunity catering various need of users, telecom operators, etc. Present the topic in a bit more detail with this 5G Emerging As Network Of Opportunity Proactive Approach For 5G Deployment. Use it as a tool for discussion and navigation on Opportunity, Mobile Technology, Growth. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing 5G Spectrum Network Coverage Proactive Approach For 5G Deployment
Addressing 5G Spectrum Network Coverage Proactive Approach For 5G DeploymentThis slide provides details regarding 5G spectrum network coverage including hotspots, urban coverage and rural coverage. Deliver an outstanding presentation on the topic using this Addressing 5G Spectrum Network Coverage Proactive Approach For 5G Deployment. Dispense information and present a thorough explanation of Hotspots, Urban, Rural using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Vulnerabilities Assessment Approach
Network Security Vulnerabilities Assessment ApproachThis slide illustrates network security vulnerabilities assessment results that help the organization to secure network security loop holes to mitigate vulnerabilities. It key components are unpatched security, patched security and total number of vulnerabilities. Introducing our Network Security Vulnerabilities Assessment Approach set of slides. The topics discussed in these slides are Sion And Configuration. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SDN Development Approaches Dashboard For Software Defined Networking SDN
SDN Development Approaches Dashboard For Software Defined Networking SDNThis slide depicts the dashboard for the software defined network by covering details of bandwidth administrator, traffic quality, active flows, development tools, completed tasks, wide area network bandwidth, and G drive. Present the topic in a bit more detail with this SDN Development Approaches Dashboard For Software Defined Networking SDN. Use it as a tool for discussion and navigation on Software, Defined, Networking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Product and services networking platform business valuation creation approach
Product and services networking platform business valuation creation approachThis slide covers the value creation approach of a platform business which focusses on demand or supply of the business and strategies involved Present the topic in a bit more detail with this Product And Services Networking Platform Business Valuation Creation Approach Use it as a tool for discussion and navigation on Stimulate Incremental Demand, Look For Underserved Networks, Create A New Supply Category This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Deployment Models Associated To 5G Network Proactive Approach For 5G Deployment
Various Deployment Models Associated To 5G Network Proactive Approach For 5G DeploymentThis slide provides details regarding 5G deployment models such as Non Standalone 5G deployment model , Standalone 5G deployment model. Deliver an outstanding presentation on the topic using this Value Enabler 4 Network Slicing And Its Importance Proactive Approach For 5G Deployment. Dispense information and present a thorough explanation of Deployment Models, 5G Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ways To Optimize 5G Network Energy Efficiency Proactive Approach For 5G Deployment
Ways To Optimize 5G Network Energy Efficiency Proactive Approach For 5G DeploymentThis slide provides details regarding various ways to optimize 5G network energy efficiency by utilizing alternate energy sources and network load optimization. Present the topic in a bit more detail with this Various Deployment Models Associated To 5G Network Proactive Approach For 5G Deployment. Use it as a tool for discussion and navigation on Network Load Optimization, Consumption Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Networking Approaches In Powerpoint And Google Slides Cpb
Networking Approaches In Powerpoint And Google Slides CpbPresenting Networking Approaches In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase two stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Networking Approaches. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
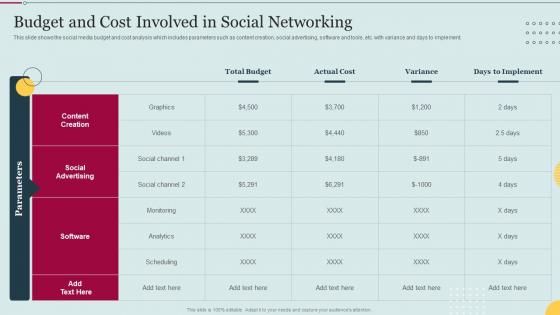 Budget And Cost Involved In Social Networking E Marketing Approaches To Increase
Budget And Cost Involved In Social Networking E Marketing Approaches To IncreaseThis slide shows the social media budget and cost analysis which includes parameters such as content creation, social advertising, software and tools, etc. with variance and days to implement. Deliver an outstanding presentation on the topic using this Budget And Cost Involved In Social Networking E Marketing Approaches To Increase. Dispense information and present a thorough explanation of Social, Networking, Involved using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Content Posting Calendar Across Social Media Networks E Marketing Approaches To Increase
Content Posting Calendar Across Social Media Networks E Marketing Approaches To IncreaseThis slide focuses on social media calendar for posting content across different platforms such as post link to open blog content, share promotional post, post reminders and recommendations, etc. Present the topic in a bit more detail with this Content Posting Calendar Across Social Media Networks E Marketing Approaches To Increase. Use it as a tool for discussion and navigation on Recommendations, Engagement, Promotional. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Different Network Ownership Approaches Associated Deployment Of 5g Wireless System
Addressing Different Network Ownership Approaches Associated Deployment Of 5g Wireless SystemThis slide provides details regarding network ownership approaches associated to 5G networks such as infrastructure sharing, neutral host, aerial network, private 5G network and bring your own small cell. Deliver an outstanding presentation on the topic using this Addressing Different Network Ownership Approaches Associated Deployment Of 5g Wireless System. Dispense information and present a thorough explanation of Ownership, Approaches, Associated using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Different Network Ownership Proactive Approach For 5G Deployment
Addressing Different Network Ownership Proactive Approach For 5G DeploymentThis slide provides details regarding network ownership approaches associated to 5G networks such as infrastructure sharing, neutral host, aerial network, private 5G network and bring your own small cell. Introducing Addressing Different Network Ownership Proactive Approach For 5G Deployment to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure Sharing, Neutral Host, Aerial Network, using this template. Grab it now to reap its full benefits.
-
 Addressing Network Deployment Regulations Proactive Approach For 5G Deployment
Addressing Network Deployment Regulations Proactive Approach For 5G DeploymentThis slide provides details regarding network deployment regulations of 5G addressing key consideration for policymakers. Introducing Addressing Network Deployment Regulations Proactive Approach For 5G Deployment to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Digital Objective, Network Sharing, Planning Processes, using this template. Grab it now to reap its full benefits.
-
 Determine 5G Era Network Flexibility Proactive Approach For 5G Deployment
Determine 5G Era Network Flexibility Proactive Approach For 5G DeploymentThis slide provides details regarding 5G era network flexibility in terms of NFV SDN and cloud RAN in order to cater customized services for major clients. Increase audience engagement and knowledge by dispensing information using Determine 5G Era Network Flexibility Proactive Approach For 5G Deployment. This template helps you present information on two stages. You can also present information on Cost Reduction, Location, Network Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine 5G Network Equipment Sourcing Proactive Approach For 5G Deployment
Determine 5G Network Equipment Sourcing Proactive Approach For 5G DeploymentThis slide provides details regarding 5G network equipment sourcing by operators such as open source or mobile operators and system integrators. Introducing Determine 5G Network Equipment Sourcing Proactive Approach For 5G Deployment to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Operators, System Integrators, Operation And Troubleshooting , using this template. Grab it now to reap its full benefits.
-
 Determine Network Capacity Drivers Spectral Proactive Approach For 5G Deployment
Determine Network Capacity Drivers Spectral Proactive Approach For 5G DeploymentThis slide provides details regarding network capacity drivers such as spectral efficiency and spectral capacity. Introducing Determine Network Capacity Drivers Spectral Proactive Approach For 5G Deployment to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Spectral Efficiency, Spectral Capacity, Network Capacity Drivers, using this template. Grab it now to reap its full benefits.
-
 Discover Unique Features Heterogeneous Networks With 5G Proactive Approach For 5G Deployment
Discover Unique Features Heterogeneous Networks With 5G Proactive Approach For 5G DeploymentThis slide provides details regarding unique features of 5G in terms of heterogeneous networks at premises, city and automobile through flexible framework to cater users coverage requirements. Present the topic in a bit more detail with this Discover Unique Features Heterogeneous Networks With 5G Proactive Approach For 5G Deployment. Use it as a tool for discussion and navigation on Customers Capacity, Cloud Radio Access Network, Networks Function Virtualization. This template is free to edit as deemed fit for your organization. Therefore download it now.




