Powerpoint Templates and Google slides for Monitor Safeguards
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SS
Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding monitoring of risk reduction outcomes for successful data loss prevention execution. It includes tracking of data loss likelihood across platforms such as web, email, etc.Deliver an outstanding presentation on the topic using this Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Marker Legend, Goals, Data Loss Likelihood using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SS
Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SSThis slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. Present the topic in a bit more detail with this Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Vulnerability Scanning, Auditing Reporting, Anomaly Detection . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
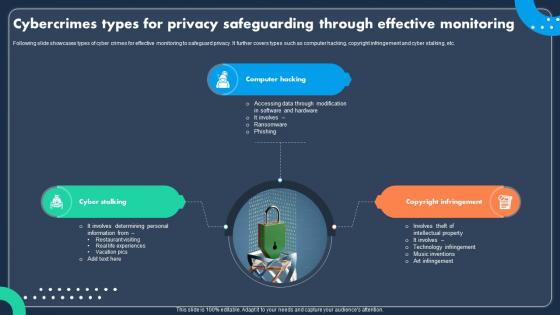 Cybercrimes Types For Privacy Safeguarding Through Effective Monitoring
Cybercrimes Types For Privacy Safeguarding Through Effective MonitoringFollowing slide showcases types of cyber crimes for effective monitoring to safeguard privacy. It further covers types such as computer hacking, copyright infringement and cyber stalking, etc. Introducing our premium set of slides with Cybercrimes Types For Privacy Safeguarding Through Effective Monitoring Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Stalking, Computer Hacking, Copyright Infringement. So download instantly and tailor it with your information.
-
 Phase 3 Of Dlp Success Execute Monitoring Program Safeguarding Business With Data Loss Cybersecurity SS
Phase 3 Of Dlp Success Execute Monitoring Program Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding execution of a monitoring program for successful data loss prevention execution. Essential roles to manage DLP integrity include technical administrator, forensics investigator, etc.Introducing Phase 3 Of Dlp Success Execute Monitoring Program Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Objective, Initiative, Forensics Investigator, Technical Administrator, using this template. Grab it now to reap its full benefits.
-
 Essential Initiatives To Safeguard Selecting Suitable It Department Activities Monitoring Tool
Essential Initiatives To Safeguard Selecting Suitable It Department Activities Monitoring ToolThis slide provides information regarding selection of potential IT infrastructure monitoring tool through comparative assessment based on various features such as real time visibility, capacity planning, network infrastructure monitoring, etc. along with costs. Deliver an outstanding presentation on the topic using this Essential Initiatives To Safeguard Selecting Suitable It Department Activities Monitoring Tool. Dispense information and present a thorough explanation of Network Infrastructure Monitoring, Virtual Machine Monitoring, Real Time Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



