Powerpoint Templates and Google slides for Mitigating Cyber Security Risks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Blockchain Cyber Security Issues And Risk Mitigation Powerpoint Ppt Template Bundles BCT MM
Blockchain Cyber Security Issues And Risk Mitigation Powerpoint Ppt Template Bundles BCT MMIf you require a professional template with great design, then this Blockchain Cyber Security Issues And Risk Mitigation Powerpoint Ppt Template Bundles BCT MM is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using thirteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Cyber Security Risk Mitigation Strategy Action Plan Icon
Cyber Security Risk Mitigation Strategy Action Plan IconIntroducing our premium set of slides with Cyber Security Risk Mitigation Strategy Action Plan Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mitigation, Strategy, Action. So download instantly and tailor it with your information.
-
 Cyber Security Risk Mitigation Methods Of Collaboration Tools
Cyber Security Risk Mitigation Methods Of Collaboration ToolsThe purpose of this slide is to highlight cyber security risk mitigation solutions of collaboration tools such as training employees on security awareness, contacting source, etc. Introducing our premium set of slides with Cyber Security Risk Mitigation Methods Of Collaboration Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Simulate Phishing Tests, Verify Senders Identity, Use Official Channels . So download instantly and tailor it with your information.
-
 Mitigating Cloning Risks In Cyber Security
Mitigating Cloning Risks In Cyber SecurityThis slide shows strategies to counter cloning attacks. The purpose of this slide is to help cybersecurity experts in identifying and preventing cybersecurity threats. It covers mitigating measures such as security awareness training, email credentials security, link authentication, etc. Introducing our premium set of slides with name Mitigating Cloning Risks In Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Awareness, Link Authentication, Security Solutions. So download instantly and tailor it with your information.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats
Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Deliver an outstanding presentation on the topic using this Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats
KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Level Of Preparedness, Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats
Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Present the topic in a bit more detail with this Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Objectives, Features, Duration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Mitigate Saas Cyber Security Risks
Strategies To Mitigate Saas Cyber Security RisksThis slide represents tips to boost SaaS cyber security by reducing risks. It aims to implement effective measures collectively to reduce cyber security risks for SaaS platform. It includes various approaches such as continuous SaaS discovery, consistent SaaS risk management, etc. Introducing our premium set of slides with Strategies To Mitigate Saas Cyber Security Risks Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Continuous Saas Discovery, Risk Management, Mitigate Vulnerabilities. So download instantly and tailor it with your information.
-
 Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence
Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk OccurrenceThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence Use it as a tool for discussion and navigation on Parameters, Impact, Probability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix
Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity MatrixThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Introducing Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Very Severe, Severe, Moderate using this template. Grab it now to reap its full benefits.
-
 Strategies To Mitigate Cyber Security Risks In Banking Sector
Strategies To Mitigate Cyber Security Risks In Banking SectorThis slide represents approaches to reduce risk of cyber security in banking sector. This template aims to cyber security risks in banking sector to protect sensitive financial data and maintain customer trust. It includes various strategies such as risk determination, mitigating identity theft and fraud, etc. Introducing our premium set of slides with Strategies To Mitigate Cyber Security Risks In Banking Sector. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Privacy Protection, Application Control, Risk Determination. So download instantly and tailor it with your information.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan
Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan. Use it as a tool for discussion and navigation on Threat, Risk, Risk Priority, Risk Reduction Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Plan For Cyber Security Risk Scenario Management
Mitigation Plan For Cyber Security Risk Scenario ManagementThis slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Presenting our well structured Mitigation Plan For Cyber Security Risk Scenario Management. The topics discussed in this slide are Risk, Risk Priority, Risk Mitigation Plan. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems
Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Mitigation Plan, Prioritized, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Impact And Mitigation Plan For Cyber Security
Risk Impact And Mitigation Plan For Cyber SecurityThis slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Introducing our Risk Impact And Mitigation Plan For Cyber Security set of slides. The topics discussed in these slides are Risk Priority, Risk Mitigation Plan, Risk Owner. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Mitigating Business Cyber Security Strategies
Risk Mitigating Business Cyber Security StrategiesThis slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access. Presenting our set of slides with name Risk Mitigating Business Cyber Security Strategies. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employees, Spyware, Data, Employee Access.
-
 Mitigating Cyber Security Risks In Powerpoint And Google Slides Cpb
Mitigating Cyber Security Risks In Powerpoint And Google Slides CpbPresenting Mitigating Cyber Security Risks In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Mitigating Cyber Security Risks. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation
Adopt Cyber Security Data Policies Cyber Attack Risks MitigationThe following slide highlights various cyber security policies to manage data control and breach. It includes elements such as network security, data, workstations, remote access etc. Introducing Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Policies, Data Security Policies, Workstation Policies, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation
Impact Of Cyber Security Policies And Practices Cyber Attack Risks MitigationThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, etc. Present the topic in a bit more detail with this Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation. Use it as a tool for discussion and navigation on Inadequate Security Guidelines, Inappropriate Privacy Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation
Multiple Strategic Cyber Security Approaches Cyber Attack Risks MitigationThe following slide depicts various cyber safety approaches to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as data, application, infrastructure, network, devices, automation etc. Increase audience engagement and knowledge by dispensing information using Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation. This template helps you present information on one stage. You can also present information on Identities, Organization Policy, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation
Organize Cyber Security Training For Employees Regularly Cyber Attack Risks MitigationThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Introducing Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Document Management, Response Process, Social Media Policy, using this template. Grab it now to reap its full benefits.
-
 Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation
Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks MitigationThe following slide showcases passive, active and offensive cyber safety techniques to ensure customer data safety. It includes elements such as inspecting vulnerabilities, penetration testing, deception technology, threat hunting etc. Increase audience engagement and knowledge by dispensing information using Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Passive Safety, Active Safety, Offensive Safety using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation
Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks MitigationThe following slide depicts the stages of cyber security to avoid information loss and improved accessibility. It includes elements such as managing attack surface, optimizing process, stakeholder engagement etc. Introducing Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Proactive, Managing Attack Surface, Optimize Process, Stakeholder Engagement, using this template. Grab it now to reap its full benefits.
-
 Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation
Stages Of Implementing Cyber Security Strategies Cyber Attack Risks MitigationThe following slide highlights major stages of executing cyber security techniques to ensure effective implementation. It includes elements such as plan, analyze, upgrade, continuous improvement etc. Increase audience engagement and knowledge by dispensing information using Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on four stages. You can also present information on Plan Strategy, Implement Strategy, Analyse Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation
Steps To Create Cyber Security Strategies Cyber Attack Risks MitigationThe following slide illustrates some steps to create and implement cybersecurity techniques. It includes elements such as determining threat type, selecting security framework, optimizing plan, implementing strategy etc. Introducing Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Comprehend Threat Landscape, Evaluate Cybersecurity Maturity, Optimize Cybersecurity Program, using this template. Grab it now to reap its full benefits.
-
 Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation
Strategic Cyber Security Action Plan Cyber Attack Risks MitigationThe following slide depicts action plan to minimize impact of cyber attacks. It includes elements such as understand, develop, deliver, assess organizational principles, evaluate alternatives, examine possible alternatives, execute actions etc. Increase audience engagement and knowledge by dispensing information using Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Understand, Develop, Deliver, Organizational Principles using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps to mitigate cyber security risks
Steps to mitigate cyber security risksPresenting this set of slides with name Steps To Mitigate Cyber Security Risks. This is a five stage process. The stages in this process are Assets Identification, Asset Protection, Incident Detection, Build Plan To Respond, Recovery To Normal Operation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
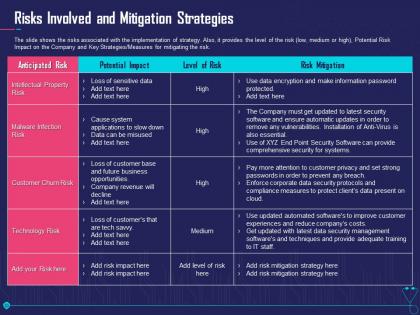 Risks involved and mitigation strategies overcome challenge cyber security healthcare ppt ideas
Risks involved and mitigation strategies overcome challenge cyber security healthcare ppt ideasThe slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies or Measures for mitigating the risk. Present the topic in a bit more detail with this Risks Involved And Mitigation Strategies Overcome Challenge Cyber Security Healthcare Ppt Ideas. Use it as a tool for discussion and navigation on Revenue, Opportunities, Management, Security, Data. This template is free to edit as deemed fit for your organization. Therefore download it now.



