Powerpoint Templates and Google slides for Managing Security Functions
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Identity And Access Management Function As Security Tool IAM Process For Effective Access
Identity And Access Management Function As Security Tool IAM Process For Effective AccessThis slide showcases function of Identity and Access Management as a security tool. The purpose of this slide is to explain the function of IAM as an essential security tool these include context awareness, identity and access governance, and so on. Present the topic in a bit more detail with this Identity And Access Management Function As Security Tool IAM Process For Effective Access. Use it as a tool for discussion and navigation on Context Awareness, Identity And Access Governance, Management Function. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Functions Of Identity And Access Management Process Securing Systems With Identity
Functions Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management process functions. The purpose of this slide is to highlight the various functions, including identification in the system, roles in the design, assigning access levels, protecting sensitive data, and so on. Introducing Functions Of Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Identification In System, Roles In System using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Introduction And Functions Securing Systems With Identity
Identity And Access Management Introduction And Functions Securing Systems With IdentityThis slide gives an overview of the Identity and Access Management process. The purpose of this slide is to explain the IAM and its functions in ensuring authentication, reporting, authorization, workflow, access management, and so on. Introducing Identity And Access Management Introduction And Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Company Data And Resources, Streamline Workflows using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Working Functions Securing Systems With Identity
Identity And Access Management Working Functions Securing Systems With IdentityThis slide discusses the working process of Identity and Access Management . The purpose of this slide is to explain the workflow of the IAM this includes identity management that validates login attempts and access management that manages the entitys access. Introducing Identity And Access Management Working Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Management, Access Management using this template. Grab it now to reap its full benefits.
-
 Addressing critical business functions recovery priorities corporate security management
Addressing critical business functions recovery priorities corporate security managementThis slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Introducing Addressing Critical Business Functions Recovery Priorities Corporate Security Management to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Addressing Critical Business Functions Recovery Priorities, using this template. Grab it now to reap its full benefits.
-
 Corporate security management ensuring collaboration among various functional areas
Corporate security management ensuring collaboration among various functional areasThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Increase audience engagement and knowledge by dispensing information using Corporate Security Management Ensuring Collaboration Among Various Functional Areas. This template helps you present information on three stages. You can also present information on Plan And Collet, Review And Analyze, Develop Strategic Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensuring collaboration among various functional corporate security management
Ensuring collaboration among various functional corporate security managementThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Increase audience engagement and knowledge by dispensing information using Ensuring Collaboration Among Various Functional Corporate Security Management. This template helps you present information on ten stages. You can also present information on Data Privacy, Internal Communication, External Communication, Business Continuity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management addressing critical business functions recovery priorities
Cyber security risk management addressing critical business functions recovery prioritiesThis slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Addressing Critical Business Functions Recovery Priorities. This template helps you present information on two stages. You can also present information on Priorities, Department, Maximum Allowable Downtime, Contracts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensuring collaboration among various functional areas cyber security risk management
Ensuring collaboration among various functional areas cyber security risk managementThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Introducing Ensuring Collaboration Among Various Functional Areas Cyber Security Risk Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Legal, Compliance, Public Relations, Human Resources, Procurement, Board And Risk Committee, using this template. Grab it now to reap its full benefits.
-
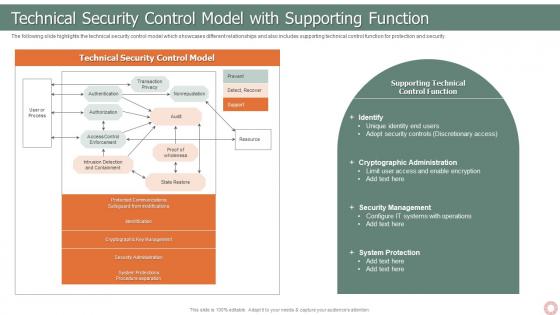 IT Risk Management Strategies Technical Security Control Model With Supporting Function
IT Risk Management Strategies Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing IT Risk Management Strategies Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technical Security, Control Model, Transaction Privacy, State Restore, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Technical Security Control Model With Supporting Function
Enterprise Risk Management Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing Enterprise Risk Management Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Cryptographic Administration, Security Management, System Protection, using this template. Grab it now to reap its full benefits.



