Powerpoint Templates and Google slides for Managing Cyber Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Incident Management Checklist During Development And Implementation Of Security
Cyber Security Incident Management Checklist During Development And Implementation Of SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Introducing Cyber Security Incident Management Checklist During Development And Implementation Of Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Triage Current Problems, Communicate, Executive Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Team Roles Development And Implementation Of Security
Cyber Security Incident Management Team Roles Development And Implementation Of SecurityThis slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Present the topic in a bit more detail with this Cyber Security Incident Management Team Roles Development And Implementation Of Security. Use it as a tool for discussion and navigation on Incident Management, Business Decision Capability, Network Management Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Management Team Structure Development And Implementation Of Security
Cyber Security Incident Management Team Structure Development And Implementation Of SecurityThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure Development And Implementation Of Security. This template helps you present information on one stages. You can also present information on Human Resources, Outside Counsel, Forensics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident
Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security IncidentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Consequences, Vulnerability, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security
Impact Of Implementing Cyber Security Incident Management Development And Implementation Of SecurityThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present the topic in a bit more detail with this Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security. Use it as a tool for discussion and navigation on Results, Post Implementation, Pre Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management
Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Increase audience engagement and knowledge by dispensing information using Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management. This template helps you present information on two stages. You can also present information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management
Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Introducing Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Privileged User Accounts, Unusual Behavior, Network Traffic, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities
Cyber Security Attacks Response Cyber Security Incident Management Team Roles And ResponsibilitiesPresent the topic in a bit more detail with this Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities. Use it as a tool for discussion and navigation on Cyber Security Incident, Management Team, Roles And Responsibilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management
Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident ManagementThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management. Dispense information and present a thorough explanation of Cyber Security Incident, Management On Organization, Software Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline
Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan TimelineThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline. Use it as a tool for discussion and navigation on Incident Response, Business Continuity, Review And Recovery, Management Action, Plan Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response
Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks ResponseThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist After An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan
Cyber Security Incident Management Team Structure Cyber Security Attacks Response PlanThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team. Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Incident Management, Team Structure, Human Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing ITThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing ITThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing ITThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Training Completion, Communication Methods, Policy Sign Off. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before
K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist BeforeThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist Before An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident Management
Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident ManagementThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery.Present the topic in a bit more detail with this Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Business Continuity, Incident Response, Review Recovery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management
Cyber Security Incident Communication Strategy Deploying Computer Security Incident ManagementThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders.Introducing Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Impacted Business, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handling Checklist Deploying Computer Security Incident Management
Cyber Security Incident Handling Checklist Deploying Computer Security Incident ManagementThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handling Checklist Deploying Computer Security Incident Management. This template helps you present information on one stage. You can also present information on Containment Eradication, Acquisition Preservation, Incident Containment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist After An Incident Deploying Computer Security
Cyber Security Incident Management Checklist After An Incident Deploying Computer SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident.Introducing Cyber Security Incident Management Checklist After An Incident Deploying Computer Security to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Reporting Requirements, Quantify Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Team Structure Deploying Computer Security Incident Management
Cyber Security Incident Management Team Structure Deploying Computer Security Incident ManagementThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure Deploying Computer Security Incident Management. This template helps you present information on five stages. You can also present information on Systems Analyst, Network Analyst, Firewall Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management
Cyber Security Incident Response Lifecycle Deploying Computer Security Incident ManagementThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc.Introducing Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Eradication Recovery, Post Incident Activity, Remove Malwares, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management
Cyber Security Threats Detection Techniques Deploying Computer Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc.Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Threat Intelligence, Access Regularly, Undercovers Intruders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
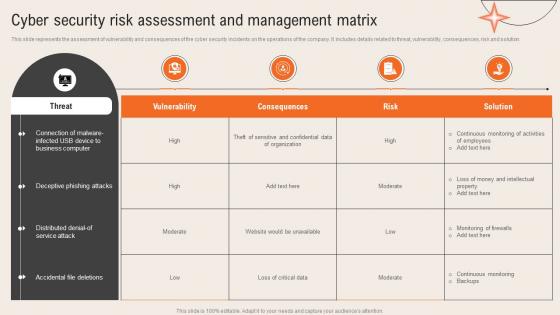 Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix
Deploying Computer Security Incident Cyber Security Risk Assessment And Management MatrixThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix. Use it as a tool for discussion and navigation on Deceptive Phishing, Business Computer, Accidental File Deletions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide Implementing Cyber Security Incident Management
Icons Slide Implementing Cyber Security Incident ManagementIntroducing our well researched set of slides titled Icons Slide Implementing Cyber Security Incident Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Ways To Detect Cyber Security Incidents Deploying Computer Security Incident Management
Ways To Detect Cyber Security Incidents Deploying Computer Security Incident ManagementThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc.Increase audience engagement and knowledge by dispensing information using Ways To Detect Cyber Security Incidents Deploying Computer Security Incident Management. This template helps you present information on four stages. You can also present information on Unusual Behavior, Privileged Accounts, Anomalies Outbound using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Success For Cyber Security Risk Management
Steps To Success For Cyber Security Risk ManagementThe following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover.Presenting our set of slides with Steps To Success For Cyber Security Risk Management. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identity, Protect, Detect, Respond.
-
 F1190 Managing Cyber Security In Manufacturing 30 Days Plan 3d Printing In Manufacturing
F1190 Managing Cyber Security In Manufacturing 30 Days Plan 3d Printing In ManufacturingThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this F1190 Managing Cyber Security In Manufacturing 30 Days Plan 3d Printing In Manufacturing. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing,Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1191 Managing Cyber Security In Manufacturing 60 Days Plan 3d Printing In Manufacturing
F1191 Managing Cyber Security In Manufacturing 60 Days Plan 3d Printing In ManufacturingThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this F1191 Managing Cyber Security In Manufacturing 60 Days Plan 3d Printing In Manufacturing. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 90 Days Plan 3d Printing In Manufacturing
Managing Cyber Security In Manufacturing 90 Days Plan 3d Printing In ManufacturingThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 90 Days Plan 3d Printing In Manufacturing. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Manufacturing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security
Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorization, Confidentiality, Availability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security
Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver an outstanding presentation on the topic using this Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Manufacturing, Government, Healthcare using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security
Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Present the topic in a bit more detail with this Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Unauthorized, Business, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security
Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Targeted Intelligence, Malware Intelligence, Reputation Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security
Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability. Deliver an outstanding presentation on the topic using this Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Categorizing, Confidentiality, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security
Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Present the topic in a bit more detail with this Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Management, Initiatives, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security
Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Comparative, Assessment, Parameters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security
Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Present the topic in a bit more detail with this Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Contingency Solutions, Contingency Considerations, Information . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security
Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Parameters, Capability, Determine . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security
Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Installation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security
Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Present the topic in a bit more detail with this Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Malicious Insider, Negligent Or Careless Insider, Third Party Insider . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security
Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Introducing Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Finance, Corporate Security, Business Division, using this template. Grab it now to reap its full benefits.
-
 Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security
Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Increase audience engagement and knowledge by dispensing information using Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security. This template helps you present information on three stages. You can also present information on Plan And Collect, Review And Analyze, Strategic Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security
Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. Deliver an outstanding presentation on the topic using this Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Potential, Technologies, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Cyber Threats Management To Enable Digital Assets Security
Table Of Contents Cyber Threats Management To Enable Digital Assets SecurityPresent the topic in a bit more detail with this Table Of Contents Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorizing, Associated, Determine Sequence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Management Deploying Computer Security
Cyber Security Incident Management Deploying Computer SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Deploying Computer Security. This template helps you present information on one stage. You can also present information on Prepare Cyber, Documented Procedures, Quantify Financial using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Deploying Computer Security
Cyber Security Incident Management Team Deploying Computer SecurityThis slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc.Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Deploying Computer Security. Dispense information and present a thorough explanation of Communication Skills, Crisis Management, Network Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Management Process In Powerpoint And Google Slides Cpb
Cyber Security Risk Management Process In Powerpoint And Google Slides CpbPresenting our Cyber Security Risk Management Process In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Risk Management Process This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 IoT In Manufacturing IT Managing Cyber Security In Manufacturing 30 Days Plan
IoT In Manufacturing IT Managing Cyber Security In Manufacturing 30 Days PlanThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this IoT In Manufacturing IT Managing Cyber Security In Manufacturing 30 Days Plan. Dispense information and present a thorough explanation of Managing, Security, Manufacturing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Threat Management Flow Chart
Cyber Security Threat Management Flow ChartThis slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Introducing our Cyber Security Threat Management Flow Chart set of slides. The topics discussed in these slides are Threat Analysis, Residual Risk Acceptable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Strategy Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cyber security strategy management colored icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cyber Security Strategy Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cyber security strategy management monotone icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation Show Slides
Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation Show SlidesThis slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc.Deliver an outstanding presentation on the topic using this Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation Show Slides. Dispense information and present a thorough explanation of Insufficient Professionals, Technology Development, Business Priorities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Effectively Managing Cyber Security Incidents Ppt Infographic Template Layout
Best Practices For Effectively Managing Cyber Security Incidents Ppt Infographic Template LayoutThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as train staff on cyber incident management process.Introducing Best Practices For Effectively Managing Cyber Security Incidents Ppt Infographic Template Layout to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Management Plan, Management Process, Responsibilities Members, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Crisis Management Action Plan Timeline Ppt File Background Images
Cyber Security Crisis Management Action Plan Timeline Ppt File Background ImagesThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery.Increase audience engagement and knowledge by dispensing information using Cyber Security Crisis Management Action Plan Timeline Ppt File Background Images. This template helps you present information on one stage. You can also present information on Business Continuity, Incident Response, Review Recovery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Event And Incident Management Architecture Ppt Portfolio Tips
Cyber Security Event And Incident Management Architecture Ppt Portfolio TipsThis slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation.Present the topic in a bit more detail with this Cyber Security Event And Incident Management Architecture Ppt Portfolio Tips. Use it as a tool for discussion and navigation on Collect Information, Confirmed Security, Classify Severity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Ppt File Visual Aids
Cyber Security Risk Assessment And Management Matrix Ppt File Visual AidsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Ppt File Visual Aids. Use it as a tool for discussion and navigation on Deceptive Phishing Attacks, Monitoring Firewalls, Continuous Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Cyber Security Incident Management Overview
Table Of Contents Cyber Security Incident Management OverviewPresent the topic in a bit more detail with this Table Of Contents Cyber Security Incident Management Overview. Use it as a tool for discussion and navigation on Security Incident, Response Workflow, Management Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
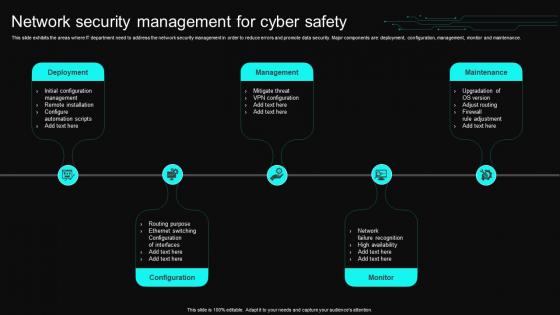 Network Security Management For Cyber Safety
Network Security Management For Cyber SafetyThis slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting our set of slides with Network Security Management For Cyber Safety. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Deployment, Management, Maintenance, Configuration.





