Powerpoint Templates and Google slides for Management And Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security information and event management benchmarking maturity model
Security information and event management benchmarking maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Security Information And Event Management Benchmarking Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve, Visibility, Identify, using this template. Grab it now to reap its full benefits.
-
 Security information and event management benefits siem services
Security information and event management benefits siem servicesThis slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management Benefits SIEM Services. This template helps you present information on four stages. You can also present information on Financial, Managing, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management calculating network device
Security information and event management calculating network deviceThis slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Present the topic in a bit more detail with this Security Information And Event Management Calculating Network Device. Use it as a tool for discussion and navigation on Calculating Network Device Velocity Sizing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management cloud siem model
Security information and event management cloud siem modelThis slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver an outstanding presentation on the topic using this Security Information And Event Management Cloud SIEM Model. Dispense information and present a thorough explanation of Visualization, Alerting, Analytics using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management companys enhanced features
Security information and event management companys enhanced featuresThis slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Present the topic in a bit more detail with this Security Information And Event Management Companys Enhanced Features. Use it as a tool for discussion and navigation on Detection, Investigation, Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management estimating ownership siem
Security information and event management estimating ownership siemThis slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver an outstanding presentation on the topic using this Security Information And Event Management Estimating Ownership SIEM. Dispense information and present a thorough explanation of Infrastructure, Product, Expenses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management fully managed service model
Security information and event management fully managed service modelPresent the topic in a bit more detail with this Security Information And Event Management Fully Managed Service Model. Use it as a tool for discussion and navigation on Visualization, Correlation, Aggregation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management how siem works
Security information and event management how siem worksDeliver an outstanding presentation on the topic using this Security Information And Event Management How SIEM Works. Dispense information and present a thorough explanation of Operating Systems, Network Device, Security Device using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management hybrid managed siem model
Security information and event management hybrid managed siem modelPresent the topic in a bit more detail with this Security Information And Event Management Hybrid Managed SIEM Model. Use it as a tool for discussion and navigation on Hybrid Managed SIEM Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management key features of siem software
Security information and event management key features of siem softwareThis slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Introducing Security Information And Event Management Key Features Of SIEM Software to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive, Collection, Compliance, using this template. Grab it now to reap its full benefits.
-
 Security information and event management log management metrics
Security information and event management log management metricsIncrease audience engagement and knowledge by dispensing information using Security Information And Event Management Log Management Metrics. This template helps you present information on eight stages. You can also present information on Configurations, Virtualization, Application using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management need for siem software in your company
Security information and event management need for siem software in your companyThis slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management Introducing Security Information And Event Management Need For SIEM Software In Your Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digital, Security, Generating, using this template. Grab it now to reap its full benefits.
-
 Security information and event management next evolution of siem software
Security information and event management next evolution of siem softwareThis slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management Next Evolution Of SIEM Software. This template helps you present information on six stages. You can also present information on Traffic Analysis, Behavior Analytics, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management our organization flow
Security information and event management our organization flowThis slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. Introducing Security Information And Event Management Our Organization Flow to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Our Organization SIEM Log Flow, using this template. Grab it now to reap its full benefits.
-
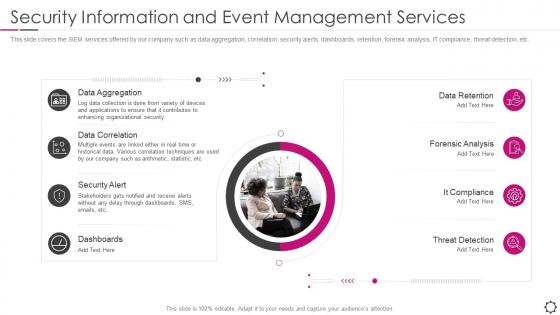 Security information and event management security management services
Security information and event management security management servicesThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Introducing Security Information And Event Management Security Management Services to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Aggregation, Data Correlation, Security Alert, using this template. Grab it now to reap its full benefits.
-
 Security information and event management siem logging sources
Security information and event management siem logging sourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management SIEM Logging Sources. This template helps you present information on four stages. You can also present information on Security Devices, Network Devices, Servers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
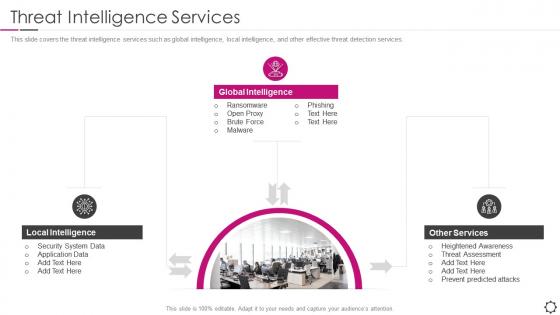 Security information and event management threat intelligence services
Security information and event management threat intelligence servicesThis slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Introducing Security Information And Event Management Threat Intelligence Services to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Global Intelligence, Local Intelligence, Services, using this template. Grab it now to reap its full benefits.
-
 Security information and event management traditional siem deployment
Security information and event management traditional siem deploymentThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Present the topic in a bit more detail with this Security Information And Event Management Traditional SIEM Deployment. Use it as a tool for discussion and navigation on Visualization, Collection, Aggregation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management various siem cost
Security information and event management various siem costThis slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an outstanding presentation on the topic using this Security Information And Event Management Various SIEM Cost. Dispense information and present a thorough explanation of Correlation, Response, Intermediate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
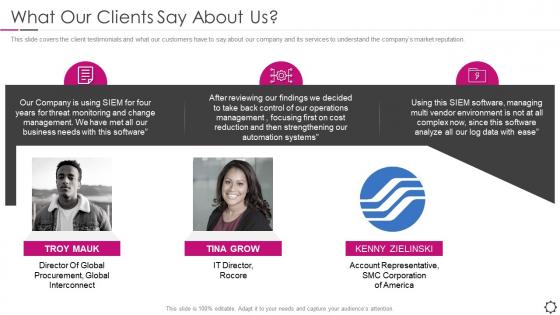 Security information and event management what about us
Security information and event management what about usThis slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation.Introducing Security Information And Event Management What About Us to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on What Our Clients Say About Us, using this template. Grab it now to reap its full benefits.
-
 Security information and event management security intelligence services
Security information and event management security intelligence servicesThis slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Introducing Security Information And Event Management Security Intelligence Services to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Cyber, Analytics, using this template. Grab it now to reap its full benefits.
-
 Security information and event management sim vs sem vs siem
Security information and event management sim vs sem vs siemIncrease audience engagement and knowledge by dispensing information using Security Information And Event Management SIM Vs SEM Vs SIEM. This template helps you present information on three stages. You can also present information on Information, Management, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Siem competitive advantage security information and event management
Siem competitive advantage security information and event managementThis slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Present the topic in a bit more detail with this SIEM Competitive Advantage Security Information And Event Management. Use it as a tool for discussion and navigation on Experience, Management, Performance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management siem software challenges
Security information and event management siem software challengesThis slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Deliver an outstanding presentation on the topic using this Security Information And Event Management SIEM Software Challenges. Dispense information and present a thorough explanation of Configurations, Respond, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Siem competitive value security information and event management
Siem competitive value security information and event managementThis slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Present the topic in a bit more detail with this SIEM Competitive Value Security Information And Event Management. Use it as a tool for discussion and navigation on SIEM Competitive Advantage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information process security information and event management
Security information process security information and event managementThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Security Information Process Security Information And Event Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Connecting, Assessing, Streaming, Protocol, using this template. Grab it now to reap its full benefits.
-
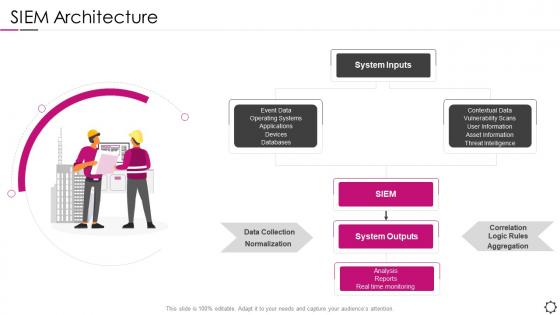 Siem architecture security information and event management
Siem architecture security information and event managementPresent the topic in a bit more detail with this SIEM Architecture Security Information And Event Management. Use it as a tool for discussion and navigation on Operating, Systems, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk reporting and likelihood effective information security risk management process
Risk reporting and likelihood effective information security risk management processMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Risk Reporting And Likelihood Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Attack Scenario, Risk Encountered, Equipment Failure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roles and responsibilities effective information security risk management process
Roles and responsibilities effective information security risk management processFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development.Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Effective Information Security Risk Management Process. This template helps you present information on one stage. You can also present information on Information Management Manager, Risk Management Officer, Development And Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5 practices of information and cyber security risk management
5 practices of information and cyber security risk managementMentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting our set of slides with 5 Practices Of Information And Cyber Security Risk Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Organization, Risk.
-
 Cyber and information security risk management framework
Cyber and information security risk management frameworkMentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Introducing our Cyber And Information Security Risk Management Framework set of slides. The topics discussed in these slides are Development, Service Transition, Service Operationalization. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon for information and cyber security risk management
Icon for information and cyber security risk managementIntroducing our premium set of slides with Icon For Information And Cyber Security Risk Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information And Cyber Security Risk Management. So download instantly and tailor it with your information.
-
 Icon for information security and risk management team
Icon for information security and risk management teamIntroducing our premium set of slides with Icon For Information Security And Risk Management Team. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information Security And Risk Management Team. So download instantly and tailor it with your information.
-
 Information and cyber security risk management maturity levels
Information and cyber security risk management maturity levelsMentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Introducing our premium set of slides with Information And Cyber Security Risk Management Maturity Levels. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Partial, Informed, Repetitive. So download instantly and tailor it with your information.
-
 Information and cyber security risk management plan
Information and cyber security risk management planMentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Introducing our Information And Cyber Security Risk Management Plan set of slides. The topics discussed in these slides are Degree Of Risk, Strategies, Devices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security risk assessment and management tools
Information security risk assessment and management toolsMentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Introducing our premium set of slides with Information Security Risk Assessment And Management Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Ratings, Automated Questionnaires, Vulnerability Assessment Report. So download instantly and tailor it with your information.
-
 Addressing asset security managing critical threat vulnerabilities and security threats
Addressing asset security managing critical threat vulnerabilities and security threatsThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Introducing Addressing Asset Security Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ownership, Location, Confidentiality, Integrity, using this template. Grab it now to reap its full benefits.
-
 Addressing critical business managing critical threat vulnerabilities and security threats
Addressing critical business managing critical threat vulnerabilities and security threatsThis slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Present the topic in a bit more detail with this Addressing Critical Business Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Department, Priorities, Allowable Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing cyber threats in managing critical threat vulnerabilities and security threats
Addressing cyber threats in managing critical threat vulnerabilities and security threatsThis slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Increase audience engagement and knowledge by dispensing information using Addressing Cyber Threats In Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on four stages. You can also present information on Healthcare, Manufacturing, Government, Energy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing indicators associated managing critical threat vulnerabilities and security threats
Addressing indicators associated managing critical threat vulnerabilities and security threatsThis slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Introducing Addressing Indicators Associated Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Authentication Levels, Data Exfiltration, Traits, Demeanor, using this template. Grab it now to reap its full benefits.
-
 Addressing internal and external managing critical threat vulnerabilities and security threats
Addressing internal and external managing critical threat vulnerabilities and security threatsThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Increase audience engagement and knowledge by dispensing information using Addressing Internal And External Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on two stages. You can also present information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, External Sources, Internal Sources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing natural calamities managing critical threat vulnerabilities and security threats
Addressing natural calamities managing critical threat vulnerabilities and security threatsThis slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an outstanding presentation on the topic using this Addressing Natural Calamities Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Threat Management Checklist using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing several financial managing critical threat vulnerabilities and security threats
Addressing several financial managing critical threat vulnerabilities and security threatsThis slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Introducing Addressing Several Financial Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Insolvency Scenario, Currency Scenario, Unexpected Fluctuations, Bankruptcy, using this template. Grab it now to reap its full benefits.
-
 Addressing threat management critical threat vulnerabilities and security threats
Addressing threat management critical threat vulnerabilities and security threatsThe threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Present the topic in a bit more detail with this Addressing Threat Management Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Hypotheticals, Workshops, Field Exercises. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing various ways to managing critical threat vulnerabilities and security threats
Addressing various ways to managing critical threat vulnerabilities and security threatsThis slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Increase audience engagement and knowledge by dispensing information using Addressing Various Ways To Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on four stages. You can also present information on Management Policies, User Accounts, Active Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing ways to handling managing critical threat vulnerabilities and security threats
Addressing ways to handling managing critical threat vulnerabilities and security threatsThis slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Introducing Addressing Ways To Handling Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cash Requirement, Financial Statements, Overheads Analysis, Currency Hedging, using this template. Grab it now to reap its full benefits.
-
 Budget for effective threat managing critical threat vulnerabilities and security threats
Budget for effective threat managing critical threat vulnerabilities and security threatsFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an outstanding presentation on the topic using this Budget For Effective Threat Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Incident Management, Risk Management, Client Onboarding Process, Document Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative assessment of managing critical threat vulnerabilities and security threats
Comparative assessment of managing critical threat vulnerabilities and security threatsThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Present the topic in a bit more detail with this Comparative Assessment Of Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Insider Threat, Social Engineering, Maintenance Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Contingency plan for cyber managing critical threat vulnerabilities and security threats
Contingency plan for cyber managing critical threat vulnerabilities and security threatsThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Introducing Contingency Plan For Cyber Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Contingency Solutions, Contingency Considerations, using this template. Grab it now to reap its full benefits.
-
 Determine sequence phases for managing critical threat vulnerabilities and security threats
Determine sequence phases for managing critical threat vulnerabilities and security threatsThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Increase audience engagement and knowledge by dispensing information using Determine Sequence Phases For Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on four stages. You can also present information on Installation, Command And Control, Actions And Objectives, Covering Tracks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine several threat actors managing critical threat vulnerabilities and security threats
Determine several threat actors managing critical threat vulnerabilities and security threatsThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an outstanding presentation on the topic using this Determine Several Threat Actors Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Determine Several Threat Actors Profile using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine staff training schedule managing critical threat vulnerabilities and security threats
Determine staff training schedule managing critical threat vulnerabilities and security threatsThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Introducing Determine Staff Training Schedule Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Advanced Software Training, Training Module, using this template. Grab it now to reap its full benefits.
-
 Determine threat management managing critical threat vulnerabilities and security threats
Determine threat management managing critical threat vulnerabilities and security threatsThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Increase audience engagement and knowledge by dispensing information using Determine Threat Management Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on two stages. You can also present information on Determine Threat Management Team Structure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine threat scenario managing critical threat vulnerabilities and security threats
Determine threat scenario managing critical threat vulnerabilities and security threatsThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Present the topic in a bit more detail with this Determine Threat Scenario Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Threat Campaign, Actions And Objectives, Covering Tracks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different kinds of insider digital managing critical threat vulnerabilities and security threats
Different kinds of insider digital managing critical threat vulnerabilities and security threatsThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Introducing Different Kinds Of Insider Digital Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Third Party Insider, Malicious Insider, using this template. Grab it now to reap its full benefits.
-
 Ensuring collaboration among managing critical threat vulnerabilities and security threats
Ensuring collaboration among managing critical threat vulnerabilities and security threatsThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Increase audience engagement and knowledge by dispensing information using Ensuring Collaboration Among Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on ten stages. You can also present information on Human Resources, Procurement, Public Relations, Compliance, Legal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensuring vital records maintenance managing critical threat vulnerabilities and security threats
Ensuring vital records maintenance managing critical threat vulnerabilities and security threatsThis slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Introducing Ensuring Vital Records Maintenance Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Settlement Agreements, Primary Location, using this template. Grab it now to reap its full benefits.
-
 Evaluating financial practices in firm managing critical threat vulnerabilities and security threats
Evaluating financial practices in firm managing critical threat vulnerabilities and security threatsThe firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an outstanding presentation on the topic using this Evaluating Financial Practices In Firm Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Accounting, Short Term Expenses, Financial Statements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How financial risk can be controlled managing critical threat vulnerabilities and security threats
How financial risk can be controlled managing critical threat vulnerabilities and security threatsThis slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Increase audience engagement and knowledge by dispensing information using How Financial Risk Can Be Controlled Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on three stages. You can also present information on Liquidity Risk, Exchange Risk, Credit Exchange Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact analysis for effective managing critical threat vulnerabilities and security threats
Impact analysis for effective managing critical threat vulnerabilities and security threatsThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Introducing Impact Analysis For Effective Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Security Requirement, Focus Areas, using this template. Grab it now to reap its full benefits.





