Powerpoint Templates and Google slides for Man-In-The-Middle Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Man In The Middle Attack In Cyber Security Training Ppt
Man In The Middle Attack In Cyber Security Training PptPresenting Man in the Browser Attack in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
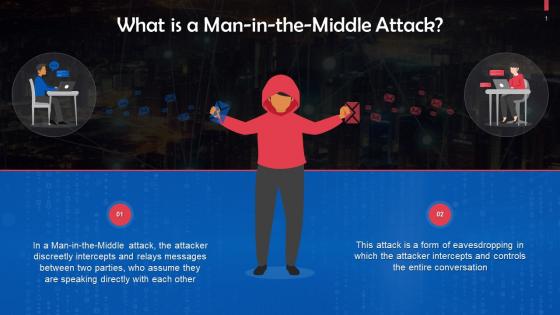 Man In The Middle Attacks In Cybersecurity Training Ppt
Man In The Middle Attacks In Cybersecurity Training PptPresenting Man in the Middle Attacks in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Working Of Man In The Middle Attacks Training Ppt
Working Of Man In The Middle Attacks Training PptPresenting Working of Man in the Middle Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
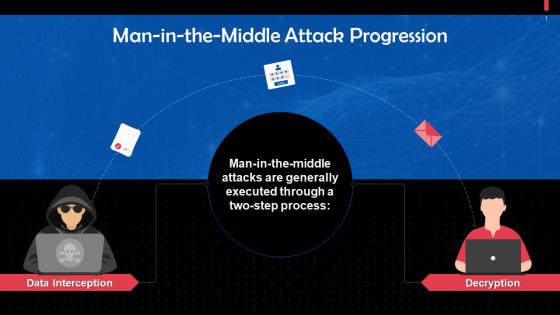 Execution Of Man In The Middle Attacks Training Ppt
Execution Of Man In The Middle Attacks Training PptPresenting Execution of Man in the Middle Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
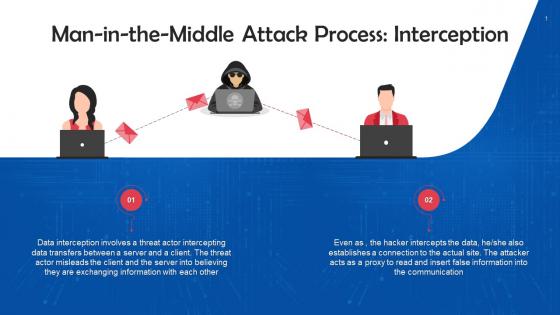 Interception Mode Of Executing Man In The Middle Attacks Training Ppt
Interception Mode Of Executing Man In The Middle Attacks Training PptPresenting Interception Mode of Executing Man in the Middle Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Decryption To Execute Man In The Middle Attacks Training Ppt
Decryption To Execute Man In The Middle Attacks Training PptPresenting Decryption to Execute Man-in-the-Middle Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Types Of Man In The Middle Attacks Training Ppt
Types Of Man In The Middle Attacks Training PptPresenting Working of Types of Man in the Middle Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
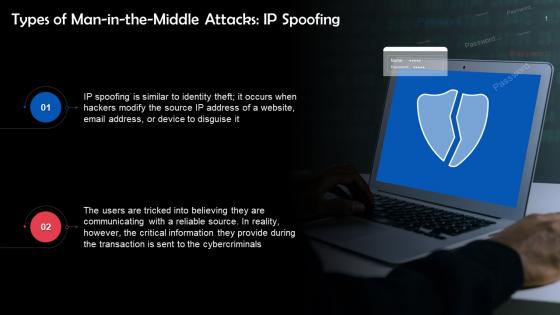 IP Spoofing As A Type Of Man In The Middle Attack Training Ppt
IP Spoofing As A Type Of Man In The Middle Attack Training PptPresenting IP Spoofing as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 HTTP Spoofing As A Type Of Man In The Middle Attack Training Ppt
HTTP Spoofing As A Type Of Man In The Middle Attack Training PptPresenting HTTP Spoofing as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 DNS Spoofing As A Type Of Man In The Middle Attack Training Ppt
DNS Spoofing As A Type Of Man In The Middle Attack Training PptPresenting DNS Spoofing as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Email Spoofing As A Type Of Man In The Middle Attack Training Ppt
Email Spoofing As A Type Of Man In The Middle Attack Training PptPresenting Email Spoofing as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 SSL Hijacking As A Type Of Man In The Middle Attack Training Ppt
SSL Hijacking As A Type Of Man In The Middle Attack Training PptPresenting SSL Hijacking as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Session Hijacking As A Type Of Man In The Middle Attack Training Ppt
Session Hijacking As A Type Of Man In The Middle Attack Training PptPresenting Session Hijacking as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Cache Poisoning As A Type Of Man In The Middle Attack Training Ppt
Cache Poisoning As A Type Of Man In The Middle Attack Training PptPresenting Cache Poisoning as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
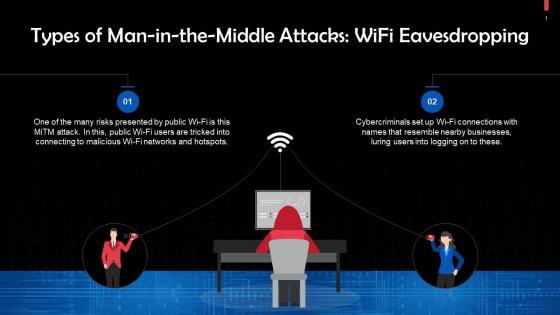 Wi Fi Eavesdropping As A Type Of Man In The Middle Attack Training Ppt
Wi Fi Eavesdropping As A Type Of Man In The Middle Attack Training PptPresenting Wi-Fi Eavesdropping as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
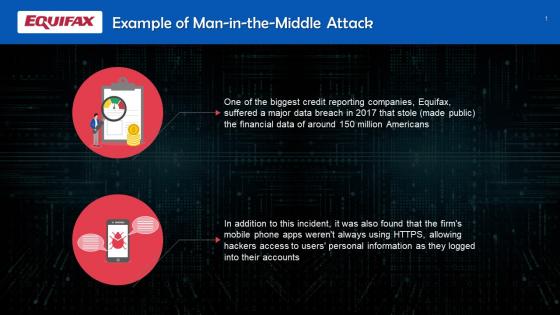 Example Of Man In The Middle Attack Training Ppt
Example Of Man In The Middle Attack Training PptPresenting Example of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
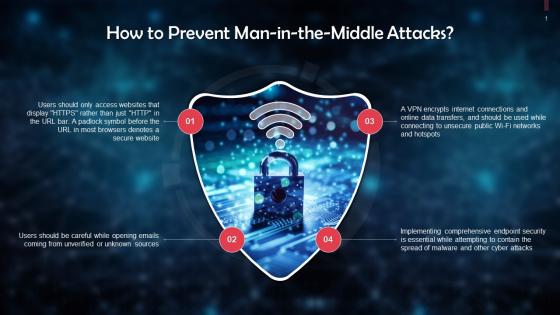 Prevention Of Man In The Middle Attacks Training Ppt
Prevention Of Man In The Middle Attacks Training PptPresenting Prevention of Man in the Middle Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber AttacksThis slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks, Interception And Decryption, Online Data Transfer, Intercepting User Traffic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram
Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack DiagramThis slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram. Dispense information and present a thorough explanation of Phishing Attack Diagram, Equifaxs Mobile Application, Toolkit Cloud Server, Intended Website Server using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Man In The Middle Mobile Banking Attacking Methods E Wallets As Emerging Payment Method Fin SS V
Man In The Middle Mobile Banking Attacking Methods E Wallets As Emerging Payment Method Fin SS VThis slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. Present the topic in a bit more detail with this Man In The Middle Mobile Banking Attacking Methods E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Interception, Communication, Web Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 NEO Banks For Digital Funds Man In The Middle Mobile Banking Attacking Methods Fin SS V
NEO Banks For Digital Funds Man In The Middle Mobile Banking Attacking Methods Fin SS VThis slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. Deliver an outstanding presentation on the topic using this NEO Banks For Digital Funds Man In The Middle Mobile Banking Attacking Methods Fin SS V. Dispense information and present a thorough explanation of Mobile Banking Attacking, Email Interception And Malware, WIFI Network Interception using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Everything About Mobile Banking Man In The Middle Mobile Banking Attack Methods Fin SS V
Everything About Mobile Banking Man In The Middle Mobile Banking Attack Methods Fin SS VThis slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. Present the topic in a bit more detail with this Everything About Mobile Banking Man In The Middle Mobile Banking Attack Methods Fin SS V. Use it as a tool for discussion and navigation on WIFI Network Interception, DNS Spoofing, Email Interception And Malware, Mobile Banking Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Banking Solutions For Improving Customer Man In The Middle Mobile Banking Attacking Methods Fin SS V
Banking Solutions For Improving Customer Man In The Middle Mobile Banking Attacking Methods Fin SS VThis slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. Deliver an outstanding presentation on the topic using this Banking Solutions For Improving Customer Man In The Middle Mobile Banking Attacking Methods Fin SS V. Dispense information and present a thorough explanation of Popular Cyberattack, Network Interception, Email Interception And Malware, Mobile Banking Attacking Methods using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Banking Applications Man In The Middle Mobile Banking Attacking Fin SS V
Mobile Banking Applications Man In The Middle Mobile Banking Attacking Fin SS VThis slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. Introducing Mobile Banking Applications Man In The Middle Mobile Banking Attacking Fin SS V to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Wifi Network Interception, Dns Spoofing, Email Interception, Malware, using this template. Grab it now to reap its full benefits.
-
 Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Man-in-the-Middle MITM Attacks in cyber terrorism. It includes mitigation startegies such as encryption, PKI, network security, 2FA and secure Wi-Fi.Introducing Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Account Security, Network Security, Encryption, using this template. Grab it now to reap its full benefits.
-
 Man In The Middle Attack Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Man In The Middle Attack Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Man in the middle attack colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Man In The Middle Attack Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Man In The Middle Attack Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Man in the middle attack monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 About Man In The Middle Phishing Scams Phishing Attacks And Strategies
About Man In The Middle Phishing Scams Phishing Attacks And StrategiesThis slide demonstrates the idea behind man in the middle phishing attacks. The purpose of this slide is to illustrate the concept of MITM attack by comparing normal scenario and MITM attack which includes attacker, proxy server, real website, etc.Present the topic in a bit more detail with this About Man In The Middle Phishing Scams Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Safe Authentication, Manipulate Sensitive, Communicating Directly. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Execution Of Man In The Middle Cyber S Phishing Attacks And Strategies
Execution Of Man In The Middle Cyber S Phishing Attacks And StrategiesThis slide illustrates the process of executing man in the middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc.Deliver an outstanding presentation on the topic using this Execution Of Man In The Middle Cyber S Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Data Transfer, Direct Interception, Password Protected using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Man In The Middle Mitm Phishing Attack Diagram Phishing Attacks And Strategies
Man In The Middle Mitm Phishing Attack Diagram Phishing Attacks And StrategiesThis slide demonstrates the working flow of man in the middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar.Present the topic in a bit more detail with this Man In The Middle Mitm Phishing Attack Diagram Phishing Attacks And Strategies. Use it as a tool for discussion and navigation on Experienced Data Breach, Exposed Financial, Man Middle Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Popular Man In The Middle Phishing Kits Phishing Attacks And Strategies
Popular Man In The Middle Phishing Kits Phishing Attacks And StrategiesThis slide outlines the various phishing kits used by attackers to conduct man in the middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and EvilProxy.Deliver an outstanding presentation on the topic using this Popular Man In The Middle Phishing Kits Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Instrumentation Stolen, Uniform Resource Locator, Expose Phishing Content using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Preventive Measures For Man In The Middle Phishing Attacks And Strategies
Preventive Measures For Man In The Middle Phishing Attacks And StrategiesThis slide outlines the various methods of preventing man in the middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.Introducing Preventive Measures For Man In The Middle Phishing Attacks And Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Connections, Avoid Phishing Emails, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber Attacks
Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber AttacksThis slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber Attacks. Dispense information and present a thorough explanation of Cyber Attacks, Intercepting User Traffic, Malicious Wi Fi Hotspots using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks
Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber AttacksThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks. This template helps you present information on four stages. You can also present information on Secure Connections, Avoid Phishing Emails, Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.



