Powerpoint Templates and Google slides for Key Cryptography
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 About Cryptography Overview And Key Objectives Cloud Cryptography
About Cryptography Overview And Key Objectives Cloud CryptographyThis slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Deliver an outstanding presentation on the topic using this About Cryptography Overview And Key Objectives Cloud Cryptography. Dispense information and present a thorough explanation of Confidentiality, Authentication, Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Benefits Of Cloud Computing Technology Cloud Cryptography
Key Benefits Of Cloud Computing Technology Cloud CryptographyThis slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Increase audience engagement and knowledge by dispensing information using Key Benefits Of Cloud Computing Technology Cloud Cryptography. This template helps you present information on eight stages. You can also present information on Collaborative, Cost Savings, Secured Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Features Of Encrypted Cloud Storage Cloud Cryptography
Key Features Of Encrypted Cloud Storage Cloud CryptographyThis slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Introducing Key Features Of Encrypted Cloud Storage Cloud Cryptography to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Encryption, Access Control, Collaboration, using this template. Grab it now to reap its full benefits.
-
 Key Uses And Applications Of Cryptographic Security Cloud Cryptography
Key Uses And Applications Of Cryptographic Security Cloud CryptographyThis slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Increase audience engagement and knowledge by dispensing information using Key Uses And Applications Of Cryptographic Security Cloud Cryptography. This template helps you present information on nine stages. You can also present information on Computer Security, Digital Currencies, Web Surfing Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets About Cryptography Overview And Key Features
Secure Your Digital Assets About Cryptography Overview And Key FeaturesThis slide discusses cryptography and its key features. The purpose of this slide is to highlight the overview of cryptography as it is the technology for protecting data and some features such as confidentiality, integrity, non- repudiation, etc. Introducing Secure Your Digital Assets About Cryptography Overview And Key Features to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Non Repudiation, Authentication, Encrypt Data And Communications, using this template. Grab it now to reap its full benefits.
-
 About Cryptography Overview And Key Features Crypto Wallets Types And Applications
About Cryptography Overview And Key Features Crypto Wallets Types And ApplicationsThis slide discusses cryptography and its key features. The purpose of this slide is to highlight the overview of cryptography as it is the technology for protecting data and some features such as confidentiality, integrity, non-repudiation, etc. Introducing About Cryptography Overview And Key Features Crypto Wallets Types And Applications to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Authentication, Cryptography, Integrity, using this template. Grab it now to reap its full benefits.
-
 Crypto Wallets Types And Applications Key Security Benefits Of Cryptography
Crypto Wallets Types And Applications Key Security Benefits Of CryptographyThis slide aims to highlight the advantages of cryptography in the market. This slide represents some benefits of crypto, such as access control, secure communication, protection against attacks, compliance with legal requirements, etc. Introducing Crypto Wallets Types And Applications Key Security Benefits Of Cryptography to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Protection Against Attacks, Compliance With Legal Requirements, Secure Communication, using this template. Grab it now to reap its full benefits.
-
 Digital Signature Creation Using Public Key Cryptography Encryption For Data Privacy In Digital Age It
Digital Signature Creation Using Public Key Cryptography Encryption For Data Privacy In Digital Age ItThis slide demonstrates the utilization of asymmetric encryption for generating digital signatures to authenticate documents. The purpose od this slide is to illustrate how digital signatures are created by employing hashing and asymmetric encryption techniques. Deliver an outstanding presentation on the topic using this Digital Signature Creation Using Public Key Cryptography Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Cryptography, Asymmetric, Document using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Benefits Of Using Cloud Cryptography Encryption For Data Privacy In Digital Age It
Key Benefits Of Using Cloud Cryptography Encryption For Data Privacy In Digital Age ItThis slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Present the topic in a bit more detail with this Key Benefits Of Using Cloud Cryptography Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Cloud Cryptography, Description, Data Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS
Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS. Use it as a tool for discussion and navigation on Potential Impact, Increased Speed, Improved User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Symmetric Key Cryptography Illustration
Symmetric Key Cryptography IllustrationThis custodial-themed PowerPoint icon features a vibrant color scheme and eye-catching design to represent techniques for symmetric key exchange. Perfect for presentations on data security and encryption, this icon will add a professional touch to your slides and grab the attention of your audience.
-
 Public Key Cryptography Example Ppt Powerpoint Presentation Layouts Template Cpb
Public Key Cryptography Example Ppt Powerpoint Presentation Layouts Template CpbPresenting our Public Key Cryptography Example Ppt Powerpoint Presentation Layouts Template Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Public Key Cryptography Example This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Quantum Cryptography Key Requirements Faithful Transmission Of Flying Qubits
Quantum Cryptography Key Requirements Faithful Transmission Of Flying QubitsThis slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data.Present the topic in a bit more detail with this Quantum Cryptography Key Requirements Faithful Transmission Of Flying Qubits. Use it as a tool for discussion and navigation on Entangled Qubits, Organizations Imagined, Reliable Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
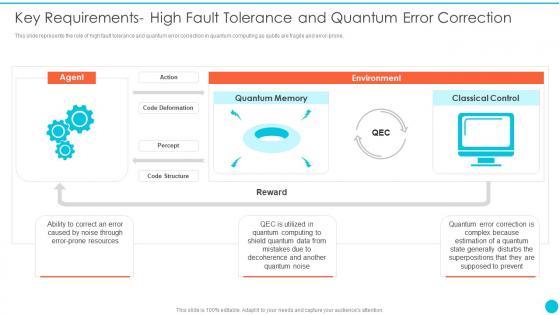 Quantum Cryptography Key Requirements High Fault Tolerance And Quantum Error Correction
Quantum Cryptography Key Requirements High Fault Tolerance And Quantum Error CorrectionThis slide represents the role of high fault tolerance and quantum error correction in quantum computing as qubits are fragile and error prone.Deliver an outstanding presentation on the topic using this Quantum Cryptography Key Requirements High Fault Tolerance And Quantum Error Correction. Dispense information and present a thorough explanation of Quantum Memory, Classical Control, Quantum Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
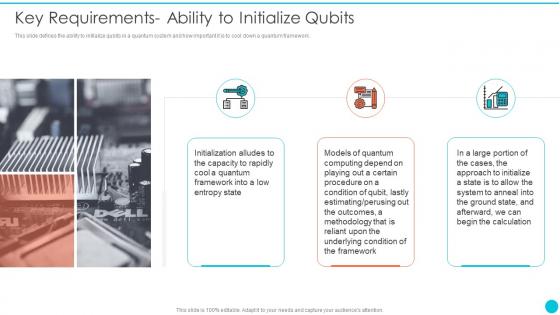 Key Requirements Ability To Initialize Qubits Quantum Cryptography
Key Requirements Ability To Initialize Qubits Quantum CryptographyThis slide defines the ability to initialize qubits in a quantum system and how important it is to cool down a quantum framework.Deliver an outstanding presentation on the topic using this Key Requirements Ability To Initialize Qubits Quantum Cryptography Dispense information and present a thorough explanation of Underlying Condition, Estimating Perusing, Models Of Quantum using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
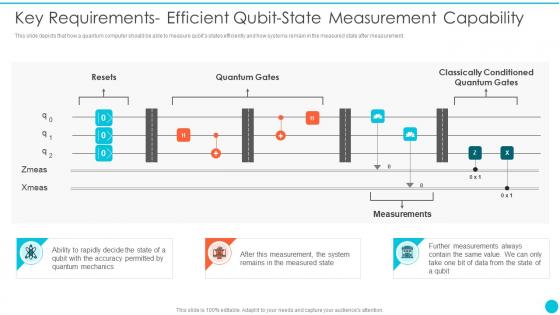 Key Requirements Efficient Qubit State Measurement Capability Quantum Cryptography
Key Requirements Efficient Qubit State Measurement Capability Quantum CryptographyThis slide depicts that how a quantum computer should be able to measure qubits states efficiently and how systems remain in the measured state after measurement.Present the topic in a bit more detail with this Key Requirements Efficient Qubit State Measurement Capability Quantum Cryptography Use it as a tool for discussion and navigation on Quantum Gates, Classically Conditioned, Measurement System This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Requirements For Quantum Computing Quantum Cryptography
Key Requirements For Quantum Computing Quantum CryptographyThis slide depicts the critical requirements for quantum computing such as long coherence time, high scalability, universal quantum gates, efficient qubit state measurement capability, etc.Present the topic in a bit more detail with this Key Requirements For Quantum Computing Quantum Cryptography Use it as a tool for discussion and navigation on Universal Quantum, Faithful Transmission, Initialize Qubits This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Requirements High Scalability Quantum Cryptography
Key Requirements High Scalability Quantum CryptographyThis slide depicts the idea of high scalability in quantum computing which means that quantum computers should be able to process increased demands.Present the topic in a bit more detail with this Key Requirements High Scalability Quantum Cryptography Use it as a tool for discussion and navigation on Quantum Computers, Measurements Might, Developed Dramatically This template is free to edit as deemed fit for your organization. Therefore download it now.
-
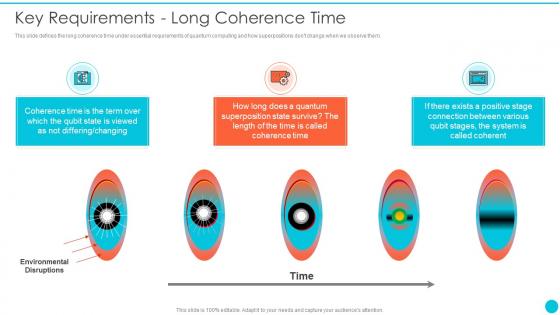 Key Requirements Long Coherence Time Quantum Cryptography
Key Requirements Long Coherence Time Quantum CryptographyThis slide defines the long coherence time under essential requirements of quantum computing and how superpositions dont change when we observe them.Deliver an outstanding presentation on the topic using this Key Requirements Long Coherence Time Quantum Cryptography Dispense information and present a thorough explanation of Differing Changing, Connection Between, Called Coherent using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
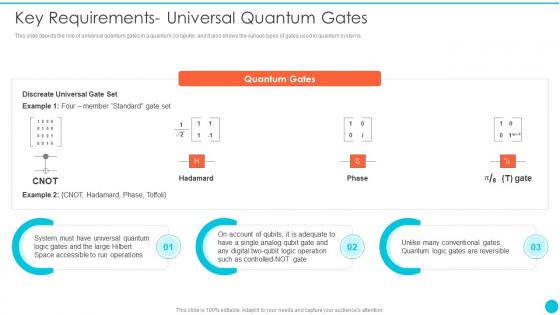 Key Requirements Universal Quantum Gates Quantum Cryptography
Key Requirements Universal Quantum Gates Quantum CryptographyThis slide depicts the role of universal quantum gates in a quantum computer, and it also shows the various types of gates used in quantum systems.Present the topic in a bit more detail with this Key Requirements Universal Quantum Gates Quantum Cryptography Use it as a tool for discussion and navigation on Quantum Gates, Conventional Gates, Universal Quantum This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Characteristics Of Blockchain Architecture Cryptographic Ledger
Key Characteristics Of Blockchain Architecture Cryptographic LedgerThis slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency.Present the topic in a bit more detail with this Key Characteristics Of Blockchain Architecture Cryptographic Ledger. Use it as a tool for discussion and navigation on Cryptography, Immutability, Decentralization . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Elements Of Blockchain Technology Cryptographic Ledger
Key Elements Of Blockchain Technology Cryptographic LedgerThis slide depicts the vital elements of blockchain technology, namely distributed ledger technology, immutable records, and smart contracts used for fast transactions.Increase audience engagement and knowledge by dispensing information using Key Elements Of Blockchain Technology Cryptographic Ledger. This template helps you present information on three stages. You can also present information on Ledger Technology, Immutable Records, Smart Contracts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Public Key Cryptography In Powerpoint And Google Slides Cpb
Public Key Cryptography In Powerpoint And Google Slides CpbPresenting Public Key Cryptography In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Public Key Cryptography. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cryptographic Technology Key Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cryptographic Technology Key Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cryptographic technology key colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cryptographic Technology Key Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cryptographic Technology Key Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cryptographic technology key monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Encryption Cryptography Keys And Lock Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Cryptography Keys And Lock Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon shows an encryption key and lock, symbolising the security of data. It is a perfect visual to represent the concept of encryption and data protection, making it ideal for presentations on cyber security.
-
 Encryption Cryptography Keys And Lock Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Cryptography Keys And Lock Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of encryption keys and locks. It is perfect for illustrating the concept of security and data protection. It is a simple yet powerful image that will help to convey the importance of encryption in any presentation.
-
 Key Tactics Involved In Implementing Blockchain Cryptography
Key Tactics Involved In Implementing Blockchain CryptographyThe purpose of this slide is to represent best practices to implement cryptography to enhance data security. It covers various tactics such as securing development cryptography, using established cryptography, encrypting data and using key management. Presenting our set of slides with Key Tactics Involved In Implementing Blockchain Cryptography. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Development Cryptography, Established Cryptography.
-
 Key Elements Of Blockchain Technology Cryptographic Ledger IT
Key Elements Of Blockchain Technology Cryptographic Ledger ITThis slide depicts the vital elements of blockchain technology, namely distributed ledger technology, immutable records, and smart contracts used for fast transactions.Increase audience engagement and knowledge by dispensing information using Key Elements Of Blockchain Technology Cryptographic Ledger IT. This template helps you present information on three stages. You can also present information on Distributed Ledger, Immutable Records, Smart Contracts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cryptographic Ledger It Key Characteristics Of Blockchain Architecture
Cryptographic Ledger It Key Characteristics Of Blockchain ArchitectureThis slide depicts the critical characteristics of blockchain architecture, namely cryptography, immutability, provenance, decentralization, anonymity, and transparency. Present the topic in a bit more detail with this Cryptographic Ledger It Key Characteristics Of Blockchain Architecture. Use it as a tool for discussion and navigation on Confirmation Among, Decentralization, Transparency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Private key cryptography ppt powerpoint presentation layouts icon cpb
Private key cryptography ppt powerpoint presentation layouts icon cpbPresenting Private Key Cryptography Ppt Powerpoint Presentation Layouts Icon Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Private Key Cryptography. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.



