Powerpoint Templates and Google slides for IT Security Technology
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
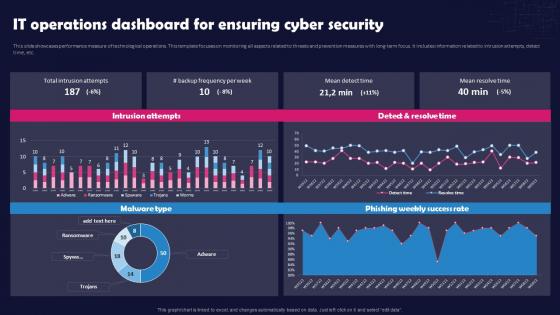 Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security
Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber SecurityThis slide showcases performance measure of technological operations. This template focuses on monitoring all aspects related to threats and prevention measures with long-term focus. It includes information related to intrusion attempts, detect time, etc. Present the topic in a bit more detail with this Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security. Use it as a tool for discussion and navigation on IT Operations Dashboard, Ensuring Cyber Security, Threats And Prevention, Technological Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improving Security By Green Computing Technology Green IT
Improving Security By Green Computing Technology Green ITThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Deliver an outstanding presentation on the topic using this Improving Security By Green Computing Technology Green IT. Dispense information and present a thorough explanation of Technology, Computing, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It
Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role of HTTPS in encrypting web communication and use of the Secure Sockets Layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake. Deliver an outstanding presentation on the topic using this Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Technology, Asymmetric, Symmetric using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internet Gateway Security IT Future Of Secure Web Gateway Technology
Internet Gateway Security IT Future Of Secure Web Gateway TechnologyThis slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. Introducing Internet Gateway Security IT Future Of Secure Web Gateway Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sales Are Predicted, SWG Market Anticipated, Security Solution, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Introduction To Secure Web Gateway Technology
Internet Gateway Security IT Introduction To Secure Web Gateway TechnologyThis slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Introducing Internet Gateway Security IT Introduction To Secure Web Gateway Technology to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, Application Control, Website Content Inspection, Data Loss Prevention, using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS
Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SSThis slide represents comparison between IT security awareness training tools based on features such as audio mixing, text animation, time mapping, titles and captions etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS. Dispense information and present a thorough explanation of Time Mapping, Text Animation, Tram Reviews, Security Awareness Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Prepare And Deploy Strong It Policies
Information Technology Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Information Technology Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong IT Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Security Technology User Market
IT Security Technology User MarketThe following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Introducing our IT Security Technology User Market set of slides. The topics discussed in these slides are IT Security Technology, User Market. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 F58 Reverse Proxy It Reverse Proxy Server Side Technology Security
F58 Reverse Proxy It Reverse Proxy Server Side Technology SecurityThis slide explains the reverse proxy server side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. Deliver an outstanding presentation on the topic using this F58 Reverse Proxy It Reverse Proxy Server Side Technology Security. Dispense information and present a thorough explanation of Security Proxy, Technology, Transmitted Securely using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 5 Operational Technology Security Controls To Improve It Security
5 Operational Technology Security Controls To Improve It SecurityFollowing slide depict operational technology OT security controls ways that can be used by an organization. Organization can enhance the security of IT infrastructure by using security controls such as update asset inventory, training, managing portable media, backup and restore and implementing secure configuration. Present the topic in a bit more detail with this 5 Operational Technology Security Controls To Improve IT Security. Use it as a tool for discussion and navigation on Update Asset Inventory, Training Manage, Portable Media, Backup And Restore, Secure Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security It Infrastructure Information Budget For Fy2022
Information Technology Security It Infrastructure Information Budget For Fy2022This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Present the topic in a bit more detail with this Information Technology Security It Infrastructure Information Budget For Fy2022. Use it as a tool for discussion and navigation on Infrastructure, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security What Is Information Technology Security And How Does It Work
Information Technology Security What Is Information Technology Security And How Does It WorkThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing Information Technology Security What Is Information Technology Security And How Does It Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
 Blockchain technology it is blockchain technology secure
Blockchain technology it is blockchain technology secureThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Introducing Blockchain Technology It Is Blockchain Technology Secure to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain, Technology, Secure, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it technological assessment of firm current
Enhancing overall project security it technological assessment of firm currentThis slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Enhancing Overall Project Security It Technological Assessment Of Firm Current. Use it as a tool for discussion and navigation on Technological, Assessment, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Effective It Security Tools For Protection Against Insider Threat
Most Effective It Security Tools For Protection Against Insider ThreatThis slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM Introducing our premium set of slides with Most Effective It Security Tools For Protection Against Insider Threat. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Loss Prevention, User Entity Behavior, Identity Access Management. So download instantly and tailor it with your information.
-
 IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems
IT Security Residual Risk Matrix With Risk Management Guide For Information Technology SystemsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver an outstanding presentation on the topic using this IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Database Access, Evaluation Question, Response Action using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure
Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt BrochureThis slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure. This template helps you present information on one stage. You can also present information on Tools For Confidentiality, Tools For Integrity, Tools For Availability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Network It Security Automation Security Automation In Information Technology
Enterprise Network It Security Automation Security Automation In Information TechnologyThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Orchestrating Network Security, Security Policy Automation, Infrastructure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Why To Automate The It Security Process Security Automation In Information Technology
Why To Automate The It Security Process Security Automation In Information TechnologyThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Automation In Information Technology. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Digital Ledger It Is Blockchain Technology Secure Ppt Styles Professional
Digital Ledger It Is Blockchain Technology Secure Ppt Styles ProfessionalThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Increase audience engagement and knowledge by dispensing information using Digital Ledger It Is Blockchain Technology Secure Ppt Styles Professional. This template helps you present information on five stages. You can also present information on Blockchain Technology Secure, Secure Mechanism, Operations Database using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Architecture In 5G Technology Working Of 5G Technology IT Ppt Topics
Security Architecture In 5G Technology Working Of 5G Technology IT Ppt TopicsThis slide represents the security architecture in 5G technology, including the system wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Present the topic in a bit more detail with this Security Architecture In 5G Technology Working Of 5G Technology IT Ppt Topics. Use it as a tool for discussion and navigation on Security Architecture, Technology, Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security In 5G Technology Architecture Working Of 5G Technology IT Ppt Ideas
Security In 5G Technology Architecture Working Of 5G Technology IT Ppt IdeasThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Increase audience engagement and knowledge by dispensing information using Security In 5G Technology Architecture Working Of 5G Technology IT Ppt Ideas. This template helps you present information on five stages. You can also present information on Mobile Technologys, Service, Delivery Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Is Blockchain Technology Secure Cryptographic Ledger IT
Is Blockchain Technology Secure Cryptographic Ledger ITThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain.Present the topic in a bit more detail with this Is Blockchain Technology Secure Cryptographic Ledger IT. Use it as a tool for discussion and navigation on Generated Math Algorithms, Weaknesses Blockchain, Networks Nevertheless. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V
Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Present the topic in a bit more detail with this Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Assessment, Technology, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prerequisites For Technology Leaders To Ensure Strategic Plan To Secure It Infrastructure Strategy SS V
Prerequisites For Technology Leaders To Ensure Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding IT professionals prerequisites to enable firm and IT success. The technology leaders include CIO, IT head, strategy team by highlighting their collaborative initiatives. Deliver an outstanding presentation on the topic using this Prerequisites For Technology Leaders To Ensure Strategic Plan To Secure It Infrastructure Strategy SS V. Dispense information and present a thorough explanation of Technology, Organizational, Success using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall technology infrastructure icon for business it security
Firewall technology infrastructure icon for business it securityPresenting this set of slides with name Firewall Technology Infrastructure Icon For Business IT Security. This is a three stage process. The stages in this process are Firewall Technology Infrastructure Icon For Business IT Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Five years enterprise it technology road mapping with security and compliance
Five years enterprise it technology road mapping with security and compliancePresenting Five Years Enterprise IT Technology Road Mapping With Security And Compliance PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
 Half yearly enterprise it technology road mapping with security and compliance
Half yearly enterprise it technology road mapping with security and compliancePresenting Half Yearly Enterprise IT Technology Road Mapping With Security And Compliance PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Quarterly enterprise it technology road mapping with security and compliance
Quarterly enterprise it technology road mapping with security and compliancePresenting Quarterly Enterprise IT Technology Road Mapping With Security And Compliance PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
 Six months enterprise it technology road mapping with security and compliance
Six months enterprise it technology road mapping with security and compliancePresenting Six Months Enterprise IT Technology Road Mapping With Security And Compliance PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Three months enterprise it technology road mapping with security and compliance
Three months enterprise it technology road mapping with security and compliancePresenting Three Months Enterprise IT Technology Road Mapping With Security And Compliance PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Devops tools selection process it addressing different categories of devops tools security ppt slide
Devops tools selection process it addressing different categories of devops tools security ppt slideThis slide provides information regarding different categories of DevOps tools such as DevOps ready, DevOps enabled and DevOps capable. Introducing Devops Tools Selection Process It Addressing Different Categories Of Devops Tools Security Ppt Slide to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on DevOps Ready, DevOps Enabled, DevOps Capable, Assessment Process, configuration automation, using this template. Grab it now to reap its full benefits.
-
 Tools used in cloud security cloud security it ppt inspiration
Tools used in cloud security cloud security it ppt inspirationThis slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Introducing Tools Used In Cloud Security Cloud Security It Ppt Inspiration to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Tools Used In Cloud Security, using this template. Grab it now to reap its full benefits.
-
 It security operations various technologies for effective secops process ppt elements
It security operations various technologies for effective secops process ppt elementsThis slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Introducing IT Security Operations Various Technologies For Effective Secops Process Ppt Elements to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Basic Tools, Advanced Tools, using this template. Grab it now to reap its full benefits.
-
 Where the company will use its funds technology security ppt model smartart
Where the company will use its funds technology security ppt model smartartThe slide provides the details about use of fund which the company will raise from ICO Initial Coin Offering. The company spend its funding amount on website and app development new technology and security expansions etc. Present the topic in a bit more detail with this Where The Company Will Use Its Funds Technology Security Ppt Model Smartart. Use it as a tool for discussion and navigation on Development, Technology, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.



