Powerpoint Templates and Google slides for IT Security Process
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
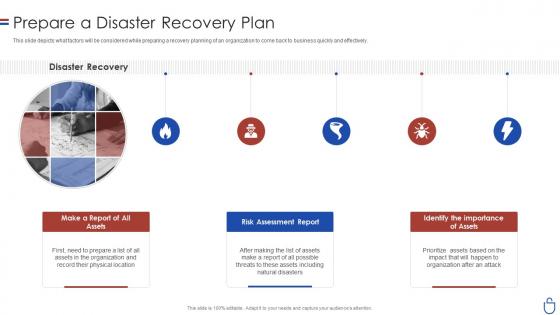 Data security it prepare a disaster recovery plan ppt slides rules
Data security it prepare a disaster recovery plan ppt slides rulesThis slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Introducing Data Security IT Prepare A Disaster Recovery Plan Ppt Slides Rules to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Disaster Recovery, Make Report Assets, Risk Assessment Report Assets, Identify importance, using this template. Grab it now to reap its full benefits.
-
 Data security it process of disaster recovery planning ppt slides download
Data security it process of disaster recovery planning ppt slides downloadThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Data Security IT Process Of Disaster Recovery Planning Ppt Slides Download to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Approval, Create Disaster, Recovery Team, Perform, Risk Analysis, Prioritize Procedures And Operations, Define Recovery Plans, using this template. Grab it now to reap its full benefits.
-
 Security Patch Management Process For Healthcare IT Systems
Security Patch Management Process For Healthcare IT SystemsFollowing slide showcases the healthcare industry security patch management process. The purpose of this slide is to help healthcare organizations in ensuring that their IT systems are patched safely and effectively. It includes steps such as define, identify and prioritize, etc.Presenting our set of slides with Security Patch Management Process For Healthcare IT Systems. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Roles Responsibilities, Ensure Introduced, Deployment Depends.
-
 Utilization Of Triage Cyber Security Process In It
Utilization Of Triage Cyber Security Process In ItThis slide represents utilization of triage cyber security process in IT which assists to handle large number of tickets and increases help desk efficiency. It includes utilization of triage cyber security process in IT such as IT operations, email, etc Presenting our set of slides with name Utilization Of Triage Cyber Security Process In It This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Software Testing, Agile Software Development, IT Operations
-
 Information security process key initiatives for project safety it ppt gallery example
Information security process key initiatives for project safety it ppt gallery exampleThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Information Security Process Key Initiatives For Project Safety It Ppt Gallery Example. Use it as a tool for discussion and navigation on Process, Information, Dynamic, System, Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security process to manage firms project safety management it
Information security process to manage firms project safety management itThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Information Security Process To Manage Firms Project Safety Management It. Use it as a tool for discussion and navigation on Security, Network, Employees, Dynamic, System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reverse Proxy It Process Of Secure Reverse Proxying
Reverse Proxy It Process Of Secure Reverse ProxyingThis slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Increase audience engagement and knowledge by dispensing information using Reverse Proxy It Process Of Secure Reverse Proxying. This template helps you present information on five stages. You can also present information on Process Of Secure Reverse Proxying using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improve it security with vulnerability information and event management logging process
Improve it security with vulnerability information and event management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Improve It Security With Vulnerability Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 It Security Audit With Risk Level Procedure To Perform Digital Marketing Audit
It Security Audit With Risk Level Procedure To Perform Digital Marketing AuditThis slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Present the topic in a bit more detail with this It Security Audit With Risk Level Procedure To Perform Digital Marketing Audit. Use it as a tool for discussion and navigation on Inactive User Accounts, Inactive Computer Accounts, Empty Security Groups. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Why To Automate The It Security Process Security Automation To Investigate And Remediate Cyberthreats
Why To Automate The It Security Process Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Introducing Why To Automate The It Security Process Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Better Threat Detection, Faster Containment, Improve Productivity, using this template. Grab it now to reap its full benefits.
-
 Why To Automate The It Security Process Security Automation In Information Technology
Why To Automate The It Security Process Security Automation In Information TechnologyThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Automation In Information Technology. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
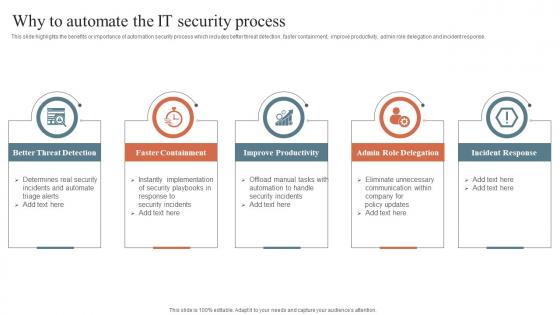 Why To Automate The It Security Process Security Orchestration Automation And Response Guide
Why To Automate The It Security Process Security Orchestration Automation And Response GuideThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Orchestration Automation And Response Guide. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
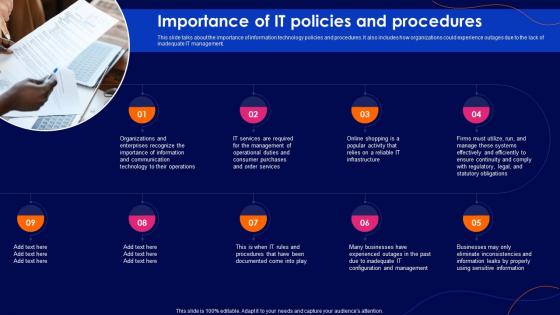 Cyber Security Policy Importance Of It Policies And Procedures
Cyber Security Policy Importance Of It Policies And ProceduresThis slide talks about the importance of information technology policies and procedures. It also includes how organizations could experience outages due to the lack of inadequate IT management. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Importance Of It Policies And Procedures. This template helps you present information on nine stages. You can also present information on Services, Operational, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy What Happens In The Absence Of It Policies And Procedures
Cyber Security Policy What Happens In The Absence Of It Policies And ProceduresThis slide represents the consequences of not having IT policies and procedures. Effects include disrupted and inconsistent operational duties, communication gaps between staff and employees, etc. Introducing Cyber Security Policy What Happens In The Absence Of It Policies And Procedures to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Procedures, Information, Corporations, using this template. Grab it now to reap its full benefits.
-
 SDN Security IT Implementation Process Of Software Defined Networking SDN
SDN Security IT Implementation Process Of Software Defined Networking SDNThis slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. Increase audience engagement and knowledge by dispensing information using SDN Security IT Implementation Process Of Software Defined Networking SDN. This template helps you present information on four stages. You can also present information on Process, Implementation, Software using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration
SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint DemonstrationThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration. This template helps you present information on one stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
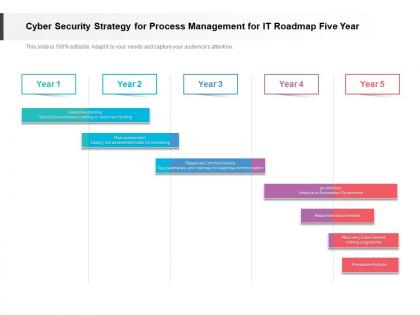 Cyber security strategy for process management for it roadmap five year
Cyber security strategy for process management for it roadmap five yearPresenting Cyber Security Strategy For Process Management For IT Roadmap Five Year PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap four quarter
Cyber security strategy for process management for it roadmap four quarterPresenting Cyber Security Strategy For Process Management For IT Roadmap Four Quarter PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
-
 Cyber security strategy for process management for it roadmap half yearly
Cyber security strategy for process management for it roadmap half yearlyPresenting Cyber Security Strategy For Process Management For IT Roadmap Half Yearly PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
 Cyber security strategy for process management for it roadmap six months
Cyber security strategy for process management for it roadmap six monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Six Months PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Cyber security strategy for process management for it roadmap three months
Cyber security strategy for process management for it roadmap three monthsPresenting Cyber Security Strategy For Process Management For IT Roadmap Three Months PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
-
 Process of disaster recovery planning cyber security it ppt powerpoint presentation styles
Process of disaster recovery planning cyber security it ppt powerpoint presentation stylesThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Process Of Disaster Recovery Planning Cyber Security IT Ppt Powerpoint Presentation Styles to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Approval, Plan Testing, Data Collection, Recovery Plans, Perform Risk Analysis, using this template. Grab it now to reap its full benefits.
-
 Costs incurred to process faulty cybersecurity transactions overcome the it security
Costs incurred to process faulty cybersecurity transactions overcome the it securityThis slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an outstanding presentation on the topic using this Costs Incurred To Process Faulty Cybersecurity Transactions Overcome The It Security. Dispense information and present a thorough explanation of Costs Incurred To Process Faulty Cybersecurity Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline process overcome the it security
Timeline process overcome the it securityIncrease audience engagement and knowledge by dispensing information using Timeline Process Overcome The It Security. This template helps you present information on five stages. You can also present information on Timeline Process 2017 To 2021 using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devops tools selection process it addressing different categories of devops tools security ppt slide
Devops tools selection process it addressing different categories of devops tools security ppt slideThis slide provides information regarding different categories of DevOps tools such as DevOps ready, DevOps enabled and DevOps capable. Introducing Devops Tools Selection Process It Addressing Different Categories Of Devops Tools Security Ppt Slide to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on DevOps Ready, DevOps Enabled, DevOps Capable, Assessment Process, configuration automation, using this template. Grab it now to reap its full benefits.
-
 It security program management ppt powerpoint presentation outline rules cpb
It security program management ppt powerpoint presentation outline rules cpbPresenting this set of slides with name IT Security Program Management Ppt Powerpoint Presentation Outline Rules Cpb. This is an editable Powerpoint one stages graphic that deals with topics like IT Security Program Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Agenda for cloud security cloud security it ppt rules
Agenda for cloud security cloud security it ppt rulesIncrease audience engagement and knowledge by dispensing information using Agenda For Cloud Security Cloud Security IT Ppt Rules. This template helps you present information on six stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud security checklist policies and procedures cloud security it ppt tips
Cloud security checklist policies and procedures cloud security it ppt tipsThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Introducing Cloud Security Checklist Policies And Procedures Cloud Security IT Ppt Tips to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Considering Cloud Security, Procedures Strictly In The Organization, Security, using this template. Grab it now to reap its full benefits.
-
 Cloud security it icons slide ppt rules
Cloud security it icons slide ppt rulesIntroducing our well researched set of slides titled Cloud Security IT Icons Slide Ppt Rules. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Cloud security threats compliance violations cloud security it ppt rules
Cloud security threats compliance violations cloud security it ppt rulesThis slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Compliance Violations Cloud Security IT Ppt Rules. This template helps you present information on one stage. You can also present information on Businesses Can Rapidly, Serious Repercussions, Authentication Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Essential pillars of cloud security cloud security it ppt rules
Essential pillars of cloud security cloud security it ppt rulesThis slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Introducing Essential Pillars Of Cloud Security Cloud Security IT Ppt Rules to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Visibility And Consistency, Process Based Security, Network Security, using this template. Grab it now to reap its full benefits.
-
 How does cloud security work governance cloud security it ppt rules
How does cloud security work governance cloud security it ppt rulesThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Security IT Ppt Rules. This template helps you present information on five stages. You can also present information on Knowledge, Owner Ship, Accessibility using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How does cloud security work legal compliance cloud security it ppt rules
How does cloud security work legal compliance cloud security it ppt rulesThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Legal Compliance Cloud Security IT Ppt Rules. This template helps you present information on eight stages. You can also present information on Governance, Regulations, Transparency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars of cloud security process based security cloud security it ppt brochure
Pillars of cloud security process based security cloud security it ppt brochureThis slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take.Introducing Pillars Of Cloud Security Process Based Security Cloud Security IT Ppt Brochure to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Running Inside The Cloud, Vulnerability Management, Noxious Movement using this template. Grab it now to reap its full benefits.
-
 It security operations various technologies for effective secops process ppt elements
It security operations various technologies for effective secops process ppt elementsThis slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Introducing IT Security Operations Various Technologies For Effective Secops Process Ppt Elements to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Basic Tools, Advanced Tools, using this template. Grab it now to reap its full benefits.
-
 Seven Step Process To Conduct IT Security Audit
Seven Step Process To Conduct IT Security AuditThis slide shows seven-step process to conduct IT security in an organization. The purpose of this slide is to provide businesses understanding regarding auditing procedures to protect digital assets from data losses. It covers steps such as setting goals, evaluating existing policies, determining technologies, implementing change management policy, etc. Introducing our premium set of slides with Seven Step Process To Conduct IT Security Audit. Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Creates Detailed, External Audits. So download instantly and tailor it with your information.



