Powerpoint Templates and Google slides for IT Risk Control
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
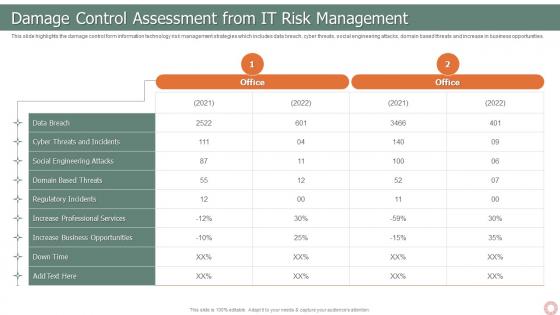 IT Risk Management Strategies Damage Control Assessment From IT Risk Management
IT Risk Management Strategies Damage Control Assessment From IT Risk ManagementThis slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Present the topic in a bit more detail with this IT Risk Management Strategies Damage Control Assessment From IT Risk Management. Use it as a tool for discussion and navigation on Data Breach, Social Engineering Attacks, Domain Based Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies Detection And Prevention Of Management Security Controls
IT Risk Management Strategies Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Introducing IT Risk Management Strategies Detection And Prevention Of Management Security Controls to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Management, Security Controls, Detection Management, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Strategies Detection And Prevention Of Operational Controls
IT Risk Management Strategies Detection And Prevention Of Operational ControlsThis slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Detection And Prevention Of Operational Controls. This template helps you present information on two stages. You can also present information on Motion Detectors, Circuit Television Monitoring, System Sensors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Risk Management Strategies Identification And Recovery Of Technical Controls
IT Risk Management Strategies Identification And Recovery Of Technical ControlsThis slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Introducing IT Risk Management Strategies Identification And Recovery Of Technical Controls to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Audit, IT Intrusion Identification, Proof Wholeness, Recover Secure State, Virus Eradication, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Strategies Preventive IT Technical Control Measures
IT Risk Management Strategies Preventive IT Technical Control MeasuresThe following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Introducing IT Risk Management Strategies Preventive IT Technical Control Measures to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Enable Control Enforcement, Secured Communications, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Strategies Residual Risk From IT Control Measures
IT Risk Management Strategies Residual Risk From IT Control MeasuresThis slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Present the topic in a bit more detail with this IT Risk Management Strategies Residual Risk From IT Control Measures. Use it as a tool for discussion and navigation on Residual Risk, Enhanced Controls, Implementation Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies Security Criteria And Control Measures For IT System Vulnerabilities
IT Risk Management Strategies Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing IT Risk Management Strategies Security Criteria And Control Measures For It System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
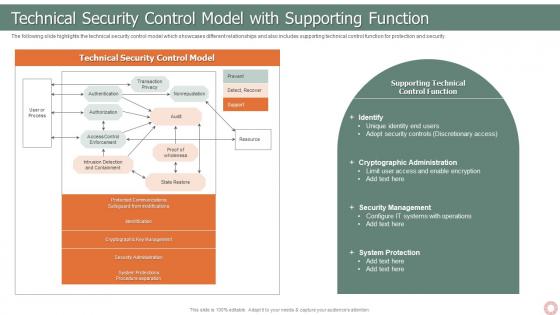 IT Risk Management Strategies Technical Security Control Model With Supporting Function
IT Risk Management Strategies Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing IT Risk Management Strategies Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technical Security, Control Model, Transaction Privacy, State Restore, using this template. Grab it now to reap its full benefits.
-
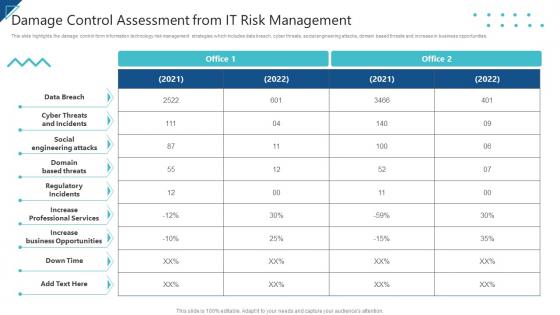 Enterprise Risk Management Damage Control Assessment From IT Risk Management
Enterprise Risk Management Damage Control Assessment From IT Risk ManagementThis slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Present the topic in a bit more detail with this Enterprise Risk Management Damage Control Assessment From IT Risk Management. Use it as a tool for discussion and navigation on Data Breach, Social Engineering Attacks, Domain Based Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Preventive IT Technical Control Measures
Enterprise Risk Management Preventive IT Technical Control MeasuresThe following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Introducing Enterprise Risk Management Preventive IT Technical Control Measures to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Enable Control Enforcement, Secured Communications, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Residual Risk From IT Control Measures Ppt Slides Mackup
Enterprise Risk Management Residual Risk From IT Control Measures Ppt Slides MackupThis slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Deliver an outstanding presentation on the topic using this Enterprise Risk Management Residual Risk From IT Control Measures Ppt Slides Mackup. Dispense information and present a thorough explanation of Residual Risk, Enhanced Controls, Implementation Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities
Enterprise Risk Management Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Damage Control Assessment From IT Risk Management Guide For Information Technology Systems
Damage Control Assessment From IT Risk Management Guide For Information Technology SystemsThis slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business. Present the topic in a bit more detail with this Damage Control Assessment From IT Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Data Breach, Social Engineering Attacks, Domain Based Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risks Safeguard Implementation Plan With Recommended Controls
IT Risks Safeguard Implementation Plan With Recommended ControlsThis slide highlights the information technology safeguard implementation plan in tabular format which includes risks, recommended controls, selected controls. Required resources and risk level. Present the topic in a bit more detail with this IT Risks Safeguard Implementation Plan With Recommended Controls. Use it as a tool for discussion and navigation on Risk Level, Recommended Controls, Required Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Preventive IT Technical Control Measures Risk Management Guide For Information Technology Systems
Preventive IT Technical Control Measures Risk Management Guide For Information Technology SystemsThe following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Introducing Preventive IT Technical Control Measures Risk Management Guide For Information Technology Systems to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Enable Control Enforcement, using this template. Grab it now to reap its full benefits.
-
 Residual Risk From IT Control Risk Management Guide For Information Technology Systems
Residual Risk From IT Control Risk Management Guide For Information Technology SystemsDeliver an outstanding presentation on the topic using this Residual Risk From IT Control Risk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Residual Risk, Minimize Threats, Control Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
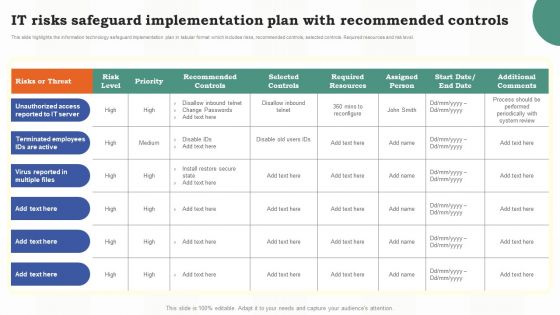 Risk Assessment Of It Systems It Risks Safeguard Implementation Plan With Recommended Controls
Risk Assessment Of It Systems It Risks Safeguard Implementation Plan With Recommended ControlsThis slide highlights the information technology safeguard implementation plan in tabular format which includes risks, recommended controls, selected controls. Required resources and risk level. Present the topic in a bit more detail with this Risk Assessment Of It Systems It Risks Safeguard Implementation Plan With Recommended Controls. Use it as a tool for discussion and navigation on Implementation, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities
Risk Assessment Of It Systems Security Criteria And Control Measures For It System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Deliver an outstanding presentation on the topic using this Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities. Dispense information and present a thorough explanation of Management Security, Operational Security, Technical Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
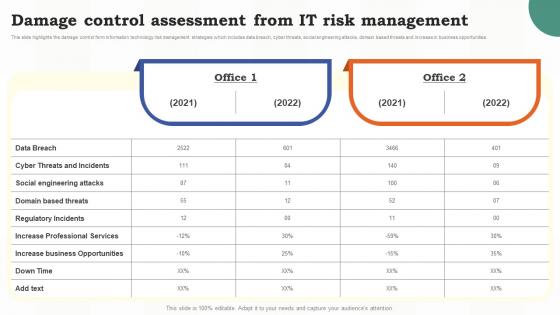 Damage Control Assessment From It Risk Management Risk Assessment Of It Systems
Damage Control Assessment From It Risk Management Risk Assessment Of It SystemsThis slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Present the topic in a bit more detail with this Damage Control Assessment From It Risk Management Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Assessment, Risk Management, Business Opportunities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Detection And Prevention Of Operational Controls Risk Assessment Of It Systems
Detection And Prevention Of Operational Controls Risk Assessment Of It SystemsThis slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. Deliver an outstanding presentation on the topic using this Detection And Prevention Of Operational Controls Risk Assessment Of It Systems. Dispense information and present a thorough explanation of Distribution, Control Measures, Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Preventive It Technical Control Measures Risk Assessment Of It Systems Ppt Slides Influencers
Preventive It Technical Control Measures Risk Assessment Of It Systems Ppt Slides InfluencersThe following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Increase audience engagement and knowledge by dispensing information using Preventive It Technical Control Measures Risk Assessment Of It Systems Ppt Slides Influencers. This template helps you present information on six stages. You can also present information on Authentication, Nonrepudiation, Secured Transactions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
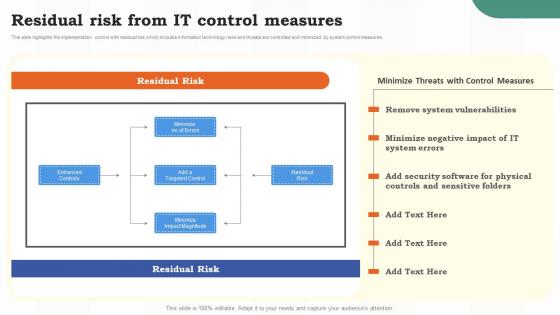 Residual Risk From It Control Measures Risk Assessment Of It Systems Ppt Slides Inspiration
Residual Risk From It Control Measures Risk Assessment Of It Systems Ppt Slides InspirationThis slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Deliver an outstanding presentation on the topic using this Residual Risk From It Control Measures Risk Assessment Of It Systems Ppt Slides Inspiration. Dispense information and present a thorough explanation of Security Software, Sensitive Folders, Physical using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment Of It Systems Detection And Prevention Of Management Security Controls
Risk Assessment Of It Systems Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Present the topic in a bit more detail with this Risk Assessment Of It Systems Detection And Prevention Of Management Security Controls. Use it as a tool for discussion and navigation on Prevention, Management, Security Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment Of It Systems Identification And Recovery Of Technical Controls
Risk Assessment Of It Systems Identification And Recovery Of Technical ControlsThis slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Introducing Risk Assessment Of It Systems Identification And Recovery Of Technical Controls to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identification, Technical Controls, Intrusion Identification, using this template. Grab it now to reap its full benefits.
-
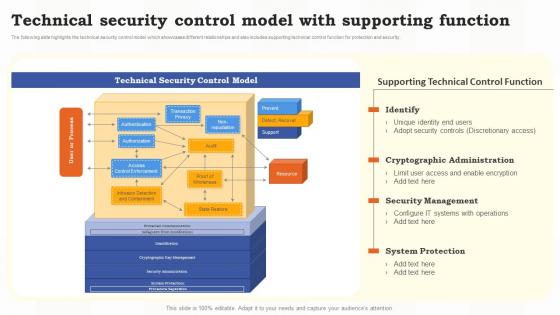 Technical Security Control Model With Supporting Function Risk Assessment Of It Systems
Technical Security Control Model With Supporting Function Risk Assessment Of It SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Supporting Function Risk Assessment Of It Systems. Dispense information and present a thorough explanation of Technical, Security Management, System Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 End user computing it controlling potential risks of end user computing ppt deck
End user computing it controlling potential risks of end user computing ppt deckThis slide represents the controlling the potential risks of end user computing by establishing and evaluating companys end user computing risks and threats in advance. Introducing End User Computing IT Controlling Potential Risks Of End User Computing Ppt Deck to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluate, Measures, Monitoring, Exception, using this template. Grab it now to reap its full benefits.



