Powerpoint Templates and Google slides for Integrate Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security and operations integration powerpoint presentation slides
Security and operations integration powerpoint presentation slidesPresenting our security and operations integration PowerPoint presentation slides. This PowerPoint design contains fifty-three slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. You can download this PPT layout from below.
-
 Threat Intelligence Integration In Endpoint Security Training Ppt
Threat Intelligence Integration In Endpoint Security Training PptPresenting Threat Intelligence Integration in Endpoint Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Firewall Network Security Steps To Integrate Next Generation Firewall In Network
Firewall Network Security Steps To Integrate Next Generation Firewall In NetworkThis slide highlights the various steps organizations should take while implementing Next Generation Firewall in a network. The steps include defining security requirements, determining NGFW placements, selecting an NGFW solution, planning network segmentation, and designing firewall policies. Introducing Firewall Network Security Steps To Integrate Next Generation Firewall In Network to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Define Security Requirements, Determine Ngfw Placement using this template. Grab it now to reap its full benefits.
-
 Securing Food Safety In Online Budget Allocation For Integrating Advanced System
Securing Food Safety In Online Budget Allocation For Integrating Advanced SystemThis slide covers budget allocation for effective utilization of resources on third party integration, cyber security software and packaging and quality control system. Present the topic in a bit more detail with this Securing Food Safety In Online Budget Allocation For Integrating Advanced System. Use it as a tool for discussion and navigation on Packaging And Quality Control, Cyber Security Systems, Online Order Management Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web Gateway
30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web GatewayThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing 30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Compatible, Performance, Production, using this template. Grab it now to reap its full benefits.
-
 Integration Of Swg Inside Sase Architecture Network Security Using Secure Web Gateway
Integration Of Swg Inside Sase Architecture Network Security Using Secure Web GatewayThis slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Deliver an outstanding presentation on the topic using this Integration Of Swg Inside Sase Architecture Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Architecture, Integration, Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roadmap To Integrate Secure Web Gateway Into Network Security Using Secure Web Gateway
Roadmap To Integrate Secure Web Gateway Into Network Security Using Secure Web GatewayThis slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Roadmap To Integrate Secure Web Gateway Into Network Security Using Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Organizational, Requirements, using this template. Grab it now to reap its full benefits.
-
 Steps To Integrate Secure Web Gateway Into Organization Network Security Using Secure Web Gateway
Steps To Integrate Secure Web Gateway Into Organization Network Security Using Secure Web GatewayThis slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc. Increase audience engagement and knowledge by dispensing information using Steps To Integrate Secure Web Gateway Into Organization Network Security Using Secure Web Gateway. This template helps you present information on six stages. You can also present information on Organization, Production, Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Integrate Secure Web Gateway Network Network Security Using Secure Web Gateway
Timeline To Integrate Secure Web Gateway Network Network Security Using Secure Web GatewayThis slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Increase audience engagement and knowledge by dispensing information using Timeline To Integrate Secure Web Gateway Network Network Security Using Secure Web Gateway. This template helps you present information on seven stages. You can also present information on Organizational, Configure Solution, Determine Use Case using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V
Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS VThis slide covers checklist for assessing vendor before integrating technology strategy in operations to enhance security. It involves key points such as IT risk assessment, threat and security experts and expertise in developing new technologies. Deliver an outstanding presentation on the topic using this Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V. Dispense information and present a thorough explanation of Cloud Environments, Risk Arising, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V
Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS VThis slide covers operational technology security controls to improve IT safety. It involves five kinds of security controls such as update asset inventory, training, ,manage portable media and secure configuration. Introducing Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Update Asset Inventory, Portable Media, Backup And Restore, using this template. Grab it now to reap its full benefits.
-
 Integrated Security System ISS Benefits For Organization
Integrated Security System ISS Benefits For OrganizationThis slide showcases benefits of integrated security system for an organization. This further includes benefits such as efficiency, theft prevention and real time monitoring. Introducing our Integrated Security System ISS Benefits For Organization set of slides. The topics discussed in these slides are Parking Management, Workforce Schedule, Centralized Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Methods To Integrate Secops V2 Into Security Operations Soc
Methods To Integrate Secops V2 Into Security Operations SocThis slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Introducing Methods To Integrate Secops V2 Into Security Operations Soc to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Build Security Center Of Excellence, Establish Culture Of Collaboration, Security Operations, using this template. Grab it now to reap its full benefits.
-
 ERP Security Integration With It In Management
ERP Security Integration With It In ManagementThis slide showcases the IT methodology for ERP security management. Its aim is to strategize and align the team leads for a common goal. This slide contains planning project, build alignment, next steps, etc. Introducing our ERP Security Integration With It In Management set of slides. The topics discussed in these slides are Phase Steps, Phase Outcome. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
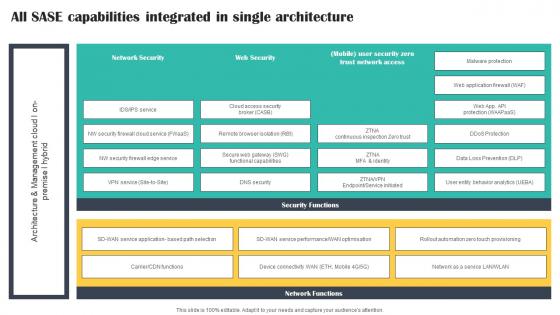 All SASE Capabilities Integrated In Single Architecture Cloud Security Model
All SASE Capabilities Integrated In Single Architecture Cloud Security ModelPresent the topic in a bit more detail with this All SASE Capabilities Integrated In Single Architecture Cloud Security Model. Use it as a tool for discussion and navigation on Capabilities, Integrated, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 All Sase Capabilities Integrated In Single Architecture Secure Access Service Edge Sase
All Sase Capabilities Integrated In Single Architecture Secure Access Service Edge SasePresent the topic in a bit more detail with this All Sase Capabilities Integrated In Single Architecture Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Architecture, Management, Malware Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial Internet
Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial InternetThis slide covers industrial internet of things security architecture. It involves key technologies such as integrity scanning, machine learning, behavior analysis, anti malware and risk detection. Present the topic in a bit more detail with this Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial Internet. Use it as a tool for discussion and navigation on Integration, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain IoT Enabled Security The Ultimate Guide To Blockchain Integration IoT SS
Blockchain IoT Enabled Security The Ultimate Guide To Blockchain Integration IoT SSThis slide presents the public safety surveillance system architecture supported by blockchain technology and internet of things devices. It includes components such as a blockchain center, community, supervisor, security official, etc. Present the topic in a bit more detail with this Blockchain IoT Enabled Security The Ultimate Guide To Blockchain Integration IoT SS. Use it as a tool for discussion and navigation on Security, System, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Integrating Security Principle With Dynamic System Development Method
Integrating Security Principle With Dynamic System Development MethodThis slide showcases incorporation of software security principles in DSDM model which helps in improving degree of project agility. It provides information regarding execution, functional model iteration, security design and security functional modulation. Introducing our Integrating Security Principle With Dynamic System Development Method set of slides. The topics discussed in these slides are Business Study, Integrating Security, Dynamic System Development. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SASE Network Security All SASE Capabilities Integrated In Single Architecture
SASE Network Security All SASE Capabilities Integrated In Single ArchitectureDeliver an outstanding presentation on the topic using this SASE Network Security All SASE Capabilities Integrated In Single Architecture. Dispense information and present a thorough explanation of Network, Security, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Management Controls To Enhance Data Integrity
Information Security Management Controls To Enhance Data IntegrityThis slide represents controls that help businesses to manage information security effectively from data breaches. It includes controls such as physical control, access control, procedural control, etc, Presenting our well structured Information Security Management Controls To Enhance Data Integrity. The topics discussed in this slide are Physical Control, Access Control, Procedural Control. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implementing Virtual Infrastructure Security Integration Roadmap
Implementing Virtual Infrastructure Security Integration RoadmapThis slide showcases timeline that assist businesses to implement virtual infrastructure to enhance data security integration and management. It includes carious phases such as resource virtualization, application virtualization, internal cloud and hybrid cloud. Introducing our premium set of slides with Implementing Virtual Infrastructure Security Integration Roadmap. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trusted Platform Incorporation, Zero Data Loss, Trusted Security. So download instantly and tailor it with your information.
-
 Secure Your Digital Assets Before Vs After Crypto Wallets Integration
Secure Your Digital Assets Before Vs After Crypto Wallets IntegrationThis slide represents the before versus after crypto wallets integration for business operations. The purpose of this slide is to showcase how integration of crypto wallets has removed the third party vendors from digital transactions. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Before Vs After Crypto Wallets Integration. This template helps you present information on five stages. You can also present information on Crypto Wallets Integration, Digital Transactions, Bitcoin Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Roadmap For Firewall Security Integration In Business
Firewall Network Security Roadmap For Firewall Security Integration In BusinessThis slide showcases a roadmap to implement firewall security in an organization. This slide highlights the various steps businesses should take while implementing firewall security, such as assessing network requirements and risks, designing and deploying firewall architecture, and so on. Introducing Firewall Network Security Roadmap For Firewall Security Integration In Business to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Use Antivirus Protection, Segmented Network, Avoid Outage using this template. Grab it now to reap its full benefits.
-
 Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SS
Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SSThis slide provides glimpse about comparative analysis of cyber security and risk management tools that can help the business in mitigating cyber threats. It includes key features, pricing, deployment, etc. Deliver an outstanding presentation on the topic using this Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SS. Dispense information and present a thorough explanation of Management Software, Cybersecurity, Supported Platforms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SS
Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SSPresent the topic in a bit more detail with this Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SS. Use it as a tool for discussion and navigation on Software Features, Real Time, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Continuous Integration And Continuous Delivery Process
Devsecops Best Practices For Secure Continuous Integration And Continuous Delivery ProcessThis slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Continuous Integration And Continuous Delivery Process. Use it as a tool for discussion and navigation on Integrate Container Security Scanners, Automate Security Updates, Automate Configuration Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Devsecops Adoption Integration Security Into Ci Cd Pipeline
Devsecops Best Practices For Secure Devsecops Adoption Integration Security Into Ci Cd PipelineThis slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, code or commit, build ottest, deploy, and monitor. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Devsecops Adoption Integration Security Into Ci Cd Pipeline. Dispense information and present a thorough explanation of Security Implementation, Devsecops Adoption, Integration Security, Seamless Security Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Pipeline Continuous Integration Commit Devsecops Best Practices For Secure
Devsecops Pipeline Continuous Integration Commit Devsecops Best Practices For SecureThis slide discusses the continuous integration commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the commit phase, which includes automating testing, speed, immediate feedback, identifying risk, security scanning, and so on. Deliver an outstanding presentation on the topic using this Devsecops Pipeline Continuous Integration Commit Devsecops Best Practices For Secure. Dispense information and present a thorough explanation of Continuous Integration, Devsecops Pipeline, Specialized Security Worker, Bundler Audit using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS V
Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Increase audience engagement and knowledge by dispensing information using Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS V. This template helps you present information on four stages. You can also present information on Fraud Detection, Compliance Tracking, Risk Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
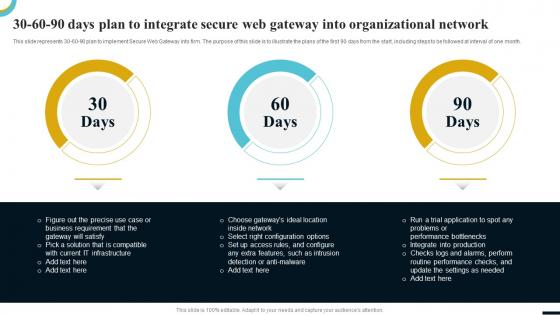 Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web
Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure WebThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Integration Of Swg Inside Sase Architecture
Internet Gateway Security IT Integration Of Swg Inside Sase ArchitectureThis slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Introducing Internet Gateway Security IT Integration Of Swg Inside Sase Architecture to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Web Sites, Cloud Apps, Private Cloud, Corporate Datacenter, using this template. Grab it now to reap its full benefits.
-
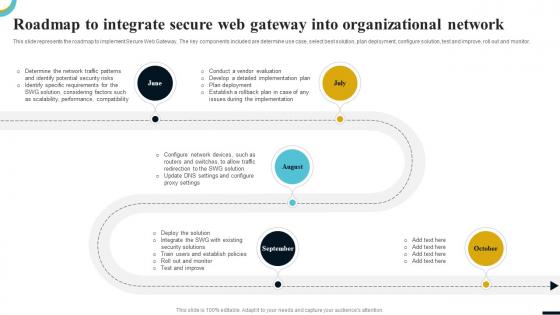 Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway
Internet Gateway Security IT Roadmap To Integrate Secure Web GatewayThis slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Performance, Compatibility, Implementation, Plan Deployment, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Steps To Integrate Secure Web Gateway
Internet Gateway Security IT Steps To Integrate Secure Web GatewayThis slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc. Introducing Internet Gateway Security IT Steps To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, Roll Out And Monitor, using this template. Grab it now to reap its full benefits.
-
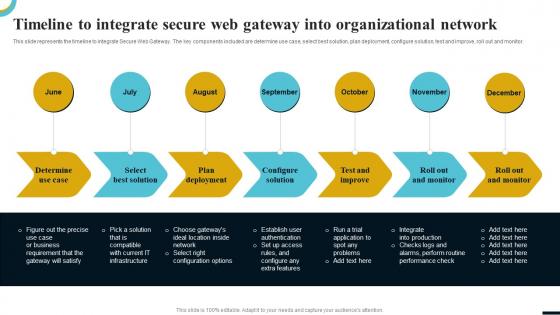 Internet Gateway Security IT Timeline To Integrate Secure Web Gateway
Internet Gateway Security IT Timeline To Integrate Secure Web GatewayThis slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Timeline To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, using this template. Grab it now to reap its full benefits.
-
 Steps To Integrate Wireless Internet For Data Security
Steps To Integrate Wireless Internet For Data SecurityThe following slide outlines crucial steps, including strong passwords, firmware updates, encryption, remote management, firewall protection, and data backup, to demonstrate the integration of wireless internet for enhanced data security. Presenting our set of slides with Steps To Integrate Wireless Internet For Data Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Backup, Firewall Protection, Disable Remote Management.
-
 Integrating ChatGPT With Other Systems Security And Compliance Glimpse About ChatGPT As AI ChatGPT SS V
Integrating ChatGPT With Other Systems Security And Compliance Glimpse About ChatGPT As AI ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Introducing Integrating ChatGPT With Other Systems Security And Compliance Glimpse About ChatGPT As AI ChatGPT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Fraud Detection, Compliance Tracking, Risk Analysis, Cybersecurity, Security And Compliance Management, using this template. Grab it now to reap its full benefits.
-
 File Integrity Monitoring Best Practices For Host And Container Security
File Integrity Monitoring Best Practices For Host And Container SecurityThis slide covers File Integrity Monitoring FIM best practices. The purpose of this template is to provide a structured approach to implementing FIM in host and container environments. It includes preparing asset inventory, detecting drift, and establishing protocols for notification, investigation, and response to security incidents. Presenting our set of slides with File Integrity Monitoring Best Practices For Host And Container Security This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Asset Inventory, Drift Detection, Investigation
-
 Security And Compliance Objectives Of File Integrity Monitoring
Security And Compliance Objectives Of File Integrity MonitoringThis slide covers the Security and Compliance Objectives of File Integrity Monitoring. The purpose of this template is to outline the key objectives that File Integrity Monitoring FIM. It includes unauthorized changes, preventing data breaches, incident response, adherence to regulatory standards, and reducing audit risks and penalties. Presenting our set of slides with Security And Compliance Objectives Of File Integrity Monitoring This exhibits information on Two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Objectives, Compliance Objectives
-
 Integrate Cyber Security Into Business Continuity And Disaster Recovery
Integrate Cyber Security Into Business Continuity And Disaster RecoveryThis slide depicts to integrate cyber security system into business continuity and disaster recovery process. Its aim is to improve operational efficiency and protect against any future threats. This slide includes planning, technology, policy, etc. Introducing our premium set of slides with Integrate Cyber Security Into Business Continuity And Disaster Recovery. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning, Technology, Policy. So download instantly and tailor it with your information.
-
 Integrating Chatgpt With Other Systems Security And Compliance Chatgpt Impact How ChatGPT SS V
Integrating Chatgpt With Other Systems Security And Compliance Chatgpt Impact How ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Increase audience engagement and knowledge by dispensing information using Integrating Chatgpt With Other Systems Security And Compliance Chatgpt Impact How ChatGPT SS V This template helps you present information on Four stages. You can also present information on Consumer Assistance, Sales Support, Customization, Consumer Feedback Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps
DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOpsThis slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, code or commit, build or test, deploy, and monitor. Present the topic in a bit more detail with this DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps. Use it as a tool for discussion and navigation on Integrate Security, Encourage Developer Ownership, Static Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Analytics And Integration Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Analytics And Integration Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations with our vibrant PowerPoint icon on big data storage solutions. This eye-catching icon features a bold color scheme and represents the latest advancements in data storage technology. Perfect for showcasing your expertise in big data management and storage solutions.
-
 Data Analytics And Integration Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Analytics And Integration Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the efficient and reliable storage solutions for big data. With its sleek design and bold color, it conveys the message of simplicity and effectiveness in managing large volumes of data. Perfect for presentations on data storage and management in the modern era.
-
 IP Security Model For Integrating Data
IP Security Model For Integrating DataThis slide showcase process of IP security. This includes data source, applications, devices, clients, activities, sensors, digital assets, integration of data, streaming data, data warehousing, storage pf object, etc. Introducing our IP Security Model For Integrating Data set of slides. The topics discussed in these slides are Data Warehouse Autonomous, Streaming Data, Services Of Big Data, Integration Of Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering
Creation Of Secure Networks Using MBSE Integrated Modelling And EngineeringThe purpose of this slide is to explain how MBSE principles can be applied to create secure networks and align with the criteria and models of information security management systems. This slide also highlights the steps involved, such as plan, do, check, and act. Present the topic in a bit more detail with this Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering. Use it as a tool for discussion and navigation on Series Of Steps, Overview, Check. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow
Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance FlowThis slide presents algorithms for encrypting data to ensure its protection and security. It includes types such as, AES advanced encryption standard and RSA rivest-shamir-adleman and ECC elliptic curve cryptography. Present the topic in a bit more detail with this Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Encryption Algorithm, Key Characteristics, Implementation In Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Integrating Third Party Application In Restaurant Pos
Securing Food Safety In Online Integrating Third Party Application In Restaurant PosThis slide covers integrating third party platform in POS system for efficient order taking, improve delivery times and tracks customer satisfaction. Introducing Securing Food Safety In Online Integrating Third Party Application In Restaurant Pos to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Efficient Order Taking, Improve Delivery Times, Track Customer Satisfaction, using this template. Grab it now to reap its full benefits.
-
 Impact Of Integrating SIEM Cyber Security In Business
Impact Of Integrating SIEM Cyber Security In BusinessThis slide showcases the benefits of incorporation SIEM cyber security. Its objective is to propose a better threat detection system. This slide includes threat detection, staff and less spend. Introducing our premium set of slides with name Impact Of Integrating SIEM Cyber Security In Business. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Better Threat Detection, Fewer Staff, Less Spend. So download instantly and tailor it with your information.
-
 Gateway Integration Security In Powerpoint And Google Slides Cpp
Gateway Integration Security In Powerpoint And Google Slides CppPresenting our Gateway Integration Security In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Gateway Integration Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Integrating Artificial Intelligence For Optimizing OT Cyber Security
Integrating Artificial Intelligence For Optimizing OT Cyber SecurityThis slide represents various applications of artificial intelligence that assist companies to enhance their OT cyber security and protect from potential cyber threats. It includes various applications such as rapid analysis, task prioritization, etc. Introducing our premium set of slides with Integrating Artificial Intelligence For Optimizing OT Cyber Security Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Detection Capabilities, Routine Task Automation So download instantly and tailor it with your information.
-
 Steps To Integrate Threat Intelligence Into Security Operations Center
Steps To Integrate Threat Intelligence Into Security Operations CenterThis slide provides a monthly timeline of steps to be implemented for integration of threat intelligence into security operation center that ensures response efficiency. Key steps are define requirements, data collection, analysis, etc. Presenting our set of slides with name Steps To Integrate Threat Intelligence Into Security Operations Center. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Define Requirements, Analysis, Evaluate, Optimize.
-
 Technology Integration For Security Operations Center
Technology Integration For Security Operations CenterThe below slide provides a technological integration architecture for security operation center that helps to understand the various technology used for threat identification and mitigation. The various technologies are cloud, network sensors, etc. Introducing our premium set of slides with name Technology Integration For Security Operations Center. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Analysis, SIEM, Intrusion Activity. So download instantly and tailor it with your information.
-
 A57 Email Security Best Practices And Email Security Solutions Integrated Cloud Email Security
A57 Email Security Best Practices And Email Security Solutions Integrated Cloud Email SecurityThe purpose of this slide is to discuss the Integrated Cloud Email Security ICES solutions of email security. This slide highlights the features of Integrated Cloud Email Security ICES , such as inline notifications, visibility to internal traffic, advanced detection techniques, etc. Present the topic in a bit more detail with this A57 Email Security Best Practices And Email Security Solutions Integrated Cloud Email Security. Use it as a tool for discussion and navigation on Inline Notifications, Visibility Into Internal Traffic, Advanced Detection Techniques, Baseline Behaviour Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Fundamental Web Security Pillars Integrity
Fundamental Web Security Pillars IntegrityThis slide describes the essential principle of web security, which is integrity. Principles include data and system integrity. Introducing Fundamental Web Security Pillars Integrity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Data Integrity, System Integrity, using this template. Grab it now to reap its full benefits.
-
 A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS V
A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Present the topic in a bit more detail with this A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS V. Use it as a tool for discussion and navigation on Fraud Detection, Compliance Tracking, Cybersecurity, Risk Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Third Party Apis And Integration Points B2b Ecommerce Service Challenges
Securing Third Party Apis And Integration Points B2b Ecommerce Service ChallengesThis slide showcases the API security workflow and the best practices that can be implemented. The purpose is to provide insights into conducting effective authentication and authorization techniques.Deliver an outstanding presentation on the topic using this Securing Third Party Apis And Integration Points B2b Ecommerce Service Challenges. Dispense information and present a thorough explanation of Implement Access Control, Encrypt Request And Response, Authenticate And Authorize using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidentiality integrity availability cyber security ppt powerpoint presentation icon example introduction cpb
Confidentiality integrity availability cyber security ppt powerpoint presentation icon example introduction cpbPresenting Confidentiality Integrity Availability Cyber Security Ppt Powerpoint Presentation Icon Example Introduction Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Confidentiality Integrity Availability Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security information and event management siem integrations
Security information and event management siem integrationsIncrease audience engagement and knowledge by dispensing information using Security Information And Event Management SIEM Integrations. This template helps you present information on four stages. You can also present information on Security Information And Event Management SIEM Integrations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Fully integrated security system ppt powerpoint presentation show cpb
Fully integrated security system ppt powerpoint presentation show cpbPresenting our Fully Integrated Security System Ppt Powerpoint Presentation Show Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Fully Integrated Security System. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.




