Powerpoint Templates and Google slides for Information Leak
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Revenue Leakage Business Information Measure Assurance Process Management
Revenue Leakage Business Information Measure Assurance Process ManagementEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Revenue Leakage Business Information Measure Assurance Process Management is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
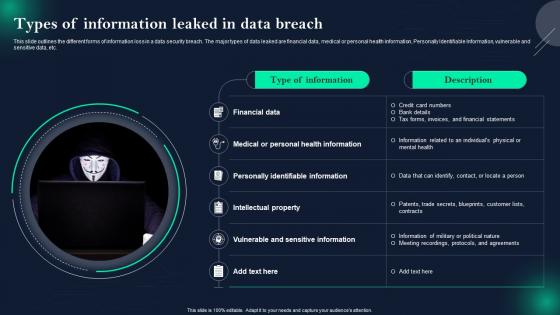 Data Breach Prevention Types Of Information Leaked In Data Breach
Data Breach Prevention Types Of Information Leaked In Data BreachThis slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc. Introducing Data Breach Prevention Types Of Information Leaked In Data Breach to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Financial Data, Intellectual Property, Vulnerable And Sensitive Information, Personally Identifiable Information, using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V
Blockchain And Cybersecurity Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Cross Check Emails, Factor Authentication, Unprotected Wi-Fi-Networks using this template. Grab it now to reap its full benefits.
-
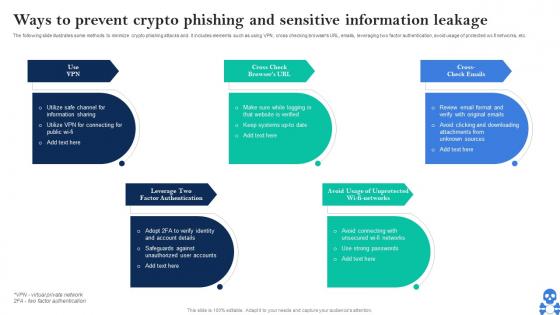 Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V
Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. it includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Use VPN, Factor Authentication, Avoid Usage Of Unprotected using this template. Grab it now to reap its full benefits.
-
 Ways To Prevent Crypto Phishing And Sensitive Information Leakage Guide For Blockchain BCT SS V
Ways To Prevent Crypto Phishing And Sensitive Information Leakage Guide For Blockchain BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Ways To Prevent Crypto Phishing And Sensitive Information Leakage Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cross Check Emails, Factor Authentication, Unprotected Wi Fi Networks using this template. Grab it now to reap its full benefits.
-
 Data Breach Response Plan Types Of Information Leaked In Data Breach
Data Breach Response Plan Types Of Information Leaked In Data BreachThis slide outlines the different forms of information loss in a data security breach. The major types of data leaked are customer personal data, payment information, purchase history, login credentials, personal preferences, social media links, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Types Of Information Leaked In Data Breach. Dispense information and present a thorough explanation of Customer Personal Data, Payment Information, Personal Preferences, Social Media Links using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Leaking confidential information workplace ppt powerpoint presentation layouts gridlines cpb
Leaking confidential information workplace ppt powerpoint presentation layouts gridlines cpbPresenting our Leaking Confidential Information Workplace Ppt Powerpoint Presentation Layouts Gridlines Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Leaking Confidential Information Workplace This PPT slide can be easily accessed in standard screen 4.3 and widescreen 16.9 aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Confidential information leak ppt powerpoint presentation professional sample cpb
Confidential information leak ppt powerpoint presentation professional sample cpbPresenting Confidential Information Leak Ppt Powerpoint Presentation Professional Sample Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both 4.3 and 16.9 aspect ratios. It is also a useful set to elucidate topics like Confidential Information Leak. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.



