Powerpoint Templates and Google slides for Incident Identification
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 ITIL Incident Identification Management Process Flow
ITIL Incident Identification Management Process FlowThis slide represents process flow of ITIL incident identification management. It further includes various factors in process such as incident occurs, event management detection, IT staff discovery, user contains IT staff, supplier discovery, etc Introducing our ITIL Incident Identification Management Process Flow set of slides. The topics discussed in these slides are Monitoring, Supplier Discovery This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Project issue identification incident and problem management
Project issue identification incident and problem managementThis slide provides the glimpse about the first step of issue escalation process which covers the identification process such as issue title, date created, issue category, priority, etc. Present the topic in a bit more detail with this Project Issue Identification Incident And Problem Management. Use it as a tool for discussion and navigation on Project Issue Identification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Response Playbook Asset Criticality Of Identified System Components
Incident Response Playbook Asset Criticality Of Identified System ComponentsMentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost. Present the topic in a bit more detail with this Incident Response Playbook Asset Criticality Of Identified System Components. Use it as a tool for discussion and navigation on Extremely Critical, Reasonably Critical, Least Critical. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Response Playbook Identifying The Origin And Type Of Cyber Incident
Incident Response Playbook Identifying The Origin And Type Of Cyber IncidentFollowing slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Increase audience engagement and knowledge by dispensing information using Incident Response Playbook Identifying The Origin And Type Of Cyber Incident. This template helps you present information on three stages. You can also present information on Source Of Origin, Theft Of Equipment, External And Removable Media using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident Response Playbook Identifying The Severity Level And Impact Of Cyber Incident
Incident Response Playbook Identifying The Severity Level And Impact Of Cyber IncidentPurpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide. Introducing Incident Response Playbook Identifying The Severity Level And Impact Of Cyber Incident to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Critical Information, Business System, Additional Resources, using this template. Grab it now to reap its full benefits.
-
 Incident Identification Icon For Escalation Process
Incident Identification Icon For Escalation ProcessIntroducing our premium set of slides with Incident Identification Icon For Escalation Process. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Incident Identification, Escalation Process. So download instantly and tailor it with your information.
-
 Security Incident Response Playbook Asset Criticality Of Identified System Components
Security Incident Response Playbook Asset Criticality Of Identified System ComponentsMentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost. Present the topic in a bit more detail with this Security Incident Response Playbook Asset Criticality Of Identified System Components. Use it as a tool for discussion and navigation on Identified, Components, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Incident Response Playbook Identifying The Origin And Type Of Cyber Incident
Security Incident Response Playbook Identifying The Origin And Type Of Cyber IncidentFollowing slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Present the topic in a bit more detail with this Security Incident Response Playbook Identifying The Origin And Type Of Cyber Incident. Use it as a tool for discussion and navigation on Identifying, Information, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Incident Response Playbook Identifying The Severity Level And Impact Of Cyber Incident
Security Incident Response Playbook Identifying The Severity Level And Impact Of Cyber IncidentPurpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide. Deliver an outstanding presentation on the topic using this Security Incident Response Playbook Identifying The Severity Level And Impact Of Cyber Incident. Dispense information and present a thorough explanation of Identifying, Compromised, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Asset Criticality Of Identified System Components Cybersecurity Incident And Vulnerability
Asset Criticality Of Identified System Components Cybersecurity Incident And VulnerabilityMentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost. Deliver an outstanding presentation on the topic using this Asset Criticality Of Identified System Components Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Host Computers, SCADA Software, Field Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying The Origin And Type Of Cyber Incident Cybersecurity Incident And Vulnerability
Identifying The Origin And Type Of Cyber Incident Cybersecurity Incident And VulnerabilityFollowing slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Deliver an outstanding presentation on the topic using this Identifying The Origin And Type Of Cyber Incident Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Web, Email, Removable Media using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying The Severity Level And Impact Of Cyber Incident Cybersecurity Incident And Vulnerability
Identifying The Severity Level And Impact Of Cyber Incident Cybersecurity Incident And VulnerabilityPurpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide. Introducing Identifying The Severity Level And Impact Of Cyber Incident Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Compromise Of Security, Service, Business System, using this template. Grab it now to reap its full benefits.
-
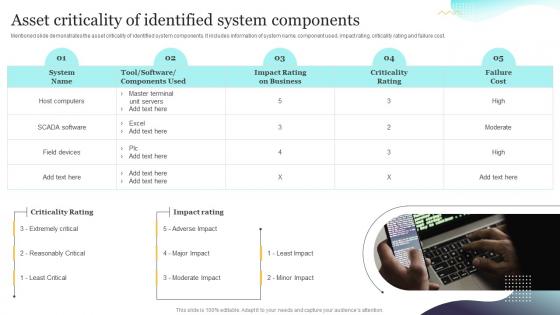 Asset Criticality Of Identified System Components Upgrading Cybersecurity With Incident Response Playbook
Asset Criticality Of Identified System Components Upgrading Cybersecurity With Incident Response PlaybookMentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost. Present the topic in a bit more detail with this Asset Criticality Of Identified System Components Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Criticality, Information, Demonstrates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying The Origin And Type Of Cyber Incident Upgrading Cybersecurity With Incident Response Playbook
Identifying The Origin And Type Of Cyber Incident Upgrading Cybersecurity With Incident Response PlaybookFollowing slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Present the topic in a bit more detail with this Identifying The Origin And Type Of Cyber Incident Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Effectively, Information, Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying The Severity Level And Impact Upgrading Cybersecurity With Incident Response Playbook
Identifying The Severity Level And Impact Upgrading Cybersecurity With Incident Response PlaybookPurpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide. Deliver an outstanding presentation on the topic using this Identifying The Severity Level And Impact Upgrading Cybersecurity With Incident Response Playbook. Dispense information and present a thorough explanation of Identifying, Business, Severity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident response showing identification of threats and recovery
Incident response showing identification of threats and recoveryPresenting this set of slides with name - Incident Response Showing Identification Of Threats And Recovery. This is a five stage process. The stages in this process are Incident Response, Incident Reaction, Incident Reply.
-
 Incident management process with identification and closure
Incident management process with identification and closurePresenting this set of slides with name Incident Management Process With Identification And Closure. This is a seven stage process. The stages in this process are Incident Management, Process, Team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.



