Powerpoint Templates and Google slides for Improves Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management
Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks ManagementThe following slide depicts the cyber security review flowchart to manage risk and minimize its impact. It includes elements such as request access, grantor, authorizer, tools, auditor, follow up, alert to end user etc. Present the topic in a bit more detail with this Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Request Access, Validate User Identity, Dismiss Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks Management
Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks ManagementThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool name, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks Management. Dispense information and present a thorough explanation of Determines Suspicious, Features, Cyber Security Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Evaluate Impact And Probability Of Risk Occurrence Improving Cyber Security Risks Management
Evaluate Impact And Probability Of Risk Occurrence Improving Cyber Security Risks ManagementThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Present the topic in a bit more detail with this Evaluate Impact And Probability Of Risk Occurrence Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Parameters, Inappropriate Configuration System, Unauthorized Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Execute Best Practices Of Patch Management Solutions Improving Cyber Security Risks Management
Execute Best Practices Of Patch Management Solutions Improving Cyber Security Risks ManagementThe following slide highlights some tips to execute patch management. It includes elements such as drafting policy, manage data and application, determining vendor updates, scanning vulnerabilities, ranking patches etc. Deliver an outstanding presentation on the topic using this Execute Best Practices Of Patch Management Solutions Improving Cyber Security Risks Management. Dispense information and present a thorough explanation of Draft Patch Policy, Manage Data And Application, Determine Vendor Updates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
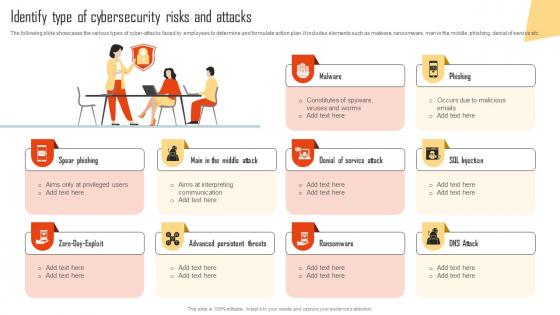 Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management
Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks ManagementThe following slide showcases the various types of cyber-attacks faced by employees to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Advanced Persistent Threats, Ransomware, Phishing, using this template. Grab it now to reap its full benefits.
-
 Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management
Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks ManagementThe following slide illustrates some best practices to execute preventive actions for cyber attacks. It includes elements such as train employees, updating systems and software, developing incident response plan, backing up data, maintaining compliance etc. Increase audience engagement and knowledge by dispensing information using Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management. This template helps you present information on six stages. You can also present information on Train Employees, Maintain Compliance, Develop Incident Response Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Plan Useful Data Backup Schedule Improving Cyber Security Risks Management
Plan Useful Data Backup Schedule Improving Cyber Security Risks ManagementThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Present the topic in a bit more detail with this Plan Useful Data Backup Schedule Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Incremental Backup, Plan Useful, Data Backup Schedule. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risks With Matrix Improving Cyber Security Risks Management
Prioritize Cyber Security Risks With Matrix Improving Cyber Security Risks ManagementThe following slide presents cyber security risks exposure grid to determine and plan mitigation actions. It includes elements such as restricting permissions, remediating constantly, postponing remediation, tracking risk escalation etc. Introducing Prioritize Cyber Security Risks With Matrix Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Restrict Permissions, Postpone Remediation, Track Risk Escalation, using this template. Grab it now to reap its full benefits.
-
 Review Cyber Security Status With Due Diligence Checklist Improving Cyber Security Risks Management
Review Cyber Security Status With Due Diligence Checklist Improving Cyber Security Risks ManagementThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Disaster Recovery, Password And Encryption, Parameters. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Run Penetration Testing To Review Risk Improving Cyber Security Risks Management
Run Penetration Testing To Review Risk Improving Cyber Security Risks ManagementThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Deliver an outstanding presentation on the topic using this Run Penetration Testing To Review Risk Improving Cyber Security Risks Management. Dispense information and present a thorough explanation of Objectives, Features, Conducted, Duration, Outcomes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Select Cybersecurity Training Program Courses Improving Cyber Security Risks Management
Select Cybersecurity Training Program Courses Improving Cyber Security Risks ManagementThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber-attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost. Present the topic in a bit more detail with this Select Cybersecurity Training Program Courses Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Cloud Security, Information Security, Cybersecurity Fundamentals. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Improving Cyber Security Risk Management Process
Table Of Contents For Improving Cyber Security Risk Management ProcessIntroducing Table Of Contents For Improving Cyber Security Risk Management Process to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risks And Attacks, Management Solutions, Program Courses, using this template. Grab it now to reap its full benefits.
-
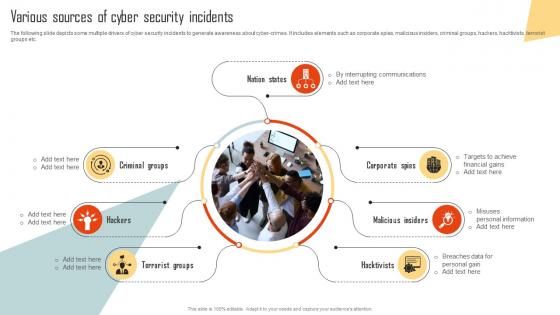 Various Sources Of Cyber Security Incidents Improving Cyber Security Risks Management
Various Sources Of Cyber Security Incidents Improving Cyber Security Risks ManagementThe following slide depicts some multiple drivers of cyber security incidents to generate awareness about cyber crimes. It includes elements such as corporate spies, malicious insiders, criminal groups, hackers, hacktivists, terrorist groups etc. Increase audience engagement and knowledge by dispensing information using Various Sources Of Cyber Security Incidents Improving Cyber Security Risks Management. This template helps you present information on seven stages. You can also present information on Criminal Groups, Terrorist Groups, Malicious Insiders, Corporate Spies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does SD WAN Improve Security Managed Wan Services
How Does SD WAN Improve Security Managed Wan ServicesThis slide depicts the various security benefits of the software defined wide area network. These advantages include centralized and scalable security, zero touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response.Increase audience engagement and knowledge by dispensing information using How Does SD WAN Improve Security Managed Wan Services. This template helps you present information on six stages. You can also present information on Traffic Prioritization, Business Resources, Encryption Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does SD WAN Improve Security Cloud WAN Ppt Infographics
How Does SD WAN Improve Security Cloud WAN Ppt InfographicsThis slide depicts the various security benefits of the software defined wide area network. These advantages include centralized and scalable security, zero touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Introducing How Does SD WAN Improve Security Cloud WAN Ppt Infographics to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security, Segmentation, Locations, using this template. Grab it now to reap its full benefits.
-
 ChatGPT For Streamlining And Improving Security Communications Leveraging ChatGPT AI SS V
ChatGPT For Streamlining And Improving Security Communications Leveraging ChatGPT AI SS VThis slide showcases overview of ChatGPT for streamlining and optimizing the security operations in organizations. Its key elements are cybersecurity training, enhanced communication during attack, developing policies and reporting after attack. Introducing ChatGPT For Streamlining And Improving Security Communications Leveraging ChatGPT AI SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Reporting After Attack, Cybersecurity Training, Developing Policies using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Security Measures To Improve Firewall Protection
Firewall Network Security Security Measures To Improve Firewall ProtectionThis slide represents the different security steps to enhance firewall protection in a network. The purpose of this slide is to showcase the various security measures to improve firewall protection, such as updating the firewall, using antivirus protection, restricting accessible ports and hosts, segmenting the network, etc. Introducing Firewall Network Security Security Measures To Improve Firewall Protection to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Screened Host Firewalls, Packet Filtering Router using this template. Grab it now to reap its full benefits.
-
 Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS V
Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Deliver an outstanding presentation on the topic using this Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS V. Dispense information and present a thorough explanation of Mobile Banking, Change Passwords Frequently, Monitor Transactions, Avoid Using Public Networks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Banking Solutions For Improving Customer Mobile Banking Application Security Testing Tools Fin SS V
Banking Solutions For Improving Customer Mobile Banking Application Security Testing Tools Fin SS VThis slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Present the topic in a bit more detail with this Banking Solutions For Improving Customer Mobile Banking Application Security Testing Tools Fin SS V. Use it as a tool for discussion and navigation on Mobile Banking Application, Security Testing Tools, Mobile Banking Apps, Real Time Bot Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improved Framework For Event Monitoring And Security
Improved Framework For Event Monitoring And SecurityThis slide contains the framework for monitoring events. Its objective is to track and evaluate monitoring events. This slide includes capturing data, analysing data, taking action, etc. Introducing Improved Framework For Event Monitoring And Security to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Capture Data, Analyse Data, Take Action, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Continuous Process Improvement In Devsecops
Devsecops Best Practices For Secure Continuous Process Improvement In DevsecopsThis slide discusses the DevSecOps program requirement for continuous improvement. The purpose of this slide is to explain the needs of the DevSecOps program for achieving efficiency, these include strategic goals, architecture operation, and program evaluation. Introducing Devsecops Best Practices For Secure Continuous Process Improvement In Devsecops to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Strategic Goals, Architecture And Operations, Program Evaluation, Devops Environment, using this template. Grab it now to reap its full benefits.
-
 Case Study 2 Improving Connected Home Security IoT Security And Privacy Safeguarding IoT SS
Case Study 2 Improving Connected Home Security IoT Security And Privacy Safeguarding IoT SSThis slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results. Increase audience engagement and knowledge by dispensing information using Case Study 2 Improving Connected Home Security IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on three stages. You can also present information on Security Solutions, Improved Customer Satisfaction, Provide Innovative using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of ZTNA To Improve Business Operations And Security Identity Defined Networking
Role Of ZTNA To Improve Business Operations And Security Identity Defined NetworkingThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Present the topic in a bit more detail with this Role Of ZTNA To Improve Business Operations And Security Identity Defined Networking. Use it as a tool for discussion and navigation on Traditional Method, Workforce Protection, Data Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V
Data Security Best Practices To Protect Using Customer Data To Improve MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V. Dispense information and present a thorough explanation of Policy, Data, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Methods To Improve Organizational Server Security
Methods To Improve Organizational Server SecurityFollowing slide showcases improving server security in organization through various methods, also including elements such as regularly update programs, website server backup, etc. Presenting our well structured Methods To Improve Organizational Server Security. The topics discussed in this slide are Regularly Update Programs, Website Server Backup, Digital Protection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By Leveraging
Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By LeveragingMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Introducing Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By Leveraging to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Network Connection, Secure Login Credentials, Keep Personal Data Private using this template. Grab it now to reap its full benefits.
-
 Improve Cyber Security By Big Data In Companies
Improve Cyber Security By Big Data In CompaniesThis slide helps you identify and improve cyber security by integrating big data in companies. Its aim is to prevent attacks and security breaches. This slide consists of prevention of malware attacks, monitor logs, assess risk, integrate big data, etc. Introducing our premium set of slides with Improve Cyber Security By Big Data In Companies. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Attacks, Monitor, Integrate. So download instantly and tailor it with your information.
-
 Saas Cyber Security Icon To Improve Operational Efficiency
Saas Cyber Security Icon To Improve Operational EfficiencyPresenting our set of slides with Saas Cyber Security Icon To Improve Operational Efficiency This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Saas Cyber Security, Icon To Improve Operational Efficiency
-
 Improving Security By Green Computing Technology Carbon Free Computing
Improving Security By Green Computing Technology Carbon Free ComputingThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Present the topic in a bit more detail with this Improving Security By Green Computing Technology Carbon Free Computing. Use it as a tool for discussion and navigation on Green Computing Technology, Computers And Networks, Security Concerns And Solution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Mesh Improved Scalability
Cyber Security Mesh Improved ScalabilityIntroducing our Cyber Security Mesh Improved Scalability set of slides. The topics discussed in these slides are Cyber Security Mesh, Improved Scalability. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security
Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And SecurityThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Introducing Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Traditional Method, ZTNA Approach, Login Capability, using this template. Grab it now to reap its full benefits.
-
 Improving Transparency And Security Of Property Title Ultimate Guide To Understand Role BCT SS
Improving Transparency And Security Of Property Title Ultimate Guide To Understand Role BCT SSThis slide covers applications of property title management such as performing land survey, title creation, blockchain title and tokenization. It also includes elements such as type of blockchain, development stage, service offering along with benefits. Increase audience engagement and knowledge by dispensing information using Improving Transparency And Security Of Property Title Ultimate Guide To Understand Role BCT SS. This template helps you present information on four stages. You can also present information on Land Survey, Title Creation, Blockchain Tilte using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Improvement In Mobile Application Development
Security Improvement In Mobile Application DevelopmentThis slide highlights the different ways to improve security in mobile application development which includes enforce updates, enable two factor authentication, etc. Introducing our premium set of slides with name Security Improvement In Mobile Application Development. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Improvement, Mobile Application Development, Handle Sensitive Data Carefully. So download instantly and tailor it with your information.
-
 ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS V
ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS VThis slide showcases overview of ChatGPT for streamlining and optimizing the security operations in organizations. Its key elements are cybersecurity training, enhanced communication during attack, developing policies and reporting after attack. Introducing ChatGPT For Streamlining And Improving Security Opportunities And Risks Of ChatGPT AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reporting After Attack, Cybersecurity Training, Developing Policies, using this template. Grab it now to reap its full benefits.
-
 ChatGPT For Streamlining And Improving Security Communications Impact Of Generative AI SS V
ChatGPT For Streamlining And Improving Security Communications Impact Of Generative AI SS VThis slide showcases overview of ChatGPT for streamlining and optimizing the security operations in organizations. Its key elements are cybersecurity training, enhanced communication during attack, developing policies and reporting after attack. Increase audience engagement and knowledge by dispensing information using ChatGPT For Streamlining And Improving Security Communications Impact Of Generative AI SS V. This template helps you present information on four stages. You can also present information on Cybersecurity Training, Enhanced Communication, Reporting After Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Tokenization For Improved Data Security
Agenda For Tokenization For Improved Data SecurityIntroducing Agenda For Tokenization For Improved Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Tokenization Training Program, Budget Allocation And Roadmap, Governance, Security, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Security And Utility Token Tokenization For Improved Data Security
Comparative Analysis Of Security And Utility Token Tokenization For Improved Data SecurityThis slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Present the topic in a bit more detail with this Comparative Analysis Of Security And Utility Token Tokenization For Improved Data Security. Use it as a tool for discussion and navigation on Comparative Analysis, Security And Utility Token, Expectations, Scam Potential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Tokenization For Improved Data Security
Icons Slide For Tokenization For Improved Data SecurityIntroducing our well researched set of slides titled Icons Slide For Tokenization For Improved Data Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents Of Tokenization For Improved Data Security
Table Of Contents Of Tokenization For Improved Data SecurityIncrease audience engagement and knowledge by dispensing information using Table Of Contents Of Tokenization For Improved Data Security. This template helps you present information on twelve stages. You can also present information on Data Security, Tokenization Market And Trends, Comparative Analysis, Training And Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization
Tokenization For Improved Data Security 30 60 90 Days Plan To Implement TokenizationThis slide depicts the 30 60 90 days plan for implementing tokenization. The plan includes the activities and goals such as assessment, planning, selecting tokenization solutions, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization. Dispense information and present a thorough explanation of Assessment And Planning, Select Tokenization Solution, Test Tokenization Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security About Non Fungible Tokenization In Crypto Currency
Tokenization For Improved Data Security About Non Fungible Tokenization In Crypto CurrencyThis slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Introducing Tokenization For Improved Data Security About Non Fungible Tokenization In Crypto Currency to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Rising Crypto Trend, Exclusive Digital Ownership, Diverse Assets, Safeguarding Digital Creations, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based Operations
Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based OperationsThis slide represents the fundamental tokenization service designed for cloud-based solutions. The purpose of this slide is to showcase the basic tokenization service for cloud-based services. Present the topic in a bit more detail with this Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based Operations. Use it as a tool for discussion and navigation on Sensitive Or Personal Information Sources, Tokenization Database, Tokenization Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security
Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data SecurityThis slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security. Dispense information and present a thorough explanation of Compliance With Regulations, Reduced Insider Threats, Exposure Of Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Best Practices For Tokenization In Data Security
Tokenization For Improved Data Security Best Practices For Tokenization In Data SecurityThe purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Best Practices For Tokenization In Data Security. This template helps you present information on four stages. You can also present information on Effective Cybersecurity And Compliance, Broaden Data Tokenization Scope, Regularly Revise Tokenization Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business
Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In BusinessThis slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business. Use it as a tool for discussion and navigation on Tokenization Solution, Integration And Customization, Infrastructure And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Challenges And Related Solutions In Utility Tokens
Tokenization For Improved Data Security Challenges And Related Solutions In Utility TokensThis slide outlines the issues faced by utility tokens in data security. The purpose of this slide is to showcase utility token challenges which include absence of inherent mechanism, inadequate promotion, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Challenges And Related Solutions In Utility Tokens. Dispense information and present a thorough explanation of Regularly Remove From Circulation, Inadequate Promotion, Cryptocurrency Adoption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data Security
Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data SecurityThis slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data Security. This template helps you present information on seven stages. You can also present information on Utility Tokenization, Data Security, Platforms Economic Activity, Blockchain Powered Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data Security
Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data SecurityThis slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Present the topic in a bit more detail with this Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data Security. Use it as a tool for discussion and navigation on Data Classification, Tokenization Algorithm Selection, Key Management, Access Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data Security
Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data SecurityThis slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Introducing Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Restricting Access To Sensitive Data, Reducing Compliance Scope, Tokenization In Data Security, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Comparative Analysis Of Encryption And Tokenization In Ds
Tokenization For Improved Data Security Comparative Analysis Of Encryption And Tokenization In DsThis slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Comparative Analysis Of Encryption And Tokenization In Ds. Dispense information and present a thorough explanation of Comparative Analysis, Encryption And Tokenization, Safeguards Private Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In Ds
Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In DsThis slide highlights the disadvantages of carrying out tokenization. The purpose of this slide is to showcase the drawbacks and its implications which include increased IT complexity, limited adoption, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In Ds. Use it as a tool for discussion and navigation on Critical Challenges, Tokenization Implementation, Alters Transaction Process, Compatibility Concerns. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Data Security Benefits Of Adopting Tokenization
Tokenization For Improved Data Security Data Security Benefits Of Adopting TokenizationThis slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Data Security Benefits Of Adopting Tokenization. Dispense information and present a thorough explanation of Builds Customer Trust, Data Security Benefits, Adopting Tokenization, Fostering Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities
Tokenization For Improved Data Security Data Tokenization Tools Key CapabilitiesPresent the topic in a bit more detail with this Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities. Use it as a tool for discussion and navigation on Data Tokenization Tools, Key Capabilities, Operational And Analytical Purposes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology
Tokenization For Improved Data Security Difference Between Tokenization And Masking TechnologyThis slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology. Dispense information and present a thorough explanation of Data Preservation, Masking Technology, Maintains Data Format using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds
Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In DsThis slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds. This template helps you present information on six stages. You can also present information on Mathematically Reversible, Cryptographic Function, Producing Tokens using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Evolution Of Tokenization From Ancient Times To Modern Era
Tokenization For Improved Data Security Evolution Of Tokenization From Ancient Times To Modern EraThis slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Evolution Of Tokenization From Ancient Times To Modern Era. Use it as a tool for discussion and navigation on Evolution Of Tokenization, Tokenization Recently Secured, Payment Card Data Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over Encryption
Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over EncryptionThis slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over Encryption. Dispense information and present a thorough explanation of Elimination Of Encryption Key Management, Format Attributes, Reduction Of Compliance Scope using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security For Table Of Contents
Tokenization For Improved Data Security For Table Of ContentsPresent the topic in a bit more detail with this Tokenization For Improved Data Security For Table Of Contents. Use it as a tool for discussion and navigation on Overview And Process, Areas Of Application, Reasons For Conducting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology
Tokenization For Improved Data Security Future Trends Of Tokenization On Business And TechnologyThis slide highlights the anticipated developments in tokenizations impact on the realms of business and technology. The purpose of this slide is to outline the future trends of tokenization. Introducing Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Anticipated Developments, Business And Technology, Future Trends Of Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





