Powerpoint Templates and Google slides for Implementing Cyber Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident Management
Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident ManagementThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Introducing Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Preparation, Detection Analysis, Containment Eradication Recovery, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Plan Timeline Development And Implementation Of Security Incident
Cyber Security Incident Response Plan Timeline Development And Implementation Of Security IncidentThis slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Present the topic in a bit more detail with this Cyber Security Incident Response Plan Timeline Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Verification Of Incident, Cyber Incident Report, Response Arrives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security
Cyber Security Incident Response Process Flow Chart Development And Implementation Of SecurityThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security. Dispense information and present a thorough explanation of Data Collection And Preservation, Perform Technical Analysis, Incident Declaration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident Management
Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident ManagementThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Present the topic in a bit more detail with this Cyber Security Incidents Follow Up Report Development And Implementation Of Security Incident Management. Use it as a tool for discussion and navigation on Confidential Information Customers, Theft Confidential Information, Organizational Projects. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident
Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security IncidentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Consequences, Vulnerability, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management
Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management. Use it as a tool for discussion and navigation on Intruder Traps, Attacker And User Behavior Analytics, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security
Impact Of Implementing Cyber Security Incident Management Development And Implementation Of SecurityThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present the topic in a bit more detail with this Impact Of Implementing Cyber Security Incident Management Development And Implementation Of Security. Use it as a tool for discussion and navigation on Results, Post Implementation, Pre Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security
Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of SecurityThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Introducing Key Parameters To Select Cyber Security Containment Strategy Development And Implementation Of Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organizational Resources, Potential Damages, Strategy, using this template. Grab it now to reap its full benefits.
-
 Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management
Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Increase audience engagement and knowledge by dispensing information using Strategies To Analyze Cyber Security Incidents Development And Implementation Of Security Incident Management. This template helps you present information on two stages. You can also present information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security
Various Cyber Security Incidents Detected By It Department Development And Implementation Of SecurityThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Various Cyber Security Incidents Detected By It Department Development And Implementation Of Security. This template helps you present information on five stages. You can also present information on Insider Threat, Phishing Attack, Malware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management
Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident ManagementThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Introducing Ways To Detect Cyber Security Incidents Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Privileged User Accounts, Unusual Behavior, Network Traffic, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management
Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident ManagementThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management. Dispense information and present a thorough explanation of Cyber Security Incident, Management On Organization, Software Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall
Cyber Security Attacks Response Plan Benefits Of Implementing Web Application FirewallThis slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall. Use it as a tool for discussion and navigation on Fights Vulnerabilities, Application Firewall, Confidential Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide Implementing Cyber Security Incident Management
Icons Slide Implementing Cyber Security Incident ManagementIntroducing our well researched set of slides titled Icons Slide Implementing Cyber Security Incident Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Development And Implementation Of Security Key Lessons Learned By Organization From Cyber Security Incident
Development And Implementation Of Security Key Lessons Learned By Organization From Cyber Security IncidentThis slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Increase audience engagement and knowledge by dispensing information using Development And Implementation Of Security Key Lessons Learned By Organization From Cyber Security Incident. This template helps you present information on three stages. You can also present information on Active, Probably Stay, No Signs Reduction Ransomware Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Development And Implementation User Awareness Training Program To Prevent Cyber Security Incidents
Development And Implementation User Awareness Training Program To Prevent Cyber Security IncidentsThis slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Deliver an outstanding presentation on the topic using this Development And Implementation User Awareness Training Program To Prevent Cyber Security Incidents. Dispense information and present a thorough explanation of Password Security, Cloud And Internet Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Implementation Approach Conceptual Framework
Cyber Security Implementation Approach Conceptual FrameworkFollowing slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Introducing our premium set of slides with Cyber Security Implementation Approach Conceptual Framework. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implementation, Approach, Conceptual. So download instantly and tailor it with your information.
-
 Implementing Cyber Security Awareness Raising Cyber Security Awareness In Organizations
Implementing Cyber Security Awareness Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to delineate a comprehensive security awareness training program that can assist corporates to mitigate cyber attacks and reduce downtime. Information covered in this slide is related to training goals, major topics to cover and projected result. Introducing Implementing Cyber Security Awareness Raising Cyber Security Awareness In Organizations to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Training Objective, Topics To Cover, Expected Result, using this template. Grab it now to reap its full benefits.
-
 Strategies We Will Implement To Make Security Raising Cyber Security Awareness In Organizations
Strategies We Will Implement To Make Security Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Introducing Strategies We Will Implement To Make Security Raising Cyber Security Awareness In Organizations to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Gamification, Personalization, High Quality Content, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Cyber Security Automation In Secops
Steps To Implement Cyber Security Automation In SecopsThis slide outline the security operations automation process that enables to ease of the burden of cybersecurity organizations by automating repetitive tasks. It includes determine standard operating procedures SOPs , analyse tools, verify existing API connectors, etc. Presenting our set of slides with Steps To Implement Cyber Security Automation In Secops. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyse Tools, Progressive Automation, Enhance Processes.
-
 Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation Impact
Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Cyber Security Risk Management Action Plan
Implementation Of Cyber Security Risk Management Action PlanThis slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks Presenting our well structured Implementation Of Cyber Security Risk Management Action Plan. The topics discussed in this slide are Security, Management, Plan. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Firewall Implementation For Cyber Security Post Firewall Implementation Impact On Business
Firewall Implementation For Cyber Security Post Firewall Implementation Impact On BusinessThis slide represents the impact of firewall implementation on the organization. The purpose of this slide is to showcase the decline in various cyber security threats such as malware, worms, Daniel of Service, botnets, and phishing attacks. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Post Firewall Implementation Impact On Business. Dispense information and present a thorough explanation of Post Firewall Implementation, Data Breaching Threats, Daniel Of Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Five years cyber security implementation approach roadmap
Five years cyber security implementation approach roadmapPresenting Five Years Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Half yearly cyber security implementation approach roadmap
Half yearly cyber security implementation approach roadmapPresenting Half Yearly Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Quarterly cyber security implementation approach roadmap
Quarterly cyber security implementation approach roadmapPresenting Quarterly Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Six months cyber security implementation approach roadmap
Six months cyber security implementation approach roadmapPresenting Six Months Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Three months cyber security implementation approach roadmap
Three months cyber security implementation approach roadmapPresenting Three Months Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
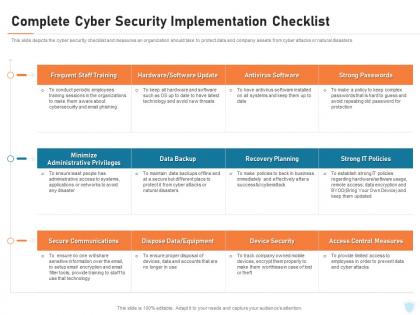 Complete cyber security implementation checklist cyber security it ppt slides portrait
Complete cyber security implementation checklist cyber security it ppt slides portraitThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Present the topic in a bit more detail with this Complete Cyber Security Implementation Checklist Cyber Security IT Ppt Slides Portrait. Use it as a tool for discussion and navigation on Training, Antivirus Software, Secure Communications, Access Control Measures, Device Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security it implementation of strong password policy ppt powerpoint ideas example
Cyber security it implementation of strong password policy ppt powerpoint ideas exampleThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Increase audience engagement and knowledge by dispensing information using Cyber Security IT Implementation Of Strong Password Policy Ppt Powerpoint Ideas Example. This template helps you present information on four stages. You can also present information on Implementation Of Strong Password Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
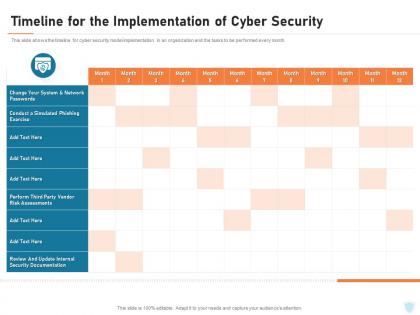 Cyber security it timeline for the implementation of cyber security ppt icon slide portrait
Cyber security it timeline for the implementation of cyber security ppt icon slide portraitThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Cyber Security IT Timeline For The Implementation Of Cyber Security Ppt Icon Slide Portrait. Use it as a tool for discussion and navigation on Internal Security Documentation, Network Passwords, Risk Assessments, Perform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security it impact on organization after implementing cyber security strategy and training
Cyber security it impact on organization after implementing cyber security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Cyber Security IT Impact On Organization After Implementing Cyber Security Strategy And Training. Use it as a tool for discussion and navigation on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
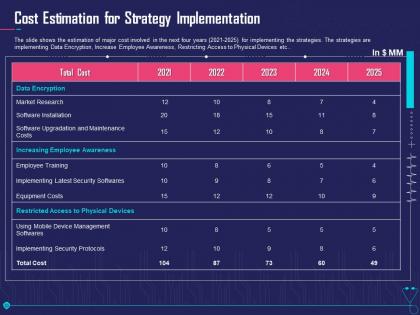 Cost estimation for strategy implementation overcome challenge cyber security healthcare
Cost estimation for strategy implementation overcome challenge cyber security healthcareThe slide shows the estimation of major cost involved in the next four years 2021 to 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Present the topic in a bit more detail with this Cost Estimation For Strategy Implementation Overcome Challenge Cyber Security Healthcare. Use it as a tool for discussion and navigation on Software, Implementing, Security, Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effect after implementing cyber risk security awareness program department ppt ideas
Effect after implementing cyber risk security awareness program department ppt ideasThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Increase audience engagement and knowledge by dispensing information using Effect After Implementing Cyber Risk Security Awareness Program Department Ppt Ideas. This template helps you present information on four stages. You can also present information on Effect After Implementing Cyber Risk Security Awareness Program using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Corporate data security awareness effect after implementing cyber risk security awareness program ppt tips
Corporate data security awareness effect after implementing cyber risk security awareness program ppt tipsThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Corporate Data Security Awareness Effect After Implementing Cyber Risk Security Awareness Program Ppt Tips. Use it as a tool for discussion and navigation on Accounts Department, Sales Department, It Department, R And D Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organization cyber security dashboard implementing security awareness program ppt clipart
Organization cyber security dashboard implementing security awareness program ppt clipartThis slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Present the topic in a bit more detail with this Organization Cyber Security Dashboard Implementing Security Awareness Program Ppt Clipart. Use it as a tool for discussion and navigation on Organization Cyber Security Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security awareness effect after implementing cyber risk security awareness program ppt styles
Information security awareness effect after implementing cyber risk security awareness program ppt stylesThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Information Security Awareness Effect After Implementing Cyber Risk Security Awareness Program Ppt Styles. Use it as a tool for discussion and navigation on Accounts Department, Sales Department, It Department, R And D Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Action Plan For Firewall Implementation In Organization
Firewall Implementation For Cyber Security Action Plan For Firewall Implementation In OrganizationThis slide outlines the action plan for firewall deployment in a company. The purpose of this slide is to highlight the detailed steps to follow while implementing a firewall in a network, such as assessment and requirement gathering, firewall type selection, vendor selection, and so on. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Action Plan For Firewall Implementation In Organization. Use it as a tool for discussion and navigation on Assessment And Requirements Gathering, Vendor Selection, Rollout Plan Creation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Before Vs After Firewall Implementation In Organization
Firewall Implementation For Cyber Security Before Vs After Firewall Implementation In OrganizationThis slide compares the company before and after firewall implementation situation. The purpose of this slide is to showcase the decline in malware attacks on different departments after implementing firewall network security. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Before Vs After Firewall Implementation In Organization. Dispense information and present a thorough explanation of Before Firewall Implementation, After Firewall Implementation, Firewall Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Budget For Cyber Security Awareness Training Program
Firewall Implementation For Cyber Security Budget For Cyber Security Awareness Training ProgramThis slide describes the breakdown of the allocated budget for the firewall and cyber security awareness training program. The purpose of this slide is to showcase the estimated cost and cost components such as instructor cost, training material cost, and so on. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Budget For Cyber Security Awareness Training Program. Dispense information and present a thorough explanation of Allocated Budget, Firewall And Cyber Security, Awareness Training Program, Instructor Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Cyber Security Awareness Training Schedule
Firewall Implementation For Cyber Security Cyber Security Awareness Training ScheduleThis slide represents the cyber security awareness training schedule for an organization staff. The purpose of this slide is to showcase the various training modules to be covered, such as phishing awareness, password security, safe internet and email usage, and so on. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Cyber Security Awareness Training Schedule. Use it as a tool for discussion and navigation on Phishing Awareness, Password Security, Social Engineering Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware Attacks
Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware AttacksThis slide represents the number of attacks on each department in an organization. The purpose of this slide is to showcase the department-wise incident analysis of cyber-attacks on different departments such as finance, R and D, sales and marketing HR, IT, and others. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware Attacks. Dispense information and present a thorough explanation of Research And Development, Sales And Marketing, Incident Analysis, Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Firewall Network Performance Tracking Dashboard
Firewall Implementation For Cyber Security Firewall Network Performance Tracking DashboardThis slide outlines the overall performance of a firewall-protected network. The purpose of this slide is to showcase the total traffic, traffic by application, URLs by actions, threats by severity, traffic by source IP, traffic by application, blocked URLs by category, threats by severity, and so on. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Firewall Network Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Firewall Network Performance, Tracking Dashboard, Traffic By Application, Firewall Protected Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Firewall Network Traffic Monitoring Dashboard
Firewall Implementation For Cyber Security Firewall Network Traffic Monitoring DashboardThis slide showcases the network traffic monitoring dashboard by firewall mechanism. The purpose of this slide is to showcase the different aspects of network traffic, such as traffic by zone, URL categories by traffic, applications by traffic, traffic source IP, and so on. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Firewall Network Traffic Monitoring Dashboard. Dispense information and present a thorough explanation of Firewall Network Traffic, Monitoring Dashboard, Applications By Traffic, Firewall Mechanism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Global Firewall Market Segmentation By Deployment And Solution
Firewall Implementation For Cyber Security Global Firewall Market Segmentation By Deployment And SolutionThis slide provides an overview of global firewall market categorization based on deployment and solution type. The purpose of this slide is to showcase the firewall market share based on deployment types and solution type, such as software and hardware services. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Global Firewall Market Segmentation By Deployment And Solution. Use it as a tool for discussion and navigation on Global Firewall Market, Software And Hardware Services, Market Segmentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Global Market Summary Of Firewall Network Security
Firewall Implementation For Cyber Security Global Market Summary Of Firewall Network SecurityThis slide illustrates the worldwide market analysis for firewall network security. The purpose of this slide is to give an overview of the global firewall network security market, including CAGR rate, regional analysis, organization size segment, and key players. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Global Market Summary Of Firewall Network Security. Dispense information and present a thorough explanation of Worldwide Market Analysis, Firewall Network Security, Global Firewall Network Security Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Malware Attacks Experienced By Company In Previous Year
Firewall Implementation For Cyber Security Malware Attacks Experienced By Company In Previous YearThis slide depicts the number of malware attack incidents faced by the organization in the previous year. The purpose of this slide is to showcase the monthly malware attacks experienced by the company in the absence of a firewall mechanism. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Malware Attacks Experienced By Company In Previous Year. Use it as a tool for discussion and navigation on Malware Attacks Experienced, Firewall Mechanism. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Problems With Current Network Security System
Firewall Implementation For Cyber Security Problems With Current Network Security SystemThis slide highlights the loss experienced by the organization due to the existing security system. The purpose of this slide is to showcase the various cyber attack incidents and losses caused by them to the organization, such as malware infections, unauthorized access, phishing, etc. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Problems With Current Network Security System. Use it as a tool for discussion and navigation on Existing Security System, Cyber Attack Incidents, Malware Infections, Unauthorized Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall System
Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall SystemThis slide represents the dashboard for threat tracking in a firewall-protected network. The purpose of this slide is to showcase the various threats based on categories such as threats by owners, risk by threats, threat report, monthly threat status, current risk status, and threats based on user role. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall System. Dispense information and present a thorough explanation of Threat Tracking Dashboard, Firewall System, Current Risk Status, Firewall Protected Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Firewall Implementation For Cyber Security Ppt Icon Slide Portrait
Table Of Contents For Firewall Implementation For Cyber Security Ppt Icon Slide PortraitIntroducing Table Of Contents For Firewall Implementation For Cyber Security Ppt Icon Slide Portrait to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Method Selection, Budget Allocation, Importance Of Firewall Implementation, using this template. Grab it now to reap its full benefits.
-
 Dashboard To Evaluate Current Cyber Risk Score Implementing Organizational Security Training
Dashboard To Evaluate Current Cyber Risk Score Implementing Organizational Security TrainingThe slide assists in evaluating the current cyber risk score after imparting cyber security awareness training in the organization. Present the topic in a bit more detail with this Dashboard To Evaluate Current Cyber Risk Score Implementing Organizational Security Training. Use it as a tool for discussion and navigation on High, Medium, Low. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda For Firewall Implementation For Cyber Security Ppt Ideas Infographic Template
Agenda For Firewall Implementation For Cyber Security Ppt Ideas Infographic TemplateIntroducing Agenda For Firewall Implementation For Cyber Security Ppt Ideas Infographic Template to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Firewall Implementation, Cyber Security, Performance Gap Analysis, Team Structure, using this template. Grab it now to reap its full benefits.
-
 Firewall Implementation For Cyber Security Budget Allocation For Firewall Implementation Project
Firewall Implementation For Cyber Security Budget Allocation For Firewall Implementation ProjectThis slide outlines the budget allocation plan for firewall implementation in an organization. The purpose of this slide is to showcase the allocated cost and cost components such as hardware software, licensing fees, professional services, training and staff education, etc. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Budget Allocation For Firewall Implementation Project. Use it as a tool for discussion and navigation on Professional Services, Network Assessment And Design, Testing And Quality Assurance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Deployment Method Selection Of Firewall Network Security
Firewall Implementation For Cyber Security Deployment Method Selection Of Firewall Network SecurityThis slide represents the implementation methods of firewall security systems. The purpose of this slide is to showcase the different implementation options of firewall security systems, such as software-based applications, hardware-based applications, and cloud-based applications. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Deployment Method Selection Of Firewall Network Security. Use it as a tool for discussion and navigation on Network Segmentation, Supports Network Segmentation, Hardware For Security Functions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Firewall Architecture Implementation Strategy Selection
Firewall Implementation For Cyber Security Firewall Architecture Implementation Strategy SelectionThis slide represents the comparative analysis of various firewall implementation architecture strategies. The purpose of this slide is to compare the three firewall architecture implementation strategies, such as packet filtering routers, screened host firewalls, and screened subset firewalls. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Firewall Architecture Implementation Strategy Selection. Dispense information and present a thorough explanation of Firewall Architecture, Strategy Selection, Screened Host Firewalls, Screened Subset Firewalls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Firewall Training Schedule For It Professionals
Firewall Implementation For Cyber Security Firewall Training Schedule For It ProfessionalsPresent the topic in a bit more detail with this Firewall Implementation For Cyber Security Firewall Training Schedule For It Professionals. Use it as a tool for discussion and navigation on Firewall Components, Intrusion Prevention And Detection, Firewall Maintenance And Troubleshooting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security For Table Of Contents Ppt Ideas Inspiration
Firewall Implementation For Cyber Security For Table Of Contents Ppt Ideas InspirationDeliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security For Table Of Contents Ppt Ideas Inspiration. Dispense information and present a thorough explanation of Firewall Implementation, Cyber Security, Firewall Network Performance, Tracking Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security How Firewall Implementation Will Improve Network Security
Firewall Implementation For Cyber Security How Firewall Implementation Will Improve Network SecurityThis slide talks about the main advantages of a firewall security system. The purpose of this slide is to highlight the key benefits of a firewall for businesses, such as spyware protection, the significant barrier against viruses, protection against hacking, privacy promotion, and network traffic monitoring. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security How Firewall Implementation Will Improve Network Security. Use it as a tool for discussion and navigation on Prevents Hacking, Privacy Promotion, Spyware Protection, Network Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Impact Of Poor Network Security System On Business
Firewall Implementation For Cyber Security Impact Of Poor Network Security System On BusinessThis slide outlines the impact of the existing network security system on the company. The purpose of this slide is to showcase the incidents that happen because of poor network security and the total losses caused by those incidents, such as data breaches and loss, downtime, and so on. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Impact Of Poor Network Security System On Business. Dispense information and present a thorough explanation of Downtime And Productivity Loss, Intellectual Property Theft, Legal And Regulatory Consequences using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Network Security Management 90 Days Plan
Firewall Implementation For Cyber Security Network Security Management 90 Days PlanDeliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Network Security Management 90 Days Plan. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Network Security Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





