Powerpoint Templates and Google slides for Implementing Cyber Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats
Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi factor authentication, conducting test etc. Introducing Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Password Test, Password Encryption, Multi Factor Authentication using this template. Grab it now to reap its full benefits.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security Threats
Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Deliver an outstanding presentation on the topic using this Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Document Management, Target Audience, Proposed Date using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats
Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Increase audience engagement and knowledge by dispensing information using Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Time Consuming Process, Speedy Process, Incremental Backup using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats
Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Present the topic in a bit more detail with this Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Objectives, Features, Duration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats
Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Deliver an outstanding presentation on the topic using this Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cloud Security, Information Security, Disaster Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats
Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Present the topic in a bit more detail with this Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Features, Free Trial, Cost This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Implementing Strategies To Mitigate Cyber Security Threats
Table Of Contents Implementing Strategies To Mitigate Cyber Security ThreatsIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Industry Overview, Current Scenario Analysis, Cyber Security Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats
Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the various types of cyber attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service tec. Introducing Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Ransomware, Phishing using this template. Grab it now to reap its full benefits.
-
 Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness Among
Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness AmongThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Introducing Implementing Strategies To Mitigate Cyber Security Data Highlighting Cyber Security Unawareness Among to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Email Attachments, Systems, Employees using this template. Grab it now to reap its full benefits.
-
 Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence
Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk OccurrenceThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Evaluate Impact And Probability Of Risk Occurrence Use it as a tool for discussion and navigation on Parameters, Impact, Probability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix
Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity MatrixThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Introducing Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Very Severe, Severe, Moderate using this template. Grab it now to reap its full benefits.
-
 Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management
Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access ManagementThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management Use it as a tool for discussion and navigation on Access Request, Approval Rules, Session Proxy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Review Cyber Security Status With Due Diligence Checklist
Implementing Strategies To Mitigate Cyber Security Review Cyber Security Status With Due Diligence ChecklistThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Deliver an outstanding presentation on the topic using this Implementing Strategies To Mitigate Cyber Security Review Cyber Security Status With Due Diligence Checklist Dispense information and present a thorough explanation of Parameters, Tasks, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Future Cyber Security Trends Implementing Project Governance Framework For Quality PM SS
Future Cyber Security Trends Implementing Project Governance Framework For Quality PM SSThis slide shows future cyber-security trends for managing activities in project governance with more effectiveness and efficiency. It includes latest trends such as zero trust policy, behavioural analytics and quantum self-encryption, etc. Present the topic in a bit more detail with this Future Cyber Security Trends Implementing Project Governance Framework For Quality PM SS. Use it as a tool for discussion and navigation on Cloud Security, Behavioural Analytics, Trust Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement ATP Cyber Security Strategies In Organisation
Implement ATP Cyber Security Strategies In OrganisationThis slide depicts the strategies for cyber security ATP. Its objective is to help formulate advanced strategies for threat protection. This slide includes broad test repository, benign software behaviour, analysis of data, etc. Presenting our set of slides with name Implement ATP Cyber Security Strategies In Organisation. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Broad Test Repository, Benign Software Behaviour, Analysis Of Data.
-
 Key Considerations Before Implementing Cyber Security Mesh
Key Considerations Before Implementing Cyber Security MeshThe following slide emphasizes essential factors like connecting to VMs, developing tooling, observability, multi-cluster security, and mesh capabilities in pre-implementation considerations for cybersecurity mesh. This aids in preparing a robust strategy for successful cyber mesh integration. Presenting our set of slides with Key Considerations Before Implementing Cyber Security Mesh This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Deployment Tooling, Exposing Mesh Capabilities, Observability
-
 Benefits Of Implementing NIPS Cyber Security
Benefits Of Implementing NIPS Cyber SecurityThis slide depicts the advantages of executing NIPS cybersecurity. This slide aims to help the business leverage NIPS cybersecurity to prevent external attacks. It includes advantages such as reducing the likelihood of cyber attacks, increasing threat protection, etc. Introducing our Benefits Of Implementing NIPS Cyber Security set of slides. The topics discussed in these slides are Advantages, Description, Impact This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 30 60 90 Day Plan For Cyber Security Framework Implementation
30 60 90 Day Plan For Cyber Security Framework ImplementationThis slide discusses the 30-60-90-day plan for cyber security framework implementation which include stakeholder alignment, awareness training and so on. Introducing 30 60 90 Day Plan For Cyber Security Framework Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Stakeholder Alignment, Conduct Initial Gap Analysis, Conduct Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Of Cyber Security Framework Implementation
Before Vs After Of Cyber Security Framework ImplementationThis slide discusses the before vs after impact of cyber security framework implementation based on aspects like security posture, incident response, etc. Present the topic in a bit more detail with this Before Vs After Of Cyber Security Framework Implementation. Use it as a tool for discussion and navigation on Incident Response, Cyber Security, Framework Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Framework Implementation Budget
Cyber Security Framework Implementation BudgetThis slide discusses the implementation budget for cyber security framework which includes compliance requirements, risk assessments and security training. Deliver an outstanding presentation on the topic using this Cyber Security Framework Implementation Budget. Dispense information and present a thorough explanation of Compliance Requirements, Risk Assessments, Security Training, Security Requirements For Business Initiatives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Framework Implementation Challenges
Cyber Security Framework Implementation ChallengesThis slide discusses the major challenges of cyber security framework implementation which include budget constraints, lack of integration and so on. Introducing Cyber Security Framework Implementation Challenges to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Insufficiently Trained Personnel, Budget Constraints, Cyber Security Framework, Implementation Challenges, using this template. Grab it now to reap its full benefits.
-
 Need For Implementing Cyber Security Framework
Need For Implementing Cyber Security FrameworkThis slide highlights the need for implementing cyber security framework which includes easily adaptable and cost efficient, collaboration opportunities, etc. Introducing Need For Implementing Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Collaboration Opportunities, Easily Maintain Compliance, Secure Supply Chain, using this template. Grab it now to reap its full benefits.
-
 Strategies For Implementing AI Powered Global Technology In Cyber Security
Strategies For Implementing AI Powered Global Technology In Cyber SecurityThis slide shows strategic approaches for implementing AI in cyber security. The purpose of this slide is to strengthen organizations defence against potential cyber attacks to maximize effectiveness of global technological solutions. It covers strategies such as resource allocation, training data, internal processes, etc. Presenting our set of slides with Strategies For Implementing AI Powered Global Technology In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resource Allocation, Training Data, Internal Processes.
-
 Best Practices For Implementing Hids Cyber Security
Best Practices For Implementing Hids Cyber SecurityThis slide represents best practices for implementing HIDS cyber security which monitors IT systems for signs of suspicious activities and unusual behaviours. It includes best practices for implementing HIDS cyber security such as monitor all hosts, contextualize data, etc Introducing our premium set of slides with Best Practices For Implementing Hids Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitor All Hosts, Contextualize Data, Consider Agentless HIDS. So download instantly and tailor it with your information.
-
 Gamification Implementation In Cyber Security Recruitment Best Practices
Gamification Implementation In Cyber Security Recruitment Best PracticesThe purpose of this slide is to ensure that gamified components are consistent with organizations culture and values and create fun and competitive atmosphere for applicants including best practices such as aligning gamification with company culture and values, promoting diversity and inclusion, etc. Introducing our premium set of slides with name Gamification Implementation In Cyber Security Recruitment Best Practices. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Design Meaningful Challenges, Make Process Enjoyable, Promote Diversity And Inclusion, Cyber Security Recruitment. So download instantly and tailor it with your information.
-
 Process To Implement Gamified Cyber Security Training
Process To Implement Gamified Cyber Security TrainingThe purpose of this slide is to create a gamified cybersecurity training program that captures attention of users also achieves specific, measurable improvements in cybersecurity awareness and skills including steps such as identifying learning objectives, structuring activities and challenges, etc. Introducing our premium set of slides with name Process To Implement Gamified Cyber Security Training. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Learning Objectives, Structure Activities And Challenges, Cyber Security Training. So download instantly and tailor it with your information.
-
 Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat
Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about business cyber security attack recovery plan. It includes key steps such as setting time based recovery goals, impact and risk assessment, build recovery team, communication plan, recovery strategies implementation, etc. Introducing Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Communication Plan, Recovery Strategies Implementation, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Implement Ethics In Data Cyber Security
Best Practices To Implement Ethics In Data Cyber SecurityThis slide represents various best practices that assist companies to implement ethics to enhance their data cybersecurity. It include various best practices such as ethical code of conduct, ethical hacking and testing, third-party ethics. Introducing our Best Practices To Implement Ethics In Data Cyber Security set of slides. The topics discussed in these slides are Best Practices, Details, Impact. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Implement Ethics In Corporate Cyber Security
Checklist To Implement Ethics In Corporate Cyber SecurityThis slide represents checklist that assist companies to implement ethical considerations in information cyber security effectively. It includes various actions such as developing incident response plan, executing safeguard system, etc. Presenting our well structured Checklist To Implement Ethics In Corporate Cyber Security. The topics discussed in this slide are Collect Informed Consent, Data Collection, Processing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Rationale Of Implementing Ethics In Cyber Security
Rationale Of Implementing Ethics In Cyber SecurityThis slide represents various rationales of implementing ethics that assist companies in enhancing their cybersecurity practices effectively. It includes various rationales such as protection of privacy and data, trust and reputation, etc. Introducing our premium set of slides with Rationale Of Implementing Ethics In Cyber Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trust And Reputation, Long Term Sustainability, Protection Privacy Data. So download instantly and tailor it with your information.
-
 Ai Technology Implementation Icon For Robust OT Cyber Security
Ai Technology Implementation Icon For Robust OT Cyber SecurityPresenting our set of slides with Ai Technology Implementation Icon For Robust OT Cyber Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Technology Implementation Icon, Robust OT Cyber Security
-
 Roadmap To Implement Robust OT Cyber Security
Roadmap To Implement Robust OT Cyber SecurityThis slide represents roadmap that guides companies to implement strong operational technology cybersecurity model for enhancing information protection. It includes various steps such as conducting OT threat assessment, know network and assets, etc. Presenting our set of slides with Roadmap To Implement Robust OT Cyber Security This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct OT Threat Assessment, Know Network And Assets, Publish OT Security Policy
-
 Best Practices To Implement NIDS For Maintaining Effective Cyber Security
Best Practices To Implement NIDS For Maintaining Effective Cyber SecurityThis Slide Represents Effective Strategies For Employing NIDS. It Aims To Help Organizations Implement NIDS To Detect, Respond And Mitigate Cyber Threats Within Networks. Introducing Our Premium Set Of Slides With Best Practices To Implement NIDS For Maintaining Effective Cyber Security. Ellicudate The Three Stages And Present Information Using This PPT Slide. This Is A Completely Adaptable Powerpoint Template Design That Can Be Used To Interpret Topics Like Proper Network Segmentation, Thorough Traffic Analysis, Signature Database Upgradation. So Download Instantly And Tailor It With Your Information.
-
 Solutions To Overcome Challenges For Implementing Cyber Security In Banking
Solutions To Overcome Challenges For Implementing Cyber Security In BankingThis slide showcases key solutions to overcome problems in banking cyber security. This slide aims to implement security solutions to prevent instances of misused or lost data and counter emerging cyber attacks. It includes various elements such as challenges, solutions and impact. Presenting our well structured Solutions To Overcome Challenges For Implementing Cyber Security In Banking. The topics discussed in this slide are Knowledge, Ransomware, Social Media. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Penetration Testing Implementation Plan Stages Of Penetration Testing In Cyber Security
Penetration Testing Implementation Plan Stages Of Penetration Testing In Cyber SecurityThis slide represents the process included in penetration testing. The purpose of this slide is to showcase the different steps of penetration testing, such as planning the penetration test, gathering information, scanning for vulnerabilities, and so on. Increase audience engagement and knowledge by dispensing information using Penetration Testing Implementation Plan Stages Of Penetration Testing In Cyber Security. This template helps you present information on Six stages. You can also present information on Plan The Penetration Test, Gather Information, Scan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS
United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SSThis slide showcases the United nations and cyber security initiatives. It includes initiatives such as UN general assembly resolutions, UNODA, UNIDIR, CTC and UNODC.Increase audience engagement and knowledge by dispensing information using United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS. This template helps you present information on five stages. You can also present information on General Assembly Resolutions, Disarmament Affairs, Disarmament Research using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt Demonstration
Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt DemonstrationThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt Demonstration. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks, Previous Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it impact of implementing cyber security measures in the company
Cyberterrorism it impact of implementing cyber security measures in the companyThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Present the topic in a bit more detail with this Cyberterrorism IT Impact Of Implementing Cyber Security Measures In The Company. Use it as a tool for discussion and navigation on Number Attacks, Cyber Terrorists Attacks 2021, Cyber Terrorists Attacks 2022. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Terrorism Attacks Impact Of Implementing Cyber Security
Cyber Terrorism Attacks Impact Of Implementing Cyber SecurityThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Cyber Terrorism Attacks Impact Of Implementing Cyber Security. Dispense information and present a thorough explanation of Impact Of Implementing Cyber Security Measures In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness Training
Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness TrainingThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Present the topic in a bit more detail with this Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Desired State, Reasons Identified, Approaches To Be Deployed. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPI Dashboard To Monitor Cyber Security Performance Implementing Security Awareness Training
KPI Dashboard To Monitor Cyber Security Performance Implementing Security Awareness TrainingThe purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. Deliver an outstanding presentation on the topic using this KPI Dashboard To Monitor Cyber Security Performance Implementing Security Awareness Training. Dispense information and present a thorough explanation of Asset Type Control, Control Issues By Standard, Review Effectiveness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training
KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness TrainingThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Current Risk Status, Threats By Owners, Risk By Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training
Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness TrainingThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, Malware, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksPresent the topic in a bit more detail with this Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks. Use it as a tool for discussion and navigation on Security Awareness, Current Assessment, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt Demonstration
Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt DemonstrationThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt Demonstration. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Implementing Cyber Security Incident Management Ppt Topics
Financial Implementing Cyber Security Incident Management Ppt TopicsPresent the topic in a bit more detail with this Financial Implementing Cyber Security Incident Management Ppt Topics. Use it as a tool for discussion and navigation on Minimum, Medium, Maximum. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
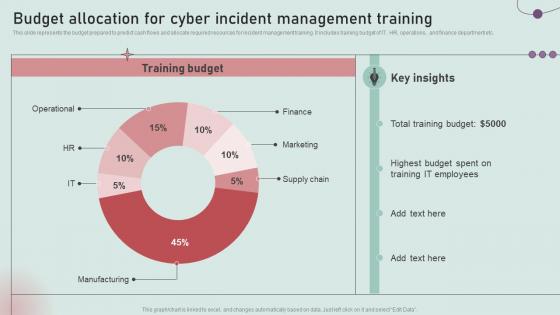 Budget Allocation For Cyber Incident Management Training Development And Implementation Of Security
Budget Allocation For Cyber Incident Management Training Development And Implementation Of SecurityThis slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Deliver an outstanding presentation on the topic using this Budget Allocation For Cyber Incident Management Training Development And Implementation Of Security. Dispense information and present a thorough explanation of Total Training Budget, It Employees, Highest Budget using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response KPI Dashboard Development And Implementation Of Security Incident
Cyber Security Incident Response KPI Dashboard Development And Implementation Of Security IncidentThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response KPI Dashboard Development And Implementation Of Security Incident. Dispense information and present a thorough explanation of Total Financial Risk, Compliance, Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security
Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of SecurityThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security. Dispense information and present a thorough explanation of Medium Risk, Unresolved Side, Inactive Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
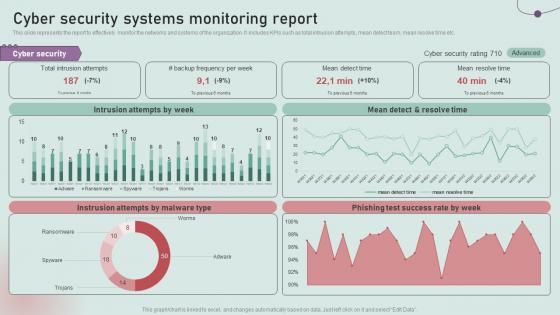 Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management
Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Deliver an outstanding presentation on the topic using this Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management. Dispense information and present a thorough explanation of Intrusion Attempts, Mean Detect, Resolve Time using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
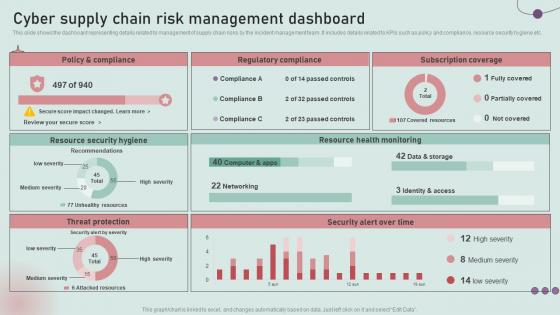 Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident
Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security IncidentThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Deliver an outstanding presentation on the topic using this Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident. Dispense information and present a thorough explanation of Regulatory Compliance, Subscription Coverage, Resource Health using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
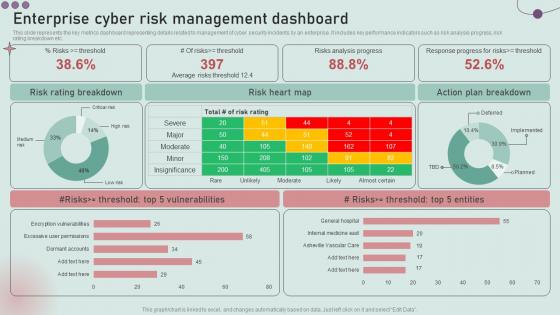 Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident
Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security IncidentThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Heart Map, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorism
Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorismThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism. This template helps you present information on four stages. You can also present information on Creating Personal Accounts, Awareness Training Employees, Keep Hardware And Software Updated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it timeline for implementation of cyber security in the company
Cyberterrorism it timeline for implementation of cyber security in the companyThis slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Present the topic in a bit more detail with this Cyberterrorism IT Timeline For Implementation Of Cyber Security In The Company. Use it as a tool for discussion and navigation on Changes System, Network Passwords, Penetration Test. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roadmap To Implement Cyber Security Cyber Terrorism Attacks
Roadmap To Implement Cyber Security Cyber Terrorism AttacksThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Introducing Roadmap To Implement Cyber Security Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Personal Accounts, Awareness Training, Software Updated, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Implementation Of Cyber Security
Roadmap For Implementation Of Cyber SecurityThis slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting our set of slides with name Roadmap For Implementation Of Cyber Security. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Roadmap, Implementation, Assessment.
-
 Cyber Security Transformation Strategy With Implementation
Cyber Security Transformation Strategy With ImplementationThe following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Introducing our premium set of slides with name Cyber Security Transformation Strategy With Implementation. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implementation, Mobilization, Vision, Analysis. So download instantly and tailor it with your information.
-
 Third Party Cyber Security Implementation Checklist
Third Party Cyber Security Implementation ChecklistIntroducing our premium set of slides with name Third Party Cyber Security Implementation Checklist. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party Cyber Security, Implementation Checklist. So download instantly and tailor it with your information.





