Powerpoint Templates and Google slides for Implementation Of Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SSThis slide highlights the impact of deploying effective Intrusion prevention system solution on organizational operations, such as increased real-time threat visibility, proactive threat detection etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Increase In Real-Time Threat Visibility, Increase In Proactive Threat Detection Rates, Decrease In Average Cost Per Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity Techniques
Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity TechniquesThis slide showcases best practices required for securing data. This template focuses on maintaining continuity of operations and minimizing potential for costly interruptions. It covers aspects related to threat detection, firewall, antivirus software, etc. Increase audience engagement and knowledge by dispensing information using Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity Techniques. This template helps you present information on four stages. You can also present information on Threat Detection And Prevention, Antivirus Software, Two Factor Authentication, Cybersecurity Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
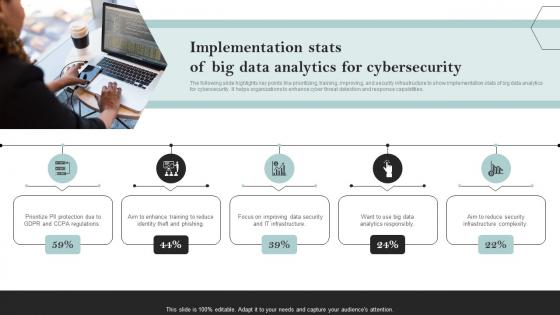 Implementation Stats Of Big Data Analytics For Cybersecurity
Implementation Stats Of Big Data Analytics For CybersecurityThe following slide highlights key points like prioritizing, training, improving, and security infrastructure to show implementation stats of big data analytics for cybersecurity. It helps organizations to enhance cyber threat detection and response capabilities. Introducing our premium set of slides with Implementation Stats Of Big Data Analytics For Cybersecurity. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulations, Reduce, Improving. So download instantly and tailor it with your information.
-
 Benefits Of Implementing Cybersecurity Measures To Safeguard It Infrastructure
Benefits Of Implementing Cybersecurity Measures To Safeguard It InfrastructureThis slide highlights the cybersecurity measures implemented to safeguard the It infrastructure. The purpose of this slide is to help the business capitalize on the benefits such as protection against cyber attacks, protection of data networks, etc. Presenting our set of slides with Benefits Of Implementing Cybersecurity Measures To Safeguard It Infrastructure This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Protection Against, Data Networks, Unauthorized Access
-
 Five Levels Of Opsec Cybersecurity Implementation
Five Levels Of Opsec Cybersecurity ImplementationThis slide showcases the five levels of opsec cybersecurity implementation. The purpose of this slide is to help the business implement all five levels to maintain cybersecurity. It includes levels such as identification of sensitive information, assessment of vulnerabilities, etc. Introducing our premium set of slides with Five Levels Of Opsec Cybersecurity Implementation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Sensitive Information, Recognize Potential Threats, Asses Vulnerabilities . So download instantly and tailor it with your information.
-
 Key Practices For Implementation Of Opsec Cybersecurity
Key Practices For Implementation Of Opsec CybersecurityThis slide depicts the key practices for opsec cybersecurity implementation. This slide aims to help the business leverage opsec through practices such as implementation of relevant processes, selection of suitable providers, restriction of access to networks, etc. Introducing our premium set of slides with Key Practices For Implementation Of Opsec Cybersecurity. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Practices, Description, Networks And Devices. So download instantly and tailor it with your information.
-
 Benefits Of Implementing Cybersecurity In Education Organization
Benefits Of Implementing Cybersecurity In Education OrganizationThis slide showcases the advantages of utilizing cybersecurity in education institutes to enhance their safety. The purpose of this slide is to help the business leverage cybersecurity to improve its overall security. It includes advantages such as protection of user information, remote workspace management, etc. Introducing our Benefits Of Implementing Cybersecurity In Education Organization set of slides. The topics discussed in these slides are Protect User Information, Remote Workspace Management, Streamline Access Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS
IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT device identity platform deployment, referable for businesses in developing mitigation process. It provides details about APIs, architecture, device client, etc. Deliver an outstanding presentation on the topic using this IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Device, Platform Deployment, Developing Mitigation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS
Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security strategy timeline, referable for developers and businesses in protection of connected devices. It provides details about credentials, authentication, cryptography, etc. Introducing Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Avoid Unnecessary Data Handling, Cryptographic Network Protocol Usage, Enforce Authentication Controls, using this template. Grab it now to reap its full benefits.
-
 IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS
IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS. This template helps you present information on one stages. You can also present information on Phishing Awareness, Objectives, Detecting Phishing Attacks, Preventing Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS
Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SSThis slide represents details related to need of implementing training program for employees regarding attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. Introducing Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Anti Phishing Training Program, Steal Sensitive Information, Employees Regarding Attacks, using this template. Grab it now to reap its full benefits.
-
 Case Study Of Implementing Mdr Cybersecurity For Aws
Case Study Of Implementing Mdr Cybersecurity For AwsThis slide represents case study that assist companies to understand applications of MDR cybersecurity solutions to enhance network protection, it includes various elements such as overview, challenges, solutions, and impact. Introducing our premium set of slides with Case Study Of Implementing Mdr Cybersecurity For Aws. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Overview, Challenges, Solutions. So download instantly and tailor it with your information.
-
 Rationales Of Implementing Mdr Cybersecurity In Smbs
Rationales Of Implementing Mdr Cybersecurity In SmbsThis slide represents various rationales of MDR cybersecurity that assist small and medium-sized businesses to enhance their data protection effectively. It includes rationales such as incident investigation, alert triage, remediation, etc. Presenting our set of slides with Rationales Of Implementing Mdr Cybersecurity In Smbs. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Incident Investigation, Remediation, Proactive Threat Hunting.
-
 Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Cisco data centers . It includes details related to problems, solutions, use cases and outcomes of deploying IPS by Cisco data centers. Present the topic in a bit more detail with this Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Softwares, Features, USP, Pricing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
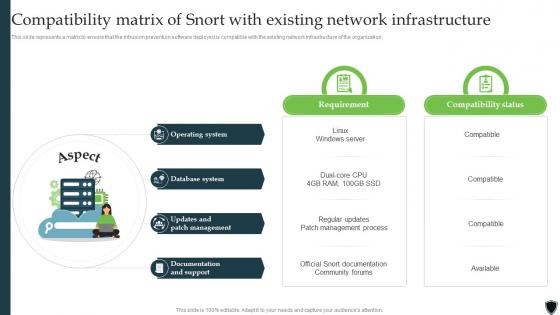 Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS
Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SSThis slide represents a matrix to ensure that the intrusion prevention software deployed is compatible with the existing network infrastructure of the organization. Introducing Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Operating System, Database System, Updates And Patch Management, Documentation And Support, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SSThis slide shows the cost-benefit analysis of deploying Intrusion prevention system, including the costs incurred in deploying IPS platform and providing training to employees. Present the topic in a bit more detail with this Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Initial Cost, Costs, Training Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
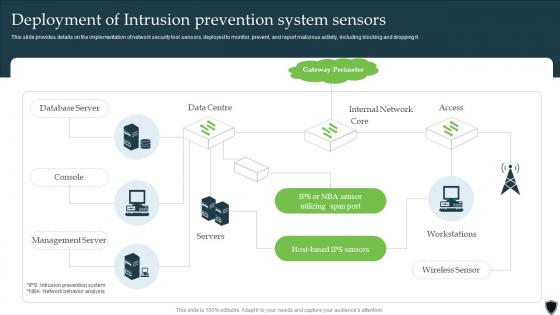 Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SSThis slide provides details on the implementation of network security tool sensors, deployed to monitor, prevent, and report malicious activity, including blocking and dropping it. Introducing Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Database Server, Gateway Perimeter, Workstations, Management Server, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS
Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SSThis slide presents critical assets and associated threats, such as data breaches, information manipulation, data corruption, identity theft, etc., identified by the IT team. Present the topic in a bit more detail with this Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS. Use it as a tool for discussion and navigation on Critical Assets, Network Infrastructure, Application Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS
Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SSThis slide compares the best end-to-end encryption software solutions based on different parameters such as password management, on-the-fly decryption, and enterprise-grade decryption.Deliver an outstanding presentation on the topic using this Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Offers Support, Password Management, Enterprise Grade Decryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SS
First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to first line of defense offered by implemented end to end encryption solution. It includes details related to process for device attestation.Introducing First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Device Management, Certificate Authority, Automatic Certificate Management Environment, using this template. Grab it now to reap its full benefits.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS
Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SSIntroducing Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Best Practices, Training Plan For Identification, using this template. Grab it now to reap its full benefits.
-
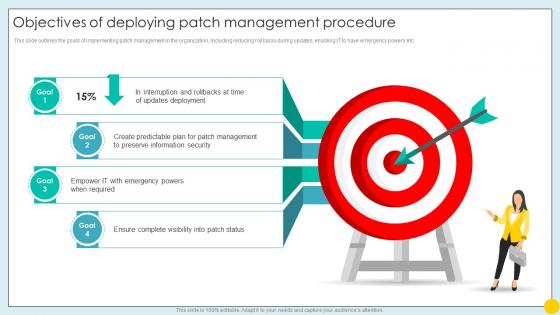 Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the goals of implementing patch management in the organization, including reducing rollbacks during updates, enabling IT to have emergency powers etc.Introducing Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Updates Deployment, Preserve Information Security, Ensure Complete Visibility, using this template. Grab it now to reap its full benefits.
-
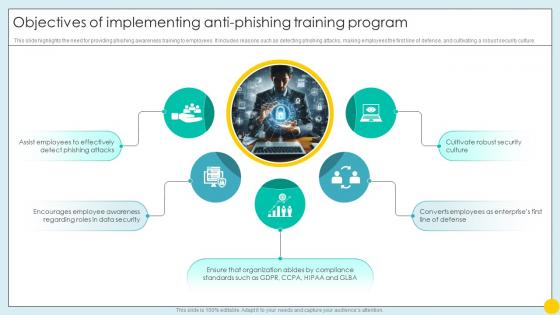 Objectives Of Implementing Anti Phishing Training Program Cybersecurity SS
Objectives Of Implementing Anti Phishing Training Program Cybersecurity SSThis slide highlights the need for providing phishing awareness training to employees. It includes reasons such as detecting phishing attacks, making employees the first line of defense, and cultivating a robust security culture.Increase audience engagement and knowledge by dispensing information using Objectives Of Implementing Anti Phishing Training Program Cybersecurity SS. This template helps you present information on five stages. You can also present information on Data Security, Cultivate Robust Security Culture, Effectively Detect Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SS
Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to second line of defense offered by implemented end to end encryption solution. It includes details related to process for certificate authentication.Increase audience engagement and knowledge by dispensing information using Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Certificate Authority, Client, Server using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SS
Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SSThis slide presents statistical data highlighting the importance of patch management in organizational operations. It includes statistics related to breach detection time, prevention of cyber attacks, etc.Introducing Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organizations Possess, Documented Process, Patch Management, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Gap Analysis, Patch Management, Dashboard Tracking, Additional Slides using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a comprehensive training plan to help employees effectively identify various types of phishing attacks, including deceptive phishing, spear phishing, whaling, vishing and smishing.Deliver an outstanding presentation on the topic using this Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Sessions, Training Hours, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
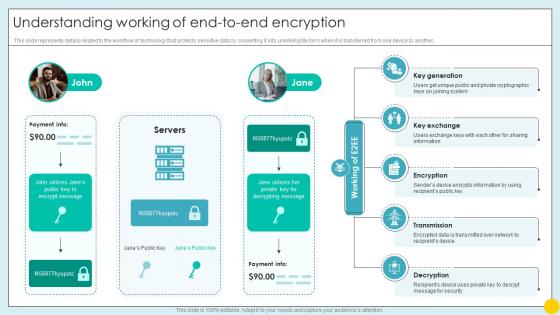 Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS
Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to the workflow of technology that protects sensitive data by converting it into unintelligible form when it is transferred from one device to another. Increase audience engagement and knowledge by dispensing information using Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Key Exchange, Encryption, Transmission, Decryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Reasons Of Implementing Cybersecurity Framework
Major Reasons Of Implementing Cybersecurity FrameworkThis slide covers some of the biggest reason for organization to implement cybersecurity framework in order to manage risks arises in digital world. It includes software,hardware failure,data corruption,malware attack,power loss, backup loss etc. Introducing our Major Reasons Of Implementing Cybersecurity Framework set of slides. The topics discussed in these slides are Hardware, Software, Cybersecurity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Impact Of Cybersecurity Incidents On Organization Implementing Cyber Security Ppt Topics
Impact Of Cybersecurity Incidents On Organization Implementing Cyber Security Ppt TopicsThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Present the topic in a bit more detail with this Impact Of Cybersecurity Incidents On Organization Implementing Cyber Security Ppt Topics. Use it as a tool for discussion and navigation on Operational Disruption, Reputational Damage, Stolen Intellectual Property. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Cybersecurity Incident Management Development And Implementation Of Security
Best Practices For Cybersecurity Incident Management Development And Implementation Of SecurityThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Cybersecurity Incident Management Development And Implementation Of Security. This template helps you present information on five stages. You can also present information on Create Cyber Incident, Management Plan, Establish Roles, Responsibilities Of Team Members using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five Phases Of Cybersecurity Incident Management Development And Implementation Of Security Incident
Five Phases Of Cybersecurity Incident Management Development And Implementation Of Security IncidentThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Introducing Five Phases Of Cybersecurity Incident Management Development And Implementation Of Security Incident to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Assess And Design, Detect And Report, Plan And Prepare, using this template. Grab it now to reap its full benefits.
-
 Gap Analysis Representing Current Situation Of Cybersecurity Development And Implementation Of Security
Gap Analysis Representing Current Situation Of Cybersecurity Development And Implementation Of SecurityThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Deliver an outstanding presentation on the topic using this Gap Analysis Representing Current Situation Of Cybersecurity Development And Implementation Of Security. Dispense information and present a thorough explanation of Report Cyber Security Incidents, Relevant Authority using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of Cybersecurity Incidents On Organization Development And Implementation Of Security Incident
Impact Of Cybersecurity Incidents On Organization Development And Implementation Of Security IncidentThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Increase audience engagement and knowledge by dispensing information using Impact Of Cybersecurity Incidents On Organization Development And Implementation Of Security Incident. This template helps you present information on five stages. You can also present information on Increased Costs, Operational Disruption, Reputational Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity Incidents
Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity IncidentsThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Introducing Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity Incidents to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Privacy, Compliance, Security, using this template. Grab it now to reap its full benefits.
-
 Impact Of Implementing Cybersecurity System Practices
Impact Of Implementing Cybersecurity System PracticesThe following slide highlights the various benefits of adopting cybersecurity framework to assess its success and ensure effective risk management. It includes key elements such as common language, collaboration, due diligence, compliance etc. Introducing our premium set of slides with Impact Of Implementing Cybersecurity System Practices. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Common Language, Collaboration, Due Diligence. So download instantly and tailor it with your information.



