Powerpoint Templates and Google slides for Implement Security Practices
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions
Devsecops Best Practices For Secure Challenges With Devsecops Implementation And SolutionsThis slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions. Dispense information and present a thorough explanation of Security Awareness And Training, Continuous Monitoring And Compliance, Managing Security Debt using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation
Devsecops Best Practices For Secure Key Elements Of Successful Devsecops ImplementationThe slide discusses the critical elements for the successful implementation of DevSecOps. The purpose of this slide is to explain the various features that are integrated automated testing into a pipeline, automated deployment, infrastructure as code, etc. Introducing Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure As Code, Integrate Security Testing Into Workflows, Automated Deployment, Devsecops Implementation, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway
Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Deliver an outstanding presentation on the topic using this Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Assessment, Functionality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V
Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users finding and tracking business owned devices and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Installation Maintenance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
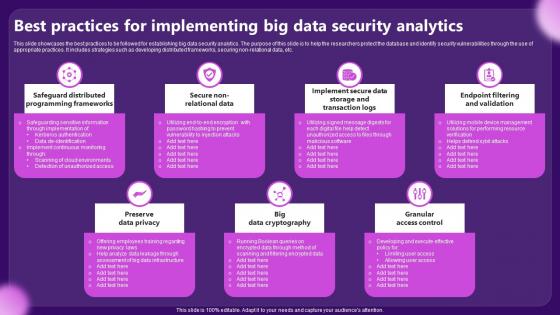 Best Practices For Implementing Big Data Security Analytics
Best Practices For Implementing Big Data Security AnalyticsThis slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non relational data, etc. Presenting our set of slides with Best Practices For Implementing Big Data Security Analytics. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preserve Data Privacy, Granular Access Control.
-
 Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a Cloud Access Security Broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Cloud Access Security Broker, Business Operations, Building Visibility, Forecasting Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network
Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into NetworkThe purpose of this slide is to outline the steps involved in implementing a security protocol into a network. These are access network requirements, plan and design, select the right protocol, prepare the network infrastructure, configure devices, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network. Dispense information and present a thorough explanation of Assess Network Requirements, Implement User Authentication, Suitable Security Protocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker Cloud Security Model
Best Practices To Implement Cloud Access Security Broker Cloud Security ModelThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Cloud Security Model. Dispense information and present a thorough explanation of Implement, Practices, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Best Practices To Implement Cloud Access Security Broker
Sase Security Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Sase Security Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Implementing, Solutions, Consumption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase
Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge SaseThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Consumption, Implementing, Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V
Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V This template helps you present information on Three stages. You can also present information on Educate Users, Find And Track Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management
Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks ManagementThe following slide illustrates some best practices to execute preventive actions for cyber attacks. It includes elements such as train employees, updating systems and software, developing incident response plan, backing up data, maintaining compliance etc. Increase audience engagement and knowledge by dispensing information using Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management. This template helps you present information on six stages. You can also present information on Train Employees, Maintain Compliance, Develop Incident Response Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Implement Cloud Access Security Broker SASE Network Security
Best Practices To Implement Cloud Access Security Broker SASE Network SecurityThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker SASE Network Security. Dispense information and present a thorough explanation of Visibility, Risk, Release using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker Next Generation CASB
Best Practices To Implement Cloud Access Security Broker Next Generation CASBThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB, Best Practices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Best Practices To Implement Cloud Access Security Broker
SD WAN Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SD WAN Model Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Network And Cloud Infrastructure Monitoring, Protection Against Risks, Specific Risk Prototypes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Checklist To Implement Devsecops In Organization
Devsecops Best Practices For Secure Checklist To Implement Devsecops In OrganizationThis slide represents the checklist to implement the DevSecOps in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying the DevSecOps system in an enterprise environment. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Checklist To Implement Devsecops In Organization. Use it as a tool for discussion and navigation on Security Training And Awareness, Collaboration And Communication, Security Automation, Vulnerability Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Devsecops Implementation Budget For Organization
Devsecops Best Practices For Secure Devsecops Implementation Budget For OrganizationThis slide represents the estimated and actual cost of implementing a DevSecOps system in an organization. The cost categories are infrastructure, security assessment, consulting or training, tool evolution, training programs, and certification. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Devsecops Implementation Budget For Organization. Use it as a tool for discussion and navigation on Security Assessment, Consulting Or Training, Training Programs, Budget For Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Enabling Devsecops Implementation Through Process
Devsecops Best Practices For Secure Enabling Devsecops Implementation Through ProcessThis slide explains the process involved in DevSecOps implementation. The purpose of his slide is to discuss the process involving automate dev. and production environments, automate software testing, automate software deployment, automate monitoring and alerting, and so on. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Enabling Devsecops Implementation Through Process. This template helps you present information on eight stages. You can also present information on Devsecops Implementation, Production Environments, Automate Software Testing, Automate Software Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Roadmap For Devsecops Implementation Strategy
Devsecops Best Practices For Secure Roadmap For Devsecops Implementation StrategyThis slide highlights the project roadmap to implement the DevSecOps plan in an organization. The purpose of this slide is to showcase the different phases of the DevSecOps implementation plan, such as foundation and preparation, tool selection and integration, etc. Introducing Devsecops Best Practices For Secure Roadmap For Devsecops Implementation Strategy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Tool Selection And Integration, Compliance And Governance, Foundation And Preparation, Security As Code, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In Organization
Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In OrganizationThis slide shows the timeline for implementing the DevSecOps process. The key steps include defining the project objective, identifying key stakeholders, sharing basic guidelines on secure coding, basic compliance checks, regularly reviewing and updating security tools, etc. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In Organization. This template helps you present information on five stages. You can also present information on Timeline To Implement Devsecops, Regularly Reviewing, Updating Security Tools, Sharing Basic Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Training Schedule For Devsecops Strategy Implementation
Devsecops Best Practices For Secure Training Schedule For Devsecops Strategy ImplementationThis slide represents the training schedule for strategy implementation for customers to manage, monitor, and troubleshoot DevSecOps implementation procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Training Schedule For Devsecops Strategy Implementation. Dispense information and present a thorough explanation of Strategy Implementation, Monitor And Troubleshoot, Devsecops Implementation Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Best Practices To Implement Cloud Access Security Broker
Sase Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Present the topic in a bit more detail with this Sase Model Best Practices To Implement Cloud Access Security Broker. Use it as a tool for discussion and navigation on Best Practices, Description, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Web Security Implementation
Best Practices For Web Security ImplementationThe purpose of this slide is to highlight the best practices for web security such as inclusive security practices, cybersecurity adoption, etc. Introducing our premium set of slides with name Best Practices For Web Security Implementation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Framework Adoption, Automation Of Security Tools, Diverse Security Measures, Web Security Implementation. So download instantly and tailor it with your information.
-
 Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment
Best Practices To Maintain Digital Wallet Security Implementation Of Cashless PaymentMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private.Increase audience engagement and knowledge by dispensing information using Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment This template helps you present information on five stages. You can also present information on Responsible Managers, Segregate Duties, Bank Statements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats
Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker CASB Cloud Security
Best Practices To Implement Cloud Access Security Broker CASB Cloud SecurityThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker CASB Cloud Security. Dispense information and present a thorough explanation of Cloud Access Security Broker, Business Operations, Building Visibility, Forecasting Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices Of QR Code Implementation Enhancing Transaction Security With E Payment
Best Practices Of QR Code Implementation Enhancing Transaction Security With E PaymentMentioned slide provides information about best practices which can be implemented by businesses to increase sales. It includes best practices such as Include call to action, personalize QR code, check code scannability, update content regularly. Introducing Best Practices Of QR Code Implementation Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Include Call To Action, Personalize QR Code, Check Code Scannability using this template. Grab it now to reap its full benefits.
-
 Best Practices For Implementing Mobile Security
Best Practices For Implementing Mobile SecurityThis slide talks about the best practices for an organization to practice mobile security device which includes minimizing public wi-fi usage, public Wi-Fi, etc. Introducing our premium set of slides with name Best Practices For Implementing Mobile Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ensuring Robust Password Protection, Security Training And Education, Enforcing Transparent Policies. So download instantly and tailor it with your information.
-
 Best Practices For Implementing Application Security
Best Practices For Implementing Application SecurityThis slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Implementing Application Security. This template helps you present information on five stages. You can also present information on Shift Security Left, Track Application Security Outcomes, Assess Threats, Application Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Best Practices For Implementing Endpoint Security
Endpoint Security Best Practices For Implementing Endpoint SecurityThis slide discusses the best approaches for endpoint security deployment which include anti-phishing deployment, ransomware protection, etc. Introducing Endpoint Security Best Practices For Implementing Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Enhanced Compliance, Improved Incident Detection, High Vulnerability To Malware, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Implementing Hids Cyber Security
Best Practices For Implementing Hids Cyber SecurityThis slide represents best practices for implementing HIDS cyber security which monitors IT systems for signs of suspicious activities and unusual behaviours. It includes best practices for implementing HIDS cyber security such as monitor all hosts, contextualize data, etc Introducing our premium set of slides with Best Practices For Implementing Hids Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitor All Hosts, Contextualize Data, Consider Agentless HIDS. So download instantly and tailor it with your information.
-
 Gamification Implementation In Cyber Security Recruitment Best Practices
Gamification Implementation In Cyber Security Recruitment Best PracticesThe purpose of this slide is to ensure that gamified components are consistent with organizations culture and values and create fun and competitive atmosphere for applicants including best practices such as aligning gamification with company culture and values, promoting diversity and inclusion, etc. Introducing our premium set of slides with name Gamification Implementation In Cyber Security Recruitment Best Practices. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Design Meaningful Challenges, Make Process Enjoyable, Promote Diversity And Inclusion, Cyber Security Recruitment. So download instantly and tailor it with your information.
-
 Best Practices To Implement Ethics In Data Cyber Security
Best Practices To Implement Ethics In Data Cyber SecurityThis slide represents various best practices that assist companies to implement ethics to enhance their data cybersecurity. It include various best practices such as ethical code of conduct, ethical hacking and testing, third-party ethics. Introducing our Best Practices To Implement Ethics In Data Cyber Security set of slides. The topics discussed in these slides are Best Practices, Details, Impact. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For IAM Process Implementation Securing Systems With Identity
Best Practices For IAM Process Implementation Securing Systems With IdentityThis slide highlights the Identity and Access Management implementation best practices. The purpose of this slide is to discuss the steps involved these are aligning IT and business needs, shifting security methodology, creating policies and processes, etc. Present the topic in a bit more detail with this Best Practices For IAM Process Implementation Securing Systems With Identity Use it as a tool for discussion and navigation on Change Management, Create Policies And Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Implement NIDS For Maintaining Effective Cyber Security
Best Practices To Implement NIDS For Maintaining Effective Cyber SecurityThis Slide Represents Effective Strategies For Employing NIDS. It Aims To Help Organizations Implement NIDS To Detect, Respond And Mitigate Cyber Threats Within Networks. Introducing Our Premium Set Of Slides With Best Practices To Implement NIDS For Maintaining Effective Cyber Security. Ellicudate The Three Stages And Present Information Using This PPT Slide. This Is A Completely Adaptable Powerpoint Template Design That Can Be Used To Interpret Topics Like Proper Network Segmentation, Thorough Traffic Analysis, Signature Database Upgradation. So Download Instantly And Tailor It With Your Information.
-
 Ways To Educate Users On Secure Online Practices Implementing E Commerce Security Measures
Ways To Educate Users On Secure Online Practices Implementing E Commerce Security MeasuresThe purpose of the slide is to educate consumers on secure online practices. It include education on strong password habits, phasing attacks and secure payment methods . Introducing Ways To Educate Users On Secure Online Practices Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Strong Password Habits, Secure Payment Methods, Educate On Phishing, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Before Vs After Implementing Email Security Policies
Email Security Best Practices Before Vs After Implementing Email Security PoliciesThis slide shows the before vs. after comparison of implementing email security policies. The different aspects compared in this slide are data security, phishing incidents, productivity, regulatory compliance, and system downtime. Present the topic in a bit more detail with this Email Security Best Practices Before Vs After Implementing Email Security Policies. Use it as a tool for discussion and navigation on Data Security, Phishing Incidents, Productivity, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Budget Of Implementing Email Security Policies
Email Security Best Practices Budget Of Implementing Email Security PoliciesThis slide represents the budget of incorporating email security policies in an organization. The different cost components are email security software, hardware and infrastructure, employee training, managed services, incident response, etc. Present the topic in a bit more detail with this Email Security Best Practices Budget Of Implementing Email Security Policies. Use it as a tool for discussion and navigation on Email Security Software, Hardware And Infrastructure, Employee Training, Managed Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Email Security Implementation Impact On Businesses
Email Security Best Practices Email Security Implementation Impact On BusinessesThis slide illustrates the business impact of implementing email security policies. The parameters described in this slide are improved data protection, reduced phishing attacks, increased employee productivity, enhanced brand reputation, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Security Implementation Impact On Businesses. Use it as a tool for discussion and navigation on Improved Data Protection, Reduced Phishing Attacks, Increased Employee Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Roadmap For Implementing Email Security Policies
Email Security Best Practices Roadmap For Implementing Email Security PoliciesThis slide represents the roadmap to implement email security policies. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Roadmap For Implementing Email Security Policies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Trustworthy Email Provider, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Timeline For Email Security Measures Implementation
Email Security Best Practices Timeline For Email Security Measures ImplementationThis slide shows the timeline for applying email security policies in organization. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Timeline For Email Security Measures Implementation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 A247 Best Practices For Web Security Implementation
A247 Best Practices For Web Security ImplementationThe purpose of this slide is to highlight the best practices for web security such as inclusive security practices, cybersecurity adoption, etc. Introducing A247 Best Practices For Web Security Implementation to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Inclusive Security Practices, Diverse Security Measures, Security Exercises, using this template. Grab it now to reap its full benefits.
-
 Practices To Improve Security Awareness Level Amongst Implementing Security Awareness Training
Practices To Improve Security Awareness Level Amongst Implementing Security Awareness TrainingThe purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. Deliver an outstanding presentation on the topic using this Practices To Improve Security Awareness Level Amongst Implementing Security Awareness Training. Dispense information and present a thorough explanation of Create Security, Awareness Program, Cyber Security Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Practices To Implement Security Automation
Key Practices To Implement Security AutomationThe following slide highlights best practices which can be implemented by firm for security automation. The major practices are prioritize automation, start with manual playbooks, adopt automation gradually and invest in the training of IT team. Introducing our premium set of slides with Key Practices To Implement Security Automation. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prioritize Automation, Start Manual Playbooks, Adopt Automation Gradually. So download instantly and tailor it with your information.
-
 Best Practices For Healthcare Iot Security Implementing Iot Devices For Care Management IOT SS
Best Practices For Healthcare Iot Security Implementing Iot Devices For Care Management IOT SSFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Present the topic in a bit more detail with this Best Practices For Healthcare Iot Security Implementing Iot Devices For Care Management IOT SS. Use it as a tool for discussion and navigation on Attack Surface Visibility, Segregated Internal Networking, Zero Trust Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Cybersecurity Incident Management Development And Implementation Of Security
Best Practices For Cybersecurity Incident Management Development And Implementation Of SecurityThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Cybersecurity Incident Management Development And Implementation Of Security. This template helps you present information on five stages. You can also present information on Create Cyber Incident, Management Plan, Establish Roles, Responsibilities Of Team Members using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Effective Endpoint Security Implementation Of ICT Strategic Plan Strategy SS
Best Practices For Effective Endpoint Security Implementation Of ICT Strategic Plan Strategy SSThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business owned devices, and installation maintenance of operating systems.Increase audience engagement and knowledge by dispensing information using Best Practices For Effective Endpoint Security Implementation Of ICT Strategic Plan Strategy SS. This template helps you present information on three stages. You can also present information on Such Business, Operating System, Frequent Basis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint Microsoft
SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint MicrosoftThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint Microsoft. Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Practices For Enterprise Blockchain Implementation
Security Practices For Enterprise Blockchain ImplementationThis slide presents security practices for blockchain implementation aimed at optimizing security and mitigation practices to improve cybersecurity technology. It covers permissioned blockchain, case analysis, create governance structure and file storage. Presenting our set of slides with Security Practices For Enterprise Blockchain Implementation. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Permissioned Blockchain, Create Governance Structure, Case Analysis, File Storage.
-
 Best Practices Implement Cloud Access Security Broker Ppt Professional Graphics Design
Best Practices Implement Cloud Access Security Broker Ppt Professional Graphics DesignThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices Implement Cloud Access Security Broker Ppt Professional Graphics Design. Dispense information and present a thorough explanation of Best Practices, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



