Powerpoint Templates and Google slides for Implement Security Plan
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Application Security Implementation Plan Powerpoint Presentation Slides
Application Security Implementation Plan Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Application Security Implementation Plan Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Implementing security management plan to reduce threats and protect sensitive company data complete deck
Implementing security management plan to reduce threats and protect sensitive company data complete deckThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Implementing Security Management Plan To Reduce Threats And Protect Sensitive Company Data Complete Deck and has templates with professional background images and relevant content. This deck consists of total of fourty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V
Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V Use it as a tool for discussion and navigation on Organisational Capability Framework, Performance Appraisal, Feedback System This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V
Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V Use it as a tool for discussion and navigation on Data Sets And Compliance, IT Service Planning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Smart Contracts Implementation Plan Statistical Data Of Security Breach Incident
Smart Contracts Implementation Plan Statistical Data Of Security Breach IncidentThis slide summarizes the security breach incident across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. Present the topic in a bit more detail with this Smart Contracts Implementation Plan Statistical Data Of Security Breach Incident. Use it as a tool for discussion and navigation on Statistical Data, Security Breach Incident, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Application Security Performance Monitoring Dashboard
Application Security Implementation Plan Application Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Performance Monitoring Dashboard. Use it as a tool for discussion and navigation on Application Security, Performance, Monitoring Dashboard, Monitor Security Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard
Application Security Implementation Plan Application Security Vulnerability Scanning DashboardThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard. Use it as a tool for discussion and navigation on Application Security Vulnerability, Scanning Dashboard, Monitor Vulnerabilities Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
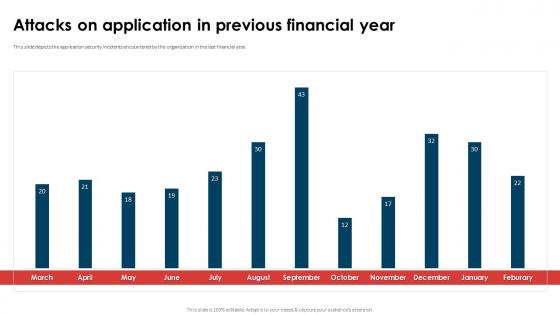 Application Security Implementation Plan Attacks On Application In Previous Financial Year
Application Security Implementation Plan Attacks On Application In Previous Financial YearThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Attacks On Application In Previous Financial Year. Dispense information and present a thorough explanation of Attacks On Application, Previous Financial Year, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Budget Allocation For Application Security Training
Application Security Implementation Plan Budget Allocation For Application Security TrainingThis slide showcases the training cost breakdown for different components such as instructor, training cost, etc. Present the topic in a bit more detail with this Application Security Implementation Plan Budget Allocation For Application Security Training. Use it as a tool for discussion and navigation on Budget Allocation, Application Security Training, Training Cost Breakdown, Training Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 EHR Security Implementation Plan Icon
EHR Security Implementation Plan IconIntroducing our EHR Security Implementation Plan Icon set of slides. The topics discussed in these slides are Ehr Security Implementation Plan Icon This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact
Security Plan To Prevent Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Program Implementation, Attacks Frequency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
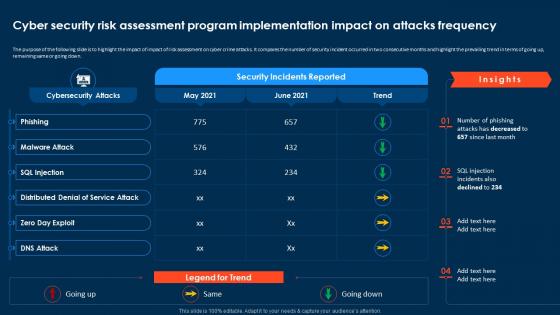 Compressive Planning Guide Cyber Security Risk Assessment Program Implementation Impact
Compressive Planning Guide Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Compressive Planning Guide Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment Program, Attacks Frequency, Distributed Denial Of Service Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges Faced During Cyber Security Management Plan Implementation
Challenges Faced During Cyber Security Management Plan ImplementationThis slide highlights the challenges faced by businesses during the implementation of a cybersecurity management plan. The purpose of this slide is to help the business establish a suitable cyber security management plan through the elimination of structural vulnerabilities such as scarcity of skilled professionals, inability to adapt to evolving cyber attacks, etc.Presenting our well structured Challenges Faced During Cyber Security Management Plan Implementation. The topics discussed in this slide are Complicated Environments, Business Operations, Defending Against. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Icon For Implementation Of Cyber Security Strategy Action Plan
Icon For Implementation Of Cyber Security Strategy Action PlanPresenting our set of slides with Icon For Implementation Of Cyber Security Strategy Action Plan. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Strategy, Security.
-
 Strategic Cyber Security Action And Implementation Plan
Strategic Cyber Security Action And Implementation PlanThe slide showcases strategic cyber security action and implementation plan for protecting confidential data in an organization. It contains quarterly timeline with points, such as benchmark, analysis, vision, roadmap, mobilization, etc. Introducing our Strategic Cyber Security Action And Implementation Plan set of slides. The topics discussed in these slides are Analysis, Vision, Implementation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V
Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V This template helps you present information on Three stages. You can also present information on Educate Users, Find And Track Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Access Security Control Models Strategy SS V
Strategic Plan To Implement Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Key Access Security Control Models Strategy SS V Dispense information and present a thorough explanation of This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V
Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on IT Governance, Visualization, Resource Management using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V
Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V Dispense information and present a thorough explanation of Communication, Data Management, Marketing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management
Cyber Security Plan Implementation Timeline Improving Cyber Security Risks ManagementThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Perform Simulated, Phishing Exercise, using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Data Breach Security Response Plan
Checklist To Implement Data Breach Security Response PlanThis slide depicts the checklist to execute response plans during data security breaches. The purpose of this checklist is to help the business ensure all suitable actions are implemented in order to prevent data leaks. It includes elements such as activity status, person responsible, etc. Presenting our well structured Checklist To Implement Data Breach Security Response Plan. The topics discussed in this slide are Isolate Affected Systems, Notify Appropriate Stakeholders, Identify The Nature. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
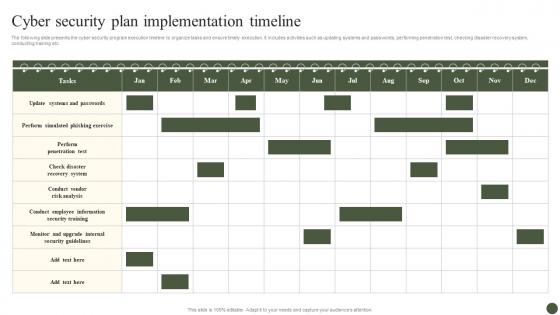 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security
Firewall Network Security 30 60 90 Days Plan To Implement Firewall SecurityThis slide outlines the 30-60-90 days plan to integrate firewalls in a business. The purpose of this slide is to showcase the various steps that should be taken at the interval of every 30 days, such as assessing the current security landscape, defining firewall requirements and selecting solutions, etc. Present the topic in a bit more detail with this Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security Use it as a tool for discussion and navigation on 30 Days, 60 Days, 90 Days This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Implementation Secure Operations
Data Breach Response Plan Implementation Secure OperationsThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Implementation Secure Operations. Use it as a tool for discussion and navigation on Secure Physical Areas, Assemble Expert Team, Consult With Legal Counsel, Secure Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops Implementation
Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops ImplementationThis slide represents the 30-60-90-day plan for DevSecOps implementation. The purpose of this slide is to showcase the approaches that need to be followed as short-term, medium, and long-term goals to implement the DevSecOps. Introducing Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Devsecops Implementation, Vulnerability Scanning, Relevant Security Standards, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Cyber Risk Assessment
Cyber Security Plan Implementation Timeline Cyber Risk AssessmentThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Cyber Risk Assessment to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Cyber Security Plan, Implementation Timeline using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness
Cyber Security Plan Implementation Timeline Creating Cyber Security AwarenessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Malware Attacks, Breaches To Company, More Challenging This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Checklist Plan For Security Incident
Implementation Checklist Plan For Security IncidentPresenting our set of slides with Implementation Checklist Plan For Security Incident. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation Checklist Plan, Security Incident.
-
 Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security Threats
Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Update Systems And Passwords, Perform Simulated Phishing Exercise, Perform Penetration Test using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 30 60 90 Days Plan For Security Testing Implementation
30 60 90 Days Plan For Security Testing ImplementationThis slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc. Introducing 30 60 90 Days Plan For Security Testing Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Assess And Plan, Skill And Tool Acquisition, Implementation And Integration, using this template. Grab it now to reap its full benefits.
-
 30 60 90 Day Plan For Cyber Security Framework Implementation
30 60 90 Day Plan For Cyber Security Framework ImplementationThis slide discusses the 30-60-90-day plan for cyber security framework implementation which include stakeholder alignment, awareness training and so on. Introducing 30 60 90 Day Plan For Cyber Security Framework Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Stakeholder Alignment, Conduct Initial Gap Analysis, Conduct Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Budget Allocation To Implement Application Security
Application Security Implementation Plan Budget Allocation To Implement Application SecurityThis slide showcases the training cost breakdown for different components such as instructor, training cost, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Budget Allocation To Implement Application Security. Dispense information and present a thorough explanation of Security Infrastructure, Security Personnel, Insurance And Legal Costs, Budget Allocation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Checklist For Effective Application Security Implementation
Application Security Implementation Plan Checklist For Effective Application Security ImplementationThis slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. Present the topic in a bit more detail with this Application Security Implementation Plan Checklist For Effective Application Security Implementation. Use it as a tool for discussion and navigation on Assessment And Planning, Education And Training, Incident Response Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Comparative Analysis Of Application Security Tools
Application Security Implementation Plan Comparative Analysis Of Application Security ToolsThis slide highlights the comparison of different application security tools and optimal selection of the tool along with the reason of selection. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Comparative Analysis Of Application Security Tools. Dispense information and present a thorough explanation of Comparative Analysis, Application Security Tools, Commercial, License using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Existing IT Security Infrastructure Threats
Application Security Implementation Plan Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Existing IT Security Infrastructure Threats. Dispense information and present a thorough explanation of Broken Authentication, Cross Site Scripting, Denial Of Service, Infrastructure Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Five Step Roadmap To Implement Application Security
Application Security Implementation Plan Five Step Roadmap To Implement Application SecurityThis slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc. Introducing Application Security Implementation Plan Five Step Roadmap To Implement Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Monitoring And Logging, Incident Response, Education And Planning, Application Security, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Implementing Effective Security Testing In Organization
Application Security Implementation Plan Implementing Effective Security Testing In OrganizationThis slide showcases the deployment process of security testing parallel to Software Development Testing Lifecycle SDLC stages. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Implementing Effective Security Testing In Organization. This template helps you present information on seven stages. You can also present information on System Testing, Implementation System Testing, Integration Testing, Requirement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Key Challenges Of Existing Application Security Infrastructure
Application Security Implementation Plan Key Challenges Of Existing Application Security InfrastructureThis slide discusses the issues faced by the organization after implementation of application security such as outdated technology, scalability concerns, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Key Challenges Of Existing Application Security Infrastructure. Dispense information and present a thorough explanation of Inadequate User Training, Scalability Concerns, Outdated Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Major Impact Of Application Security On Business
Application Security Implementation Plan Major Impact Of Application Security On BusinessThis slide showcases the after application security impact on business along with factors that have improved the overall performance. Introducing Application Security Implementation Plan Major Impact Of Application Security On Business to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats Surge, Security Increase, Reduced Attacks On Applications, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Of Table Of Contents
Application Security Implementation Plan Of Table Of ContentsPresent the topic in a bit more detail with this Application Security Implementation Plan Of Table Of Contents. Use it as a tool for discussion and navigation on Application Security, Implementation Plan, Attacks On Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Performance Gap Analysis For Implementing Application Security
Application Security Implementation Plan Performance Gap Analysis For Implementing Application SecurityThe purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Performance Gap Analysis For Implementing Application Security. This template helps you present information on four stages. You can also present information on Proper Functioning, Implement Robust Encryption Protocols, Lack Of Ideal Security Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Process Of Implementing Cloud Native Application Security
Application Security Implementation Plan Process Of Implementing Cloud Native Application SecurityThis slide highlights the steps for deploying cloud-native application security which include understanding principles, risk assessment, etc. Introducing Application Security Implementation Plan Process Of Implementing Cloud Native Application Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Continuous Monitoring, Container Security, Implement Strong Access Controls, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Process Phases For Effective Authentication Implementation
Application Security Implementation Plan Process Phases For Effective Authentication ImplementationThis slide showcases the steps for deploying effective authentication which include defining requirements, selecting authentication method, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Process Phases For Effective Authentication Implementation. This template helps you present information on seven stages. You can also present information on Implement Login Mechanism, Choose Authentication Method, Secure Storage Of Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Project Summary For Implementing Application Security
Application Security Implementation Plan Project Summary For Implementing Application SecurityThe purpose of this slide is to represent the summary of the application security project providing information regarding problems faced, solution, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Project Summary For Implementing Application Security. Dispense information and present a thorough explanation of Vulnerability In Application, Estimated Cost, Estimated Timeline, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan RACI Matrix To Deploy Application Security
Application Security Implementation Plan RACI Matrix To Deploy Application SecurityThis slide showcases a RACI matrix for application security, outlining the appropriate roles and steps to be taken during application security implementation. Present the topic in a bit more detail with this Application Security Implementation Plan RACI Matrix To Deploy Application Security. Use it as a tool for discussion and navigation on Secure Development Practices, Risk Assessment, Data Encryption, Application Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security
Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application SecurityThe purpose of this slide is to discuss the challenges faced while implementing application security such as data breaches, third-party risks, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security. Dispense information and present a thorough explanation of Vulnerabilities In Applications, Data Breaches, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Statistics Of It Infrastructure Attacks On Organization
Application Security Implementation Plan Statistics Of It Infrastructure Attacks On OrganizationThis slide summarizes security attacks across different organizational departments, such as IT, HR, Sales, Finance, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Statistics Of IT Infrastructure Attacks On Organization. Dispense information and present a thorough explanation of Statistics Of IT Infrastructure, Attacks On Organization, Organizational Departments, Finance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Steps For Deploying Application Security Testing
Application Security Implementation Plan Steps For Deploying Application Security TestingThis slide showcases the steps for deploying effective application security testing which include establishing test case, including security exam, etc. Introducing Application Security Implementation Plan Steps For Deploying Application Security Testing to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Execute Security Exam, Examine Outcomes, Include Security Exam, Stablish Working Test Case, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Steps For Effective Encryption Method Deployment
Application Security Implementation Plan Steps For Effective Encryption Method DeploymentThis slide highlights the steps for deploying effective encryption which include selecting appropriate algorithm, choosing correct key size, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Steps For Effective Encryption Method Deployment. This template helps you present information on six stages. You can also present information on Select Appropriate Algorithm, Select Appropriate Program, Maintain Key Security, Encryption Method Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Steps To Deploy Efficient Access Control
Application Security Implementation Plan Steps To Deploy Efficient Access ControlThis slide discusses the process phases of implementing access control which include taking inventory of systems, examining staffs, etc. Introducing Application Security Implementation Plan Steps To Deploy Efficient Access Control to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Establish Roles, Resist Sporadic Adjustments, Examine The Staff, Take Inventory Of Systems, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Team Structure For Application Security Deployment
Application Security Implementation Plan Team Structure For Application Security DeploymentThis slide represents the team structure for the application security in the IT infrastructure which includes manager, team lead, application security team, etc. Present the topic in a bit more detail with this Application Security Implementation Plan Team Structure For Application Security Deployment. Use it as a tool for discussion and navigation on Application Security Team, Database Management Team, Security Analyst, Malware Analyst. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Timeline For Deploying Efficient Application Security
Application Security Implementation Plan Timeline For Deploying Efficient Application SecurityThis slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Timeline For Deploying Efficient Application Security. This template helps you present information on six stages. You can also present information on Education And Training, Patch Management, Incident Response Planning, Establish Security Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Top Application Security Service Providers
Application Security Implementation Plan Top Application Security Service ProvidersThis slide outlines the comparison of different application security service providers and optimal selection of the provider along with the reason of selection. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Top Application Security Service Providers. Dispense information and present a thorough explanation of Service Provider Application, Security Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Working Process Of Effective Logging Implementation
Application Security Implementation Plan Working Process Of Effective Logging ImplementationThis slide outlines the steps for deploying effective logging which include assess requirements, select logging tool, defining logging standards, etc. Introducing Application Security Implementation Plan Working Process Of Effective Logging Implementation to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Security, Centralize Log Management, Define Logging Standards, Select Logging Tools, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Application Security Implementation Plan
Icons Slide For Application Security Implementation PlanIntroducing our well researched set of slides titled Icons Slide For Application Security Implementation Plan. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Application Security Implementation Plan
Table Of Contents For Application Security Implementation PlanIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Application Security Implementation Plan. This template helps you present information on fifteen stages. You can also present information on Implementation Process, Project Roadmap, Risks And Mitigation Strategies, Project Implementation Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Selection Of Optimal Application Security Technique
Application Security Implementation Plan Selection Of Optimal Application Security TechniqueThis slide outlines the comparison of different application testing techniques on the basis of parameters such as security provided and cost. Present the topic in a bit more detail with this Application Security Implementation Plan Selection Of Optimal Application Security Technique. Use it as a tool for discussion and navigation on Authorization, Encryption, Security Testing, Access Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization
Tokenization For Improved Data Security 30 60 90 Days Plan To Implement TokenizationThis slide depicts the 30 60 90 days plan for implementing tokenization. The plan includes the activities and goals such as assessment, planning, selecting tokenization solutions, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization. Dispense information and present a thorough explanation of Assessment And Planning, Select Tokenization Solution, Test Tokenization Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




