Powerpoint Templates and Google slides for Implement Secure
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation Slides
Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation SlidesEnthrall your audience with this Implementing Security Awareness Training To Prevent Cyber Attacks Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising senenty five slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Firewall Implementation For Cyber Security Powerpoint Presentation Slides
Firewall Implementation For Cyber Security Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Firewall Implementation For Cyber Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Development And Implementation Of Security Incident Management Powerpoint Presentation Slides V
Development And Implementation Of Security Incident Management Powerpoint Presentation Slides VEnthrall your audience with this Development And Implementation Of Security Incident Management Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Implementing Cyber Security Incident Management Powerpoint Presentation Slides
Implementing Cyber Security Incident Management Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this Implementing Cyber Security Incident Management Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with sixty nine slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Implementing Organizational Security Training To Prevent Cyberattacks Complete Deck
Implementing Organizational Security Training To Prevent Cyberattacks Complete DeckDitch the Dull templates and opt for our engaging Implementing Organizational Security Training To Prevent Cyberattacks Complete Deck deck to attract your audience. Our visually striking design effortlessly combines creativity with functionality, ensuring your content shines through. Compatible with Microsoft versions and Google Slides, it offers seamless integration of presentation. Save time and effort with our pre-designed PPT layout, while still having the freedom to customize fonts, colors, and everything you ask for. With the ability to download in various formats like JPG, JPEG, and PNG, sharing your slides has never been easier. From boardroom meetings to client pitches, this deck can be the secret weapon to leaving a lasting impression.
-
 Implementing Strategies To Mitigate Cyber Security Threats Powerpoint Presentation Slides
Implementing Strategies To Mitigate Cyber Security Threats Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Implementing Strategies To Mitigate Cyber Security Threats Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Application Security Implementation Plan Powerpoint Presentation Slides
Application Security Implementation Plan Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Application Security Implementation Plan Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Implementing E Commerce Security Measures To Prevent Fraud Powerpoint Presentation Slides
Implementing E Commerce Security Measures To Prevent Fraud Powerpoint Presentation SlidesDo not compromise on a template that erodes your messages impact. Introducing our engaging Implementing E Commerce Security Measures To Prevent Fraud Powerpoint Presentation Slides complete deck, thoughtfully crafted to grab your audiences attention instantly. With this deck, effortlessly download and adjust elements, streamlining the customization process. Whether you are using Microsoft versions or Google Slides, it fits seamlessly into your workflow. Furthermore, it is accessible in JPG, JPEG, PNG, and PDF formats, facilitating easy sharing and editing. Not only that you also play with the color theme of your slides making it suitable as per your audiences preference.
-
 Implementing a security awareness program powerpoint presentation slides
Implementing a security awareness program powerpoint presentation slidesPresenting our implementing a security awareness program PowerPoint presentation slides. This PowerPoint design contains fifty-one slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. It can be downloaded in varying formats like JPEG, PDF, PNG, etc. You can download this PPT layout by clicking on the button below.
-
 E Mail Security Industry Overview And Implementation Report Powerpoint Presentation Slides
E Mail Security Industry Overview And Implementation Report Powerpoint Presentation SlidesThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on E Mail Security Industry Overview And Implementation Report Powerpoint Presentation Slides and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of fourty two slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Implementing security management plan to reduce threats and protect sensitive company data complete deck
Implementing security management plan to reduce threats and protect sensitive company data complete deckThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Implementing Security Management Plan To Reduce Threats And Protect Sensitive Company Data Complete Deck and has templates with professional background images and relevant content. This deck consists of total of fourty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Cyber Security Implementation Powerpoint Ppt Template Bundles
Cyber Security Implementation Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Cyber Security Implementation Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using thirty slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Implementing Blockchain Security Solutions Powerpoint Ppt Template Bundles
Implementing Blockchain Security Solutions Powerpoint Ppt Template BundlesIntroduce your topic and host expert discussion sessions with this Implementing Blockchain Security Solutions Powerpoint Ppt Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twenty one slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Implementing Identity And Access Management For Operational Security OPSEC Training Ppt
Implementing Identity And Access Management For Operational Security OPSEC Training PptPresenting Implementing Identity and Access Management for Operational Security OPSEC. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Blockchain Implementation Challenges In Education Industry Security Concerns Training Ppt
Blockchain Implementation Challenges In Education Industry Security Concerns Training PptPresenting Challenges Faced While Incorporating Blockchain in Education Industry due to Security Concerns. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
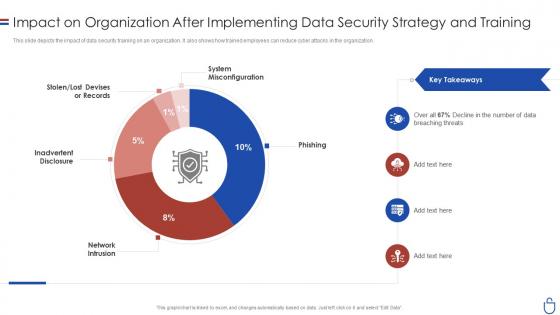 Data security it impact on organization after implementing data security strategy
Data security it impact on organization after implementing data security strategyThis slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver an outstanding presentation on the topic using this Data Security IT Impact On Organization After Implementing Data Security Strategy. Dispense information and present a thorough explanation of Phishing, Network Intrusion, Inadvertent Disclosure, System Misconfiguration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
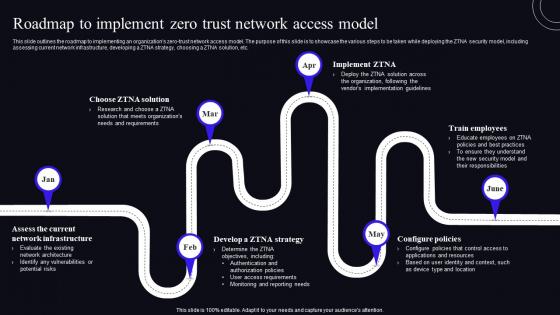 Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model
Roadmap To Implement Zero Trust Network Access Model Zero Trust Security ModelThis Slide Outlines The Roadmap To Implementing An Organizations Zero-Trust Network Access Model. The Purpose Of This Slide Is To Showcase The Various Steps To Be Taken While Deploying The ZTNA Security Model, Including Assessing Current Network Infrastructure, Developing A ZTNA Strategy, Choosing A ZTNA Solution, Etc. Increase Audience Engagement And Knowledge By Dispensing Information Using Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model. This Template Helps You Present Information On Six Stages. You Can Also Present Information On Roadmap, Network Infrastructure, Configure Policies Using This PPT Design. This Layout Is Completely Editable So Personaize It Now To Meet Your Audiences Expectations.
-
 Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V
Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V. Use it as a tool for discussion and navigation on Issues By Control Type, Standard Control Issues. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V
Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Deliver an outstanding presentation on the topic using this Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V. Dispense information and present a thorough explanation of Survey Goal, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secops V2 Effective Implementation Impact On Security Breaches
Secops V2 Effective Implementation Impact On Security BreachesThis slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Present the topic in a bit more detail with this Secops V2 Effective Implementation Impact On Security Breaches. Use it as a tool for discussion and navigation on Network Intrusion, Security Breaches, Sensitive Data Leakage, Configuration Information Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V
Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V Use it as a tool for discussion and navigation on Organisational Capability Framework, Performance Appraisal, Feedback System This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V
Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V Use it as a tool for discussion and navigation on Data Sets And Compliance, IT Service Planning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions
Devsecops Best Practices For Secure Challenges With Devsecops Implementation And SolutionsThis slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions. Dispense information and present a thorough explanation of Security Awareness And Training, Continuous Monitoring And Compliance, Managing Security Debt using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation
Devsecops Best Practices For Secure Key Elements Of Successful Devsecops ImplementationThe slide discusses the critical elements for the successful implementation of DevSecOps. The purpose of this slide is to explain the various features that are integrated automated testing into a pipeline, automated deployment, infrastructure as code, etc. Introducing Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure As Code, Integrate Security Testing Into Workflows, Automated Deployment, Devsecops Implementation, using this template. Grab it now to reap its full benefits.
-
 Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Prevented Attacks, Cyber Attack Trends This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Present the topic in a bit more detail with this Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Current And Future Goal Analysis, Breach Risk Trend This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats
Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the key reasons of cyber attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Deliver an outstanding presentation on the topic using this Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Employees, Management, Training Courses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
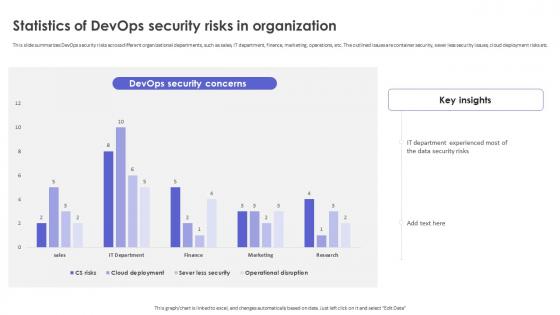 Strategic Roadmap To Implement DevSecOps Statistics Of Devops Security Risks In Organization
Strategic Roadmap To Implement DevSecOps Statistics Of Devops Security Risks In OrganizationThis slide summarizes DevOps security risks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined issues are container security, sever less security issues, cloud deployment risks etc. Deliver an outstanding presentation on the topic using this Strategic Roadmap To Implement DevSecOps Statistics Of Devops Security Risks In Organization. Dispense information and present a thorough explanation of Devops Security Risks Across, Organizational Departments, Finance, Marketing, Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Testing Implementation Training Budget
Security Testing Implementation Training BudgetThe purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Deliver an outstanding presentation on the topic using this Security Testing Implementation Training Budget. Dispense information and present a thorough explanation of Security Testing Implementation, Training Budget, Training Material Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Contracts Implementation Plan Statistical Data Of Security Breach Incident
Smart Contracts Implementation Plan Statistical Data Of Security Breach IncidentThis slide summarizes the security breach incident across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. Present the topic in a bit more detail with this Smart Contracts Implementation Plan Statistical Data Of Security Breach Incident. Use it as a tool for discussion and navigation on Statistical Data, Security Breach Incident, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPI Report Of Cyber Security Framework Implementation
KPI Report Of Cyber Security Framework ImplementationThis slide depicts the KPI report of cyber security framework implementation based on total intrusion attempts, mean detect time, mean resolve time, etc. Deliver an outstanding presentation on the topic using this KPI Report Of Cyber Security Framework Implementation. Dispense information and present a thorough explanation of KPI Report Of Cyber Security, Framework Implementation, Mean Detect Time, Mean Resolve Time using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Application Security Performance Monitoring Dashboard
Application Security Implementation Plan Application Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Performance Monitoring Dashboard. Use it as a tool for discussion and navigation on Application Security, Performance, Monitoring Dashboard, Monitor Security Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard
Application Security Implementation Plan Application Security Vulnerability Scanning DashboardThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard. Use it as a tool for discussion and navigation on Application Security Vulnerability, Scanning Dashboard, Monitor Vulnerabilities Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
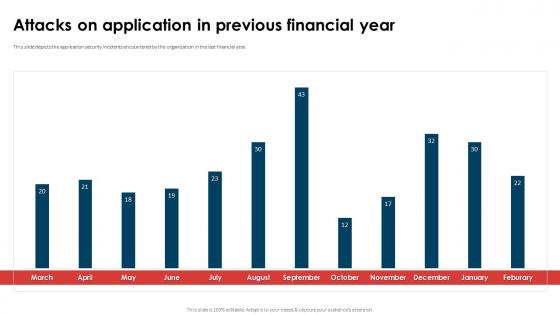 Application Security Implementation Plan Attacks On Application In Previous Financial Year
Application Security Implementation Plan Attacks On Application In Previous Financial YearThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Attacks On Application In Previous Financial Year. Dispense information and present a thorough explanation of Attacks On Application, Previous Financial Year, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Budget Allocation For Application Security Training
Application Security Implementation Plan Budget Allocation For Application Security TrainingThis slide showcases the training cost breakdown for different components such as instructor, training cost, etc. Present the topic in a bit more detail with this Application Security Implementation Plan Budget Allocation For Application Security Training. Use it as a tool for discussion and navigation on Budget Allocation, Application Security Training, Training Cost Breakdown, Training Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures
Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security MeasuresThis slide portrays the common types of fraud attacks experienced by ecommerce businesses in recent years. It include frauds such as card testing, phishing, account takeover and the reason of attacks. Deliver an outstanding presentation on the topic using this Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Poor Website Security, In Frequent Monitoring, Secure Payment Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
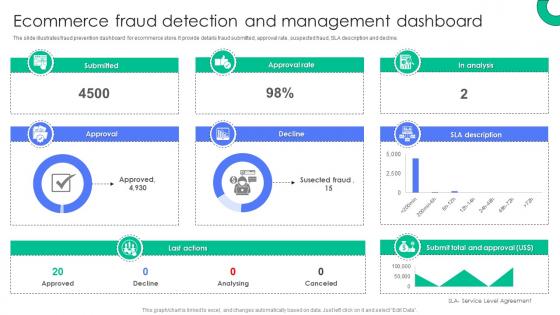 Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures
Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security MeasuresThe slide illustrates fraud prevention dashboard for ecommerce store. It provide details fraud submitted, approval rate, suspected fraud, SLA description and decline. Present the topic in a bit more detail with this Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Submitted, Approval, Approval Rate, Decline, Last Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
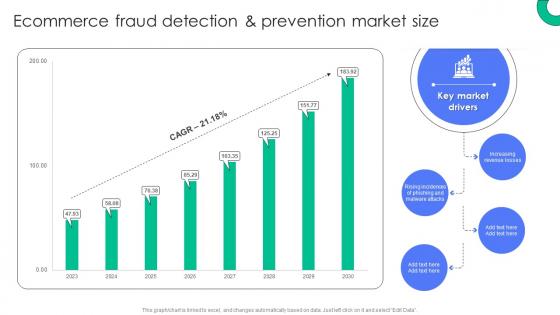 Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security Measures
Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security MeasuresDeliver an outstanding presentation on the topic using this Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Increasing Revenue Losses, Key Market, Drivers, Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
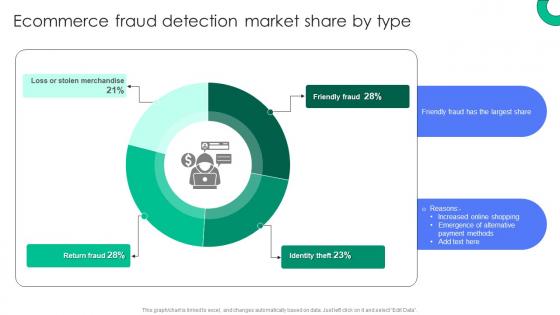 Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures
Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security MeasuresPresent the topic in a bit more detail with this Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Identity Theft, Friendly Fraud, Return Fraud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures
Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security MeasuresThis slide represents the impact of fraud attacks on ecommerce companies. It provide information about chargeback fee, high network fee, delayed expansion or investment. Deliver an outstanding presentation on the topic using this Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Card Payment, Manage Fraud, Businesses Delay Investment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures
Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security MeasuresThe slide highlights the ways to track and analyze transaction patterns and log in attempts. It provide details about risk scoring, real time monitoring, account monitoring and behavioral analytics.Present the topic in a bit more detail with this Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Account Monitoring, Behavioral Analytics, Real Time Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures
Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security MeasuresThis slide showcases financial challenges faced by the company related to cybersecurity attacks, referable for businesses facing similar situation. It cover losses caused due to lack of awareness about attacks. Present the topic in a bit more detail with this Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Key Insights, Ecommerce Business, Key Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Fraud Prevention Strategies Impact On Financial Losses Implementing E Commerce Security Measures
Fraud Prevention Strategies Impact On Financial Losses Implementing E Commerce Security MeasuresThe slide showcases post impact of ecommerce fraud prevention strategy on buisness losses. It include reasons for decreasing losses such as compliant monitoring and auditing.Deliver an outstanding presentation on the topic using this Fraud Prevention Strategies Impact On Financial Losses Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Ecommerce Business, Key Insights, Compliant Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures
Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security MeasuresThe slide outlines major multifactor authentication methods to safeguard ecommerce stores. It include details about knowledge factors, possession factor along with potential impact. Present the topic in a bit more detail with this Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Information Inherent, Potential Impact, Reduced Suspicious Logins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Post Impact Analysis Of Ecommerce Fraud Strategies Implementing E Commerce Security Measures
Post Impact Analysis Of Ecommerce Fraud Strategies Implementing E Commerce Security MeasuresThis slide depicts the fraud prevention strategies impact on ecommerce company. It covers frauds such as phishing, friendly fraud, identify theft, account takeover etc. Deliver an outstanding presentation on the topic using this Post Impact Analysis Of Ecommerce Fraud Strategies Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Poor Website Security, In Frequent Monitoring, Secure Payment Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS
Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SSBudget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS This slide showcases expenses share to implement mobile device threat management solutions. Its key elements are biometric solutions, VPN, software upgradation, mobile device management Present the topic in a bit more detail with this Biometric Solutions, Security Awareness Use it as a tool for discussion and navigation on Biometric Solutions, Security Awareness This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS
Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases decrease in cyber attacks after implementation of mobile security. Its key elements are malware, phishing attacks and ransomware Deliver an outstanding presentation on the topic using this Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Advanced Persistent Threats, Diverse Cyber Threat Landscape using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material
Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology MaterialEnhance your audiences knowledge with this well researched complete deck. Showcase all the important features of the deck with perfect visuals. This deck comprises of total of ten slides with each slide explained in detail. Each template comprises of professional diagrams and layouts. Our professional PowerPoint experts have also included icons, graphs and charts for your convenience. All you have to do is DOWNLOAD the deck. Make changes as per the requirement. Yes, these PPT slides are completely customizable. Edit the colour, text and font size. Add or delete the content from the slide. And leave your audience awestruck with the professionally designed Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material complete deck.
-
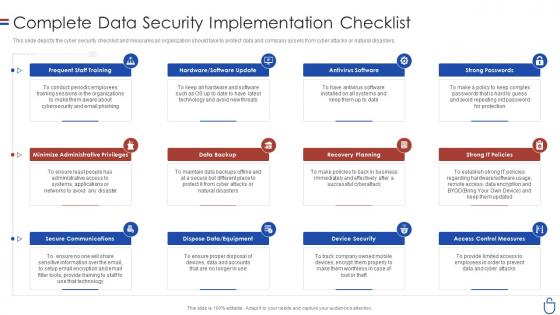 Data security it complete data security implementation checklist
Data security it complete data security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Data Security IT Complete Data Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Antivirus Software, Strong Passwords, Minimize Administrative Privileges, Data Backup, Recovery Planning, Strong IT Policies, Secure Communications, Device Security, using this template. Grab it now to reap its full benefits.
-
 Data security it implementation of strong password policy
Data security it implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Data Security IT Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Special Characters, Employees, Protected Accounts, using this template. Grab it now to reap its full benefits.
-
 Data security it timeline for the implementation of data security
Data security it timeline for the implementation of data securityThis slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Data Security IT Timeline For The Implementation Of Data Security. Use it as a tool for discussion and navigation on Phishing Exercise, Risk Assessments, Security Documentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
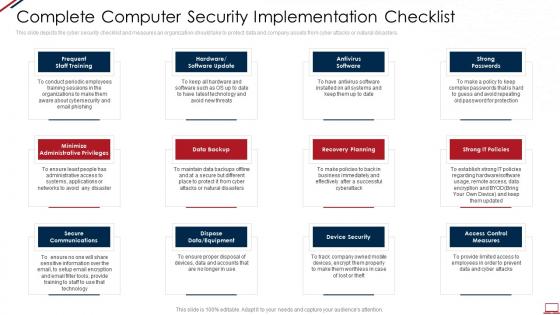 Computer system security complete computer security implementation checklist
Computer system security complete computer security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Increase audience engagement and knowledge by dispensing information using Computer System Security Complete Computer Security Implementation Checklist. This template helps you present information on twelve stages. You can also present information on Data Backup, Secure Communications, Recovery Planning, Strong Passwords, Device Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security impact on organization after implementing computer security strategy and training
Computer system security impact on organization after implementing computer security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Increase audience engagement and knowledge by dispensing information using Computer System Security Impact On Organization After Implementing Computer Security Strategy And Training. This template helps you present information on five stages. You can also present information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security implementation of strong password policy
Computer system security implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Computer System Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Computer system security timeline for the implementation of computer security
Computer system security timeline for the implementation of computer securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Computer System Security Timeline For The Implementation Of Computer Security. Use it as a tool for discussion and navigation on Security, Risk Assessments, Perform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model
Before Vs After Zero Trust Network Access Implementation Zero Trust Security ModelThis slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Deliver an outstanding presentation on the topic using this Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model. Dispense information and present a thorough explanation of Implementation, Distributed, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Estimated Cost Summary For ZTNA Implementation Zero Trust Security Model
Estimated Cost Summary For ZTNA Implementation Zero Trust Security ModelThis slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Present the topic in a bit more detail with this Estimated Cost Summary For ZTNA Implementation Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Organization, Represents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model
F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security ModelThis slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Present the topic in a bit more detail with this F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Organizations, Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.




