Powerpoint Templates and Google slides for Implement Preventive
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
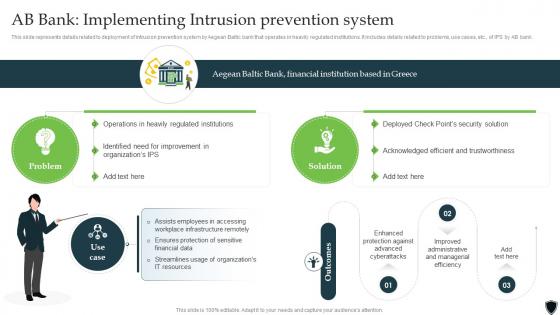 Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Aegean Baltic bank that operates in heavily regulated institutions. It includes details related to problems, use cases, etc., of IPS by AB bank. Introducing Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Solution, Enhanced Protection Against Advanced Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SS
Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SSThis slide outlines the steps to configure an alerting system for a network security tool implemented to monitor networks to prevent, report, and block malicious activities. Introducing Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Automate Monitoring For Intrusions, Cyber Security Data Breaches, Deploy Alarms For Detected, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SS
Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SSThis slide represents tactics to effectively configure switched port analyzers such as focusing on filtering, checking logs, and not over-capturing and analyzing the organizational environment. Introducing Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Focus On Filtering, Check Logs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SS
Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SSThis slide outlines the issues that enterprise face with outdated cybersecurity solutions, including limited threat visibility, inability to combat APTs, lack of granular control, and insufficient incident response capabilities. Introducing Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Limited Threat Visibility, Inability To Combat Apts, Lack Of Granular Control, Insufficient Incident Response, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SS
Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Cisco data centers . It includes details related to problems, solutions, use cases and outcomes of deploying IPS by Cisco data centers. Introducing Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Solution, Outcomes, Fewer Service Interruptions, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Cisco data centers . It includes details related to problems, solutions, use cases and outcomes of deploying IPS by Cisco data centers. Present the topic in a bit more detail with this Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Softwares, Features, USP, Pricing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
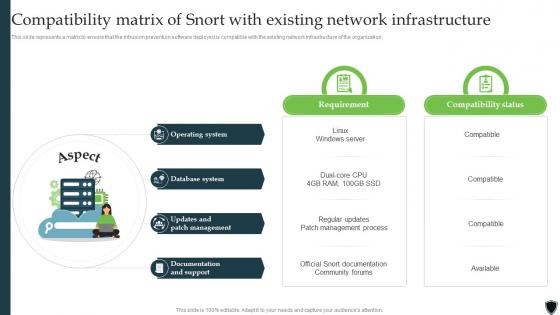 Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS
Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SSThis slide represents a matrix to ensure that the intrusion prevention software deployed is compatible with the existing network infrastructure of the organization. Introducing Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Operating System, Database System, Updates And Patch Management, Documentation And Support, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SSThis slide represents details related to the configuration of alerts for deployed network security tool that monitors networks for preventing, reporting, and blocking malicious activities. Introducing Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on SNMP Alert Objects, Remote Syslog Alert Objects, Quarantine Response Objects, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SSThis slide shows the cost-benefit analysis of deploying Intrusion prevention system, including the costs incurred in deploying IPS platform and providing training to employees. Present the topic in a bit more detail with this Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Initial Cost, Costs, Training Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SS
Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SSThis slide details the costs associated with deploying an Intrusion prevention system solution in an enterprise. It includes expenses for implementing IPS software, IT talent acquisition costs, training costs etc. Introducing Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Intrusion Prevention Software, IT Talent Acquisition Costs, Training Costs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SS
Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SSThis slide represents details related to the first step of deploying a network security tool that monitors networks to prevent malicious activities including blocking, reporting or dropping it. Introducing Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SS to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Active Directory, IT Monitoring Servers, Public Servers, Database Servers, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SSThis slide represents details related to customization of implemented network security tool that monitors networks to prevent, report and block malicious activities to organizations IT environment. Introducing Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Servers, Metric Performance, Values, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SS
Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SSThis slide represents a strategic plan to effectively respond to cybersecurity incidents experienced by the organization, including action steps such as a cyber incident reports, verification of incidents, etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SS. Use it as a tool for discussion and navigation on Cyber Incident Report, Verification Of Incident, Response Arrives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
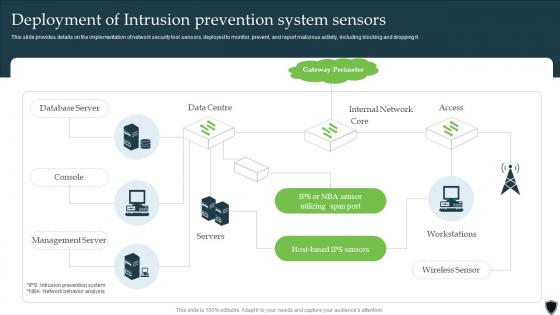 Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SSThis slide provides details on the implementation of network security tool sensors, deployed to monitor, prevent, and report malicious activity, including blocking and dropping it. Introducing Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Database Server, Gateway Perimeter, Workstations, Management Server, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS
Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SSThis slide represents details related to fine-tuning threat detection rules for the implemented IPS software to effectively align with the organizations threat landscape. Present the topic in a bit more detail with this Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS. Use it as a tool for discussion and navigation on Preprocessor Rule, Standard Text Rule, Shared Object Rule. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
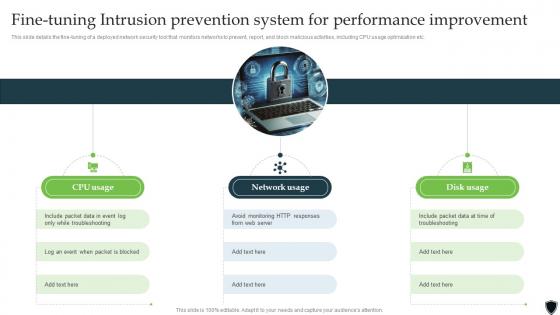 Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SSThis slide details the fine-tuning of a deployed network security tool that monitors networks to prevent, report, and block malicious activities, including CPU usage optimization etc. Introducing Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on CPU Usage, Network Usage, Disk Usage, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS
Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SSThis slide outlines the hardware requirements to consider when selecting a network security tool to monitor and prevent malicious activities. These requirements include network interfaces etc. Introducing Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Interfaces, Storage, Redundancy, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS
Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SSThis slide presents critical assets and associated threats, such as data breaches, information manipulation, data corruption, identity theft, etc., identified by the IT team. Present the topic in a bit more detail with this Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS. Use it as a tool for discussion and navigation on Critical Assets, Network Infrastructure, Application Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS
Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SSThis slide covers details related to real-time monitoring of system alerts provided by deployed network security tool that monitors networks for preventing, reporting and blocking malicious activities. Introducing Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Pattern Recognition, Automated Response, Behavioral Analysis, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SS
Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SSThis slide represents a strategic plan for protecting the organization against software vulnerabilities, including action steps such as establishing a regular patching schedule, successfully testing patches, etc. Introducing Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Establish Regular Patching Schedule, Progress Status, Successfully Test Patches, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS
Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SSThis slide represents cybersecurity attacks detected and prevented by a network security tool that monitors the network for malicious activities, including DDoS attacks, ARP spoofing, and IP fragmentation. Introducing Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Distributed Denial Of Service, Address Resolution Protocol ARP Spoofing, IP Fragmentation, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SSThis slide presents reasons to invest in a network security tool that monitors the network to prevent malicious activities, protect against known and unknown threats, etc. Introducing Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Protection Against Known, Unknown Threats, Real-Time Detection, Blocking Of Malicious Traffic, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SS
Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SSThis slide outlines the software requirements to consider when selecting a network security tool to monitor and prevent malicious activities. These requirements include scalability, operating system etc. Introducing Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Operating System, Database Management System, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SS
Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SSThis slide details the training plan to facilitate the effective use of deployed IPS software by employees. It includes training topics such as traffic analysis, IPS signatures and analysis, web app attacks etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SS. Use it as a tool for discussion and navigation on Training Method, Traffic Analysis, Anomaly Detection Systems, Web Application Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Update Signatures And Rules For Deployed Ips Solution Cybersecurity SS
Implementing Intrusion Prevention Update Signatures And Rules For Deployed Ips Solution Cybersecurity SSThis slide represents details related to upgradation of signatures and rules for the implemented network security tool that monitors networks to prevent, report and block malicious activities. Present the topic in a bit more detail with this Implementing Intrusion Prevention Update Signatures And Rules For Deployed Ips Solution Cybersecurity SS. Use it as a tool for discussion and navigation on Update Server, Internet, Manager Server, Sensor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a training plan to help employees effectively prevent phishing attacks. It covers topics such as email communication, blocking popups and ads, report phishing attempts etc.Deliver an outstanding presentation on the topic using this Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Method, Expected Completion Date, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksPresent the topic in a bit more detail with this Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks. Use it as a tool for discussion and navigation on Security Awareness, Current Assessment, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Implementing Security Awareness Training
Social Engineering Attack Prevention Techniques Implementing Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
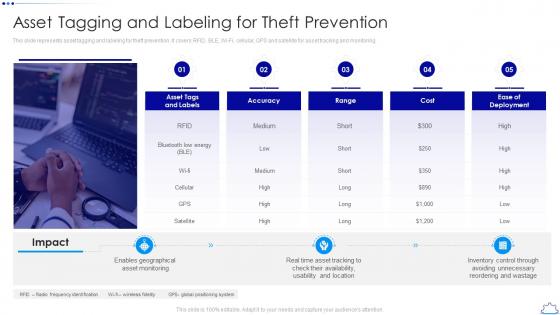 Asset Tagging And Labeling For Theft Prevention Implementing Fixed Asset Management
Asset Tagging And Labeling For Theft Prevention Implementing Fixed Asset ManagementThis slide represents asset tagging and labeling for theft prevention. It covers RFID, BLE, Wi Fi, cellular, GPS and satellite for asset tracking and monitoring. Increase audience engagement and knowledge by dispensing information using Asset Tagging And Labeling For Theft Prevention Implementing Fixed Asset Management. This template helps you present information on five stages. You can also present information on Asset Tagging, Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist For Violence Prevention Policy Implementation At Workplace
Checklist For Violence Prevention Policy Implementation At WorkplaceThis slide covers prerequisites for implementation of policy at workplace. It includes obligations such as conducting risk assessment, status on pre-existing policy, inclusion of mission statement, committee member details, etc. Introducing our Checklist For Violence Prevention Policy Implementation At Workplace set of slides. The topics discussed in these slides are Risk Assessment Conducted, Mission Statement, Committee Members. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Agenda For Implementing Security Awareness Training To Prevent Cyber Attacks
Agenda For Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing Agenda For Implementing Security Awareness Training To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Awareness Campaign, Cyber Security, Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Dos And Donts Of Prevention From Ransomware Attack Implementing Security Awareness Training
Dos And Donts Of Prevention From Ransomware Attack Implementing Security Awareness TrainingThe purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Introducing Dos And Donts Of Prevention From Ransomware Attack Implementing Security Awareness Training to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Prevention, Ransomware Attack, using this template. Grab it now to reap its full benefits.
-
 G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Current Assessment, Organization, Cyber Security, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Implementing Security Awareness Training To Prevent Cyber Attacks
Icons Slide For Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing our well researched set of slides titled Icons Slide For Implementing Security Awareness Training To Prevent Cyber Attacks. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Various Techniques To Successfully Prevent Business Implementing Security Awareness Training
Various Techniques To Successfully Prevent Business Implementing Security Awareness TrainingThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Increase audience engagement and knowledge by dispensing information using Various Techniques To Successfully Prevent Business Implementing Security Awareness Training. This template helps you present information on one stage. You can also present information on Sender Policy Framework, Strong Process For Wire Transfers, Strong Password Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Management System For Theft Prevention Strategic Guide To Manage And Control Warehouse
Implementing Management System For Theft Prevention Strategic Guide To Manage And Control WarehouseThis slide showcases implementation of warehouse management system that can help organization in theft prevention. It showacses features and impact of implementing WMS in organization. Present the topic in a bit more detail with this Implementing Management System For Theft Prevention Strategic Guide To Manage And Control Warehouse. Use it as a tool for discussion and navigation on Stock Keeping Units, Cycle Counting, Licence Plating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Hazard Prevention And Control Based On Hierarchy Control Implementation Of Safety Management Workplace Injuries
Hazard Prevention And Control Based On Hierarchy Control Implementation Of Safety Management Workplace InjuriesThe following slide showcases the strategy to prevent and control hazards at workplace through hierarchy of control model. Key requirements for the implementation of model are comparative analysis of current control methods and potential control options with the company. Present the topic in a bit more detail with this Hazard Prevention And Control Based On Hierarchy Control Implementation Of Safety Management Workplace Injuries. Use it as a tool for discussion and navigation on Prevention, Hierarchy, Comparative. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cost Involved In Implementing Customer Attrition Prevent Customer Attrition And Build
Cost Involved In Implementing Customer Attrition Prevent Customer Attrition And BuildThis slide shows the cost involved in implementing customer attrition management strategies such as onboarding process, CRM implementation, customer loyalty program and engagement platforms. Introducing Cost Involved In Implementing Customer Attrition Prevent Customer Attrition And Build to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Customer Onboarding Process, Customer Loyalty Program, Management Strategies, using this template. Grab it now to reap its full benefits.
-
 In House Training Schedule We Will Implement Preventing Data Breaches Through Cyber Security
In House Training Schedule We Will Implement Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto jacking and IoT Based attack. Present the topic in a bit more detail with this In House Training Schedule We Will Implement Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Compromise, Training. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security
Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Increase audience engagement and knowledge by dispensing information using Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Gamification, Personalization, High Quality Content using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline Implementing Transaction Monitoring Preventing Money Laundering Through Transaction
Timeline Implementing Transaction Monitoring Preventing Money Laundering Through TransactionThis slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc.Increase audience engagement and knowledge by dispensing information using Timeline Implementing Transaction Monitoring Preventing Money Laundering Through Transaction. This template helps you present information on one stage. You can also present information on Scenario Planning, Threshold Setting, Customer Segmentation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline Implementing Transaction Monitoring Using AML Monitoring Tool To Prevent
Timeline Implementing Transaction Monitoring Using AML Monitoring Tool To PreventThis slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc.Present the topic in a bit more detail with this Timeline Implementing Transaction Monitoring Using AML Monitoring Tool To Prevent. Use it as a tool for discussion and navigation on Automated Transaction, Monitoring Approach, Onboarding Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Tactics To Prevent Cyber Attacks Cyber Attack Risks Mitigation
Implement Tactics To Prevent Cyber Attacks Cyber Attack Risks MitigationThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Implement Tactics To Prevent Cyber Attacks Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Opening Suspicious Emails, Keep Systems Up To Date, Leverage Firewalls, using this template. Grab it now to reap its full benefits.
-
 Implementing Warehouse Management System For Theft Prevention Ppt Pictures
Implementing Warehouse Management System For Theft Prevention Ppt PicturesThis slide showcases implementation of warehouse management system that can help organization in theft prevention. It showacses features and impact of implementing WMS in organization. Deliver an outstanding presentation on the topic using this Implementing Warehouse Management System For Theft Prevention Ppt Pictures Dispense information and present a thorough explanation of Stock Keeping, Cycle, Licence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Development And Implementation User Awareness Training Program To Prevent Cyber Security Incidents
Development And Implementation User Awareness Training Program To Prevent Cyber Security IncidentsThis slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Deliver an outstanding presentation on the topic using this Development And Implementation User Awareness Training Program To Prevent Cyber Security Incidents. Dispense information and present a thorough explanation of Password Security, Cloud And Internet Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Customer Loyalty Program Paid Strengthening Customer Loyalty By Preventing
Implementing Customer Loyalty Program Paid Strengthening Customer Loyalty By PreventingMentioned slide outlines a paid loyalty program through which corporates can increase customer lifetime value CLV and product sales. Information covered in this slide is related to promotional days, discount on purchase, bonus points on exclusive sale, free shipping, invitation to special events, etc. Introducing Implementing Customer Loyalty Program Paid Strengthening Customer Loyalty By Preventing to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Customer, Loyalty, Program, using this template. Grab it now to reap its full benefits.
-
 Implementing Customer Loyalty Program Points Based Strengthening Customer Loyalty By Preventing
Implementing Customer Loyalty Program Points Based Strengthening Customer Loyalty By PreventingMentioned slide outlines a points based loyalty program that can assist managers in improving the customer retention rate. It contains detailed information about the points system and rewards the customer will get after reaching certain points. Present the topic in a bit more detail with this Implementing Customer Loyalty Program Points Based Strengthening Customer Loyalty By Preventing. Use it as a tool for discussion and navigation on Product, Facebook, Instagram. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Customer Loyalty Program Tiered Strengthening Customer Loyalty By Preventing
Implementing Customer Loyalty Program Tiered Strengthening Customer Loyalty By PreventingMentioned slide outlines a tier based customer loyalty program that can be used to generate more referrals and increase the purchase rate. The program provides information about key elements such as sign up offer, birthday gift, free beauty set, early access to exclusive sale, etc. Introducing Implementing Customer Loyalty Program Tiered Strengthening Customer Loyalty By Preventing to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Customer, Loyalty, Program, using this template. Grab it now to reap its full benefits.
-
 Q925 Implementing Warehouse Management System For Theft Prevention Techniques To Optimize
Q925 Implementing Warehouse Management System For Theft Prevention Techniques To OptimizeThis slide showcases implementation of warehouse management system that can help organization in theft prevention. It showacses features and impact of implementing WMS in organization. Present the topic in a bit more detail with this Q925 Implementing Warehouse Management System For Theft Prevention Techniques To Optimize. Use it as a tool for discussion and navigation on Parameters, System Security, Warehouse Theft. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cost Involved In Implementing Customer Attrition Customer Retention Plan To Prevent Churn
Cost Involved In Implementing Customer Attrition Customer Retention Plan To Prevent ChurnThis slide shows the cost involved in implementing customer attrition management strategies such as onboarding process, CRM implementation, customer loyalty program and engagement platforms. Deliver an outstanding presentation on the topic using this Cost Involved In Implementing Customer Attrition Customer Retention Plan To Prevent Churn. Dispense information and present a thorough explanation of Implementing, Customer, Strategies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How Blockchain Prevents Fraud And Implementing Blockchain Security Solutions
How Blockchain Prevents Fraud And Implementing Blockchain Security SolutionsThis slide describes the different methods used by blockchain technology to prevent data from fraud and stealing. The purpose of this slide is to showcase the various techniques and technologies used in blockchain technology to prevent fraud and data theft.Increase audience engagement and knowledge by dispensing information using How Blockchain Prevents Fraud And Implementing Blockchain Security Solutions. This template helps you present information on four stages. You can also present information on Extremely Difficult, Blockchain Incorporates, Techniques Such using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Preventive Measures Against Implementing Blockchain Security Solutions
Preventive Measures Against Implementing Blockchain Security SolutionsThis slide represents the steps to prevent distributed daniel of service attacks in blockchain technology. The purpose of this slide is to showcase the different security measures against ddos attacks, including implementing traffic filtering, employing load balancing, utilizing rate limiting and so on..Present the topic in a bit more detail with this Preventive Measures Against Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Collaborate Communicate, Decentralized Network, Implement Traffic Filtering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Customer Loyalty Program Paid Customer Attrition Rate Prevention
Implementing Customer Loyalty Program Paid Customer Attrition Rate PreventionMentioned slide outlines a paid loyalty program through which corporates can increase customer lifetime value CLV and product sales. Information covered in this slide is related to promotional days, discount on purchase, bonus points on exclusive sale, free shipping, invitation to special events, etc. Present the topic in a bit more detail with this Implementing Customer Loyalty Program Paid Customer Attrition Rate Prevention. Use it as a tool for discussion and navigation on Promotional Days, Access To Special Discounts, Invitation To Special Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Customer Loyalty Program Points Based Customer Attrition Rate Prevention
Implementing Customer Loyalty Program Points Based Customer Attrition Rate PreventionMentioned slide outlines a points-based loyalty program that can assist managers in improving the customer retention rate. It contains detailed information about the points system and rewards the customer will get after reaching certain points. Introducing Implementing Customer Loyalty Program Points Based Customer Attrition Rate Prevention to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Implementing Customer, Loyalty Program, Points Based, using this template. Grab it now to reap its full benefits.
-
 Implementing Customer Loyalty Program Tiered Based Customer Attrition Rate Prevention
Implementing Customer Loyalty Program Tiered Based Customer Attrition Rate PreventionMentioned slide outlines a tier based customer loyalty program that can be used to generate more referrals and increase the purchase rate. The program provides information about key elements such as sign up offer, birthday gift, free beauty set, early access to exclusive sale, etc. Present the topic in a bit more detail with this Implementing Customer Loyalty Program Tiered Based Customer Attrition Rate Prevention. Use it as a tool for discussion and navigation on Products, Early Access To Sales, Implementing Customer. This template is free to edit as deemed fit for your organization. Therefore download it now.





