Powerpoint Templates and Google slides for Implement Network Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
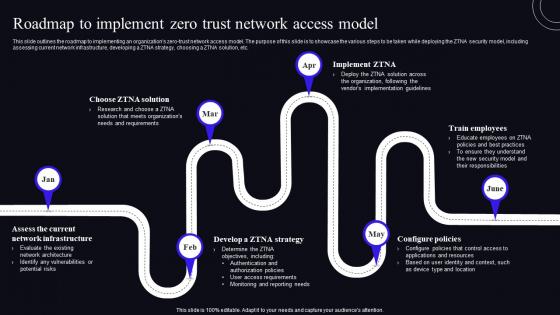 Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model
Roadmap To Implement Zero Trust Network Access Model Zero Trust Security ModelThis Slide Outlines The Roadmap To Implementing An Organizations Zero-Trust Network Access Model. The Purpose Of This Slide Is To Showcase The Various Steps To Be Taken While Deploying The ZTNA Security Model, Including Assessing Current Network Infrastructure, Developing A ZTNA Strategy, Choosing A ZTNA Solution, Etc. Increase Audience Engagement And Knowledge By Dispensing Information Using Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model. This Template Helps You Present Information On Six Stages. You Can Also Present Information On Roadmap, Network Infrastructure, Configure Policies Using This PPT Design. This Layout Is Completely Editable So Personaize It Now To Meet Your Audiences Expectations.
-
 Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model
Before Vs After Zero Trust Network Access Implementation Zero Trust Security ModelThis slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Deliver an outstanding presentation on the topic using this Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model. Dispense information and present a thorough explanation of Implementation, Distributed, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model
F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security ModelThis slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Present the topic in a bit more detail with this F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Organizations, Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Security Model
Steps To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Protection, Monitor The Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model
Timeline To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Implementation, Applications, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway
Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web GatewayThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Productivity, Enforcement, Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway
Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Deliver an outstanding presentation on the topic using this Best Practices For Secure Web Gateway Implementation Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Assessment, Functionality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Secure Web Gateway Network Security Using Secure Web Gateway
Checklist To Implement Secure Web Gateway Network Security Using Secure Web GatewayThis slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Deliver an outstanding presentation on the topic using this Checklist To Implement Secure Web Gateway Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Configure Solution, Plan Deployment, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Methods To Implement Security Policies On Network Security Using Secure Web Gateway
Methods To Implement Security Policies On Network Security Using Secure Web GatewayThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Deliver an outstanding presentation on the topic using this Methods To Implement Security Policies On Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Organizational, Examination, Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Implementation Methodology Explicit Network Security Using Secure Web Gateway
Secure Implementation Methodology Explicit Network Security Using Secure Web GatewayThis slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Deliver an outstanding presentation on the topic using this Secure Implementation Methodology Explicit Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Methodology, Concentrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateway Implementation Transparent Network Security Using Secure Web Gateway
Secure Web Gateway Implementation Transparent Network Security Using Secure Web GatewayThis slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Deliver an outstanding presentation on the topic using this Secure Web Gateway Implementation Transparent Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Methodology, Communications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web Gateway
Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web GatewayThis slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Present the topic in a bit more detail with this Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Implementation, Methodology, Analyzer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Network Security Model To Effective Communication Strategy SS V
Implementation Of Information Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Present the topic in a bit more detail with this Implementation Of Information Network Security Model To Effective Communication Strategy SS V. Use it as a tool for discussion and navigation on Message Transformation, Information Channel. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network
Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into NetworkThe purpose of this slide is to outline the steps involved in implementing a security protocol into a network. These are access network requirements, plan and design, select the right protocol, prepare the network infrastructure, configure devices, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network. Dispense information and present a thorough explanation of Assess Network Requirements, Implement User Authentication, Suitable Security Protocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Security Protocols Required According To Type Of Network
Encryption Implementation Strategies Security Protocols Required According To Type Of NetworkThe purpose of this slide is to outline different security protocols used in various types of networks, and their specific applications. These network types are wired, wireless networks, Local Area Networks LANs, Wide Area Networks WANs, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Security Protocols Required According To Type Of Network. Use it as a tool for discussion and navigation on Local Area Networks, Wide Area Networks, Wired Networks, Wireless Networks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Approaches To Implement Zero Trust Network Access Cloud Security Model
Approaches To Implement Zero Trust Network Access Cloud Security ModelThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Approaches To Implement Zero Trust Network Access
Sase Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Sase Security Approaches To Implement Zero Trust Network Access. Dispense information and present a thorough explanation of Approaches, Organizations, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase
Approaches To Implement Zero Trust Network Access Secure Access Service Edge SaseThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Approaches, Endpoint Initiated, Service Initiated using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V
Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V Dispense information and present a thorough explanation of Communication, Data Management, Marketing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker SASE Network Security
Best Practices To Implement Cloud Access Security Broker SASE Network SecurityThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker SASE Network Security. Dispense information and present a thorough explanation of Visibility, Risk, Release using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Implementation Models SASE Network Security
Cloud Access Security Broker Implementation Models SASE Network SecurityThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Cloud Access Security Broker Implementation Models SASE Network Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward, Reverse, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Approaches To Implement Zero Trust Network Access
SASE Network Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero trust network access. It also includes how users access business services and applications in both approaches. Increase audience engagement and knowledge by dispensing information using SASE Network Security Approaches To Implement Zero Trust Network Access. This template helps you present information on two stages. You can also present information on Program, Environment, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Budget To Implement Secure Access Service Edge
SASE Network Security Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD WAN, SWG, ZTNA, CASB, and FWaaS. Deliver an outstanding presentation on the topic using this SASE Network Security Budget To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Network, Secure, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Challenges And Solutions For SASE Implementation
SASE Network Security Challenges And Solutions For SASE ImplementationThis slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. Deliver an outstanding presentation on the topic using this SASE Network Security Challenges And Solutions For SASE Implementation. Dispense information and present a thorough explanation of Security, Management, Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Checklist To Implement Secure Access Service Edge
SASE Network Security Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SASE Network Security Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Responsible, Service, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Roadmap To Implement Secure Access Service Edge
SASE Network Security Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SASE Network Security Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Providers, Deployment, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Secure Access Service Edge Implementation Steps
SASE Network Security Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD WAN backbone, incorporating zero trust solutions, etc. Introducing SASE Network Security Secure Access Service Edge Implementation Steps to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Requirements, Solutions, Service, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Timeline To Implement Cloud Access Security Broker
SASE Network Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing SASE Network Security Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Applications, Company, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Secure Access Service Edge SASE Network Security
Timeline To Implement Secure Access Service Edge SASE Network SecurityThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge SASE Network Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Solutions, Regularly, using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Standard Architectural Implementations Of Network Firewalls
Firewall Network Security Standard Architectural Implementations Of Network FirewallsThis slide outlines the common architectural deployments of network firewalls. The purpose of this slide is to showcase the different architectural implementations of firewalls, including packet filtering routers, screened host firewalls, dual-homed host, and screened subnet with DMZ. Present the topic in a bit more detail with this Firewall Network Security Standard Architectural Implementations Of Network Firewalls Use it as a tool for discussion and navigation on Access Control List, Workflow, Overview This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security
Firewall Network Security 30 60 90 Days Plan To Implement Firewall SecurityThis slide outlines the 30-60-90 days plan to integrate firewalls in a business. The purpose of this slide is to showcase the various steps that should be taken at the interval of every 30 days, such as assessing the current security landscape, defining firewall requirements and selecting solutions, etc. Present the topic in a bit more detail with this Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security Use it as a tool for discussion and navigation on 30 Days, 60 Days, 90 Days This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Cost Summary For Firewall Network Security Implementation
Firewall Network Security Cost Summary For Firewall Network Security ImplementationThis slide outlines the summary of total budget for implementing firewalls in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Deliver an outstanding presentation on the topic using this Firewall Network Security Cost Summary For Firewall Network Security Implementation Dispense information and present a thorough explanation of Project Cost Summary, Project Details using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS
Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SSThis slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Deliver an outstanding presentation on the topic using this Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Assets Organisations, Between Segments, Monitor Segments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide shows the cost-benefit analysis of implementing network vulnerability management strategies, including the costs incurred in end-to-end encryption and phishing awareness training, etc.Deliver an outstanding presentation on the topic using this Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Costs, Benefits, Description, Initial Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide details the costs associated with deploying network vulnerability management solutions for an enterprise. It includes expenses for implementing E2E software, IT talent acquisition costs etc.Deliver an outstanding presentation on the topic using this Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Parameters, Forecasted Budget, Actual Costs, Variance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
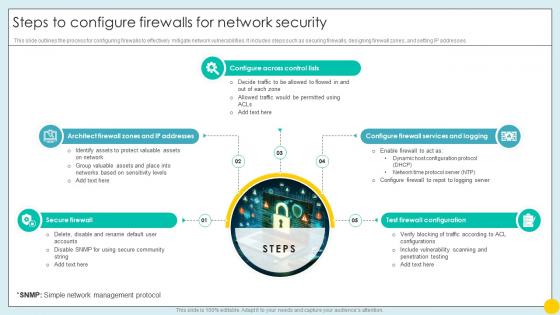 Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS
Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the process for configuring firewalls to effectively mitigate network vulnerabilities. It includes steps such as securing firewalls, designing firewall zones, and setting IP addresses.Increase audience engagement and knowledge by dispensing information using Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Secure Firewall, Configure Across Control Lists, Test Firewall Configuration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Impact On Organization After Implementing
Network Security Impact On Organization After ImplementingThis slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver an outstanding presentation on the topic using this Network Security Impact On Organization After Implementing. Dispense information and present a thorough explanation of Impact On Organization After Implementing Network Security Strategy And Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Complete Network Security Implementation Checklist
Network Security Complete Network Security Implementation ChecklistThis slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Introducing Network Security Complete Network Security Implementation Checklist to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Complete Network Security Implementation Checklist, using this template. Grab it now to reap its full benefits.
-
 Network Security Implementation Of Strong Password Policy
Network Security Implementation Of Strong Password PolicyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Network Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Network Security Timeline For The Implementation Of Network Security
Network Security Timeline For The Implementation Of Network SecurityThis slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Network Security Timeline For The Implementation Of Network Security. Use it as a tool for discussion and navigation on Timeline For The Implementation Of Network Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business
Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping BusinessThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business. Use it as a tool for discussion and navigation on Strategy, Authentication, Appropriate Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Implementation Of Complete Digital Security Network
Icon For Implementation Of Complete Digital Security NetworkPresenting our set of slides with name Icon For Implementation Of Complete Digital Security Network. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Security Network.
-
 Implementation Process Of Network Infra Security
Implementation Process Of Network Infra SecurityThe following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Introducing Implementation Process Of Network Infra Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Segmentation, Hardware, Software, using this template. Grab it now to reap its full benefits.
-
 SDN Security IT Implementation Process Of Software Defined Networking SDN
SDN Security IT Implementation Process Of Software Defined Networking SDNThis slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. Increase audience engagement and knowledge by dispensing information using SDN Security IT Implementation Process Of Software Defined Networking SDN. This template helps you present information on four stages. You can also present information on Process, Implementation, Software using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SDN Security IT Roadmap For Software Defined Network Implementation
SDN Security IT Roadmap For Software Defined Network ImplementationThis slide outlines the roadmap for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Increase audience engagement and knowledge by dispensing information using SDN Security IT Roadmap For Software Defined Network Implementation. This template helps you present information on four stages. You can also present information on Roadmap, Software, Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SDN Security IT Timeline For Software Defined Network Implementation
SDN Security IT Timeline For Software Defined Network ImplementationThis slide talks about the timeline for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Introducing SDN Security IT Timeline For Software Defined Network Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Software, Network, using this template. Grab it now to reap its full benefits.
-
 Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SS
Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SSThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc.Present the topic in a bit more detail with this Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Message Transformation, Secure Message, Security Breaches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network security implementation ppt powerpoint presentation icon deck cpb
Network security implementation ppt powerpoint presentation icon deck cpbPresenting this set of slides with name Network Security Implementation Ppt Powerpoint Presentation Icon Deck Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Network Security Implementation to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Firewall Implementation For Cyber Security Firewall Network Performance Tracking Dashboard
Firewall Implementation For Cyber Security Firewall Network Performance Tracking DashboardThis slide outlines the overall performance of a firewall-protected network. The purpose of this slide is to showcase the total traffic, traffic by application, URLs by actions, threats by severity, traffic by source IP, traffic by application, blocked URLs by category, threats by severity, and so on. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Firewall Network Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Firewall Network Performance, Tracking Dashboard, Traffic By Application, Firewall Protected Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Firewall Network Traffic Monitoring Dashboard
Firewall Implementation For Cyber Security Firewall Network Traffic Monitoring DashboardThis slide showcases the network traffic monitoring dashboard by firewall mechanism. The purpose of this slide is to showcase the different aspects of network traffic, such as traffic by zone, URL categories by traffic, applications by traffic, traffic source IP, and so on. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Firewall Network Traffic Monitoring Dashboard. Dispense information and present a thorough explanation of Firewall Network Traffic, Monitoring Dashboard, Applications By Traffic, Firewall Mechanism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Global Market Summary Of Firewall Network Security
Firewall Implementation For Cyber Security Global Market Summary Of Firewall Network SecurityThis slide illustrates the worldwide market analysis for firewall network security. The purpose of this slide is to give an overview of the global firewall network security market, including CAGR rate, regional analysis, organization size segment, and key players. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Global Market Summary Of Firewall Network Security. Dispense information and present a thorough explanation of Worldwide Market Analysis, Firewall Network Security, Global Firewall Network Security Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Problems With Current Network Security System
Firewall Implementation For Cyber Security Problems With Current Network Security SystemThis slide highlights the loss experienced by the organization due to the existing security system. The purpose of this slide is to showcase the various cyber attack incidents and losses caused by them to the organization, such as malware infections, unauthorized access, phishing, etc. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Problems With Current Network Security System. Use it as a tool for discussion and navigation on Existing Security System, Cyber Attack Incidents, Malware Infections, Unauthorized Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Deployment Method Selection Of Firewall Network Security
Firewall Implementation For Cyber Security Deployment Method Selection Of Firewall Network SecurityThis slide represents the implementation methods of firewall security systems. The purpose of this slide is to showcase the different implementation options of firewall security systems, such as software-based applications, hardware-based applications, and cloud-based applications. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Deployment Method Selection Of Firewall Network Security. Use it as a tool for discussion and navigation on Network Segmentation, Supports Network Segmentation, Hardware For Security Functions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security How Firewall Implementation Will Improve Network Security
Firewall Implementation For Cyber Security How Firewall Implementation Will Improve Network SecurityThis slide talks about the main advantages of a firewall security system. The purpose of this slide is to highlight the key benefits of a firewall for businesses, such as spyware protection, the significant barrier against viruses, protection against hacking, privacy promotion, and network traffic monitoring. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security How Firewall Implementation Will Improve Network Security. Use it as a tool for discussion and navigation on Prevents Hacking, Privacy Promotion, Spyware Protection, Network Security. This template is free to edit as deemed fit for your organization. Therefore download it now.




