Powerpoint Templates and Google slides for Guide Implementation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Timeline For Hybrid Work Strategy Implementation Guide For Hybrid Workplace Strategy
Timeline For Hybrid Work Strategy Implementation Guide For Hybrid Workplace StrategyThis slide illustrates a timeline for the successful implementation of a hybrid workplace strategy. Various steps included are establishing centralized cloud-based system, adopting remote-working model, etc. Introducing Timeline For Hybrid Work Strategy Implementation Guide For Hybrid Workplace Strategy to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Establish Centralized, Cloud Based System, Optimize Remote Collaboration, using this template. Grab it now to reap its full benefits.
-
 Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SS
Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SSThis slide showcases Access management techniques to prevent cyber attacks. It includes strategies such as Single sign-On, password management, biometric authentication and access control lists ACLs.Introducing Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Password Management, Biometric Authentication, Access Control Lists, using this template. Grab it now to reap its full benefits.
-
 Attribution And Anonymity In Cyberspace To Deal Terrorism Strategic Guide To Implement Strategy SS
Attribution And Anonymity In Cyberspace To Deal Terrorism Strategic Guide To Implement Strategy SSThis slide showcases the Attribution and anonymity in cyberspace to deal terrorism. It inludes elements such as definition, its importance, challenges, use cases and tools.Increase audience engagement and knowledge by dispensing information using Attribution And Anonymity In Cyberspace To Deal Terrorism Strategic Guide To Implement Strategy SS. This template helps you present information on two stages. You can also present information on Importance, Challenges, Anonymity, Attribution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Botnet Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Botnet Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Botnet attack with mitigation strategies, key elements and example. It also includes mitigation strategies such as cyber security measures and network monitoring.Introducing Botnet Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Key Elements, Mitigation Strategies, Example, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS
Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SSPresent the topic in a bit more detail with this Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Social Media, Gamepad, Firewall, Storage, Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Criminal Actor With Characteristics And Aspects Strategic Guide To Implement Strategy SS
Cyber Criminal Actor With Characteristics And Aspects Strategic Guide To Implement Strategy SSThis slide showcases an overview of cyber criminal. It includes its characteristics and activities such as financial motivation, diverse criminal activities, black market activities, legal consequences and impact on victims.Introducing Cyber Criminal Actor With Characteristics And Aspects Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Diverse Criminal Activities, Financial Motivation, Black Market Activities, using this template. Grab it now to reap its full benefits.
-
 Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Cyber Espionage attack with mitigation strategies and example. It includes mitigation strategies such as regular security audits and threat intelligence.Increase audience engagement and knowledge by dispensing information using Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Key Elements, Mitigation Strategies, Example using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SSThis slide showcases the Cyber security Best Practices essential for government. It includes best practices such as Investment in cyber security, International Cooperation, Public-Private Partnerships and Capacity Building.Introducing Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Public Private Partnerships, International Cooperation, Investment In Cybersecurity, Capacity Building, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SSThis slide showcases Cyber security Best Practices essential for individual. It includes best practices such as strong passwords, public Wi-Fi, device security and social media privacy. Increase audience engagement and knowledge by dispensing information using Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Strong Passwords, Device Security, Social Media Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SSThis slide showcases the Cyber security Best Practices essential for organizations. It includes strategies such as Network Security, Access control, Patch Management and Vendor Security.Present the topic in a bit more detail with this Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Access Controls, Network Security, Patch Management, Vendor Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism Framework In Digital Age Strategic Guide To Implement Strategy SS
Cyberterrorism Framework In Digital Age Strategic Guide To Implement Strategy SSIncrease audience engagement and knowledge by dispensing information using Cyberterrorism Framework In Digital Age Strategic Guide To Implement Strategy SS. This template helps you present information on one stages. You can also present information on Threat Actors, Targeted Servers, Legitimate User, Obfuscate Their Identities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SS
Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Dark web and encrypted communications in cyber terrorism. It includes elements such as definition, characteristics, implications and use cases.Introducing Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Implications, Use Cases, Characteristics, Define, using this template. Grab it now to reap its full benefits.
-
 Denial Of Service Dos And Distributed Denial Of Service Ddos Strategic Guide To Implement Strategy SS
Denial Of Service Dos And Distributed Denial Of Service Ddos Strategic Guide To Implement Strategy SSThis slide showcases the Denial-of-Service DoS and Distributed Denial-of-Service DDoS Attacks. It also includes mitigation measures such as firewalls that used to determine inbound requests to website are legitimate.Present the topic in a bit more detail with this Denial Of Service Dos And Distributed Denial Of Service Ddos Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Mitigation Measures, Example, Firewalls, Handle Legitimate Service Requests. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 DNS Spoofing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
DNS Spoofing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the DNS spoofing attack with mitigation strategies and example. It also includes mitigation strategies such as use DNSSEC, use trusted DNS servers and frequent monitoring DNS software.Introducing DNS Spoofing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, using this template. Grab it now to reap its full benefits.
-
 Eavesdropping Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Eavesdropping Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Eavesdropping attack with mitigation strategies and example. It also includes mitigation strategies such as secure networks and endpoint security.Increase audience engagement and knowledge by dispensing information using Eavesdropping Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
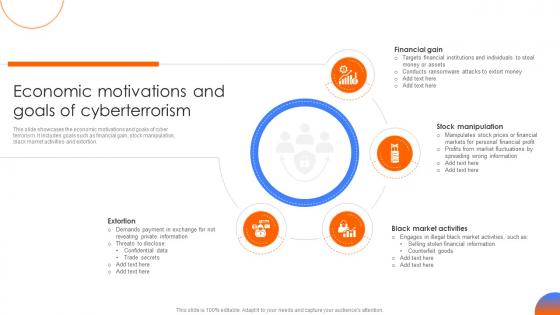 Economic Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS
Economic Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the economic motivations and goals of cyber terrorism. It includes goals such as financial gain, stock manipulation, black market activities and extortion.Introducing Economic Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Financial Gain, Stock Manipulation, Black Market Activities, Extortion, using this template. Grab it now to reap its full benefits.
-
 Education And Awareness Campaigns For Cyber Terrorism Strategic Guide To Implement Strategy SS
Education And Awareness Campaigns For Cyber Terrorism Strategic Guide To Implement Strategy SSThis slide showcases the Education and Awareness Campaigns for cyber terrorism. It includes best practices such as Government and Industry Partnership, Interactive Training, Public-Private Partnerships and Online Resources.Increase audience engagement and knowledge by dispensing information using Education And Awareness Campaigns For Cyber Terrorism Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Interactive Training, Government And Industry Partnerships, Public Private Partnerships, Online Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Emerging Threats Quantum Computing And Ai Strategic Guide To Implement Strategy SS
Emerging Threats Quantum Computing And Ai Strategic Guide To Implement Strategy SSThis slide showcases the Emerging Threats Quantum Computing and AI. It includes elements such as defining Quantum computers and AI and its implications.Introducing Emerging Threats Quantum Computing And Ai Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Quantum Computers, Secure Communication, Quantum Computing, Artificial Intelligence, using this template. Grab it now to reap its full benefits.
-
 Global Historical Evolution Of Cyberterrorism Strategic Guide To Implement Strategy SS
Global Historical Evolution Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the global historical evolution od cyber terrorism. It includes some events such as start of hacking era, 414s group arrested, worm spread globally, WannaCry and NotPetya ransom ware attacks.Increase audience engagement and knowledge by dispensing information using Global Historical Evolution Of Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on six stages. You can also present information on Supply Chain Attacks, Cyber Threats, University Systems, Hacking Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Hacktivists Actors With Characteristics And Aspects Strategic Guide To Implement Strategy SS
Hacktivists Actors With Characteristics And Aspects Strategic Guide To Implement Strategy SSThis slide showcases the Hacktivists actors. It includes its characteristics and activities such as motivation, protest and awareness, tactics and techniques, targets and impact.Introducing Hacktivists Actors With Characteristics And Aspects Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Motivation, Protest And Awareness, Tactics And Techniques, Impact, Targets, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Icons Slide For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIntroducing our well researched set of slides titled Icons Slide For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Ideological Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS
Ideological Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Ideological motivations and goals of cyber terrorism. It includes goals such as anti-globalization, environmental activism, extremist ideologies and anti-corporate movements.Introducing Ideological Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Environmental Activism, Extremist Ideologies, Anti Corporate Movements, using this template. Grab it now to reap its full benefits.
-
 Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SS
Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SSThis slide showcases the Incident Response and Recovery Strategies for cyber terrorism. It includes strategies such as Incident Identification, Containment and Mitigation, Data Restoration and Resilience.Present the topic in a bit more detail with this Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Containment And Mitigation, Incident Identification, Eradication, Forensics And Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Insiders In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SS
Insiders In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SSThis slide showcases the insiders overview. It includes malicious insiders who intentionally misuse their authorized access for personal profit and negligent insiders who inadvertently endanger a company.Introducing Insiders In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Insiders, Negligent Insiders, Financial Crimes, Engages In Espionage, using this template. Grab it now to reap its full benefits.
-
 International Agreements And Treaties Of Cyberterrorism Strategic Guide To Implement Strategy SS
International Agreements And Treaties Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the International Agreements and Treaties of cyberterrorism. It includes agreements and treaties such as Budapest convention on cybercrime, united nations GGE reports, Tallinn manual, CCDCOE and US-EU privacy shield.Present the topic in a bit more detail with this International Agreements And Treaties Of Cyberterrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Tallinn Manual, Budapest Convention, Privacy Shield, Addressing Cyber Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SS
Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SSThis slide showcases the introduction to cyber terrorism. It includes its impact such as financial losses, economic impact, data breaches, political instability and social disruption.Deliver an outstanding presentation on the topic using this Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Economic Impact, Data Breaches, Social Disruption, Political Instability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction To Types Of Cyber Threat Actors Strategic Guide To Implement Strategy SS
Introduction To Types Of Cyber Threat Actors Strategic Guide To Implement Strategy SSThis slide showcases the market scenario of global automobile industry. It includes elements such as top worlds vehicle producers, number of cars sold worldwide and preference for type of engine in next vehicle.Introducing Introduction To Types Of Cyber Threat Actors Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Thrill Seekers, Cybercriminal Actors, Insiders, Hacktivists Actors, using this template. Grab it now to reap its full benefits.
-
 Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SS
Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SSThis slide showcases the major categories of cyber terrorism for data protection. It includes categories such as simple and unstructured, advanced-structure and complex-coordinated.Present the topic in a bit more detail with this Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Advanced Structure, Complex Coordinated, Categories, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Man-in-the-Middle MITM Attacks in cyber terrorism. It includes mitigation startegies such as encryption, PKI, network security, 2FA and secure Wi-Fi.Introducing Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Account Security, Network Security, Encryption, using this template. Grab it now to reap its full benefits.
-
 Nation State Actors With Characteristics And Activities Strategic Guide To Implement Strategy SS
Nation State Actors With Characteristics And Activities Strategic Guide To Implement Strategy SSThis slide showcases the nation-state actors. It includes its characteristics and activities such as government backing, activities, objectives and techniques.Increase audience engagement and knowledge by dispensing information using Nation State Actors With Characteristics And Activities Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Government Backing, Activities, Objectives, Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS
Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SSThis slide showcases the Need for vigilance and adaptation in cyber security. It includes key points such as evolving threat landscape, pervasive cyber attacks, data as a target, adaptive strategies and resilience building.Present the topic in a bit more detail with this Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Pervasive Cyberattacks, Adaptive Strategies, Resilience Building, Evolving Threat Landscape. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Objectives Of Cyber Terrorist To Increase Activities Strategic Guide To Implement Strategy SS
Objectives Of Cyber Terrorist To Increase Activities Strategic Guide To Implement Strategy SSThis slide showcases the main objectives of cyber terrorist to enhance activities. It includes objectives such as political goals, making money, causing fear, revenge and payback and stealing secrets.Deliver an outstanding presentation on the topic using this Objectives Of Cyber Terrorist To Increase Activities Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Political Goals, Making Money, Revenge And Payback, Stealing Secrets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SS
Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SSThis slide showcases the Offensive Cyber Operations and Deterrence. It includes elements such as definition, objective and examples.Present the topic in a bit more detail with this Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Define, Objective, Examples, Deterrence Cyber Operations, Offensive Cyber Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SS
Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SSThis slide showcases the Ongoing Threat of Cyber terrorism in digital age. It includes key aspects such as constant evolution of tactics, wide-ranging targets, legislation and regulation and future perspectives.Deliver an outstanding presentation on the topic using this Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Wide Ranging Targets, Legislation And Regulation, Future Perspectives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Phishing attack with mitigation strategies and its example. It also includes mitigation strategies such as user education, email filtering, MFA and incident reaction strategies.Introducing Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Example, Phishing Attack, Ideological Purposes, using this template. Grab it now to reap its full benefits.
-
 Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS
Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the political motivation and goals of cyber terrorism. It includes goals such as nationalism and separatism, conflict and warfare, influence elections and revenge and retaliation.Increase audience engagement and knowledge by dispensing information using Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Conflict And Warfare, Nationalism And Separatism, Influence Elections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SS
Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SSThis slide showcases the Psychological Factors of cyber terrorism identify potential risks. It includes goals such as revenge and grudges, mental helath isuues, desire for power and frustration and alienation.Present the topic in a bit more detail with this Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Mental Health Issues, Frustration And Alienation, Revenge And Grudges. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Ransomware attack with mitigation strategies and example. It also includes mitigation strategies such as regular backups, email security and antivirus and anti-malware.Increase audience engagement and knowledge by dispensing information using Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Encrypts Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SS
Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Role of Interpol and Europol in cyber terrorism. It also includes role such as global network, digital forensics, coordination and EC3, investigation support, operational coordination and public awareness.Introducing Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Global Network, Capacity Building, Digital Forensics, Coordination, using this template. Grab it now to reap its full benefits.
-
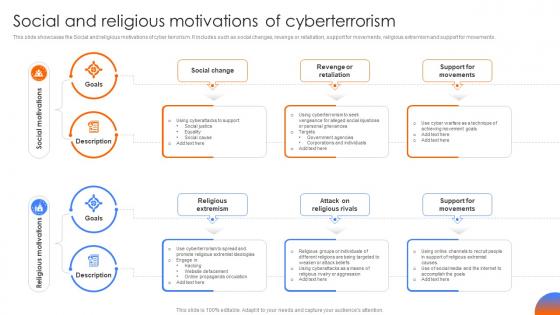 Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SS
Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Social and religious motivations of cyber terrorism. It includes such as social changes, revenge or retaliation, support for movements, religious extremism and support for movements.Present the topic in a bit more detail with this Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Description, Goals, Social Change, Social Motivations, Religious Motivations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Spear phishing attack with mitigation strategies and its example. It also includes mitigation strategies such as email filtering, Multi-factor authentication MFA and network segmentation.Increase audience engagement and knowledge by dispensing information using Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Presidential Election using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the SQL injection attack with mitigation strategies and example. It also includes mitigation strategies such as parameterized SQL statements, install a WAF and restrict the database users privileges.Introducing SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, Seize System Control, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS. This template helps you present information on eight stages. You can also present information on Motivations And Goals, Cyberterrorist Actors, Conclusion, Future Trends using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIntroducing Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Intelligence Agencies, Cyber Security Initiatives, International Agreements, using this template. Grab it now to reap its full benefits.
-
 Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SS
Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SSThis slide showcases the Techniques to prevent employee personal accounts. It includes strategies such as education and training, device security, two-factor authentication 2FA and secure Wi-Fi and networks.Increase audience engagement and knowledge by dispensing information using Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Device Security, Education And Training, Two Factor Authentication, Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Thrill Seekers In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SS
Thrill Seekers In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SSThis slide showcases an overview of thrill seekers. It includes its characteristics and activities such as motivation, intent, skill and knowledge, targets and impact.Introducing Thrill Seekers In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Motivation, Intent, Skill And Knowledge, Targets, Impact, using this template. Grab it now to reap its full benefits.
-
 Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS
Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SSThis slide showcases the Train employees on cyber attack prevention. It includes techniques such as email impersonation, vigilance in clicking links, verification of email addresses and use of common sense.Present the topic in a bit more detail with this Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Threat Scenario, Description, Employee Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Trojan horses attack with mitigation strategies and example. It includes mitigation strategies such as use updated version of antivirus and regular updates of operating systems.Introducing Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, using this template. Grab it now to reap its full benefits.
-
 United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS
United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SSThis slide showcases the United nations and cyber security initiatives. It includes initiatives such as UN general assembly resolutions, UNODA, UNIDIR, CTC and UNODC.Increase audience engagement and knowledge by dispensing information using United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS. This template helps you present information on five stages. You can also present information on General Assembly Resolutions, Disarmament Affairs, Disarmament Research using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 User Based Security Training Model Strategic Guide To Implement Strategy SS
User Based Security Training Model Strategic Guide To Implement Strategy SSIntroducing User Based Security Training Model Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Compromised System, Compromised Network, Critical Assets, Exfiltrate Sensitive Data, using this template. Grab it now to reap its full benefits.
-
 Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Whale phishing attack with mitigation strategies and its example. It includes mitigation strategies such as email filtering, Multi-factor authentication MFA and updates and patching.Increase audience engagement and knowledge by dispensing information using Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Mitigation Strategies, Description, Example, Email Filtering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS
Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SSThis slide showcases the Wi-Fi security to protect network and connected devices. It includes strategies such as strong passwords, encryption, firewall and intrusion detection systems IDS and two-factor authentication 2FA.Introducing Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two Factor Authentication, Intrusion Detection Systems, Encryption, Strong Passwords, using this template. Grab it now to reap its full benefits.
-
 XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the XSS attack with mitigation strategies and example. It includes mitigation strategies such as content security policy and web application firewalls.Increase audience engagement and knowledge by dispensing information using XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Content Security Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Steps Customize The Account Cont Crm System Implementation Guide For Businesses
Implementation Steps Customize The Account Cont Crm System Implementation Guide For BusinessesThis slide covers various steps for customizing a CRM account. It includes action steps such as creating layouts and editing field properties. Present the topic in a bit more detail with this Implementation Steps Customize The Account Cont Crm System Implementation Guide For Businesses. Use it as a tool for discussion and navigation on Implementation, Customize, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Sales Strategies Implemented By Companies A Comprehensive Guide MKT SS V
Major Sales Strategies Implemented By Companies A Comprehensive Guide MKT SS VThis slide covers effective sales strategies commonly used by brands. The mentioned strategies are urgency strategy, sales, and discounts, feature benefit selling, value added strategy, niche market, word of mouth, social selling, customer centric selling, and giveaways. Present the topic in a bit more detail with this Major Sales Strategies Implemented By Companies A Comprehensive Guide MKT SS V. Use it as a tool for discussion and navigation on Survey Details Conducted, Commonly Used Sales Strategies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement processes powerpoint guide
Implement processes powerpoint guidePresenting implement processes powerpoint guide. This is a implement processes powerpoint guide. This is a six stage process. The stages in this process are improve processes, implement processes, analysis business processes, monitor and check processes, design and model processes, planning and process strategy.
-
 Implementation marketing diagram powerpoint guide
Implementation marketing diagram powerpoint guidePresenting implementation marketing diagram powerpoint guide. This is a implementation marketing diagram powerpoint guide. This is a four stage process. The stages in this process are immediate, low priority, don?t bother, longer term.
-
 Crm Software Deployment Guide Post Implementation Impacts On Company Sales
Crm Software Deployment Guide Post Implementation Impacts On Company SalesThis slide covers the forecasted impacts of deploying CRM systems in the organization. It includes outcomes such as increase in sales, increases in sales team productivity, increased rates of customer retention and satisfaction, return on investment, and shortened sales cycle. Deliver an outstanding presentation on the topic using this Crm Software Deployment Guide Post Implementation Impacts On Company Sales. Dispense information and present a thorough explanation of Accessibility, Implementation, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Post Implementation Impacts On Business Aspects Crm Software Deployment Guide
Post Implementation Impacts On Business Aspects Crm Software Deployment GuideThis slide covers major improvements after CRM software implementation. It includes major impact on areas such as customer retention, customer satisfaction, sales revenue, and upselling or cross-selling. Deliver an outstanding presentation on the topic using this Post Implementation Impacts On Business Aspects Crm Software Deployment Guide. Dispense information and present a thorough explanation of Implementation, Business, Improvements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cost Reduction Post Cdn Implementation Delivery Network Ppt Slides Guide
Cost Reduction Post Cdn Implementation Delivery Network Ppt Slides GuideThis slide demonstrates the graph about how bandwidth costs are reduced by 99 percent after the implementation of the content delivery network. Deliver an outstanding presentation on the topic using this Cost Reduction Post Cdn Implementation Delivery Network Ppt Slides Guide. Dispense information and present a thorough explanation of Implementation, Reduction, Demonstrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





