Powerpoint Templates and Google slides for Generating Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Internet Gateway Security IT Introduction To Next Generation Secure Web
Internet Gateway Security IT Introduction To Next Generation Secure WebThis slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Introducing Internet Gateway Security IT Introduction To Next Generation Secure Web to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Applications, Services, Risks Enabled, Vulnerability, Public Resources, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Growth Drivers Of Next Generation
Internet Gateway Security IT Key Growth Drivers Of Next GenerationThis slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Introducing Internet Gateway Security IT Key Growth Drivers Of Next Generation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Growing Cloud Applications, Services, Rising Data Theft And Vulnerability, Cloud Dominated World, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Steps To Select Next Generation Secure Web
Internet Gateway Security IT Steps To Select Next Generation Secure WebThis slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Introducing Internet Gateway Security IT Steps To Select Next Generation Secure Web to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Adopt Real Cloud Architecture, Decodes Apps And Cloud Services, Adapts To New Threats, using this template. Grab it now to reap its full benefits.
-
 Conventional CASB Vs Next Generation CASB Cloud Security
Conventional CASB Vs Next Generation CASB Cloud SecurityThis slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Deliver an outstanding presentation on the topic using this Conventional CASB Vs Next Generation CASB Cloud Security. Dispense information and present a thorough explanation of Integration Approach, Management Complexity, Deployment Flexibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E Payment
Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E PaymentFollowing slide showcases comparative analysis of multiple code generators whose services can be leveraged by businesses to design customized QR code. It includes key attributes such as Deliver an outstanding presentation on the topic using this Comparative Assessment Of QR Code Generating Professionals Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Attributes, QR Code Generator Pro, Flow Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reference Architecture For Next Generation Cyber Security Framework
Reference Architecture For Next Generation Cyber Security FrameworkThis slide illustrates the reference architecture for next generation cyber security framework which includes identity management, user interface, etc. Deliver an outstanding presentation on the topic using this Reference Architecture For Next Generation Cyber Security Framework. Dispense information and present a thorough explanation of Reference Architecture, Cyber Security Framework, Identity Management, Context Repository using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ChatGPT For Streamlining And Improving Security Communications Impact Of Generative AI SS V
ChatGPT For Streamlining And Improving Security Communications Impact Of Generative AI SS VThis slide showcases overview of ChatGPT for streamlining and optimizing the security operations in organizations. Its key elements are cybersecurity training, enhanced communication during attack, developing policies and reporting after attack. Increase audience engagement and knowledge by dispensing information using ChatGPT For Streamlining And Improving Security Communications Impact Of Generative AI SS V. This template helps you present information on four stages. You can also present information on Cybersecurity Training, Enhanced Communication, Reporting After Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ChatGPT Use Cases For Streamlining Security Operations Impact Of Generative AI SS V
ChatGPT Use Cases For Streamlining Security Operations Impact Of Generative AI SS VThis slide showcases various ChatGPT use cases for streamlining and automating the cybersecurity operations of organization. Its key elements are establish security policies, automate repetitive tasks and identification of vulnerabilities. Increase audience engagement and knowledge by dispensing information using ChatGPT Use Cases For Streamlining Security Operations Impact Of Generative AI SS V. This template helps you present information on three stages. You can also present information on Establish Security, Automate Repetitive Tasks, Identify Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Limitations Of Leveraging ChatGPT For Security Operations Impact Of Generative AI SS V
Limitations Of Leveraging ChatGPT For Security Operations Impact Of Generative AI SS VThis slide showcases various disadvantages of leveraging ChatGPT for security operations. Its key elements are information inaccuracy, over-reliance on automation, input misinterpretation, output bias and confidentially concerns. Increase audience engagement and knowledge by dispensing information using Limitations Of Leveraging ChatGPT For Security Operations Impact Of Generative AI SS V. This template helps you present information on five stages. You can also present information on Information Inaccuracy, Input Misinterpretation, Confidentiality Concerns using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Importance Of Streamlining Security Operations Impact Of Generative AI SS V
Overview And Importance Of Streamlining Security Operations Impact Of Generative AI SS VThis slide showcases overview of streamlining security operations which can help organization to prevent cyber attacks in organization. It also highlight various benefits of streamlining security operations such as timely incident response, vulnerability assessment, reduction in cyber attacks etc. Increase audience engagement and knowledge by dispensing information using Overview And Importance Of Streamlining Security Operations Impact Of Generative AI SS V. This template helps you present information on four stages. You can also present information on Organization Infrastructure, Cyber Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Generate SIEM Cyber Security Project
Steps To Generate SIEM Cyber Security ProjectThis slide showcases the steps to curate SIEM cyber security project. Its purpose is to understand the critical threats. This slide includes determining business data source, priority alerts and success metrics. Introducing our premium set of slides with name Steps To Generate SIEM Cyber Security Project. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Make Event, Data Insightful, Determine Business Critical. So download instantly and tailor it with your information.
-
 Generic Database Architecture Of Mobile Security Mobile Security
Generic Database Architecture Of Mobile Security Mobile SecurityThis slide illustrates the key database architecture of mobile security which include mobile worker, internet, mobile server, firewall and database server. Present the topic in a bit more detail with this Generic Database Architecture Of Mobile Security Mobile Security Use it as a tool for discussion and navigation on Logical Device Access, Mobile Functions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Building Next Generation Endpoint Security Cybersecurity SS
Agenda Building Next Generation Endpoint Security Cybersecurity SSIntroducing Agenda Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Cyberattacks, Enhanced Security, Key Organizational Kpis, using this template. Grab it now to reap its full benefits.
-
 Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS
Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SSDeliver an outstanding presentation on the topic using this Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Process, Output, Input using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building Next Generation Endpoint Security Table Of Contents Cybersecurity SS
Building Next Generation Endpoint Security Table Of Contents Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Building Next Generation Endpoint Security Table Of Contents Cybersecurity SS. This template helps you present information on one stages. You can also present information on Antivirus Enhancement, Smart Endpoint Application Control, Least Privilege Approach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases gap analysis which can help companies realize their need assessment position by calculating current and desired state, assisting them plan action items. Present the topic in a bit more detail with this Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Parameters, Current State, Impact, Importance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Multiple Edr Tools Building Next Generation Endpoint Security Cybersecurity SS
Comparative Analysis Of Multiple Edr Tools Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases comparative assessment of various endpoint detection and response EDR tools. It provides details about multi level views, forensics breakdown, ransomware detection, etc.Deliver an outstanding presentation on the topic using this Comparative Analysis Of Multiple Edr Tools Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Product, Features, Pricing, Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases comparative analysis for endpoint security tools. It provides details about endpoint firewall, compatibility, data loss prevention, regulatory compliance, etc.Present the topic in a bit more detail with this Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Regulatory Compliance, Data Loss Prevention, Endpoint Firewall. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Crucial Ways To Avoid Malicious Code Building Next Generation Endpoint Security Cybersecurity SS
Crucial Ways To Avoid Malicious Code Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases major ways to prevent malicious code infections. This can help developers avoid attacks from public networks, verify sources and avoid harmless links code.Introducing Crucial Ways To Avoid Malicious Code Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Public Networks, Legitimacy Of Sources, Harmless Links, using this template. Grab it now to reap its full benefits.
-
 Current Challenges With Traditional Endpoint Building Next Generation Endpoint Security Cybersecurity SS
Current Challenges With Traditional Endpoint Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases current scenario of roadblocks faced by business w.r.t traditional endpoint security. It includes challenges such as false positives, privileges, anti-virus, etc.Increase audience engagement and knowledge by dispensing information using Current Challenges With Traditional Endpoint Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information on six stages. You can also present information on Modern Attacks Missed, Challenges, Vulnerabilities Highlighted using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS
Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SSPresent the topic in a bit more detail with this Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Management, Contact Distribution, Endpoint Protection Clients. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS
Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases deploying endpoint detection and response EDR for advanced threat protection. It provides details about alert triage, containment, incident data search, etc.Deliver an outstanding presentation on the topic using this Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Advanced Threat Detection, Incident Data Search, Alert Triage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Deploying Enhanced Anti Virus For Endpoint Building Next Generation Endpoint Security Cybersecurity SS
Deploying Enhanced Anti Virus For Endpoint Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases enhanced antivirus platform for endpoint security. It includes details about attack surface reduction, centralized configuration, zero-day attacks, etc.Present the topic in a bit more detail with this Deploying Enhanced Anti Virus For Endpoint Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Our Platform Capabilities, Potential Impact, Centralized Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Cyber Security General Overview Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Cyber Security General Overview Building Next Generation Endpoint Security Cybersecurity SSIntroducing Endpoint Cyber Security General Overview Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Computer Viruses, Smartphones And Tablets, Servers, using this template. Grab it now to reap its full benefits.
-
 Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint data loss prevention DLP tool process. It includes stages such as identification, assistance and tracking of endpoint data.Increase audience engagement and knowledge by dispensing information using Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information three stages. You can also present information on Identify, Assist, Track, Potential Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Least Privilege Approach Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Least Privilege Approach Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases least privilege approach for endpoint security. It includes steps such as granular access control, regular access reviews, whitelisting, etc.Introducing Endpoint Security Least Privilege Approach Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Granular Access Control, Regular Access Reviews, App Control And Whitelisting, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SSIntroducing Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Gather Information, Choose Security Solutions, Implement Chosen Solutions, using this template. Grab it now to reap its full benefits.
-
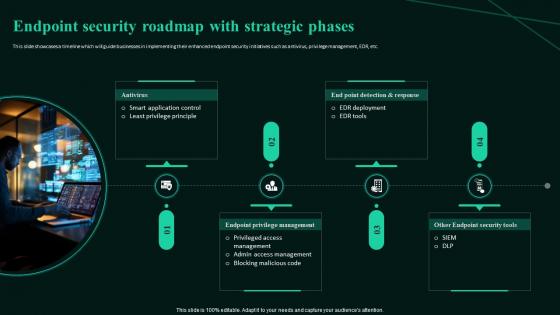 Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases a timeline which will guide businesses in implementing their enhanced endpoint security initiatives such as antivirus, privilege management, EDR, etc.Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information on one stages. You can also present information on Other Endpoint Security Tools, Endpoint Privilege Management, Antivirus, End Point Detection And Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Team Training Plan Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Team Training Plan Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security team training plan. It provides details about endpoint detection and response, network security, applied threat hunting, etc.Present the topic in a bit more detail with this Endpoint Security Team Training Plan Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Training Provider, Duration, Modules, Sessions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SS
Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint privilege management for maximum security. It includes details about admin rights, application privileges, just in time access, etcIntroducing Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Current Scenario, Remedial Solutions, Potential Impact, using this template. Grab it now to reap its full benefits.
-
 Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS
Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases how to establish privilege access management process. It provides details about prepare, protect, operate, monitor, etc.Present the topic in a bit more detail with this Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Prepare, Protect, Operate, Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Building Next Generation Endpoint Security Cybersecurity SS
Icons Slide For Building Next Generation Endpoint Security Cybersecurity SSPresenting our premium Icons Slide For Building Next Generation Endpoint Security Cybersecurity SS set of slides with flexible icons. The icons are designed by our group of professionals. Add these XXXXXXXXXXXXXXXXXXXX to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
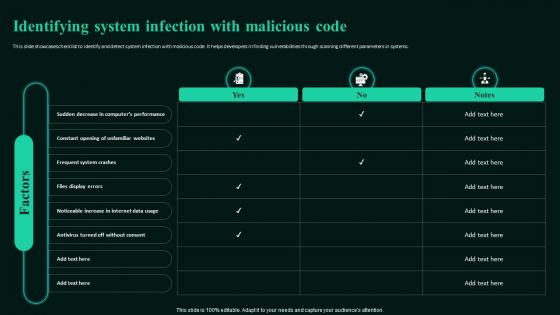 Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS
Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases checklist to identify and detect system infection with malicious code. It helps developers in finding vulnerabilities through scanning different parameters in systems.Deliver an outstanding presentation on the topic using this Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Frequent System Crashes, Files Display Errors, Unfamiliar Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Analysis Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Impact Analysis Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases current scenario of improvements w.r.t traditional endpoint security. It includes details such as false positives, privileges, anti-virus, etc.Introducing Impact Analysis Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Improvements, Vulnerabilities Solved, Modern Attacks Missed, using this template. Grab it now to reap its full benefits.
-
 Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for avoiding accidental misuses. It provides details about security controls, data discovery, etc.Deliver an outstanding presentation on the topic using this Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Action Steps, Real Problem Solved, Layering Security Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for segregation of duties. It provides details about time limits, certain access, etc.Introducing Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Action Steps, Real Problem Solved, Financial Data, using this template. Grab it now to reap its full benefits.
-
 Mitigation Plan For Malicious Code Protection Building Next Generation Endpoint Security Cybersecurity SS
Mitigation Plan For Malicious Code Protection Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases mitigation plan for protection against malicious code. It can help detect malware, adware, etc. and plan action items accordingly.Present the topic in a bit more detail with this Mitigation Plan For Malicious Code Protection Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Malware Infection, Unauthorized Access, Adware Intrusion, Phishing Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security team responsible, accountable, consulted and informed RACI matrix. It provides details about endpoint detection and response, network security, etc.Deliver an outstanding presentation on the topic using this Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Monitor Security, Identity Strategic Risk, Perform Business Impact Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Removing Admin Rights For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Removing Admin Rights For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases process to remove admin rights for increased endpoint security. It includes details about discover, analyze, remediate, etc. Introducing Removing Admin Rights For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Analyze, Remediate, Discover, Improves Risk Mitigation, using this template. Grab it now to reap its full benefits.
-
 Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS
Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases security information and event management SIEM tools which can help endpoint security teams detect and address potential security threats.Present the topic in a bit more detail with this Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Collection, Detection, Investigation, Response. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SS
Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases smart endpoint app control process. It can help developers reduce attacks through blocklist rules, risk assessment, recommendation engine, etc.Deliver an outstanding presentation on the topic using this Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Symantec Application Control, Symantec Application Control, Recommendation Engine using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Building Next Generation Endpoint Security Cybersecurity SS
Table Of Contents Building Next Generation Endpoint Security Cybersecurity SSIntroducing Table Of Contents Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Security Strategies, Endpoint Security Team, Current Endpoint Security Scenario, using this template. Grab it now to reap its full benefits.
-
 Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS
Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SSPresent the topic in a bit more detail with this Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Mobile Threat Defense, Endpoint Protection Platform, Advanced Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS V
A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Present the topic in a bit more detail with this A211 ChatGPT Next Generation AI Integrating ChatGPT With Other Systems Security ChatGPT SS V. Use it as a tool for discussion and navigation on Fraud Detection, Compliance Tracking, Cybersecurity, Risk Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Column Chart Generating Security Awareness Among Employees To Reduce
Column Chart Generating Security Awareness Among Employees To ReduceDeliver an outstanding presentation on the topic using this Column Chart Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Column Chart using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attack Incident Generating Security Awareness Among Employees To Reduce
Cyber Attack Incident Generating Security Awareness Among Employees To ReduceThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Generating Security Awareness Among Employees To Reduce Use it as a tool for discussion and navigation on Infected Hosts, Prevented Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Generating Security Awareness Among Employees To Reduce
Data Breach Trend Generating Security Awareness Among Employees To ReduceThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Deliver an outstanding presentation on the topic using this Data Breach Trend Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Data Breach Trend, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Generating Security Awareness Among Employees To Reduce
Information Technology Generating Security Awareness Among Employees To ReduceThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Present the topic in a bit more detail with this Information Technology Generating Security Awareness Among Employees To Reduce Use it as a tool for discussion and navigation on Cyber Security, Budget Spent This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Generating Security Awareness Among Employees To Reduce
Major Causes Of Cyber Generating Security Awareness Among Employees To ReduceThe following slide highlights the key reasons of cyber attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Generating Security Awareness Among Employees To Reduce Use it as a tool for discussion and navigation on Unawareness Among, Security Trainings This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Generation internet security controls ppt powerpoint presentation outline grid cpb
Generation internet security controls ppt powerpoint presentation outline grid cpbPresenting our Generation Internet Security Controls Ppt Powerpoint Presentation Outline Grid Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Generation Internet Security Controls. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 General Outlook Of Ransomware Attack Building A Security Awareness Program
General Outlook Of Ransomware Attack Building A Security Awareness ProgramThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Deliver an outstanding presentation on the topic using this General Outlook Of Ransomware Attack Building A Security Awareness Program. Dispense information and present a thorough explanation of Programme, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 What Security Features Does 5G 5th Generation Evolution Of Wireless Telecommunication
What Security Features Does 5G 5th Generation Evolution Of Wireless TelecommunicationThis slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Increase audience engagement and knowledge by dispensing information using What Security Features Does 5G 5th Generation Evolution Of Wireless Telecommunication. This template helps you present information on eight stages. You can also present information on Component Individually, Technology Include using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For Staff
General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For StaffThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Introducing General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For Staff to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Files Are Encrypted, Ransomware Works, General Outlook, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Security Breach General Consequences Developing Cyber Security Awareness Training
Impact Of Cyber Security Breach General Consequences Developing Cyber Security Awareness TrainingThe purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Introducing Impact Of Cyber Security Breach General Consequences Developing Cyber Security Awareness Training to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reputational Damage, Operational Disruption, Monetary Penalty, Theft Events, using this template. Grab it now to reap its full benefits.
-
 Conducting Security Awareness Impact Of Cyber Security Breach General Consequences
Conducting Security Awareness Impact Of Cyber Security Breach General ConsequencesThe purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetxary penalty and operational disruption. Introducing Conducting Security Awareness Impact Of Cyber Security Breach General Consequences to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reputational Damage, Operational Disruption, Monetary Penalty, Theft Events, using this template. Grab it now to reap its full benefits.
-
 General Outlook Of Ransomware Attack Conducting Security Awareness
General Outlook Of Ransomware Attack Conducting Security AwarenessThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Introducing General Outlook Of Ransomware Attack Conducting Security Awareness to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Decrypt Data, Employees System, Time Left, using this template. Grab it now to reap its full benefits.
-
 Cps Security And Privacy Life Cycle Next Generation Computing Systems Ppt Show Graphics Design
Cps Security And Privacy Life Cycle Next Generation Computing Systems Ppt Show Graphics DesignThis slide depicts the cyber-physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Present the topic in a bit more detail with this Cps Security And Privacy Life Cycle Next Generation Computing Systems Ppt Show Graphics Design. Use it as a tool for discussion and navigation on Performance, Operational, Capability . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
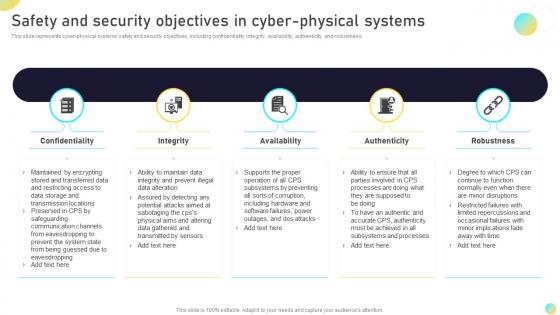 Safety And Security Objectives In Cyber Physical Systems Next Generation Computing Systems
Safety And Security Objectives In Cyber Physical Systems Next Generation Computing SystemsThis slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present the topic in a bit more detail with this Safety And Security Objectives In Cyber Physical Systems Next Generation Computing Systems. Use it as a tool for discussion and navigation on Confidentiality, Availability, Authenticity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Strategic Planning Process For Cps Next Generation Computing Systems
Security Strategic Planning Process For Cps Next Generation Computing SystemsThis slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Present the topic in a bit more detail with this Security Strategic Planning Process For Cps Next Generation Computing Systems. Use it as a tool for discussion and navigation on Strategic, Planning, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps For Cps Security Strategy Plan Next Generation Computing Systems Ppt Show Design Inspiration
Steps For Cps Security Strategy Plan Next Generation Computing Systems Ppt Show Design InspirationThis slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Present the topic in a bit more detail with this Steps For Cps Security Strategy Plan Next Generation Computing Systems Ppt Show Design Inspiration. Use it as a tool for discussion and navigation on Communicate, Implementation, Continuous Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.





