Powerpoint Templates and Google slides for Encryptions
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 File Encryption Sharing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
File Encryption Sharing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is perfect for representing File Sharing. It features a folder with an arrow pointing to the right, symbolizing the sharing of files from one device to another. It is simple, yet effective and can be used in any presentation.
-
 Password Security Authentication Encryption Illustration
Password Security Authentication Encryption IllustrationThis coloured powerpoint icon is a visual representation of password security. It features a padlock with a keyhole, a shield, and a key. It is perfect for illustrating the importance of secure passwords in presentations.
-
 Confidential Computing Hardware What Is Fully Homomorphic Encryption FHE
Confidential Computing Hardware What Is Fully Homomorphic Encryption FHEThis slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Introducing Confidential Computing Hardware What Is Fully Homomorphic Encryption FHE to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Fully Homomorphic Encryption, Strict Regulatory Compliance, Enhanced Cloud Security, using this template. Grab it now to reap its full benefits.
-
 Encryption Scan WIFI Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Scan WIFI Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for presentations and displays. It features a modern, sleek design and is available in a range of vibrant colours. It is easy to use and adds a professional touch to your work.
-
 Encryption Scan WIFI Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Scan WIFI Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon on Scan WIFI is a simple yet effective way to add a professional look to your presentation. It is easy to customize and can be used to illustrate any concept related to scanning a wireless network. It is an ideal choice for any business or educational presentation.
-
 Digital Signature Encryptions Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Digital Signature Encryptions Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for illustrating the concept of digital signature. It is a high-resolution, vector-based graphic with a vibrant and eye-catching colour palette. It is an ideal choice for presentations, infographics, and other visuals.
-
 Digital Signature Encryptions Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Digital Signature Encryptions Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Digital Signature is a modern and stylish way to represent the concept of digital signature. It is a simple yet powerful graphic that will add a professional touch to any presentation. It is easy to customize and can be used for a variety of purposes.
-
 Data Security Encryption Technology Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Encryption Technology Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Data Security Encryption Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Encryption Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Encryption Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon features a broken shield with a distressed texture. It is perfect for conveying a sense of vulnerability, fragility, or failure in presentations. It is available in a range of vibrant colours and can be used to highlight key points or draw attention to important concepts.
-
 Encryption Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint icon depicts a broken shield, representing a lack of protection or security. It is perfect for conveying a sense of vulnerability, fragility, or danger in presentations. It can also be used to illustrate a lack of trust or loyalty.
-
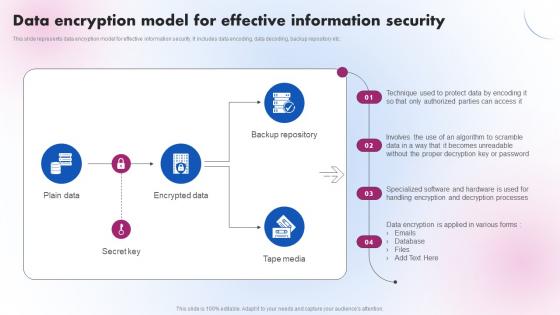 Data Encryption Model For Effective Information Delivering ICT Services For Enhanced Business Strategy SS V
Data Encryption Model For Effective Information Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Introducing Data Encryption Model For Effective Information Delivering ICT Services For Enhanced Business Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authorized Parties, Proper Decryption, Decryption Processes, using this template. Grab it now to reap its full benefits.
-
 Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V
Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Consortium What Is Fully Homomorphic Encryption FHE
Confidential Computing Consortium What Is Fully Homomorphic Encryption FHEThis slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Increase audience engagement and knowledge by dispensing information using Confidential Computing Consortium What Is Fully Homomorphic Encryption FHE. This template helps you present information on three stages. You can also present information on Strict Regulatory Compliance, Enhanced Cloud Security, Execute Data Computation, Encrypted Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cryptography Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cryptography Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Cryptography Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cryptography Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Data Encryption Key Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Key Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Data Encryption Key Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Key Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Digital Signatures Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Digital Signatures Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Digital Signatures Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Digital Signatures Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Encryption Algorithms Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Algorithms Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Encryption Algorithms Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Algorithms Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Identity Management Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Identity Management Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Identity Management Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Identity Management Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Encryption Code Decoder Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Code Decoder Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis powerpoint icon is a vibrant, multi coloured symbol that conveys the idea of decoding and problem solving. It is perfect for presentations, websites and other digital projects that require a modern, eye catching icon. The icon is available in a variety of colours and sizes, making it easy to customise to your projects needs.
-
 Encryption Code Decoder Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Code Decoder Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone Powerpoint Icon is a perfect choice for presentations. It is a professional looking icon that is easy to use and customize. It can be used to create a modern and stylish look for any presentation. It is also available in different sizes and colors to suit your needs.
-
 Encryption Techniques Icon For Securing Big Data Analytics
Encryption Techniques Icon For Securing Big Data AnalyticsIntroducing our Encryption Techniques Icon For Securing Big Data Analytics set of slides. The topics discussed in these slides are Encryption Techniques, Securing Big Data Analytics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Types Of Encryption For Securing Big Data Analytics
Types Of Encryption For Securing Big Data AnalyticsThis slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum proof encryption, homomorphic encryption, etc. Introducing our premium set of slides with Types Of Encryption For Securing Big Data Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Homomorphic Encryption, Differential Privacy. So download instantly and tailor it with your information.
-
 Agenda Cloud Data Encryption Implementation Plan
Agenda Cloud Data Encryption Implementation PlanIntroducing Agenda Cloud Data Encryption Implementation Plan to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Represent Challenges, Performance Analysis, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Cloud Data Encryption Implementation Cloud Data Encryption
Before Vs After Cloud Data Encryption Implementation Cloud Data EncryptionThis slide compares the scenario after integrating encryption protocols in organizational networks. The purpose of this slide is to represent before and after situations based on several parameters. The factors used to make the comparison are unauthorized access, data breaches, etc. Present the topic in a bit more detail with this Before Vs After Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Unauthorized Access, Data Breaches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget Summary For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Budget Summary For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide represents the budget for securing cloud data using encryption techniques. The purpose of this slide is to showcase the estimated and actual cost of implementing cloud data encryption. The components include hardware and software, maintenance and support, training, etc. Present the topic in a bit more detail with this Budget Summary For Cloud Data Encryption Implementation Plan Cloud Data Encryption. Use it as a tool for discussion and navigation on Maintenance And Support, Hardware And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Implement Cloud Data Encryption In Organization Cloud Data Encryption
Checklist To Implement Cloud Data Encryption In Organization Cloud Data EncryptionThis slide represents the checklist for integrating cloud encryption into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Deliver an outstanding presentation on the topic using this Checklist To Implement Cloud Data Encryption In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Key Approaches, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Client Side Encryption To Protect Cloud Data Cloud Data Encryption
Client Side Encryption To Protect Cloud Data Cloud Data EncryptionThis slide discusses client side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc. Introducing Client Side Encryption To Protect Cloud Data Cloud Data Encryption to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Following Scenarios, Encrypted, using this template. Grab it now to reap its full benefits.
-
 Client Side Encryption Using Cryptomator Software Cloud Data Encryption
Client Side Encryption Using Cryptomator Software Cloud Data EncryptionThis slide discusses the Cryptomator software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with Cryptomator software, such as downloading and installing, using the password to view the encrypted files, etc. Increase audience engagement and knowledge by dispensing information using Client Side Encryption Using Cryptomator Software Cloud Data Encryption. This template helps you present information on one stages. You can also present information on Rapidly Encrypt, Online Storage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Client Side Encryption Using Nordlocker Software Cloud Data Encryption
Client Side Encryption Using Nordlocker Software Cloud Data EncryptionThis slide discusses the NordLocker software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with NordLocker software, such as downloading and installing, creating a password, using the password to view the encrypted files, etc. Introducing Client Side Encryption Using Nordlocker Software Cloud Data Encryption to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Download And Install, Create The Master, using this template. Grab it now to reap its full benefits.
-
 Client Side Encryption With Customer Managed Keys Cloud Data Encryption
Client Side Encryption With Customer Managed Keys Cloud Data EncryptionThis slide shows the client side encryption and decryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encrypted data key, etc. Present the topic in a bit more detail with this Client Side Encryption With Customer Managed Keys Cloud Data Encryption. Use it as a tool for discussion and navigation on Encrypted Object Data, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Data Encryption Implementation Plan Table Of Contents
Cloud Data Encryption Implementation Plan Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Cloud Data Encryption Implementation Plan Table Of Contents. This template helps you present information on one stages. You can also present information on Key Challenges, Cloud Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Data Encryption Service Providers Cloud Data Encryption
Cloud Data Encryption Service Providers Cloud Data EncryptionThis slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Present the topic in a bit more detail with this Cloud Data Encryption Service Providers Cloud Data Encryption. Use it as a tool for discussion and navigation on Providers, Reason For Selecting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data Encryption
Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data EncryptionThis slide outlines several cloud storage providers with in built zero knowledge encryption. The key points include name, storage provided in a free plan, cost of the monthly subscription plan, and advantages and disadvantages of the service provider. Deliver an outstanding presentation on the topic using this Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data Encryption. Dispense information and present a thorough explanation of Storage Provided Free Plan, Cost Of Monthly Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparison Between Cryptomator And Nordlocker Software Cloud Data Encryption
Comparison Between Cryptomator And Nordlocker Software Cloud Data EncryptionThis slide compares the two popular encryption software, named Cryptomator and NordLocker. The comparison is carried out based on several factors, such as encryption method, client side encryption, platforms supported, user interface, pricing, etc. Present the topic in a bit more detail with this Comparison Between Cryptomator And Nordlocker Software Cloud Data Encryption. Use it as a tool for discussion and navigation on Cryptomator, Nordlocker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Between Server-Side And Client Side Encryption Cloud Data Encryption
Comparison Between Server-Side And Client Side Encryption Cloud Data EncryptionThe purpose of this slide is to compare client side and server side encryption procedures. The comparison is carried out based on several factors, such as encryption performed, key management, data privacy, complexity, collaboration, performance overhead, etc. Deliver an outstanding presentation on the topic using this Comparison Between Server Side And Client Side Encryption Cloud Data Encryption. Dispense information and present a thorough explanation of Encryption Performed, Key Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Considerations For Zero Knowledge Encryption Service Selection Cloud Data Encryption
Considerations For Zero Knowledge Encryption Service Selection Cloud Data EncryptionThe purpose of this slide is to highlight the several factors to be considered while selecting zero knowledge encryption service providers. The main discussed factors are storage space, privacy and security, price, and other perks. Present the topic in a bit more detail with this Considerations For Zero Knowledge Encryption Service Selection Cloud Data Encryption. Use it as a tool for discussion and navigation on Storage Space, Privacy And Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Stages Of Cloud Data Encryption Implementation Cloud Data Encryption
Different Stages Of Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the different steps involved in the cloud data encryption implementation process. These stages discussed in this slide are client side encryption or zero knowledge encryption, in transit encryption, and server side encryption. Increase audience engagement and knowledge by dispensing information using Different Stages Of Cloud Data Encryption Implementation Cloud Data Encryption. This template helps you present information on three stages. You can also present information on Encryption Performed, Service Provider using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Estimated Budget Of Cloud Data Encryption Implementation Cloud Data Encryption
Estimated Budget Of Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the budget for integrating cloud encryption in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. Present the topic in a bit more detail with this Estimated Budget Of Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Services, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Existing Cloud Data Infrastructure Constituents Cloud Data Encryption
Existing Cloud Data Infrastructure Constituents Cloud Data EncryptionThis slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc. Deliver an outstanding presentation on the topic using this Existing Cloud Data Infrastructure Constituents Cloud Data Encryption. Dispense information and present a thorough explanation of Cloud Storage, Cloud Databases using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide Cloud Data Encryption Implementation Plan
Icons Slide Cloud Data Encryption Implementation PlanIntroducing our well researched set of slides titled Icons Slide Cloud Data Encryption Implementation Plan. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption
Impact Of Encryption Implementation On Cloud Security Cloud Data EncryptionThis slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data Encryption
Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data EncryptionThis slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. Present the topic in a bit more detail with this Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data Encryption. Use it as a tool for discussion and navigation on Data Security Concerns, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data Encryption
Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data EncryptionThe purpose of this slide is to discuss the challenges faced while encrypting cloud data. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies. Deliver an outstanding presentation on the topic using this Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data Encryption. Dispense information and present a thorough explanation of Probability, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Performance Analysis Of Existing Cloud Network Cloud Data Encryption
Performance Analysis Of Existing Cloud Network Cloud Data EncryptionThe purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Present the topic in a bit more detail with this Performance Analysis Of Existing Cloud Network Cloud Data Encryption. Use it as a tool for discussion and navigation on Where We Are, Where We Want To Be. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Project Summary For Cloud Data Encryption Implementation Cloud Data Encryption
Project Summary For Cloud Data Encryption Implementation Cloud Data EncryptionThe purpose of this slide is to represent the summary of the cloud data encryption implementation project providing information regarding problems faced, recommended solution, estimated project cost, and estimated timeline. Deliver an outstanding presentation on the topic using this Project Summary For Cloud Data Encryption Implementation Cloud Data Encryption. Dispense information and present a thorough explanation of Problem, Solution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide shows the matrix to assign multiple responsibilities to the different team members for the cloud data encryption implementation project. The responsibilities include problem assessment, solution selection, encryption implementation, etc. Present the topic in a bit more detail with this Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data Encryption. Use it as a tool for discussion and navigation on Problem Assessment, Solution Selection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
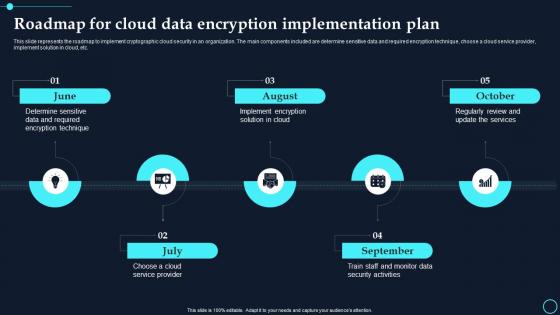 Roadmap For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Roadmap For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc.Increase audience engagement and knowledge by dispensing information using Roadmap For Cloud Data Encryption Implementation Plan Cloud Data Encryption. This template helps you present information on five stages. You can also present information on August, October using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Server Side Encryption To Protect Cloud Data Cloud Data Encryption
Server Side Encryption To Protect Cloud Data Cloud Data EncryptionThis slide discusses server side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc. Present the topic in a bit more detail with this Server Side Encryption To Protect Cloud Data Cloud Data Encryption. Use it as a tool for discussion and navigation on Readable, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Server Side Encryption With Customer Managed Keys Cloud Data Encryption
Server Side Encryption With Customer Managed Keys Cloud Data EncryptionThis slide demonstrates the server side encryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encryption, decryption, etc. Deliver an outstanding presentation on the topic using this Server Side Encryption With Customer Managed Keys Cloud Data Encryption. Dispense information and present a thorough explanation of Customer Key, Encryption Algorithm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Service Comparison Of Zero Knowledge Encryption Providers Cloud Data Encryption
Service Comparison Of Zero Knowledge Encryption Providers Cloud Data EncryptionThis slide highlights the availability of various services in different zero knowledge encryption providers to encrypt the data stored in the cloud. The significant services mentioned in this slide are sync folder, file link sharing, folder sharing, and versioning. Deliver an outstanding presentation on the topic using this Service Comparison Of Zero Knowledge Encryption Providers Cloud Data Encryption. Dispense information and present a thorough explanation of Service Provider, Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setup And Retrieval Process For Key Distribution Cloud Data Encryption
Setup And Retrieval Process For Key Distribution Cloud Data EncryptionThis slide represents the key management process for encrypted cloud storage. The components included are the setup process, cloud server, retrieval process, data users, key distribution, data owner, query expansion, search query, central index, etc. Present the topic in a bit more detail with this Setup And Retrieval Process For Key Distribution Cloud Data Encryption. Use it as a tool for discussion and navigation on Mandatory Process, Optional Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Cloud Data Encryption Implementation Plan
Table Of Contents Cloud Data Encryption Implementation PlanIncrease audience engagement and knowledge by dispensing information using Table Of Contents Cloud Data Encryption Implementation Plan. This template helps you present information on one stages. You can also present information on Existing Cloud Data, Infrastructure Constituents using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Team Structure For Cloud Data Encryption Implementation Cloud Data Encryption
Team Structure For Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the team structure for the cloud data encryption implementation project. The team members are the project manger, encryption engineer, software developer, systems administrator, operations engineer, cloud administrator, etc. Present the topic in a bit more detail with this Team Structure For Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Development Team, Encryption Engineer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline For Cloud Data Security Implementation Cloud Data Encryption
Timeline For Cloud Data Security Implementation Cloud Data EncryptionThis slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Introducing Timeline For Cloud Data Security Implementation Cloud Data Encryption to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Test Encryption Solutions, Implement Encryptions Solution, using this template. Grab it now to reap its full benefits.





