Powerpoint Templates and Google slides for Encryption Steps
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption Implementation Strategies Steps To Implement Encryption Techniques In Organization
Encryption Implementation Strategies Steps To Implement Encryption Techniques In OrganizationThis slide discusses the procedure for implementing encryption in applications. The steps mentioned in this slide are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Encryption Implementation Strategies Steps To Implement Encryption Techniques In Organization to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Implement Data Encryption At Rest, Deploy Data Encryption In Transit, Assess Encryption Requirements, Choose Encryption Algorithms, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age It
Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure for implementing encryption in applications. The steps mentioned in this slide are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Steps To Implement Encryption Techniques In Organization Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Identify Sensitive Data, Choose Encryption Algorithms, Deploy Data Encryption In Transit, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections
Encryption Implementation Strategies Steps Followed By Internet Protocol Security ConnectionsThe purpose of this slide is to outline the working steps of internet protocol security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Present the topic in a bit more detail with this Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections. Use it as a tool for discussion and navigation on Protocol Security Connections, Packet Authentication, Encryption, Data Transmission, Decryption Of Data Packets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Steps For Quantum Safe Certificate Migration
Encryption Implementation Strategies Steps For Quantum Safe Certificate MigrationThis slide demonstrates the process of replicating the old certificates with quantum-safe certificates. The steps included are quantum-safe PKI, update servers cryptography, update clients cryptography, install QS roots, install QS certificates, and deprecate old cryptography. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Steps For Quantum Safe Certificate Migration. Dispense information and present a thorough explanation of Quantum Safe Certificate Migration, Deprecate Old Cryptography, Support Recent Algorithms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Steps Involved In Working Of Cloud Storage Encryption
Encryption Implementation Strategies Steps Involved In Working Of Cloud Storage EncryptionThis slide demonstrates the working process of cloud encryption technique to secure data stored in the cloud. The purpose of this slide is to discuss two main components of cloud cryptography, known as data-in-transit and data-at-rest. Present the topic in a bit more detail with this Encryption Implementation Strategies Steps Involved In Working Of Cloud Storage Encryption. Use it as a tool for discussion and navigation on Cloud Storage Encryption, Data In Transit, Cloud Cryptography, Cloud Encryption Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
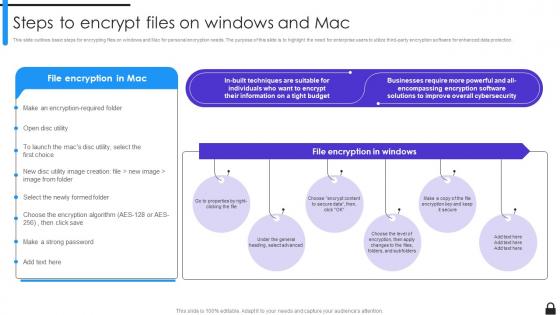 Encryption Implementation Strategies Steps To Encrypt Files On Windows And Mac
Encryption Implementation Strategies Steps To Encrypt Files On Windows And MacThis slide outlines basic steps for encrypting files on windows and Mac for personal encryption needs. The purpose of this slide is to highlight the need for enterprise users to utilize third-party encryption software for enhanced data protection. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Steps To Encrypt Files On Windows And Mac. This template helps you present information on six stages. You can also present information on Encrypting Files On Windows, Mac For Personal Encryption Needs, Encryption Software, Enhanced Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Steps To Implement Regulatory Compliance Plan
Encryption Implementation Strategies Steps To Implement Regulatory Compliance PlanThe purpose of this slide is to outline the critical steps involved in implementing a compliance plan to ensure data protection and privacy. These steps include auditing the environment, hiring a compliance officer, maintaining policies, providing employee training, etc. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Steps To Implement Regulatory Compliance Plan. This template helps you present information on six stages. You can also present information on Maintain Policies, Regulatory Compliance Plan, Continuous Improvement, Audit Existing Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Steps To Set Up Field Level Encryption
Encryption Implementation Strategies Steps To Set Up Field Level EncryptionThis slide represents the process of setting up field level encryption technology. The key steps involved in this procedure are identify sensitive fields and select encryption method, get encryption keys, make a profile for field-level encryption, etc. Introducing Encryption Implementation Strategies Steps To Set Up Field Level Encryption to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Identify Sensitive Fields, Select Encryption Method, Get Encryption Keys, Symmetric Or Asymmetric, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Working Steps Of Asymmetric Key Encryption
Encryption Implementation Strategies Working Steps Of Asymmetric Key EncryptionThis slide demonstrates the steps included in the working process of asymmetric key cryptography. The purpose of this slide is to illustrate the flow diagram of public key encryption. The key components included are registration, lookup, encrypt, decode, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Working Steps Of Asymmetric Key Encryption. Use it as a tool for discussion and navigation on Working Steps Of Asymmetric, Encrypt, Public Key Encryption, Asymmetric Key Cryptography. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It
Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the working steps of Internet Protocol Security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Deliver an outstanding presentation on the topic using this Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Connections, Protocol Security, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps For Quantum Safe Certificate Migration Encryption For Data Privacy In Digital Age It
Steps For Quantum Safe Certificate Migration Encryption For Data Privacy In Digital Age ItThis slide demonstrates the process of replicating the old certificates with quantum-safe certificates. The steps included are Quantum-safe PKI, update server or s cryptography, update clients cryptography, install QS roots, install QS certificates, and deprecate old cryptography. Introducing Steps For Quantum Safe Certificate Migration Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cryptography, Install Qs Certificates, Process, using this template. Grab it now to reap its full benefits.
-
 Steps Involved In Working Of Cloud Storage Encryption Encryption For Data Privacy In Digital Age It
Steps Involved In Working Of Cloud Storage Encryption Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working process of cloud encryption technique to secure the data being stored in the cloud. The purpose of this slide is to discuss two main components of cloud cryptography, known as data-in-transit and data-at-rest. Deliver an outstanding presentation on the topic using this Steps Involved In Working Of Cloud Storage Encryption Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encapsulates, Encryption, Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps Of Key Signing And Verification In Digital Signatures Encryption For Data Privacy In Digital Age It
Steps Of Key Signing And Verification In Digital Signatures Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to represent the entire process of key signing and verification, serving as a comprehensive guide to understanding the digital signature procedure. The key components include public key, private key, hash function, etc. Present the topic in a bit more detail with this Steps Of Key Signing And Verification In Digital Signatures Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Verification, Comparable, Procedure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Encrypt Website With Https Encryption For Data Privacy In Digital Age It
Steps To Encrypt Website With Https Encryption For Data Privacy In Digital Age ItThis slide represents the process of website encryption using Hypertext Transfer Protocol Secure HTTPS. The key steps are determine which services and web servers require encryption, obtain certificates, set the web server up to utilize HTTPS, and manage and administer certificates. Increase audience engagement and knowledge by dispensing information using Steps To Encrypt Website With Https Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Manage And Administer Certifications, Obtain Certificates, Require Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Prepare For Adoption Of Quantum Safe Standards Encryption For Data Privacy In Digital Age It
Steps To Prepare For Adoption Of Quantum Safe Standards Encryption For Data Privacy In Digital Age ItThis slide represents the key milestones to help industries to implement new quantum-safe standards. The main components of this slide are data discovery and classification, create a crypto inventory, embrace crypto agility and quantum safe. Deliver an outstanding presentation on the topic using this Steps To Prepare For Adoption Of Quantum Safe Standards Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Classification, Data Discovery, Embrace Crypto Agility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Set Up Field Level Encryption Encryption For Data Privacy In Digital Age It
Steps To Set Up Field Level Encryption Encryption For Data Privacy In Digital Age ItThis slide represents the process of setting up field level encryption technology. The key steps involved in this procedure are identify sensitive fields and select encryption method, get encryption keys, make a profile for field-level encryption, etc. Increase audience engagement and knowledge by dispensing information using Steps To Set Up Field Level Encryption Encryption For Data Privacy In Digital Age It. This template helps you present information on six stages. You can also present information on Requirements, Asymmetric, Symmetric using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working Steps Of Asymmetric Key Encryption Encryption For Data Privacy In Digital Age It
Working Steps Of Asymmetric Key Encryption Encryption For Data Privacy In Digital Age ItThis slide demonstrates the steps included in working process of asymmetric key cryptography. The purpose of this slide is to illustrate the flow diagram of public key encryption. The key components included are registration, lookup, encrypt, decode, etc. Present the topic in a bit more detail with this Working Steps Of Asymmetric Key Encryption Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric, Encryption, Registration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Steps Of Link Level Encryption Encryption For Data Privacy In Digital Age It
Working Steps Of Link Level Encryption Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to demonstrate how link level encryption technology works. This slide also discusses about the determination of min-max values for encryption key size negotiation and finding a common key size for link level encryption. Deliver an outstanding presentation on the topic using this Working Steps Of Link Level Encryption Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Key Size Negotiation, Finding The Min Max Values, Level Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Steps Of Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age It
Working Steps Of Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure of Triple Data Encryption Algorithm TDEA. The purpose of this slide is to explain the TDES encryption and decryption process using Data Encryption algorithm DEA and three keys named as K1, K2 and K3. Present the topic in a bit more detail with this Working Steps Of Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Encryption, Algorithm, Decryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Implement A Secure Encryption Algorithm
Steps To Implement A Secure Encryption AlgorithmThis slide represents steps to implement encryption algorithm which assists to provide privacy, authenticity and integrity to data. It includes steps to implement secure encryption algorithm such as choose right algorithm, choose right key, etc. Presenting our set of slides with name Steps To Implement A Secure Encryption Algorithm. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Choose Right Algorithm, Choose Right Software, Keep Key Secure.
-
 Next Steps For Encryption Framework Upgradation Proposal
Next Steps For Encryption Framework Upgradation ProposalThis slide covers the next step that the organization must sign. It covers discussion for project and acceptance of proposal etc. Increase audience engagement and knowledge by dispensing information using Next Steps For Encryption Framework Upgradation Proposal. This template helps you present information on seven stages. You can also present information on Project And Acceptance Of Proposal, Encryption Framework, Upgradation Proposal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 End To End Encryption Challenges With Action Steps
End To End Encryption Challenges With Action StepsThis slide covers the challenges associated with implementing end-to-end encryption. The purpose of this template is to enlighten stakeholders on key issues such as key management complexity, cross-platform compatibility, user experience impact, data recovery challenges, and regulatory compliance complexity. Deliver an outstanding presentation on the topic using this End To End Encryption Challenges With Action Steps Dispense information and present a thorough explanation of Key Management Complexity, User Experience Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Five Step Process To Implement End To End Encryption
Five Step Process To Implement End To End EncryptionThis slide covers a 5-stage process for implementing end-to-end encryption. The purpose of this template is to provide a comprehensive roadmap for effectively working on end-to-end encryption, including defining requirements, selecting encryption algorithms, testing, deploying, and monitoring the solution.Introducing Five Step Process To Implement End To End Encryption to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Select Encryption Algorithms, Testing And Validation, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Steps For Effective Encryption Method Deployment
Application Security Implementation Plan Steps For Effective Encryption Method DeploymentThis slide highlights the steps for deploying effective encryption which include selecting appropriate algorithm, choosing correct key size, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Steps For Effective Encryption Method Deployment. This template helps you present information on six stages. You can also present information on Select Appropriate Algorithm, Select Appropriate Program, Maintain Key Security, Encryption Method Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Data Encryption Backend Plans
Steps To Implement Data Encryption Backend PlansThe purpose of this slide is to guide organizations in implementing data encryption backend plans. It ensures seamless integration of robust strategies to safeguard sensitive data and enhance cybersecurity. Presenting our set of slides with name Steps To Implement Data Encryption Backend Plans. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encryption Types, Algorithm Selection, Key Management.



