Powerpoint Templates and Google slides for Encryption Overview
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments
Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different DepartmentsThis slide summarizes data security attacks across different organizational departments, such as human resources, IT department, finance, marketing, operations, etc. The outlined attacks are phishing scams, malware infections, data breaches, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments. Use it as a tool for discussion and navigation on Human Resources, IT Department, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies About Bring Your Own Encryption Overview And Benefits
Encryption Implementation Strategies About Bring Your Own Encryption Overview And BenefitsThis slide discusses about widely used encryption method known as Bring Your Own Encryption BYOE. The purpose of this slide is to elaborate the meaning of BYOE. This slide also outlines the benefits of Bring Your Own Keys BYOK method. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies About Bring Your Own Encryption Overview And Benefits. This template helps you present information on eight stages. You can also present information on Bring Your Own Encryption, Bring Your Own Keys, Control And Monitoring using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies About File Level Encryption Overview And Types
Encryption Implementation Strategies About File Level Encryption Overview And TypesThe purpose of this slide is to compare the administration and security levels of the various types of file-level encryption. The kinds of file-level encryption discussed in this slide are application level, file-system level, volume, partition, etc. Introducing Encryption Implementation Strategies About File Level Encryption Overview And Types to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Administration And Security Levels, File Level Encryption, Application Level, File System Level, using this template. Grab it now to reap its full benefits.
-
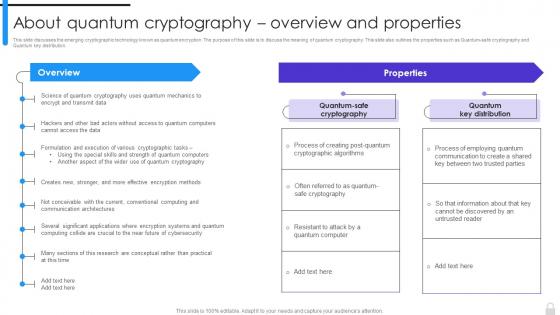 Encryption Implementation Strategies About Quantum Cryptography Overview And Properties
Encryption Implementation Strategies About Quantum Cryptography Overview And PropertiesThis slide discusses the emerging cryptographic technology known as quantum encryption. The purpose of this slide is to discuss the meaning of quantum cryptography. This slide also outlines the properties such as Quantum-safe cryptography and Quantum key distribution. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies About Quantum Cryptography Overview And Properties. Dispense information and present a thorough explanation of Quantum Safe Cryptography, Quantum Key Distribution, Quantum Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Encryption As A Service Overview And Features
Encryption Implementation Strategies Encryption As A Service Overview And FeaturesThis slide discusses the Encryption-as-a-Service model of securing data using cryptographic techniques. This slide also outlines the characteristics of Encryption-as-a-Service, such as confidentiality, authentication, integrity, nonrepudiation, etc. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Encryption As A Service Overview And Features. This template helps you present information on six stages. You can also present information on Text Message Encoding, Encryption Services, Subscription Packages, Data Encryption Security Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use
Encryption Implementation Strategies Overview Of Encryption For Securing Data In UseThe purpose of this slide is to outline the different possible ways of protecting data in use. The methods include IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use. Dispense information and present a thorough explanation of Information Rights Management, Encryption For Securing Data, Role Based Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies
Overview Of Encryption For Securing Data At Rest Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data at rest. The storage methods include file servers, network shares, document management systems, external storage, databases, endpoint devices, mobile devices, cloud storage, etc. Present the topic in a bit more detail with this Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies. Use it as a tool for discussion and navigation on Database Encryption, Information Rights Management, Data Leak Prevention, Mobile Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies
Overview Of Encryption For Securing Data In Transit Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data in transit. The methods include email encryption, MFT Managed File Transfer, IRM Information Rights Management, CASB Cloud Access Security Brokers, and DLP Data Leak Prevention. Deliver an outstanding presentation on the topic using this Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Common Data Encryption Des Overview And Applications Cloud Cryptography
Common Data Encryption Des Overview And Applications Cloud CryptographyThis slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Deliver an outstanding presentation on the topic using this Common Data Encryption Des Overview And Applications Cloud Cryptography. Dispense information and present a thorough explanation of Overview, Applications, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Standard For Advanced Encryption Aes Overview And Features Cloud Cryptography
Standard For Advanced Encryption Aes Overview And Features Cloud CryptographyThis slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Introducing Standard For Advanced Encryption Aes Overview And Features Cloud Cryptography to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Key Expansion, Overview, Processing, using this template. Grab it now to reap its full benefits.
-
 About Bring Your Own Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It
About Bring Your Own Encryption Overview And Benefits Encryption For Data Privacy In Digital Age ItThis slide discusses about widely used encryption method known as Bring Your Own Encryption BYOE. The purpose of this slide is to elaborate the meaning of BYOE. This slide also outlines the benefits of Bring Your Own Keys BYOK method. Present the topic in a bit more detail with this About Bring Your Own Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Overview, Encryption, Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Deniable Encryption Overview And Advantages Encryption For Data Privacy In Digital Age It
About Deniable Encryption Overview And Advantages Encryption For Data Privacy In Digital Age ItThis slide talks about a unique concept of cryptography, known as deniable encryption. The purpose of this slide is to outline the several benefits of deniable encryption such as plausible deniability, privacy protection and safeguard against forced decryption. Present the topic in a bit more detail with this About Deniable Encryption Overview And Advantages Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Encryption, Overview, Decryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Digital Signatures Overview And Methods Encryption For Data Privacy In Digital Age It
About Digital Signatures Overview And Methods Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the concept and methods of digital signatures in public key cryptography. This slide also discusses the use of public and private keys, the decryption process, and use of RSA and DSA algorithms to implement digital signatures. Deliver an outstanding presentation on the topic using this About Digital Signatures Overview And Methods Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Implementation, Overview, Significantly using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Full Disk Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It
About Full Disk Encryption Overview And Benefits Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to discuss full disk encryption technology to safeguard the data present on disk. This slide also outlines the benefits of full disk encryption method such as protects data at rest, temporary file encryption, quicker than manual encryption, etc. Deliver an outstanding presentation on the topic using this About Full Disk Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Overview, Automatically using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Homomorphic Encryption Overview And Types Encryption For Data Privacy In Digital Age It
About Homomorphic Encryption Overview And Types Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the concept of homomorphic encryption. The benefits of this technique are privacy preservation, data security, secure outsourcing, trust in untrusted environments, enhanced data exchange, etc. Present the topic in a bit more detail with this About Homomorphic Encryption Overview And Types Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Homomorphic, Encryption, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It
About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role and functionality of IPsec Internet Protocol Security in securing connections between devices. This slide also outlines the uses of IPsec such as protecting data during transmission over open networks, use in building VPNs, etc. Deliver an outstanding presentation on the topic using this About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Overview, Protocol Security, Destination using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Link Level Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It
About Link Level Encryption Overview And Benefits Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to discuss link level encryption technology to safeguard the data transmission from one link to another. This slide also outlines the benefits of LLE method and different levels of security provided by LLE such as 0-bit, 56-bit and 128-bit. Present the topic in a bit more detail with this About Link Level Encryption Overview And Benefits Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Encryption, Overview, Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Quantum Cryptography Overview And Properties Encryption For Data Privacy In Digital Age It
About Quantum Cryptography Overview And Properties Encryption For Data Privacy In Digital Age ItThis slide discusses the emerging cryptographic technology known as quantum encryption. The purpose of this slide is to discuss the meaning of quantum cryptography. This slide also outlines the properties such as Quantum-safe cryptography and Quantum key distribution. Deliver an outstanding presentation on the topic using this About Quantum Cryptography Overview And Properties Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Quantum, Cryptography, Properties using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Ssl Certificate Overview And Working Encryption For Data Privacy In Digital Age It
About Ssl Certificate Overview And Working Encryption For Data Privacy In Digital Age ItThis slide talks about the Secure Sockets Layer SSL certificates. The purpose of this slide is to discuss the installation process of SSL certificates. This slide also represents the certificate chain which includes root intermediate and server certificate. Present the topic in a bit more detail with this About Ssl Certificate Overview And Working Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Certificate, Overview, Intermediate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Asymmetric Key Data Encryption Overview Encryption For Data Privacy In Digital Age It
Asymmetric Key Data Encryption Overview Encryption For Data Privacy In Digital Age ItThis slide discusses about public key cryptography. The purpose of this slide is to outline the steps of asymmetric data encryption. The key components included are original text, encrypted data, public key, private key, encryption, decryption, etc. Deliver an outstanding presentation on the topic using this Asymmetric Key Data Encryption Overview Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Asymmetric, Encryption, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Standard Algorithm Overview And Applications Encryption For Data Privacy In Digital Age It
Data Standard Algorithm Overview And Applications Encryption For Data Privacy In Digital Age ItThis slide discusses about Data Encryption Standard DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Present the topic in a bit more detail with this Data Standard Algorithm Overview And Applications Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Overview, Applications, Data Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption As A Service Overview And Features Encryption For Data Privacy In Digital Age It
Encryption As A Service Overview And Features Encryption For Data Privacy In Digital Age ItThis slide talks about the Encryption-as-a-Service model of securing data using cryptographic techniques. This slide also outlines the characteristics of Encryption-as-a-Service, such as confidentiality, authentication, integrity, nonrepudiation, etc. Deliver an outstanding presentation on the topic using this Encryption As A Service Overview And Features Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Service, Overview, Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Encryption Overview And Implementation Methods Encryption For Data Privacy In Digital Age It
Network Encryption Overview And Implementation Methods Encryption For Data Privacy In Digital Age ItThis slide talks about the network encryption methods to secure communication between two sites. This slide also demonstrates the ways to implement network encryption such as Communication Support Modules CSMs, Secure Sockets Layer SSL, etc. Deliver an outstanding presentation on the topic using this Network Encryption Overview And Implementation Methods Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Overview, Implementation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Different Data Encryption Algorithm Types Encryption For Data Privacy In Digital Age It
Overview Of Different Data Encryption Algorithm Types Encryption For Data Privacy In Digital Age ItThis slide outlines the several data encryption algorithms. The purpose of this slide is to divide all available cryptographic algorithms into two types of encryption, namely symmetric and asymmetric. These algorithms are 3DES encryption, Twofish encryption, etc. Introducing Overview Of Different Data Encryption Algorithm Types Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Encryption, Algorithm, Overview, using this template. Grab it now to reap its full benefits.
-
 Standard For Advanced Encryption Aes Overview Encryption For Data Privacy In Digital Age It
Standard For Advanced Encryption Aes Overview Encryption For Data Privacy In Digital Age ItThis slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Present the topic in a bit more detail with this Standard For Advanced Encryption Aes Overview Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Key Expansion, Overview, Key Length. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Encryption Security Attacks In IoT Security And Privacy Safeguarding IoT SS
Overview Of Encryption Security Attacks In IoT Security And Privacy Safeguarding IoT SSThis slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Introducing Overview Of Encryption Security Attacks In IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Attackers Deploy, Possess Either, Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data Security
Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data SecurityThis slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data Security. Use it as a tool for discussion and navigation on Employing Mathematical Algorithms, Transform Sensitive Data, Unstructured Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data What Is Encryption General Overview Cybersecurity SS
Encryption For Data What Is Encryption General Overview Cybersecurity SSThis slide showcases general overview of encryption technology which acts as a cornerstone of data privacy. It provides details about plaintext, ciphertext, data privacy, integrity, compliance issues, etc. Introducing Encryption For Data What Is Encryption General Overview Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Benefits, Overview, Increase Consumer Trust, using this template. Grab it now to reap its full benefits.



