Powerpoint Templates and Google slides for Encrypt Data
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Client Side Encryption With Customer Managed Keys Cloud Data Encryption
Client Side Encryption With Customer Managed Keys Cloud Data EncryptionThis slide shows the client side encryption and decryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encrypted data key, etc. Present the topic in a bit more detail with this Client Side Encryption With Customer Managed Keys Cloud Data Encryption. Use it as a tool for discussion and navigation on Encrypted Object Data, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Data Encryption Implementation Plan Table Of Contents
Cloud Data Encryption Implementation Plan Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Cloud Data Encryption Implementation Plan Table Of Contents. This template helps you present information on one stages. You can also present information on Key Challenges, Cloud Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Data Encryption Service Providers Cloud Data Encryption
Cloud Data Encryption Service Providers Cloud Data EncryptionThis slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Present the topic in a bit more detail with this Cloud Data Encryption Service Providers Cloud Data Encryption. Use it as a tool for discussion and navigation on Providers, Reason For Selecting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data Encryption
Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data EncryptionThis slide outlines several cloud storage providers with in built zero knowledge encryption. The key points include name, storage provided in a free plan, cost of the monthly subscription plan, and advantages and disadvantages of the service provider. Deliver an outstanding presentation on the topic using this Cloud Storage Providers With In Built Zero Knowledge Encryption Cloud Data Encryption. Dispense information and present a thorough explanation of Storage Provided Free Plan, Cost Of Monthly Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparison Between Cryptomator And Nordlocker Software Cloud Data Encryption
Comparison Between Cryptomator And Nordlocker Software Cloud Data EncryptionThis slide compares the two popular encryption software, named Cryptomator and NordLocker. The comparison is carried out based on several factors, such as encryption method, client side encryption, platforms supported, user interface, pricing, etc. Present the topic in a bit more detail with this Comparison Between Cryptomator And Nordlocker Software Cloud Data Encryption. Use it as a tool for discussion and navigation on Cryptomator, Nordlocker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Between Server-Side And Client Side Encryption Cloud Data Encryption
Comparison Between Server-Side And Client Side Encryption Cloud Data EncryptionThe purpose of this slide is to compare client side and server side encryption procedures. The comparison is carried out based on several factors, such as encryption performed, key management, data privacy, complexity, collaboration, performance overhead, etc. Deliver an outstanding presentation on the topic using this Comparison Between Server Side And Client Side Encryption Cloud Data Encryption. Dispense information and present a thorough explanation of Encryption Performed, Key Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Considerations For Zero Knowledge Encryption Service Selection Cloud Data Encryption
Considerations For Zero Knowledge Encryption Service Selection Cloud Data EncryptionThe purpose of this slide is to highlight the several factors to be considered while selecting zero knowledge encryption service providers. The main discussed factors are storage space, privacy and security, price, and other perks. Present the topic in a bit more detail with this Considerations For Zero Knowledge Encryption Service Selection Cloud Data Encryption. Use it as a tool for discussion and navigation on Storage Space, Privacy And Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Stages Of Cloud Data Encryption Implementation Cloud Data Encryption
Different Stages Of Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the different steps involved in the cloud data encryption implementation process. These stages discussed in this slide are client side encryption or zero knowledge encryption, in transit encryption, and server side encryption. Increase audience engagement and knowledge by dispensing information using Different Stages Of Cloud Data Encryption Implementation Cloud Data Encryption. This template helps you present information on three stages. You can also present information on Encryption Performed, Service Provider using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Estimated Budget Of Cloud Data Encryption Implementation Cloud Data Encryption
Estimated Budget Of Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the budget for integrating cloud encryption in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. Present the topic in a bit more detail with this Estimated Budget Of Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Services, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Existing Cloud Data Infrastructure Constituents Cloud Data Encryption
Existing Cloud Data Infrastructure Constituents Cloud Data EncryptionThis slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc. Deliver an outstanding presentation on the topic using this Existing Cloud Data Infrastructure Constituents Cloud Data Encryption. Dispense information and present a thorough explanation of Cloud Storage, Cloud Databases using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide Cloud Data Encryption Implementation Plan
Icons Slide Cloud Data Encryption Implementation PlanIntroducing our well researched set of slides titled Icons Slide Cloud Data Encryption Implementation Plan. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption
Impact Of Encryption Implementation On Cloud Security Cloud Data EncryptionThis slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data Encryption
Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data EncryptionThis slide discusses the security issues faced by the organization due to a lack of encryption in cloud services. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. Present the topic in a bit more detail with this Key Challenges Of Existing Cloud Storage Infrastructure Cloud Data Encryption. Use it as a tool for discussion and navigation on Data Security Concerns, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data Encryption
Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data EncryptionThe purpose of this slide is to discuss the challenges faced while encrypting cloud data. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies. Deliver an outstanding presentation on the topic using this Major Risks And Mitigation Strategies For Cloud Encryption Implementation Cloud Data Encryption. Dispense information and present a thorough explanation of Probability, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Performance Analysis Of Existing Cloud Network Cloud Data Encryption
Performance Analysis Of Existing Cloud Network Cloud Data EncryptionThe purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Present the topic in a bit more detail with this Performance Analysis Of Existing Cloud Network Cloud Data Encryption. Use it as a tool for discussion and navigation on Where We Are, Where We Want To Be. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Project Summary For Cloud Data Encryption Implementation Cloud Data Encryption
Project Summary For Cloud Data Encryption Implementation Cloud Data EncryptionThe purpose of this slide is to represent the summary of the cloud data encryption implementation project providing information regarding problems faced, recommended solution, estimated project cost, and estimated timeline. Deliver an outstanding presentation on the topic using this Project Summary For Cloud Data Encryption Implementation Cloud Data Encryption. Dispense information and present a thorough explanation of Problem, Solution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide shows the matrix to assign multiple responsibilities to the different team members for the cloud data encryption implementation project. The responsibilities include problem assessment, solution selection, encryption implementation, etc. Present the topic in a bit more detail with this Raci Matrix For Cloud Data Encryption Implementation Plan Cloud Data Encryption. Use it as a tool for discussion and navigation on Problem Assessment, Solution Selection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
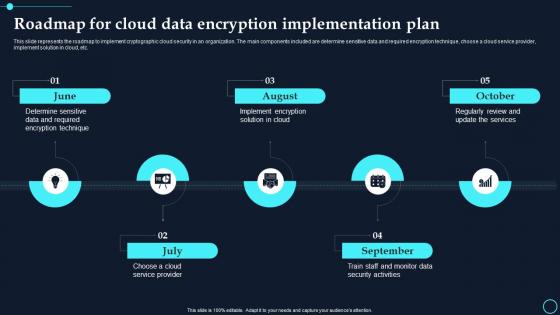 Roadmap For Cloud Data Encryption Implementation Plan Cloud Data Encryption
Roadmap For Cloud Data Encryption Implementation Plan Cloud Data EncryptionThis slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc.Increase audience engagement and knowledge by dispensing information using Roadmap For Cloud Data Encryption Implementation Plan Cloud Data Encryption. This template helps you present information on five stages. You can also present information on August, October using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Server Side Encryption To Protect Cloud Data Cloud Data Encryption
Server Side Encryption To Protect Cloud Data Cloud Data EncryptionThis slide discusses server side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc. Present the topic in a bit more detail with this Server Side Encryption To Protect Cloud Data Cloud Data Encryption. Use it as a tool for discussion and navigation on Readable, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Server Side Encryption With Customer Managed Keys Cloud Data Encryption
Server Side Encryption With Customer Managed Keys Cloud Data EncryptionThis slide demonstrates the server side encryption process with the keys provided by the customer. The components included are object data, encryption algorithm, encrypted object data, customer key, encryption, decryption, etc. Deliver an outstanding presentation on the topic using this Server Side Encryption With Customer Managed Keys Cloud Data Encryption. Dispense information and present a thorough explanation of Customer Key, Encryption Algorithm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Service Comparison Of Zero Knowledge Encryption Providers Cloud Data Encryption
Service Comparison Of Zero Knowledge Encryption Providers Cloud Data EncryptionThis slide highlights the availability of various services in different zero knowledge encryption providers to encrypt the data stored in the cloud. The significant services mentioned in this slide are sync folder, file link sharing, folder sharing, and versioning. Deliver an outstanding presentation on the topic using this Service Comparison Of Zero Knowledge Encryption Providers Cloud Data Encryption. Dispense information and present a thorough explanation of Service Provider, Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setup And Retrieval Process For Key Distribution Cloud Data Encryption
Setup And Retrieval Process For Key Distribution Cloud Data EncryptionThis slide represents the key management process for encrypted cloud storage. The components included are the setup process, cloud server, retrieval process, data users, key distribution, data owner, query expansion, search query, central index, etc. Present the topic in a bit more detail with this Setup And Retrieval Process For Key Distribution Cloud Data Encryption. Use it as a tool for discussion and navigation on Mandatory Process, Optional Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Cloud Data Encryption Implementation Plan
Table Of Contents Cloud Data Encryption Implementation PlanIncrease audience engagement and knowledge by dispensing information using Table Of Contents Cloud Data Encryption Implementation Plan. This template helps you present information on one stages. You can also present information on Existing Cloud Data, Infrastructure Constituents using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Team Structure For Cloud Data Encryption Implementation Cloud Data Encryption
Team Structure For Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the team structure for the cloud data encryption implementation project. The team members are the project manger, encryption engineer, software developer, systems administrator, operations engineer, cloud administrator, etc. Present the topic in a bit more detail with this Team Structure For Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Development Team, Encryption Engineer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline For Cloud Data Security Implementation Cloud Data Encryption
Timeline For Cloud Data Security Implementation Cloud Data EncryptionThis slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Introducing Timeline For Cloud Data Security Implementation Cloud Data Encryption to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Test Encryption Solutions, Implement Encryptions Solution, using this template. Grab it now to reap its full benefits.
-
 Training Plan For Cloud Data Encryption Implementation Cloud Data Encryption
Training Plan For Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the composition of a training plan for cloud data encryption implementation. The key components include the training module, expected learning, mode of training, training hours, and expected completion date. Present the topic in a bit more detail with this Training Plan For Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Training Module, Expected Learning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Knowledge Cloud Storage Services Cloud Data Encryption
Zero Knowledge Cloud Storage Services Cloud Data EncryptionThis slide discusses zero knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable. Deliver an outstanding presentation on the topic using this Zero Knowledge Cloud Storage Services Cloud Data Encryption. Dispense information and present a thorough explanation of Scrambles Data Using, Service Provider using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Before Vs After Adopting Data Encryption Techniques
Encryption Implementation Strategies Before Vs After Adopting Data Encryption TechniquesThis slide compares the scenario after integrating encryption protocols in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are data protection, insider threat protection, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Before Vs After Adopting Data Encryption Techniques. Use it as a tool for discussion and navigation on Data Protection, Security Breach Impact, Regulatory Compliance, Data Sharing And Collaboration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Challenges Of Data At Rest Encryption And Solutions
Encryption Implementation Strategies Challenges Of Data At Rest Encryption And SolutionsThis slide outlines the various limitations of data at rest protection and their possible solutions. These are scattered documentation, sensitive data stored on personal mobile devices, lack of control over data stored in cloud, compliance with data protection regulations in different verticals, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Challenges Of Data At Rest Encryption And Solutions. Use it as a tool for discussion and navigation on Data At Rest Protection, Scattered Documentation, Sensitive Data Stored, Personal Mobile Devices, Data Protection Regulations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Challenges Of Data In Transit Encryption And Solutions
Encryption Implementation Strategies Challenges Of Data In Transit Encryption And SolutionsThis slide outlines the various limitations of data in transit protection and their possible solutions. These are infinite number of channels for communication, protection of an infinite number of cloud applications, loss of control at the receiving end, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Challenges Of Data In Transit Encryption And Solutions. Dispense information and present a thorough explanation of Data In Transit, Encryption And Solutions, Cloud Applications, Channels For Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions
Encryption Implementation Strategies Challenges Of Data In Use Protection And SolutionsThis slide outlines the various limitations of data in use protection and their possible solutions. These include limited control after data access, unauthorized copying or sharing of data, limitations of collaboration platforms, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions. Use it as a tool for discussion and navigation on Limitations Of Collaboration Platforms, Unauthorized Copying Or Sharing Of Data, Limited Control After Data Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Checklist To Implement Data Encryption Technology
Encryption Implementation Strategies Checklist To Implement Data Encryption TechnologyThis slide outlines the steps to be taken to protect the organizations data using encryption. The key approaches include identify sensitive data, assess requirements, select method, implement encryption, test functionality, establish monitoring, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Checklist To Implement Data Encryption Technology. Dispense information and present a thorough explanation of Assess Requirements, Implement Encryption, Establish Monitoring, Test Functionality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Column Level Data Encryption In SQL Servers
Encryption Implementation Strategies Column Level Data Encryption In SQL ServersThis slide discusses the encryption hierarchy in column level data encryption. The purpose of this slide is to represent different tiers of encryption hierarchy such as windows level, SQL server level, user database level, instance level, and master database level. Present the topic in a bit more detail with this Encryption Implementation Strategies Column Level Data Encryption In SQL Servers. Use it as a tool for discussion and navigation on Encrypts Service Key, Master Database, Encrypts Database Encryption Key. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Comparison Between Column Level And Whole Database Encryption
Encryption Implementation Strategies Comparison Between Column Level And Whole Database EncryptionThe purpose of this slide is to outline the differences between column level and whole database encryption technologies. This slide compares the mentioned techniques based on several parameters such as scope, level of encryption, flexibility, compliance, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Comparison Between Column Level And Whole Database Encryption. Dispense information and present a thorough explanation of Whole Database Encryption, Flexibility, Compliance, Mentioned Techniques, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Criteria To Select Best Data Storage Encryption Method
Encryption Implementation Strategies Criteria To Select Best Data Storage Encryption MethodThis slide represents a guide to analyze the need for data protection in an organization. The criteria used to select the best data storage encryption method involves several factors such as security strength, performance impact, key management, compatibility, compliance, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Criteria To Select Best Data Storage Encryption Method. Dispense information and present a thorough explanation of Security Strength, Performance Impact, Key Management, Compatibility And Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Data Confidentiality Using End To End Encryption
Encryption Implementation Strategies Data Confidentiality Using End To End EncryptionThis slide illustrates the use of end-to-end encryption mechanism to maintain data confidentiality and secure digital ecosystems. The purpose of this slide is to demonstrate how data can be transformed into an encrypted format to transmit it over a network. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Confidentiality Using End To End Encryption. Dispense information and present a thorough explanation of Data Confidentiality, Encryption Mechanism, Demonstrate, Digital Ecosystems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Data Security Concerns Faced By Company
Encryption Implementation Strategies Data Security Concerns Faced By CompanyThis slide discusses the security issues faced by the organization due to a lack of encryption and data protection technologies. These concerns are unauthorized access, data breaches, insider threats, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Security Concerns Faced By Company. Dispense information and present a thorough explanation of Data Security Concerns, Phishing Attacks, Data Protection Technologies, Compliance And Regulations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Database Encryption Methods For Business Security
Encryption Implementation Strategies Database Encryption Methods For Business SecurityThis slide discusses the database encryption methods used to encrypt the data of different departments, such as finance, sales, and human resources. The database encryption levels are application-level encryption, plug-in method, TDE, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Database Encryption Methods For Business Security. Use it as a tool for discussion and navigation on Database Encryption Methods, Business Security, Sales And Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Different States Of Data Which Requires Protection
Encryption Implementation Strategies Different States Of Data Which Requires ProtectionThis slide discusses various customer demands to ensure data privacy and authenticity. The purpose of this slide is to highlight the various states of data that require encryption, such as data-at-rest, data-in-transit, and data-in-use. Introducing Encryption Implementation Strategies Different States Of Data Which Requires Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Customer Demands, Data Privacy And Authenticity, Require Encryption, Collaboration Software, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest
Encryption Implementation Strategies Encryption Technologies To Secure Data At RestThis slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Full Disk Encryption, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Estimated Budget Of Data Encryption Implementation
Encryption Implementation Strategies Estimated Budget Of Data Encryption ImplementationThis slide represents the budget for securing data using encryption techniques. The purpose of this slide is to showcase the estimated and actual cost for installing cryptographic solutions. The components include hardware and software, maintenance and support, training, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Estimated Budget Of Data Encryption Implementation. Use it as a tool for discussion and navigation on Maintenance And Support, Deployment Team, Data Encryption, Estimated Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use
Encryption Implementation Strategies Overview Of Encryption For Securing Data In UseThe purpose of this slide is to outline the different possible ways of protecting data in use. The methods include IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use. Dispense information and present a thorough explanation of Information Rights Management, Encryption For Securing Data, Role Based Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Roadmap To Encrypt Application Data Of Organization
Encryption Implementation Strategies Roadmap To Encrypt Application Data Of OrganizationThis slide represents the roadmap to implement encryption security in an organization. The main components included are are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Encryption Implementation Strategies Roadmap To Encrypt Application Data Of Organization to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Security, Identify Sensitive Data, Assess Encryption Requirements, Encryption Algorithms, Implement Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Symmetric Key Data Encryption Technique
Encryption Implementation Strategies Symmetric Key Data Encryption TechniqueThis slide illustrates the steps involved in transferring data using symmetric encryption. The purpose of this slide is to demonstrate how symmetric key encryption works. The critical components included are the sender, symmetric key, encrypted data, etc. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Symmetric Key Data Encryption Technique. This template helps you present information on five stages. You can also present information on Encrypted Data, Symmetric Key, Data Encryption Technique, Non Understandable Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Timeline To Implement Data Encryption In Organization
Encryption Implementation Strategies Timeline To Implement Data Encryption In OrganizationThe purpose of this slide is to represent the timeline to implement data encryption in an organization. The main phases highlighted in this slide are planning, research and evaluation, development, testing and quality assurance, deployment, etc. Introducing Encryption Implementation Strategies Timeline To Implement Data Encryption In Organization to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Development Phase, Testing And Quality Assurance Phase, Research And Evaluation Phase, Planning Phase, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection
Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data ProtectionThe purpose of this slide is to summarize several relevant regulations. These are GDPR General Data Protection Regulation, CCPA California Consumer Privacy Act, PCI DSS Payment Card Industry Data Security Standard, NIST, and HIPAA, along with their descriptions and scopes. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection. Dispense information and present a thorough explanation of General Data Protection Regulation, California Consumer Privacy Act, Health Insurance Portability And Accountability Act using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Training Program For Data Encryption Implementation
Encryption Implementation Strategies Training Program For Data Encryption ImplementationThis slide describes the training program for employees to implement data encryption in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Present the topic in a bit more detail with this Encryption Implementation Strategies Training Program For Data Encryption Implementation. Use it as a tool for discussion and navigation on Symmetric And Asymmetric Cryptography, Data Encryption Best Practices, Case Studies And Practical, Implementing Cryptographic Techniques. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies
Encryption Technologies To Secure Data In Transit Encryption Implementation StrategiesThis slide compares different data in transit protection methods, including their working and associated cost. These methods are email encryption, Managed File Transfer MFT, Data Leak Prevention DLP, Cloud Access Security Brokers CASB, etc. Deliver an outstanding presentation on the topic using this Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Managed File Transfer, Cloud Access Security Brokers, Email Encryption, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies
Overview Of Encryption For Securing Data At Rest Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data at rest. The storage methods include file servers, network shares, document management systems, external storage, databases, endpoint devices, mobile devices, cloud storage, etc. Present the topic in a bit more detail with this Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies. Use it as a tool for discussion and navigation on Database Encryption, Information Rights Management, Data Leak Prevention, Mobile Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies
Overview Of Encryption For Securing Data In Transit Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data in transit. The methods include email encryption, MFT Managed File Transfer, IRM Information Rights Management, CASB Cloud Access Security Brokers, and DLP Data Leak Prevention. Deliver an outstanding presentation on the topic using this Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Encryption Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of secure computer. It is a modern, vibrant and eye catching icon that will help to create an impactful presentation. It is a great way to emphasize the importance of data security and safety.
-
 Data Encryption Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on secure computer systems. It features a black and white design depicting a computer with a padlock, symbolizing the safety of your data. Use this icon to emphasize the importance of secure computing.
-
 Common Data Encryption Des Overview And Applications Cloud Cryptography
Common Data Encryption Des Overview And Applications Cloud CryptographyThis slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Deliver an outstanding presentation on the topic using this Common Data Encryption Des Overview And Applications Cloud Cryptography. Dispense information and present a thorough explanation of Overview, Applications, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Common Data Encryption Des Algorithm Cloud Cryptography
Working Of Common Data Encryption Des Algorithm Cloud CryptographyThis slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Deliver an outstanding presentation on the topic using this Working Of Common Data Encryption Des Algorithm Cloud Cryptography. Dispense information and present a thorough explanation of Pseudorandom, Initialization, Independent using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS V
Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS VThis slide represents data encryption model for effective information security It includes data encoding, data decoding, backup repository etc Introducing our Data Encryption Model For Effective Comprehensive Guide For Deployment Strategy SS V set of slides The topics discussed in these slides are Specialized Software, Handling Encryption, Authorized Parties This is an immediately available PowerPoint presentation that can be conveniently customized Download it and convince your audience
-
 Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management Process
Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management ProcessThe following slide illustrates various methods to encrypt and back-up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost. Present the topic in a bit more detail with this Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Advantages, Disadvantages. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Encryption Storage Lock File Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Storage Lock File Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Data Encryption Storage Lock File Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Storage Lock File Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.





