Powerpoint Templates and Google slides for Effective Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Information Security Program For Effective Cybersecurity Risk Management Powerpoint Presentation Slides
Information Security Program For Effective Cybersecurity Risk Management Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fifty six slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Effective Technologies For Cybersecurity Incident Response
Effective Technologies For Cybersecurity Incident ResponseThis slide explores effective security technology for cybersecurity incident response, optimizing response times, minimizing impact, and strengthening overall defense against evolving cyber threats. Introducing our Effective Technologies For Cybersecurity Incident Response set of slides. The topics discussed in these slides are Effective Technologies, Cybersecurity Incident Response, Minimizing Impact, Strengthening. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Plan With Effective Healthcare Tools
Cybersecurity Plan With Effective Healthcare ToolsThis slide presents healthcare cybersecurity plan, helpful in identifying nature of threats and using tools to protect system from malicious practices. It includes affected components such as patient, privacy protection, healthcare legacy system and tools such as Microsoft EMET and Exact Trak Introducing our Cybersecurity Plan With Effective Healthcare Tools set of slides. The topics discussed in these slides are Cybersecurity Key Components, Cybersecurity Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Cybersecurity Kpis And Metrics Categories
Effective Cybersecurity Kpis And Metrics CategoriesThis slide showcases the effective cybersecurity KPIs and metrics categories which helps an organization to measure objectives of raw data and helps to detect possible threats. It include details such as security program maturity, impacts, etc. Introducing our Effective Cybersecurity Kpis And Metrics Categories set of slides. The topics discussed in these slides are Security Program Maturity, Kpis And Metric Category. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Assessment Test To Measure Effectiveness Of Improving IoT Device Cybersecurity IoT SS
Assessment Test To Measure Effectiveness Of Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight assessment test through which companies can evaluate effectiveness of Internet of Things IoT cyber security plan. It covers information about questions such as spam, cyberbullying, self replicate, etc. Increase audience engagement and knowledge by dispensing information using Assessment Test To Measure Effectiveness Of Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Describes, Requires, Cyberbullying using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective Prerequisites Of AUP Cybersecurity Accountability
Effective Prerequisites Of AUP Cybersecurity AccountabilityThis slide exhibits AUP cybersecurity framework for safe, secure technology usage within an organization and ensuring legal compliance. It includes aspects such as constraints, computing resources, employee behavior, etc. Presenting our set of slides with Effective Prerequisites Of AUP Cybersecurity Accountability This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Awareness, Compliance, Risk Mitigation
-
 Effective Blackberry Cybersecurity Solutions For Enhanced Protection
Effective Blackberry Cybersecurity Solutions For Enhanced ProtectionThis slide showcases blackberry cybersecurity solutions for better safety. The purpose of this template is to provide businesses with solutions for enhancing protection against digital threats and vulnerabilities. It includes elements such as incident response, unified endpoint management, etc. Introducing our premium set of slides with Effective Blackberry Cybersecurity Solutions For Enhanced Protection. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Management, Protect, Response. So download instantly and tailor it with your information.
-
 Csirt Cybersecurity Challenges With Effective Solutions
Csirt Cybersecurity Challenges With Effective SolutionsThis slide showcases problems faced by CSIRT cyber security. The main purpose of this template is to showcase ways of addressing challenges. This includes resource limitation, skill shortage, regulatory compliance pressure, etc. Presenting our well structured Csirt Cybersecurity Challenges With Effective Solutions. The topics discussed in this slide are Resource Limitation, Skill Shortage, Regulatory Compliance Pressure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Role Of Csirt Cybersecurity Team
Effective Role Of Csirt Cybersecurity TeamThis slide provides different roles of CSIRT cyber security. The main purpose of this template is to showcase comprehensive approach for effective management. This includes incident responder, forensics report , legal advisor, etc. Introducing our premium set of slides with Effective Role Of Csirt Cybersecurity Team. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Intelligence Analyst, Incident Responder, Forensics Analyst. So download instantly and tailor it with your information.
-
 Comparative Analysis Of Effective Firewalls For Cybersecurity
Comparative Analysis Of Effective Firewalls For CybersecurityThis slide showcases the comparison between effective firewalls used for cybersecurity which helps an organization to carefully select the best tool that reduce operational costs. It include details such as price or month, ratings, scalability, integrations, etc. Presenting our well structured Comparative Analysis Of Effective Firewalls For Cybersecurity. The topics discussed in this slide are Comparative, Analysis, Cybersecurity. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Future Trends Of Cybersecurity Firewall
Effective Future Trends Of Cybersecurity FirewallThis slide showcases the major future trends of cybersecurity firewall which helps an organization to secure computer network from malicious traffic and unauthorized access. It include details such as cloud based, zero trust and artificial intelligence firewall. Presenting our set of slides with Effective Future Trends Of Cybersecurity Firewall. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Based Firewalls, Zero Trust Firewalls, AI Powered Firewalls .
-
 BCP Cybersecurity Icon To Address Information Threats Effectively
BCP Cybersecurity Icon To Address Information Threats EffectivelyPresenting our set of slides with BCP Cybersecurity Icon To Address Information Threats Effectively This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on BCP Cybersecurity, Address Information, Threats Effectively
-
 Effective Cybersecurity Measures In Retail Sector
Effective Cybersecurity Measures In Retail SectorThis slide highlights best practices for ensuring retail cyber security. The purpose of this template is to assist security teams in developing and implementing techniques for protecting enterprises from digital attacks. It includes elements such as employee training, recovery plan, etc. Presenting our set of slides with Effective Cybersecurity Measures In Retail Sector This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employee Training, Adherence, Regular Audits, Recovery Plan
-
 Effective Cybersecurity Program Management Framework
Effective Cybersecurity Program Management FrameworkFollowing slide showcases cybersecurity program management with customized methodology for early threat detection. It further covers directions, experience, culture and technology such as strategic roadmap, data driven innovation, defined audience, etc. Introducing our Effective Cybersecurity Program Management Framework set of slides. The topics discussed in these slides are Scalable Architecture, Integrated Systems, Data Driven Innovation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Cybersecurity Risk Management Process Flow
Effective Cybersecurity Risk Management Process FlowFollowing slide highlights process flow of cyber security risk management for enhanced efficiency. It further covers data sources, cyber security communities, private organizations, government organizations, continuous monitoring and threat modelling, etc. Presenting our well structured Effective Cybersecurity Risk Management Process Flow. The topics discussed in this slide are Cyber Security Communities, Private Organizations, Governative Organization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Of Cybersecurity Tools Used To Develop Effective Policy
Comparative Analysis Of Cybersecurity Tools Used To Develop Effective PolicyThis slide showcases the comparison between cybersecurity software used for creating effective and productive policies which helps an organization to carefully choose the best tool for business growth. It include details such as pricemonth, ratings, integrations, scalability, etc. Presenting our well structured Comparative Analysis Of Cybersecurity Tools Used To Develop Effective Policy The topics discussed in this slide are Vulnerability Management, Web Application SecurityThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Policy Effective Use Cases
Cybersecurity Policy Effective Use CasesThis slide showcases the effective and successful application of cybersecurity policy which helps an organization to recruit employees having exceptional skills and talent required for business growth. It include details such as data breach response, disaster recovery and business continuity. Introducing our premium set of slides with Cybersecurity Policy Effective Use Cases Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Breach Response, Disaster Recovery, Business Continuity So download instantly and tailor it with your information.
-
 Effective Steps To Create Cybersecurity Policy
Effective Steps To Create Cybersecurity PolicyThis slide showcases the effective and productive guidelines to develop cybersecurity policy which helps an organization to guide employees regarding accurate tomes for sharing business information. It include details such as manage sensitive data, prepare for incident, etc. Introducing our premium set of slides with Effective Steps To Create Cybersecurity Policy Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Manage Sensitive Data , Tackle Technology, Media Access So download instantly and tailor it with your information.
-
 Key Considerations To Select Pam Vendor For Effective Cybersecurity
Key Considerations To Select Pam Vendor For Effective CybersecurityThis slide represents various considerations that assist companies to select best PAM vendor to enhance their data protection and cybersecurity effectively. It includes various factors such as price transparency, easy management, user onboarding, etc. Presenting our well structured Key Considerations To Select Pam Vendor For Effective Cybersecurity. The topics discussed in this slide are Easy Management, Price Transparency, Innovation And Updates. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SS
Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SSThis slide represents checklist for promoting strategy adopted by security professionals for preventing and mitigating cyber security risks. It includes activities such as gain executive buy-in etc. Present the topic in a bit more detail with this Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Organizational Activities, Security Awareness Training, Ensure Effective Completion. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SS
Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SSThis slide represents essential elements for developing training program which helps to mitigate cyber security risks. It include components such as educational content, testing etc. Introducing Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Educational Content, Metrics And Reporting, Testing, Security Awareness Training Program, using this template. Grab it now to reap its full benefits.
-
 Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SS
Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SSThis slide represents procedure for developing training program which helps to mitigate cyber security risks. It include steps such as identify risks, change behavior etc. Increase audience engagement and knowledge by dispensing information using Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SS. This template helps you present information on five stages. You can also present information on Change Behavior, Identify Risks, Security Awareness, Training Program, Track Metrics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security team responsible, accountable, consulted and informed RACI matrix. It provides details about endpoint detection and response, network security, etc.Deliver an outstanding presentation on the topic using this Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Monitor Security, Identity Strategic Risk, Perform Business Impact Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Business Challenges For Effective Mdr Cybersecurity Adoption
Addressing Business Challenges For Effective Mdr Cybersecurity AdoptionThis slide represents various strategies that assist IT companies to mitigate challenges faced during MDR adoption for enhancing cybersecurity. It includes various challenges such as staffing, alert fatigue, and time to maturity. Introducing our Addressing Business Challenges For Effective Mdr Cybersecurity Adoption set of slides. The topics discussed in these slides are Mitigation, Strategies, Business. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Considerations To Select Mdr Vendor For Effective Cybersecurity
Key Considerations To Select Mdr Vendor For Effective CybersecurityThis slide represents various considerations that assist companies to select best MDR vendor to enhance their data protection and cybersecurity effectively. It includes various considerations such as expertise, facilities, and methodology. Introducing our Key Considerations To Select Mdr Vendor For Effective Cybersecurity set of slides. The topics discussed in these slides are Key Considerations, Cybersecurity, Methodology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mdr Architecture To Mitigate Cybersecurity Threats Effectively
Mdr Architecture To Mitigate Cybersecurity Threats EffectivelyThis slide represents MDR architecture that assists companies in mitigating cybersecurity threats to enhance data protection effectively. It includes elements such as company infrastructure, MDR platforms, D and R teams, customers, etc. Presenting our well structured Mdr Architecture To Mitigate Cybersecurity Threats Effectively. The topics discussed in this slide are Architecture, Cybersecurity, Threats Effectively. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS
Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SSThis slide outlines the hardware requirements to consider when selecting a network security tool to monitor and prevent malicious activities. These requirements include network interfaces etc. Introducing Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Interfaces, Storage, Redundancy, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SS
Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SSThis slide outlines the software requirements to consider when selecting a network security tool to monitor and prevent malicious activities. These requirements include scalability, operating system etc. Introducing Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Operating System, Database Management System, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
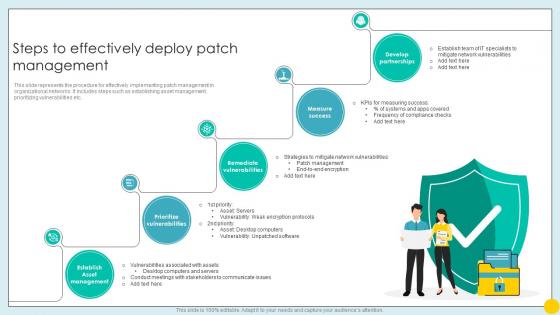 Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide represents the procedure for effectively implementing patch management in organizational networks. It includes steps such as establishing asset management, prioritizing vulnerabilities etc.Introducing Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Prioritize Vulnerabilities, Remediate Vulnerabilities, Measure Success, Develop Partnerships, using this template. Grab it now to reap its full benefits.
-
 Malware Assessment For Effective Management Of Cybersecurity Risk
Malware Assessment For Effective Management Of Cybersecurity RiskThis slide displays statistical report to analyze year wise total number of malware reported in organization. It includes years such as 2023, 2022, 2021, 2020, etc. Introducing our Malware Assessment For Effective Management Of Cybersecurity Risk set of slides. The topics discussed in these slides are Assessment, Management, Cybersecurity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Program Effective Cybersecurity Risk Management Table Of Contents
Security Program Effective Cybersecurity Risk Management Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Security Program Effective Cybersecurity Risk Management Table Of Contents. This template helps you present information on seven stages. You can also present information on Risk Governance, Enterprise Risk Ecosystem, Program Effectiveness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Information Security Program For Effective Cybersecurity Risk Management
Icons Slide Information Security Program For Effective Cybersecurity Risk ManagementIntroducing our well researched set of slides titled Icons Slide Information Security Program For Effective Cybersecurity Risk Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Agenda Security Program For Effective Cybersecurity Risk Management
Agenda Security Program For Effective Cybersecurity Risk ManagementIntroducing Agenda Security Program For Effective Cybersecurity Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digitalization, Cybersecurity, Business, using this template. Grab it now to reap its full benefits.
-
 Information Security Program Cybersecurity Checklist Effectively Managing Asset Security
Information Security Program Cybersecurity Checklist Effectively Managing Asset SecurityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Information Security Program Cybersecurity Checklist Effectively Managing Asset Security. Use it as a tool for discussion and navigation on Checklist For Effectively Managing Asset Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Information Security Program For Effective Cybersecurity Risk Management
Table Of Contents Information Security Program For Effective Cybersecurity Risk ManagementIncrease audience engagement and knowledge by dispensing information using Table Of Contents Information Security Program For Effective Cybersecurity Risk Management. This template helps you present information on eight stages. You can also present information on Requirements, Technologies, Gap Identification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
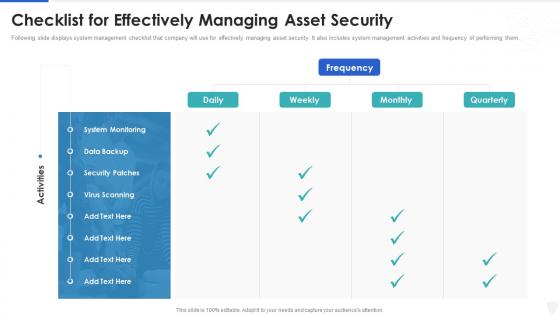 Cybersecurity and digital business risk management checklist for effectively managing asset security
Cybersecurity and digital business risk management checklist for effectively managing asset securityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Checklist For Effectively Managing Asset Security. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Effective Cybersecurity Awareness Training Program
Best Practices For Effective Cybersecurity Awareness Training ProgramThis slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting our set of slides with name Best Practices For Effective Cybersecurity Awareness Training Program. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Getting Into Compliance, Establishing Basics, Including Everyone.
-
 Cybersecurity Attack Vector Analysis For Effective Awareness Training
Cybersecurity Attack Vector Analysis For Effective Awareness TrainingThis slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Introducing our premium set of slides with Cybersecurity Attack Vector Analysis For Effective Awareness Training. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Attack Vector, Examples, Objective, Problem Identifier. So download instantly and tailor it with your information.
-
 Cybersecurity Awareness Topics To Considered For Effective Training
Cybersecurity Awareness Topics To Considered For Effective TrainingThis slide covers cybersecurity awareness topics to considered for effective training. It involves topics such as removable media, cloud security, public wi fi and physical security. Presenting our set of slides with name Cybersecurity Awareness Topics To Considered For Effective Training. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Removable Media, Cloud Security, Physical Security, Public Wi Fi.
-
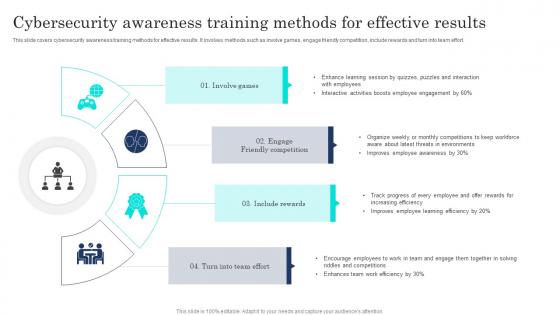 Cybersecurity Awareness Training Methods For Effective Results
Cybersecurity Awareness Training Methods For Effective ResultsThis slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Introducing our premium set of slides with Cybersecurity Awareness Training Methods For Effective Results. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Awareness Training, Methods, Effective Results. So download instantly and tailor it with your information.
-
 Cybersecurity Awareness Training Program Process To Ensure Effectiveness
Cybersecurity Awareness Training Program Process To Ensure EffectivenessThis slide covers cybersecurity awareness training program process to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Presenting our set of slides with name Cybersecurity Awareness Training Program Process To Ensure Effectiveness. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implement Training, Evaluate Training Program, Determine Type Of Training, Identify Training Need.
-
 Cybersecurity Awareness Training To Enhance Effectiveness Of Employees
Cybersecurity Awareness Training To Enhance Effectiveness Of EmployeesThis slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Introducing our premium set of slides with Cybersecurity Awareness Training To Enhance Effectiveness Of Employees. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Document Management, Passwords And Authentication, Social Engineering And Phishing. So download instantly and tailor it with your information.
-
 Employee Questionnaire To Assess Cybersecurity Awareness Training Effectiveness
Employee Questionnaire To Assess Cybersecurity Awareness Training EffectivenessThis slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Introducing our Employee Questionnaire To Assess Cybersecurity Awareness Training Effectiveness set of slides. The topics discussed in these slides are Employee Questionnaire, Cybersecurity Awareness Training, Effectiveness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Communication Plan For Effective Incident Management Cybersecurity Incident And Vulnerability
Communication Plan For Effective Incident Management Cybersecurity Incident And VulnerabilityThis slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person. Introducing Communication Plan For Effective Incident Management Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Delivery Method, Incident Information, Team Meetings, using this template. Grab it now to reap its full benefits.
-
 Impact Categories For Effectively Handling Cyber Security Incidents Cybersecurity Incident And Vulnerability
Impact Categories For Effectively Handling Cyber Security Incidents Cybersecurity Incident And VulnerabilityMentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. Increase audience engagement and knowledge by dispensing information using Impact Categories For Effectively Handling Cyber Security Incidents Cybersecurity Incident And Vulnerability. This template helps you present information on three stages. You can also present information on Functional Impact, Information Impact, Recoverability Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Communication Plan For Effective Incident Upgrading Cybersecurity With Incident Response Playbook
Communication Plan For Effective Incident Upgrading Cybersecurity With Incident Response PlaybookThis slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person. Present the topic in a bit more detail with this Communication Plan For Effective Incident Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Communication, Management, Deliverable. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Categories For Effectively Handling Cyber Upgrading Cybersecurity With Incident Response Playbook
Impact Categories For Effectively Handling Cyber Upgrading Cybersecurity With Incident Response PlaybookMentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. Present the topic in a bit more detail with this Impact Categories For Effectively Handling Cyber Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Functional Impact, Information Impact, Recoverability Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Approaches To Overcome Cybersecurity Risk Faced Effective Risk Management Strategies
Approaches To Overcome Cybersecurity Risk Faced Effective Risk Management StrategiesThe following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add ons, using a customized web application firewall etc. Present the topic in a bit more detail with this Approaches To Overcome Cybersecurity Risk Faced Effective Risk Management Strategies. Use it as a tool for discussion and navigation on Ransomware, Phishing, Business Email Compromise. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Cybersecurity Strategic Plan For Crisis Communication
Effective Cybersecurity Strategic Plan For Crisis CommunicationThis slide presents cybersecurity plan helpful in seamless communication during crisis within an organization and to deliver accurate and comprehensive messages to stakeholders. It includes plan for phishing attack, spy attack and denial of service. Introducing our Effective Cybersecurity Strategic Plan For Crisis Communication set of slides. The topics discussed in these slides are Phising Attack, Risk, Communication, Channel This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Cybersecurity Risk Mitigation Strategies
Effective Cybersecurity Risk Mitigation StrategiesThe following slide illustrates key risk mitigation strategies for cybersecurity to limit impact of potential threats. This covers five strategies risk assessment, data encryption, firewalls, employee training and incident response plan.Presenting our set of slides with Effective Cybersecurity Risk Mitigation Strategies. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Risk Assessment, Encryption Software, Incident Response.
-
 Compliance Standards For Effective Cybersecurity In Healthcare
Compliance Standards For Effective Cybersecurity In HealthcareThis slide presents compliance standards for effective application of cybersecurity in healthcare helpful for providing patients more control over health information and defining baseline of minimum requirements for organisations. It includes HIPAA, GDPR, PIPEDA. Presenting our well structured Compliance Standards For Effective Cybersecurity In Healthcare The topics discussed in this slide are Compliance Standards, Description, Countries Covered. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Checklist For Cybersecurity In Healthcare
Effective Checklist For Cybersecurity In HealthcareThis slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption. Introducing our Effective Checklist For Cybersecurity In Healthcare set of slides. The topics discussed in these slides are Factors, Description, Status This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Strategies For Enhanced Healthcare Cybersecurity
Effective Strategies For Enhanced Healthcare CybersecurityThis slide presents multiple strategies for improving cybersecurity in healthcare helpful for organisations to prevent loss of medical devices and records. It includes prompt software update, strong system access controls, cybersecurity training, risk assessment and updating passwords regularly. Presenting our set of slides with Effective Strategies For Enhanced Healthcare Cybersecurity This exhibits information on fivestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prompt Software Updates, Cybersecurity Training, Risk Assessments.
-
 Cybersecurity Awareness Areas For Effective Planning And Communication
Cybersecurity Awareness Areas For Effective Planning And CommunicationThis slide showcases process of initiating cybersecurity communication plan. This template focuses on protecting information to ensure that it is not corrupted. It includes information related to network security,malware protection, etc.Presenting our set of slides with Cybersecurity Awareness Areas For Effective Planning And Communication. This exhibits information on nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Event Management, Home Working, Detachable Media Controls.
-
 Smart Analysis Of Cybersecurity Effective Goals
Smart Analysis Of Cybersecurity Effective GoalsThis slide presents SMART analysis of cybersecurity goals helpful in creating cybersecurity plan based on requirements. It includes indicators such as specific, measurable, attainable, relevant and time-bound goals that are highly effective in use Introducing our premium set of slides with Smart Analysis Of Cybersecurity Effective Goals. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Attainable, Relevant, Measurable. So download instantly and tailor it with your information.
-
 Budget for effective cybersecurity management document powerpoint presentation deck
Budget for effective cybersecurity management document powerpoint presentation deckThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting this set of slides with name Budget For Effective Cybersecurity Management Document Powerpoint Presentation Deck. The topics discussed in these slides are Budget Effective, Cybersecurity, Management Document. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.




