Powerpoint Templates and Google slides for Digital Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD
Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MDIf you require a professional template with great design, then this Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty one slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Play 11 Administering Security And Privacy Through Reusable Digital Service Management Playbook
Play 11 Administering Security And Privacy Through Reusable Digital Service Management PlaybookThis slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Present the topic in a bit more detail with this Play 11 Administering Security And Privacy Through Reusable Digital Service Management Playbook. Use it as a tool for discussion and navigation on Procedures, Administering, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 US Digital Services Management Play 11 Administering Security And Privacy Through ReUSable
US Digital Services Management Play 11 Administering Security And Privacy Through ReUSableThis slide provides information regarding digital services play which helps in managing security and privacy through reUSable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Deliver an outstanding presentation on the topic USing this US Digital Services Management Play 11 Administering Security And Privacy Through ReUSable Dispense information and present a thorough explanation of Department Or Agency, Secure Controllability USing the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
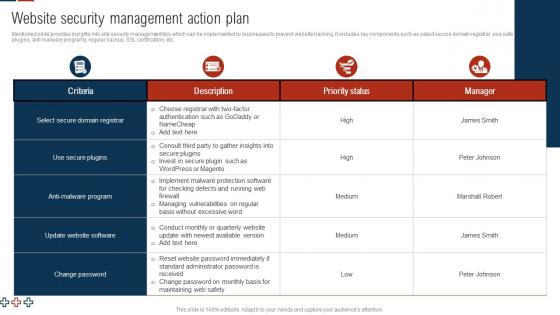 Comprehensive Guide For Digital Website Website Security Management Action Plan
Comprehensive Guide For Digital Website Website Security Management Action PlanMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Present the topic in a bit more detail with this Comprehensive Guide For Digital Website Website Security Management Action Plan. Use it as a tool for discussion and navigation on Criteria, Priority Status, Manager. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital Security Management In Powerpoint And Google Slides Cpb
Digital Security Management In Powerpoint And Google Slides CpbPresenting our Digital Security Management In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Digital Security Management. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Digital Transformation Icon For Information Security Management
Digital Transformation Icon For Information Security ManagementIntroducing our premium set of slides with Digital Transformation Icon For Information Security Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Digital Transformation Icon, Information Security Management. So download instantly and tailor it with your information.
-
 Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS
Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SSThe following slide depicts details about security tokens to offer benefits to investors. It includes elements such as stocks, bonds, real world assets, improved liquidity, foster innovation, transparency, automated payments, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS This template helps you present information on Four stages. You can also present information on Improved Liquidity, Foster Innovation, Offers Transparency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Crisis Management Icon For Digital Security
Cyber Crisis Management Icon For Digital SecurityIntroducing our premium set of slides with name Cyber Crisis Management Icon For Digital Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Crisis Management, Digital Security. So download instantly and tailor it with your information.
-
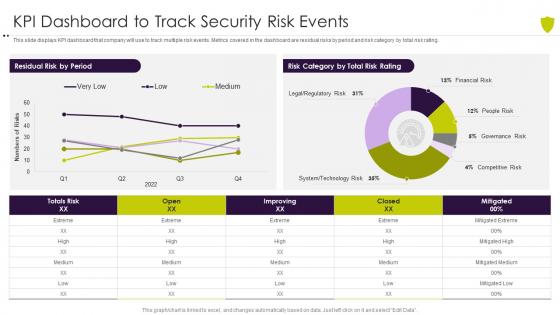 Kpi dashboard to track security risk events managing cyber risk in a digital age
Kpi dashboard to track security risk events managing cyber risk in a digital ageThis slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Track Security Risk Events Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of KPI Dashboard To Track Security Risk Events using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
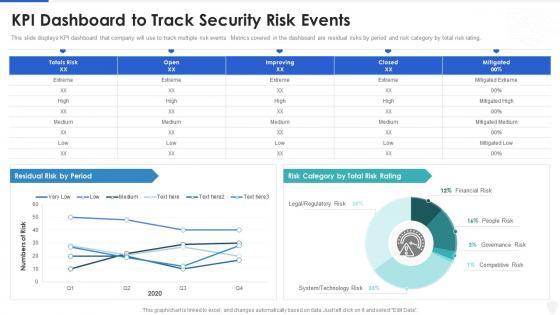 Cybersecurity and digital business risk management kpi dashboard to track security risk events
Cybersecurity and digital business risk management kpi dashboard to track security risk eventsPresent the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Kpi Dashboard To Track Security Risk Events. Use it as a tool for discussion and navigation on KPI Dashboard To Track Security Risk Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets Security
Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. Present the topic in a bit more detail with this Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Periodic Risk Assessment, Individuals, Implement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security
Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Deliver an outstanding presentation on the topic using this Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Exploitation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different kinds of insider digital managing critical threat vulnerabilities and security threats
Different kinds of insider digital managing critical threat vulnerabilities and security threatsThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Introducing Different Kinds Of Insider Digital Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Third Party Insider, Malicious Insider, using this template. Grab it now to reap its full benefits.
-
 Different kinds of insider digital threats corporate security management
Different kinds of insider digital threats corporate security managementThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Introducing Different Kinds Of Insider Digital Threats Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Insider, Negligent Or Careless Insider, Third Party Insider, using this template. Grab it now to reap its full benefits.
-
 Eliminating manual security processes managing cyber risk in a digital age
Eliminating manual security processes managing cyber risk in a digital ageMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Eliminating Manual Security Processes Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Vulnerability, Scanning, Resolution, Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security program framework managing cyber risk in a digital age
Information security program framework managing cyber risk in a digital ageMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Information Security Program Framework Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Information Security Program Framework Key Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing cyber risk in a digital age information security program values to business
Managing cyber risk in a digital age information security program values to businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Introducing Managing Cyber Risk In A Digital Age Information Security Program Values To Business to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Security lifecycle managing cyber risk in a digital age
Security lifecycle managing cyber risk in a digital ageIncrease audience engagement and knowledge by dispensing information using Security Lifecycle Managing Cyber Risk In A Digital Age. This template helps you present information on one stages. You can also present information on Security Lifecycle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Summary existing security managing cyber risk in a digital age
Summary existing security managing cyber risk in a digital ageFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Present the topic in a bit more detail with this Summary Existing Security Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Summary Existing Security Management Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
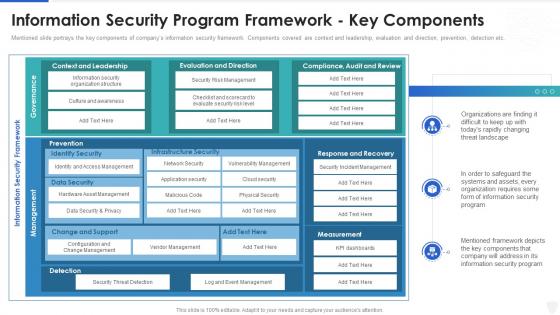 Cybersecurity and digital business risk management security program framework
Cybersecurity and digital business risk management security program frameworkMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Security Program Framework. Dispense information and present a thorough explanation of Framework, Information, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity digital business management information security program values business
Cybersecurity digital business management information security program values businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Deliver an outstanding presentation on the topic using this Cybersecurity Digital Business Management Information Security Program Values Business. Dispense information and present a thorough explanation of Environment, Management, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management different kinds of insider digital threats
Cyber security risk management different kinds of insider digital threatsThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Introducing Cyber Security Risk Management Different Kinds Of Insider Digital Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Insider, Negligent Or Careless Insider, Third Party Insider, using this template. Grab it now to reap its full benefits.
-
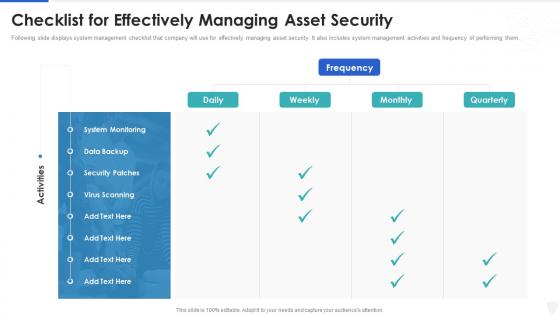 Cybersecurity and digital business risk management checklist for effectively managing asset security
Cybersecurity and digital business risk management checklist for effectively managing asset securityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Checklist For Effectively Managing Asset Security. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
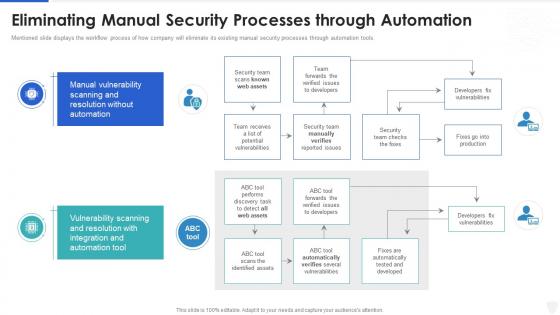 Cybersecurity and digital business risk management eliminating manual security processes
Cybersecurity and digital business risk management eliminating manual security processesMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Eliminating Manual Security Processes. Use it as a tool for discussion and navigation on Processes, Resolution, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity and digital business risk management key security controls to be addressed
Cybersecurity and digital business risk management key security controls to be addressedPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Increase audience engagement and knowledge by dispensing information using Cybersecurity And Digital Business Risk Management Key Security Controls To Be Addressed. This template helps you present information on three stages. You can also present information on Framework, Authentification, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
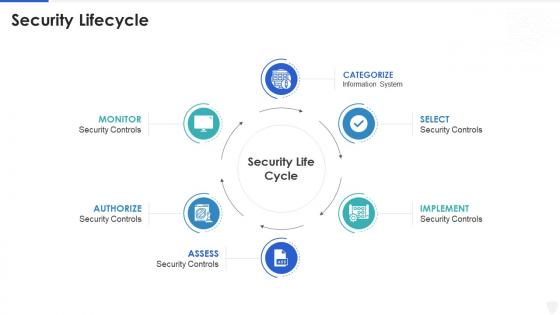 Cybersecurity and digital business risk management security lifecycle
Cybersecurity and digital business risk management security lifecycleIntroducing Cybersecurity And Digital Business Risk Management Security Lifecycle to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security Lifecycle, using this template. Grab it now to reap its full benefits.
-
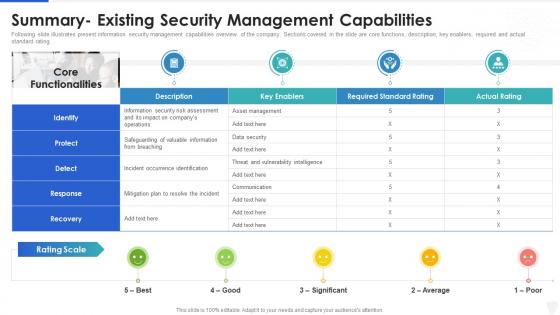 Cybersecurity and digital business risk management summary- existing security management
Cybersecurity and digital business risk management summary- existing security managementFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Summary- Existing Security Management. Dispense information and present a thorough explanation of Management, Information, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security
Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorization, Confidentiality, Availability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security
Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver an outstanding presentation on the topic using this Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Manufacturing, Government, Healthcare using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security
Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Present the topic in a bit more detail with this Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Unauthorized, Business, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security
Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Targeted Intelligence, Malware Intelligence, Reputation Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security
Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability. Deliver an outstanding presentation on the topic using this Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Categorizing, Confidentiality, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security
Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Present the topic in a bit more detail with this Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Management, Initiatives, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security
Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Comparative, Assessment, Parameters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security
Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Present the topic in a bit more detail with this Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Contingency Solutions, Contingency Considerations, Information . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security
Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Parameters, Capability, Determine . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security
Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Installation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security
Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Present the topic in a bit more detail with this Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Malicious Insider, Negligent Or Careless Insider, Third Party Insider . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security
Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Introducing Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Finance, Corporate Security, Business Division, using this template. Grab it now to reap its full benefits.
-
 Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security
Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Increase audience engagement and knowledge by dispensing information using Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security. This template helps you present information on three stages. You can also present information on Plan And Collect, Review And Analyze, Strategic Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security
Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. Deliver an outstanding presentation on the topic using this Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Potential, Technologies, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Cyber Threats Management To Enable Digital Assets Security
Table Of Contents Cyber Threats Management To Enable Digital Assets SecurityPresent the topic in a bit more detail with this Table Of Contents Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorizing, Associated, Determine Sequence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital media management network security business process transformation cpb
Digital media management network security business process transformation cpbPresenting this set of slides with name - Digital Media Management Network Security Business Process Transformation Cpb. This is an editable five stages graphic that deals with topics like Digital Media Management, Network Security, Business Process Transformation to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Digital payment business solution payment security and fraud management solutions analysis ppt grid
Digital payment business solution payment security and fraud management solutions analysis ppt gridFrom prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Introducing Digital Payment Business Solution Payment Security And Fraud Management Solutions Analysis Ppt Grid to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Before The Payment, On The Payment Page, After The Payment, using this template. Grab it now to reap its full benefits.
-
 Payment security and fraud management solutions browser digital payment business solution ppt model
Payment security and fraud management solutions browser digital payment business solution ppt modelPayment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Introducing Payment Security And Fraud Management Solutions Browser Digital Payment Business Solution Ppt Model to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Costs, Process, Analytics, Development, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Web Wallets For Accessible Cryptocurrency Management
Secure Your Digital Assets Web Wallets For Accessible Cryptocurrency ManagementThis slide represents the introduction and commonly used web wallets. This slide outlines the ordinary web wallets in the market, such as bit2me, Binance, coin base, myether wallet, metamask, atomic wallet, etc. Introducing Secure Your Digital Assets Web Wallets For Accessible Cryptocurrency Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Web Wallets For Accessible, Cryptocurrency Management, Ordinary Web Wallets, Security Of The Private Keys, using this template. Grab it now to reap its full benefits.



