Powerpoint Templates and Google slides for Determining Threats
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS V
Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS VThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Risk Analysis Risk Analysis Register To Determine Potential Threat Supplier Negotiation Strategy SS V. Dispense information and present a thorough explanation of Likelihood Of Occurring, Mitigation Plan, Inaccurate Forecasting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Register Determine Potential Threat Achieving Business Goals Procurement Strategies Strategy SS V
Risk Register Determine Potential Threat Achieving Business Goals Procurement Strategies Strategy SS VThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Risk Register Determine Potential Threat Achieving Business Goals Procurement Strategies Strategy SS V. Dispense information and present a thorough explanation of Risk Analysis, Potential, Disruptions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cost Reduction Strategies Risk Analysis Risk Analysis Register To Determine Potential Threat Strategy SS V
Cost Reduction Strategies Risk Analysis Risk Analysis Register To Determine Potential Threat Strategy SS VThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Cost Reduction Strategies Risk Analysis Risk Analysis Register To Determine Potential Threat Strategy SS V. Dispense information and present a thorough explanation of Likelihood Of Occurring, Severity, Mitigation Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
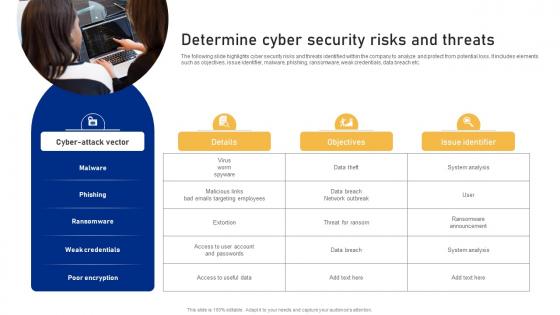 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Creating Cyber Security Awareness
Determine Cyber Security Risks And Threats Creating Cyber Security AwarenessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Human Errors, Factor Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats
Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Deliver an outstanding presentation on the topic using this Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining Data Loss Impact Due To Cyber Threat Safeguarding Business With Data Loss Cybersecurity SS
Determining Data Loss Impact Due To Cyber Threat Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding impact of data loss due to threat agents such as insider threat, social engineering, malware, specific enterprise cyber threats, etc.Present the topic in a bit more detail with this Determining Data Loss Impact Due To Cyber Threat Safeguarding Business With Data Loss Cybersecurity SS. Use it as a tool for discussion and navigation on Insider Threat, Social Engineering, Maintenance Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security
Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Deliver an outstanding presentation on the topic using this Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Exploitation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine phases of threat attack disrupting it project safety contd key initiatives for project safety it
Determine phases of threat attack disrupting it project safety contd key initiatives for project safety itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Determine Phases Of Threat Attack Disrupting It Project Safety Contd Key Initiatives For Project Safety It. This template helps you present information on four stages. You can also present information on System, Communication, Network, Implement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine phases of threat attack disrupting it project safety key initiatives for project safety it
Determine phases of threat attack disrupting it project safety key initiatives for project safety itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Determine Phases Of Threat Attack Disrupting It Project Safety Key Initiatives For Project Safety It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Networks, Systems, Email, Information, Target, using this template. Grab it now to reap its full benefits.
-
 Cyber threat management workplace determine sequence phases for attack
Cyber threat management workplace determine sequence phases for attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Threat Management Workplace Determine Sequence Phases For Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber threat management workplace determine threat scenario analysis
Cyber threat management workplace determine threat scenario analysisThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Determine Threat Scenario Analysis. Dispense information and present a thorough explanation of Threat Scenario, Threat Campaign, Exploitation, Command And Control, Actions And Objectives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat management workplace determine several threat actors profile
Cyber threat management workplace determine several threat actors profileThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Cyber Threat Management Workplace Determine Several Threat Actors Profile. Use it as a tool for discussion and navigation on Cyber Criminal, Targeted Asset, Objective. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat management workplace determine staff training schedule skills
Cyber threat management workplace determine staff training schedule skillsThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Determine Staff Training Schedule Skills. Dispense information and present a thorough explanation of Advanced Software Training, Advanced Skills Training, Training Module, Self Assessment Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat management workplace determine threat management team
Cyber threat management workplace determine threat management teamThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Introducing Cyber Threat Management Workplace Determine Threat Management Team to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Management Head, Security Manager, Crisis Management Advisor, Medical Advisor, HR Advisor, Legal Advisor, using this template. Grab it now to reap its full benefits.
-
 Determine sequence phases for threat cyber threat management workplace
Determine sequence phases for threat cyber threat management workplaceThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Cyber Threat Management Workplace to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Determine sequence phases for managing critical threat vulnerabilities and security threats
Determine sequence phases for managing critical threat vulnerabilities and security threatsThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Increase audience engagement and knowledge by dispensing information using Determine Sequence Phases For Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on four stages. You can also present information on Installation, Command And Control, Actions And Objectives, Covering Tracks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine several threat actors managing critical threat vulnerabilities and security threats
Determine several threat actors managing critical threat vulnerabilities and security threatsThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an outstanding presentation on the topic using this Determine Several Threat Actors Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Determine Several Threat Actors Profile using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine staff training schedule managing critical threat vulnerabilities and security threats
Determine staff training schedule managing critical threat vulnerabilities and security threatsThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Introducing Determine Staff Training Schedule Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Advanced Software Training, Training Module, using this template. Grab it now to reap its full benefits.
-
 Determine threat management managing critical threat vulnerabilities and security threats
Determine threat management managing critical threat vulnerabilities and security threatsThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Increase audience engagement and knowledge by dispensing information using Determine Threat Management Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on two stages. You can also present information on Determine Threat Management Team Structure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine threat scenario managing critical threat vulnerabilities and security threats
Determine threat scenario managing critical threat vulnerabilities and security threatsThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Present the topic in a bit more detail with this Determine Threat Scenario Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Threat Campaign, Actions And Objectives, Covering Tracks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing critical threat vulnerabilities and security threats determine sequence phases
Managing critical threat vulnerabilities and security threats determine sequence phasesThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Managing Critical Threat Vulnerabilities And Security Threats Determine Sequence Phases to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Delivery, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Corporate security management determine sequence phases for threat attack
Corporate security management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Corporate Security Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack actions corporate security management
Determine sequence phases for threat attack actions corporate security managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Actions Corporate Security Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Determine several threat actors profile corporate security management
Determine several threat actors profile corporate security managementThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Corporate Security Management. Use it as a tool for discussion and navigation on Determine Several Threat Actors Profile. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine threat management team structure corporate security management
Determine threat management team structure corporate security managementThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Increase audience engagement and knowledge by dispensing information using Determine Threat Management Team Structure Corporate Security Management. This template helps you present information on two stages. You can also present information on Legal Advisor, HR Advisor, Medical Advisor, Security Manager using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine threat scenario analysis corporate security management
Determine threat scenario analysis corporate security managementThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Corporate Security Management. Dispense information and present a thorough explanation of Command And Control, Actions And Objectives, Reconnaissance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management for organization critical determine sequence phases for threat
Threat management for organization critical determine sequence phases for threatThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Threat Management For Organization Critical Determine Sequence Phases For Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Threat management for organization critical determine sequence threat attack contd
Threat management for organization critical determine sequence threat attack contdThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Threat Management For Organization Critical Determine Sequence Threat Attack Contd. This template helps you present information on four stages. You can also present information on Installation, Command And Control, Actions And Objectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine threat scenario analysis threat management for organization critical
Determine threat scenario analysis threat management for organization criticalThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Present the topic in a bit more detail with this Determine Threat Scenario Analysis Threat Management For Organization Critical. Use it as a tool for discussion and navigation on Reconnaissance, Exploitation, Actions And Objectives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management for organization critical determine threat management team structure
Threat management for organization critical determine threat management team structureThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impactsboth employees and community, company reputation, share values, and corporate assets. Introducing Threat Management For Organization Critical Determine Threat Management Team Structure to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Determine Threat Management Team Structure, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management determine sequence phases for threat attack
Cyber security risk management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Exploitation, Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management determine several threat actors profile
Cyber security risk management determine several threat actors profileThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Determine Several Threat Actors Profile. Dispense information and present a thorough explanation of Cyber Criminal, Targeted Asset, Objective using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management determine threat management team
Cyber security risk management determine threat management teamThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Introducing Cyber Security Risk Management Determine Threat Management Team to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Management Head, Security Manager, Crisis Management Advisor, Medical Advisor, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management determine threat scenario analysis
Cyber security risk management determine threat scenario analysisThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Threat Scenario Analysis. This template helps you present information on two stages. You can also present information on Threat Scenario, Threat Campaign, Exploitation, Command And Control, Actions And Objectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack contd cyber security risk management
Determine sequence phases for threat attack contd cyber security risk managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Contd Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Determine Sequence Phases For Threat Attack Contd Vulnerability Administration At Workplace
Determine Sequence Phases For Threat Attack Contd Vulnerability Administration At WorkplaceThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Increase audience engagement and knowledge by dispensing information using Determine Sequence Phases For Threat Attack Contd Vulnerability Administration At Workplace. This template helps you present information on four stages. You can also present information on Installation, Communication, Sequence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability Administration At Workplace Determine Threat Scenario Analysis
Vulnerability Administration At Workplace Determine Threat Scenario AnalysisThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Determine Threat Scenario Analysis. Use it as a tool for discussion and navigation on Determine Threat Scenario Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine phases of threat attack disrupting it project safety enhancing overall project security it
Determine phases of threat attack disrupting it project safety enhancing overall project security itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Determine Phases Of Threat Attack Disrupting It Project Safety Enhancing Overall Project Security It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it determine phases of threat attack disrupting project safety contd
Enhancing overall project security it determine phases of threat attack disrupting project safety contdThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Introducing Enhancing Overall Project Security It Determine Phases Of Threat Attack Disrupting Project Safety Contd to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace Overview
Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace OverviewThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an outstanding presentation on the topic using this Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Packages, Training, Enhancement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Threat Management Team Structure Managing IT Threats At Workplace Overview
Determine Threat Management Team Structure Managing IT Threats At Workplace OverviewThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the company s internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Introducing Determine Threat Management Team Structure Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Determine, Threat Management, Team Structure, using this template. Grab it now to reap its full benefits.
-
 Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security
Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Parameters, Capability, Determine . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security
Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Installation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 4 quadrant model to determine strength weakness opportunity and threat
4 quadrant model to determine strength weakness opportunity and threatPresenting this set of slides with name - 4 Quadrant Model To Determine Strength Weakness Opportunity And Threat. This is a four stage process. The stages in this process are 4 Quadrant Model, 4 Quadrant Framework, 4 Quadrant Structure.
-
 Determine phases of threat attack disrupting it project safety management to improve project safety it
Determine phases of threat attack disrupting it project safety management to improve project safety itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Determine Phases Of Threat Attack Disrupting IT Project Safety Management To Improve Project Safety IT. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine phases of threat attack disrupting project safety contd management to improve project safety it
Determine phases of threat attack disrupting project safety contd management to improve project safety itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Phases Of Threat Attack Disrupting Project Safety Contd Management To Improve Project Safety IT to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.



