Powerpoint Templates and Google slides for Determine Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Virus Assistant Performing Concentration Determining Security
Virus Assistant Performing Concentration Determining SecurityIt covers all the important concepts and has relevant templates which cater to your business needs. This complete deck has PPT slides on Virus Assistant Performing Concentration Determining Security with well suited graphics and subject driven content. This deck consists of total of twelve slides. All templates are completely editable for your convenience. You can change the colour, text and font size of these slides. You can add or delete the content as per your requirement. Get access to this professionally designed complete deck presentation by clicking the download button below.
-
 Overview And Features To Determine Security Token Offerings Security Token Offerings BCT SS
Overview And Features To Determine Security Token Offerings Security Token Offerings BCT SSThe following slide depicts brief introduction of security token offerings STOs along with some features to determine that particular token is security. It includes elements such as ownership or stake of assets, investment of money, expectations of profits, etc. Introducing Overview And Features To Determine Security Token Offerings Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Showcases Ownership, Security Regulations, Overview, using this template. Grab it now to reap its full benefits.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
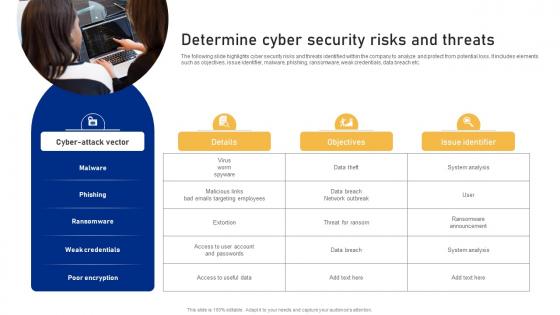 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Creating Cyber Security Awareness
Determine Cyber Security Risks And Threats Creating Cyber Security AwarenessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Human Errors, Factor Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats
Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Deliver an outstanding presentation on the topic using this Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Process To Determine Adequate Cyber Security Control
Process To Determine Adequate Cyber Security ControlThis slide represents the process to identifying adequate cyber security control for business to prevent online threats and implement necessary steps. It includes various steps such as evaluate size of the company, identify scope of IT infrastructure, etc. Presenting our set of slides with Process To Determine Adequate Cyber Security Control This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Scope Of It Infrastructure, Evaluate Size Of Company, Investment In Cyber Security
-
 Overview And Features To Determine Security Token Ultimate Guide Smart BCT SS V
Overview And Features To Determine Security Token Ultimate Guide Smart BCT SS VThe following slide depicts brief introduction of security token offerings STOs along with some features to determine that particular token is security. It includes elements such as ownership or stake of assets, investment of money, expectations of profits, etc. Deliver an outstanding presentation on the topic using this Overview And Features To Determine Security Token Ultimate Guide Smart BCT SS V. Dispense information and present a thorough explanation of Security, Common Enterprise, Expectation Profits using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure video sharing platform investor funding elevator determine potential market size online video hosting
Secure video sharing platform investor funding elevator determine potential market size online video hostingThis slide caters details about potential market size of video hosting platform with affordability to mass video production and accessibility of broadband internet to critical masses as video delivery platform. Deliver an outstanding presentation on the topic using this Secure Video Sharing Platform Investor Funding Elevator Determine Potential Market Size Online Video Hosting. Dispense information and present a thorough explanation of Determine, Potential, Accessibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Determining The Priority Requirements For Buying Iot Products
Information Security Program Determining The Priority Requirements For Buying Iot ProductsThis slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Present the topic in a bit more detail with this Information Security Program Determining The Priority Requirements For Buying Iot Products. Use it as a tool for discussion and navigation on Requirements, Products, Determining. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining The Priority A Risk Based Approach To Cyber Security
Determining The Priority A Risk Based Approach To Cyber SecurityThis slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility.Deliver an outstanding presentation on the topic using this Determining The Priority A Risk Based Approach To Cyber Security Dispense information and present a thorough explanation of Companies Are Starting, Relationships And Product, Development Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Impact Of Effective Mobile Android Device Security Management
Determine Impact Of Effective Mobile Android Device Security ManagementThis slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. Deliver an outstanding presentation on the topic using this Determine Impact Of Effective Mobile Android Device Security Management. Dispense information and present a thorough explanation of Malwares Samples, Data Breaches, Device Management Solution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Standard Mobile Android Device Security Management
Determine Standard Mobile Android Device Security ManagementThis slide provides information regarding essential standard mobile device management components terms of asset management module, security management module, kiosk module. Introducing Determine Standard Mobile Android Device Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Asset Management Module, Kiosk Module, Security Management Module, using this template. Grab it now to reap its full benefits.
-
 Determining The Actors Behind Building A Security Awareness Program
Determining The Actors Behind Building A Security Awareness ProgramThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver an outstanding presentation on the topic using this Determining The Actors Behind Building A Security Awareness Program. Dispense information and present a thorough explanation of Foreign Government, Malicious Insiders, Significant Cyber Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness
Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security AwarenessThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness. Use it as a tool for discussion and navigation on Determining The Actors, Behind Most Significant, Cyber Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Incident Response Playbook Determining The Ransom Payment Paid By Organizations Over Time
Security Incident Response Playbook Determining The Ransom Payment Paid By Organizations Over TimeFollowing graphical slide shows the amount of ransom paid by organizations over the last two years. Graph indicates that ransom payments appear to have stabilized as a result of effective incident response approaches. Deliver an outstanding presentation on the topic using this Security Incident Response Playbook Determining The Ransom Payment Paid By Organizations Over Time. Dispense information and present a thorough explanation of Determining, Organizations, Approaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Current Scenario Of Mobile Android Device Security Management
Determine Current Scenario Of Mobile Android Device Security ManagementThis slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. Present the topic in a bit more detail with this Determine Current Scenario Of Mobile Android Device Security Management. Use it as a tool for discussion and navigation on Determine Current Scenario, Mobile Devices Usage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Conducting Security Awareness
Determining The Actors Behind Most Significant Cyber Attack Conducting Security AwarenessThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver an outstanding presentation on the topic using this Determining The Actors Behind Most Significant Cyber Attack Conducting Security Awareness. Dispense information and present a thorough explanation of Online Criminals, Foreign Government Officials, Malicious Insiders using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Current Scenario Of Mobile Devices Usage Enterprise Mobile Security For On Device
Determine Current Scenario Of Mobile Devices Usage Enterprise Mobile Security For On DeviceThis slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device.Present the topic in a bit more detail with this Determine Current Scenario Of Mobile Devices Usage Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Determine Frequency, Employees Consider, Percentage Device. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Impact Of Effective Mobile Nterprise Mobile Security For On Device
Determine Impact Of Effective Mobile Nterprise Mobile Security For On DeviceThis slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter.Deliver an outstanding presentation on the topic using this Determine Impact Of Effective Mobile Nterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Records Exposed, Malwares Samples, Devices Workplace using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Standard Mobile Device Management Enterprise Mobile Security For On Device
Determine Standard Mobile Device Management Enterprise Mobile Security For On DeviceThis slide provides information regarding essential standard mobile device management components terms of central management console, registry.Introducing Determine Standard Mobile Device Management Enterprise Mobile Security For On Device to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Components Comprise, Management Console, Provide Performance, using this template. Grab it now to reap its full benefits.
-
 Determining The Actors Behind Most Significant Implementing Security Awareness Training
Determining The Actors Behind Most Significant Implementing Security Awareness TrainingThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Current Scenario Of Unified Endpoint Security
Determine Current Scenario Of Unified Endpoint SecurityThis slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. Present the topic in a bit more detail with this Determine Current Scenario Of Unified Endpoint Security. Use it as a tool for discussion and navigation on Determine Frequency, Employees Consider, Employee Consider. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Standard Mobile Device Management Components Unified Endpoint Security
Determine Standard Mobile Device Management Components Unified Endpoint SecurityThis slide provides information regarding essential standard mobile device management components terms of central management console, registry.Increase audience engagement and knowledge by dispensing information using Determine Standard Mobile Device Management Components Unified Endpoint Security. This template helps you present information on two stages. You can also present information on Components Comprise, Devices Workplace, Provide Performance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing Performance Indicators To Determine Security Strategic Organizational Security Plan
Addressing Performance Indicators To Determine Security Strategic Organizational Security PlanThis slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Deliver an outstanding presentation on the topic using this Addressing Performance Indicators To Determine Security Strategic Organizational Security Plan. Dispense information and present a thorough explanation of Incidents, Offender Management, Risk Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security
Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Deliver an outstanding presentation on the topic using this Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Exploitation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine established security centre overview key initiatives for project safety it
Determine established security centre overview key initiatives for project safety itThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an outstanding presentation on the topic using this Determine Established Security Centre Overview Key Initiatives For Project Safety It. Dispense information and present a thorough explanation of Functional Business, Security, External Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine role of security centre to ensure project safety key initiatives for project safety it
Determine role of security centre to ensure project safety key initiatives for project safety itThis slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Present the topic in a bit more detail with this Determine Role Of Security Centre To Ensure Project Safety Key Initiatives For Project Safety It. Use it as a tool for discussion and navigation on Organizational, System, Projects, Security, Analysts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine established security centre overview project safety management it
Determine established security centre overview project safety management itThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Present the topic in a bit more detail with this Determine Established Security Centre Overview Project Safety Management It. Use it as a tool for discussion and navigation on Functional Business, Security, Management, Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine role of security centre to ensure project safety project safety management it
Determine role of security centre to ensure project safety project safety management itThis slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Present the topic in a bit more detail with this Determine Role Of Security Centre To Ensure Project Safety Project Safety Management It. Use it as a tool for discussion and navigation on Organizational, System, Security, Team, Analysts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure video sharing platform investor determine profitable business model of online video hosting platform
Secure video sharing platform investor determine profitable business model of online video hosting platformThis slide caters details about profitable business model for video hosting platform by addressing its key partners, value propositions, revenue streams, etc. Deliver an outstanding presentation on the topic using this Secure Video Sharing Platform Investor Determine Profitable Business Model Of Online Video Hosting Platform. Dispense information and present a thorough explanation of Profitable, Business, Revenue using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace determine role of security centre in firm
Implementing advanced analytics system at workplace determine role of security centre in firmThis slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Determine Role Of Security Centre In Firm. Use it as a tool for discussion and navigation on Determine Role Of Security Centre In Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine sequence phases for managing critical threat vulnerabilities and security threats
Determine sequence phases for managing critical threat vulnerabilities and security threatsThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Increase audience engagement and knowledge by dispensing information using Determine Sequence Phases For Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on four stages. You can also present information on Installation, Command And Control, Actions And Objectives, Covering Tracks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine several threat actors managing critical threat vulnerabilities and security threats
Determine several threat actors managing critical threat vulnerabilities and security threatsThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an outstanding presentation on the topic using this Determine Several Threat Actors Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Determine Several Threat Actors Profile using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine staff training schedule managing critical threat vulnerabilities and security threats
Determine staff training schedule managing critical threat vulnerabilities and security threatsThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Introducing Determine Staff Training Schedule Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Advanced Software Training, Training Module, using this template. Grab it now to reap its full benefits.
-
 Determine threat management managing critical threat vulnerabilities and security threats
Determine threat management managing critical threat vulnerabilities and security threatsThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Increase audience engagement and knowledge by dispensing information using Determine Threat Management Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on two stages. You can also present information on Determine Threat Management Team Structure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine threat scenario managing critical threat vulnerabilities and security threats
Determine threat scenario managing critical threat vulnerabilities and security threatsThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Present the topic in a bit more detail with this Determine Threat Scenario Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Threat Campaign, Actions And Objectives, Covering Tracks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing critical threat vulnerabilities and security threats determine sequence phases
Managing critical threat vulnerabilities and security threats determine sequence phasesThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Managing Critical Threat Vulnerabilities And Security Threats Determine Sequence Phases to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Delivery, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Corporate security management determine sequence phases for threat attack
Corporate security management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Corporate Security Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack actions corporate security management
Determine sequence phases for threat attack actions corporate security managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Actions Corporate Security Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Determine several threat actors profile corporate security management
Determine several threat actors profile corporate security managementThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Corporate Security Management. Use it as a tool for discussion and navigation on Determine Several Threat Actors Profile. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine staff training schedule for skills enhancement corporate security management
Determine staff training schedule for skills enhancement corporate security managementThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Introducing Determine Staff Training Schedule For Skills Enhancement Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Advanced Software Training, Advanced Skills Training, Training Module, using this template. Grab it now to reap its full benefits.
-
 Determine threat management team structure corporate security management
Determine threat management team structure corporate security managementThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Increase audience engagement and knowledge by dispensing information using Determine Threat Management Team Structure Corporate Security Management. This template helps you present information on two stages. You can also present information on Legal Advisor, HR Advisor, Medical Advisor, Security Manager using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine threat scenario analysis corporate security management
Determine threat scenario analysis corporate security managementThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Corporate Security Management. Dispense information and present a thorough explanation of Command And Control, Actions And Objectives, Reconnaissance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Overview Of Established Security Centre Enabling It Intelligence Framework
Determine Overview Of Established Security Centre Enabling It Intelligence FrameworkThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system.Introducing Determine Overview Of Established Security Centre Enabling It Intelligence Framework to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Functional Business, Management Staff, Steering Committee using this template. Grab it now to reap its full benefits.
-
 Determine Role Of Security Centre In Firm Enabling It Intelligence Framework
Determine Role Of Security Centre In Firm Enabling It Intelligence FrameworkThis slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation.Present the topic in a bit more detail with this Determine Role Of Security Centre In Firm Enabling It Intelligence Framework Use it as a tool for discussion and navigation on Threats And Actual, Organizational System, Security Analysts This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Overview Of Established Security Centre Building Business Analytics Architecture
Determine Overview Of Established Security Centre Building Business Analytics ArchitectureThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Present the topic in a bit more detail with this Determine Overview Of Established Security Centre Building Business Analytics Architecture. Use it as a tool for discussion and navigation on Functional Business Units, Security Centre, External Systems, Internal Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Role Of Security Centre In Firm Building Business Analytics Architecture
Determine Role Of Security Centre In Firm Building Business Analytics ArchitectureThis slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an outstanding presentation on the topic using this Determine Role Of Security Centre In Firm Building Business Analytics Architecture. Dispense information and present a thorough explanation of Before Security, After Security, Towards Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Performance indicators to determine security building organizational security strategy plan
Performance indicators to determine security building organizational security strategy planThis slide provides information about performance indicators in order to determine security standards at workplace in terms of staff and customer satisfaction, financial and staff. Deliver an outstanding presentation on the topic using this Performance Indicators To Determine Security Building Organizational Security Strategy Plan. Dispense information and present a thorough explanation of Performance, Satisfaction, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management determine sequence phases for threat attack
Cyber security risk management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Exploitation, Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management determine several threat actors profile
Cyber security risk management determine several threat actors profileThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Determine Several Threat Actors Profile. Dispense information and present a thorough explanation of Cyber Criminal, Targeted Asset, Objective using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management determine staff training schedule for skills
Cyber security risk management determine staff training schedule for skillsThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Staff Training Schedule For Skills. This template helps you present information on three stages. You can also present information on Advanced Software Training, Advanced Skills Training, Training Module, Self Assessment Tools using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management determine threat management team
Cyber security risk management determine threat management teamThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Introducing Cyber Security Risk Management Determine Threat Management Team to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Management Head, Security Manager, Crisis Management Advisor, Medical Advisor, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management determine threat scenario analysis
Cyber security risk management determine threat scenario analysisThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Threat Scenario Analysis. This template helps you present information on two stages. You can also present information on Threat Scenario, Threat Campaign, Exploitation, Command And Control, Actions And Objectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack contd cyber security risk management
Determine sequence phases for threat attack contd cyber security risk managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Contd Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Building organizational security strategy plan addressing performance indicators to determine
Building organizational security strategy plan addressing performance indicators to determineThis slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Addressing Performance Indicators To Determine. Use it as a tool for discussion and navigation on Performance, Information, Assessments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan determine department wise incident reporting
Building organizational security strategy plan determine department wise incident reportingThis slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Determine Department Wise Incident Reporting. Dispense information and present a thorough explanation of Determine Department Wise Incident Reporting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building organizational security strategy plan determine overview of established security centre
Building organizational security strategy plan determine overview of established security centreThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Determine Overview Of Established Security Centre. Use it as a tool for discussion and navigation on Overview, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan determine security policy framework at workplace
Building organizational security strategy plan determine security policy framework at workplaceThis slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Determine Security Policy Framework At Workplace. Use it as a tool for discussion and navigation on Framework, Workplace, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan determine staff training schedule for skills enhancement
Building organizational security strategy plan determine staff training schedule for skills enhancementThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Determine Staff Training Schedule For Skills Enhancement. Dispense information and present a thorough explanation of Schedule, Enhancement , Development using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




