Powerpoint Templates and Google slides for Data Security Tools
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Tools Processing Model Visualization Layer Security Segment
Data Tools Processing Model Visualization Layer Security SegmentDeliver a lucid presentation by utilizing this Data Tools Processing Model Visualization Layer Security Segment. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Processing Model, Visualization Layer, Security Segment. All the twenty nine slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Risk Management Maturity Model Information Security Data Technology Culture
Risk Management Maturity Model Information Security Data Technology CultureDeliver a credible and compelling presentation by deploying this Risk Management Maturity Model Information Security Data Technology Culture. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty eight slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Risk Management Maturity Model Information Security Data Technology Culture PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Benefits Of Blockchain Technology For Data Security Training Ppt
Benefits Of Blockchain Technology For Data Security Training PptPresenting Benefits of Blockchain Technology for Data Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Enterprise data security tools ppt powerpoint presentation icon graphics template cpb
Enterprise data security tools ppt powerpoint presentation icon graphics template cpbPresenting Enterprise Data Security Tools Ppt Powerpoint Presentation Icon Graphics Template Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Enterprise Data Security Tools. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data Breach Prevention Data Breach Prevention Services Provided By Security Tools
Data Breach Prevention Data Breach Prevention Services Provided By Security ToolsThis slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Present the topic in a bit more detail with this Data Breach Prevention Data Breach Prevention Services Provided By Security Tools. Use it as a tool for discussion and navigation on Data Breach Prevention, Services Provided By Security Tools, Obfuscates Sensitive Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Encryption Technology Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Encryption Technology Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Data Security Encryption Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Encryption Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It
Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role of HTTPS in encrypting web communication and use of the Secure Sockets Layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake. Deliver an outstanding presentation on the topic using this Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Technology, Asymmetric, Symmetric using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
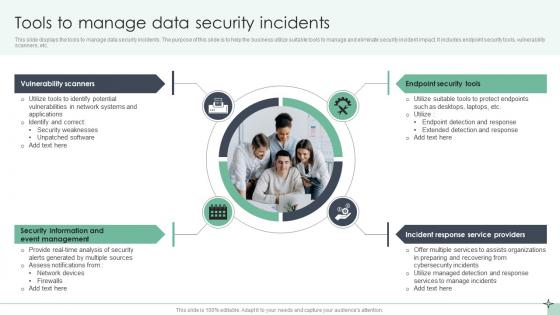 Tools To Manage Data Security Incidents
Tools To Manage Data Security IncidentsThis slide displays the tools to manage data security incidents. The purpose of this slide is to help the business utilize suitable tools to manage and eliminate security incident impact. It includes endpoint security tools, vulnerability scanners, etc. Presenting our set of slides with Tools To Manage Data Security Incidents. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability Scanners, Endpoint Security Tools, Incident Response.
-
 Data Protection Server Security Technology Icon
Data Protection Server Security Technology IconPresenting our set of slides with Data Protection Server Security Technology Icon. This exhibits information on threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Server Security Technology.
-
 Technology Project Goals Icon To Strength Data Security
Technology Project Goals Icon To Strength Data SecurityPresenting our set of slides with Technology Project Goals Icon To Strength Data Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Technology, Goals, Strength.
-
 Big Data Security Technology To Enhance Systems Efficiency
Big Data Security Technology To Enhance Systems EfficiencyThis slide represents big data security technology which enhances security of non relational databases and boosts endpoint security. It includes big data security technology to enhance systems efficiency such as encryption, user access control etc. Presenting our set of slides with name Big Data Security Technology To Enhance Systems Efficiency. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Centralized Key Management, Physical Security, User Access Control, Encryption.
-
 Checklist For Holistic Data Security And Privacy In Big Data Technology
Checklist For Holistic Data Security And Privacy In Big Data TechnologyThis slide represents checklist for data security and privacy in big data technology which assists to prevent unauthorized access and provides safeguard against cyber threat. It includes key steps such as secure and monitor, find and classify, etc. Introducing our Checklist For Holistic Data Security And Privacy In Big Data Technology set of slides. The topics discussed in these slides are Find And Classify, Secure And Monitor, Harden, Protect And Remain Vigilant. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Privacy And Security Issues Faced In Big Data Technology
Privacy And Security Issues Faced In Big Data TechnologyThis slide represents privacy and security issues faced in big data technology which provides greater insight into data and assists to make better business decisions. It includes privacy and security issues faced in big data technology such as secure computations, access control, etc. Presenting our set of slides with name Privacy And Security Issues Faced In Big Data Technology. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Computations, Access Control, Protecting Data And Transaction Logs, Real Time Security Monitoring.
-
 Comparative Assessment For Data Security Management Tools
Comparative Assessment For Data Security Management ToolsThis slide represents the comparative analysis assisting businesses to choose correct tools to enhance data security management. It includes various tools such as oracle data safe, satori data security platform, etc. Introducing our Comparative Assessment For Data Security Management Tools set of slides. The topics discussed in these slides are Oracle Data Safe, Data Security Platform, Manager For Databases. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies And Tools To Enhance Big Data Security Management
Strategies And Tools To Enhance Big Data Security ManagementThis slide showcases the strategies and tools helping companies to effectively manage and monitor big data security from cyber threats. It includes strategies such as cloud security monitoring, centralized key management, incident investigation, etc. Introducing our Strategies And Tools To Enhance Big Data Security Management set of slides. The topics discussed in these slides are Cloud Security Monitoring, Centralized Key Management, Network Traffic Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
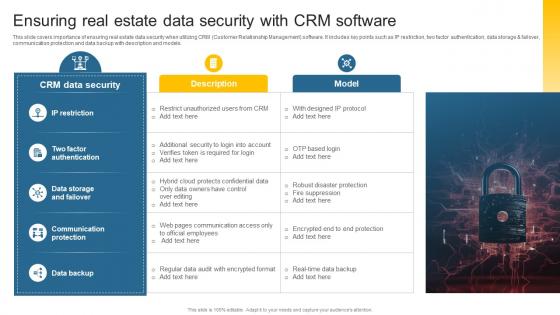 Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company
Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate CompanyThis slide covers importance of ensuring real estate data security when utilizing CRM Customer Relationship Management software. It includes key points such as IP restriction, two factor authentication, data storage and failover, communication protection and data backup with description and models. Introducing Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Storage And Failover, Communication Protection, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Comparison Analysis Of Data Masking Tools For Information Security
Comparison Analysis Of Data Masking Tools For Information SecurityThis slide represents comparison analysis of data masking tools that assist companies to enhance their sensitive information security. It includes various tools such as K2View data masking, DATPROF data masking tool, Oracle data masking and subsetting, etc. Presenting our well structured Comparison Analysis Of Data Masking Tools For Information Security. The topics discussed in this slide are Virtualization, Synthetic Data Generation, Tokenization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities
Tokenization For Improved Data Security Data Tokenization Tools Key CapabilitiesPresent the topic in a bit more detail with this Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities. Use it as a tool for discussion and navigation on Data Tokenization Tools, Key Capabilities, Operational And Analytical Purposes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology
Tokenization For Improved Data Security Difference Between Tokenization And Masking TechnologyThis slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology. Dispense information and present a thorough explanation of Data Preservation, Masking Technology, Maintains Data Format using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology
Tokenization For Improved Data Security Future Trends Of Tokenization On Business And TechnologyThis slide highlights the anticipated developments in tokenizations impact on the realms of business and technology. The purpose of this slide is to outline the future trends of tokenization. Introducing Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Anticipated Developments, Business And Technology, Future Trends Of Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology
Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain TechnologyThis slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A plus, S regulations, etc. Introducing Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Regulations Of Security Tokens, Blockchain Technology, Data Security, using this template. Grab it now to reap its full benefits.
-
 Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS
Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SSIncrease audience engagement and knowledge by dispensing information using Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS. This template helps you present information on three stages. You can also present information on Security Protocols, Authorized Access, Responsible Data Use using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint data loss prevention DLP tool process. It includes stages such as identification, assistance and tracking of endpoint data.Increase audience engagement and knowledge by dispensing information using Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information three stages. You can also present information on Identify, Assist, Track, Potential Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IOT Security System Tools For Data Protection
IOT Security System Tools For Data ProtectionThis slide showcases methods to secure IoT security systems. It includes digital certificates, network and application programming interface security. Presenting our set of slides with name IOT Security System Tools For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security, API Security, Digital Certificates.
-
 IOT Technology Data Security Icon
IOT Technology Data Security IconPresenting our set of slides with name IOT Technology Data Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IoT Technology, Data Security.
-
 Information Technology Security Data Backup For Sensitive Information
Information Technology Security Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Information Technology Security Data Backup For Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Prepare Data Backup For Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Dispose Data And Equipment Properly
Information Technology Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Introducing Information Technology Security Dispose Data And Equipment Properly to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Dispose Data And Equipment Properly, using this template. Grab it now to reap its full benefits.
-
 Security Of Data And Networks In Edge Computing Distributed Information Technology
Security Of Data And Networks In Edge Computing Distributed Information TechnologyThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Deliver an outstanding presentation on the topic using this Security Of Data And Networks In Edge Computing Distributed Information Technology. Dispense information and present a thorough explanation of Security Of Data And Networks In Edge Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Data Protection Tools Used In Cloud Security
Cloud Data Protection Tools Used In Cloud SecurityThis slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Increase audience engagement and knowledge by dispensing information using Cloud Data Protection Tools Used In Cloud Security. This template helps you present information on one stage. You can also present information on Cloud Solutions, Security, Networks using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Icon Showing Data Security Through Blockchain Technology In Supply Chain
Icon Showing Data Security Through Blockchain Technology In Supply ChainPresenting our well structured Icon Showing Data Security Through Blockchain Technology In Supply Chain. The topics discussed in this slide are Icon Showing Data Security, Blockchain Technology, Supply Chain. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of Data Masking Security Technology
Applications Of Data Masking Security TechnologyThis slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Introducing our premium set of slides with Applications Of Data Masking Security Technology. Elucidate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Date Aging, Encryption, Scrambling, Nulling Out, Substitution. So download instantly and tailor it with your information.
-
 Business Data Encryption Security Technology
Business Data Encryption Security TechnologyThis slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting our set of slides with name Business Data Encryption Security Technology. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Privacy, Authentication, Regulatory Compliance, Security.
-
 Firewall Data Network Security Technology
Firewall Data Network Security TechnologyThe below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Introducing our premium set of slides with Firewall Data Network Security Technology. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Packet Filtering, Proxy Service, UTM, Stateful Inspection, Next Gen Firewall. So download instantly and tailor it with your information.
-
 Data Security Governance Tool Assessment Matrix
Data Security Governance Tool Assessment MatrixThis slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Introducing our premium set of slides with Data Security Governance Tool Assessment Matrix. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Intelligence, Advanced Data Governance. So download instantly and tailor it with your information.
-
 Blockchain Technology Impact On Data Security
Blockchain Technology Impact On Data SecurityThis slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking. Introducing our premium set of slides with Blockchain Technology Impact On Data Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption And Validation, Decentralized Data Security, Difficulties In Hacking. So download instantly and tailor it with your information.
-
 Data Transfer Security Using Blockchain Technology Icon
Data Transfer Security Using Blockchain Technology IconIntroducing our premium set of slides with Data Transfer Security Using Blockchain Technology Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Transfer, Security Using, Blockchain Technology, Icon. So download instantly and tailor it with your information.
-
 Usb security shield and tools for data safety ppt slides
Usb security shield and tools for data safety ppt slidesPresenting usb security shield and tools for data safety ppt slides. This is a usb security shield and tools for data safety ppt slides. This is a two stage process. The stages in this process are security.
-
 Mobile apps and data security powerpoint slide ideas
Mobile apps and data security powerpoint slide ideasPresenting mobile apps and data security PowerPoint slide ideas PPT slide. Easy to download link. Time saviour. Impressive picture quality and visuals. Ease of inclusion and exclusion of content as per the need. Uniqueness in idea and presentation. High-resolution visuals. Compatibility with trending software and formats. Can very easily be used by business professionals and students as well for the winter season and snowy time trending PowerPoint presentations.
-
 Technology infrastructure data security review ppt powerpoint presentation pictures cpb
Technology infrastructure data security review ppt powerpoint presentation pictures cpbPresenting this set of slides with name Technology Infrastructure Data Security Review Ppt Powerpoint Presentation Pictures Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Technology Infrastructure Data Security Review to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Key emerging security technology for data protection
Key emerging security technology for data protectionPresenting this set of slides with name Key Emerging Security Technology For Data Protection. This is a five stage process. The stages in this process are Hardware Authentication, User Behavior Analytics, Data Loss Prevention, Deep Learning, Cloud. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Network security technology for data privacy
Network security technology for data privacyPresenting this set of slides with name Network Security Technology For Data Privacy. This is a two stage process. The stages in this process are Network Security Technology For Data Privacy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Woman using vpn technology for data security
Woman using vpn technology for data securityPresenting this set of slides with name Woman Using VPN Technology For Data Security. This is a three stage process. The stages in this process are Woman Using VPN Technology For Data Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Icon showing technology challenge of data security
Icon showing technology challenge of data securityIntroducing our Icon Showing Technology Challenge Of Data Security set of slides. The topics discussed in these slides are Icon Showing, Technology Challenge, Data Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security technology ppt powerpoint presentation summary graphics example cpb
Data security technology ppt powerpoint presentation summary graphics example cpbPresenting our Data Security Technology Ppt Powerpoint Presentation Summary Graphics Example Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Data Security Technology This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data management security tools with major segments
Data management security tools with major segmentsThis slide showcase data management security tools with major segments. It includes major outcomes such as-privacy design and development, beardless identity administration etc. Presenting our well-structured Data Management Security Tools With Major Segments. The topics discussed in this slide are Security Segment, Expected Enterprise Outcomes, Required Security Controls. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.



