Powerpoint Templates and Google slides for Data And Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Data Migration Security Risks And Solutions
Cloud Data Migration Security Risks And SolutionsThe below slide highlights the multiple security risks associated with cloud data migration along with the potential solutions to eliminate them. The various risks mentioned are unauthorized access, data breaches, weak data encryption, etc. Introducing our Cloud Data Migration Security Risks And Solutions set of slides. The topics discussed in these slides are Unauthorized Access, Data Breaches, Weak Data Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS
Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SSIncrease audience engagement and knowledge by dispensing information using Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS. This template helps you present information on three stages. You can also present information on Security Protocols, Authorized Access, Responsible Data Use using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pam Framework For Optimizing Cyber Security And Data Protection
Pam Framework For Optimizing Cyber Security And Data ProtectionThis slide represents framework that assists companies to implement PAM cybersecurity to enhance their data protection and risk management. It includes various components such as use cases, defining requirements, architecture development, etc. Presenting our well structured Pam Framework For Optimizing Cyber Security And Data Protection. The topics discussed in this slide are Determine Use Cases, Define Requirements, Develop Architecture. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Email Security Best Practices Email Data Protection Overview And Features
Email Security Best Practices Email Data Protection Overview And FeaturesThe purpose of this slide is to discuss the Email Data Protection EDP solutions of email security. This slide highlights the features of Email Data Protection EDP , such as content-based email control, recipient authentication, data anonymization, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Data Protection Overview And Features. Use it as a tool for discussion and navigation on Content-Based Email Control, Recipient Authentication, Two-Factor Authentication, Data Anonymization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Managing Big Data Governance And Security With AWS
Icon For Managing Big Data Governance And Security With AWSPresenting our set of slides with Icon For Managing Big Data Governance And Security With AWS. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Managing Big Data, Governance And Security, AWS.
-
 Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents the importance of data security in cloud virtualization. With a vibrant design, it visually conveys the significance of protecting sensitive information in a virtual environment. Use it to enhance your presentations on cloud computing and data protection.
-
 Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect addition to your presentation on Cloud virtualization data security. With a sleek design and clear imagery, it effectively represents the topic of data security in the cloud. Use it to enhance your slides and make a lasting impression on your audience.
-
 Data Protection Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your incident response capabilities with our vibrant PowerPoint icon, representing the power of EDR solutions. With its eye-catching color and design, this icon is the perfect addition to your presentation on facilitating incident response trends. Grab your audiences attention and showcase the importance of EDR in handling security incidents.
-
 Data Protection Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your incident response strategy with our Monotone PowerPoint icon. This sleek and modern design represents the power of EDR solutions in facilitating efficient and effective response to security incidents. Perfect for presentations on cybersecurity and risk management, this icon will elevate your content and captivate your audience.
-
 Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on cyber risk management with our vibrant Computer Security PowerPoint icon. This eye-catching icon features a lock symbol in bold colors, representing the importance of safeguarding your data and systems. Perfect for showcasing the importance of cyber security in todays digital age.
-
 Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the importance of computer security in cyber risk management. It is a visual representation of the need for safeguarding sensitive information and protecting against potential cyber threats. Use this icon to enhance presentations on cyber security and emphasize the significance of risk management in the digital world.
-
 Data Security And Privacy Survey Overview Report Survey SS
Data Security And Privacy Survey Overview Report Survey SSFollowing slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Presenting our well structured Data Security And Privacy Survey Overview Report Survey SS. The topics discussed in this slide are Data Security Tools, Budget Allocated, Software Solutions. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Framework for big data control and security presentation outline
Framework for big data control and security presentation outlinePresenting framework for big data control and security presentation outline. This is a framework for big data control and security presentation outline. This is a four stage process. The stages in this process are define, data discovery, data classification, dissect, data intelligence, data analytics.
-
 Model of governance and security of big data diagram ppt presentations
Model of governance and security of big data diagram ppt presentationsPresenting model of governance and security of big data diagram ppt presentations. This is a model of governance and security of big data diagram ppt presentations. This is a three stage process. The stages in this process are confidentiality, integrity, availability, security model.
-
 Data Center Dashboard Snapshot With Security And User Assessment
Data Center Dashboard Snapshot With Security And User AssessmentIntroducing our Data Center Dashboard Snapshot With Security And User Assessment set of slides. The topics discussed in these slides are Security Assessment, User Assessment, Data Discovery. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Dashboard For Data Security Risk Assessment And Management Plan For Information Security
Dashboard For Data Security Risk Assessment And Management Plan For Information SecurityThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Deliver an outstanding presentation on the topic using this Dashboard For Data Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Dashboard, Management, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting
Risk Assessment And Management Plan For Information Security Information And Data Breach ImpactingDeliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting. Dispense information and present a thorough explanation of Information, Business, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information And Data Breach Impacting Customer Loyalty Information Security Risk Management
Information And Data Breach Impacting Customer Loyalty Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Information And Data Breach Impacting Customer Loyalty Information Security Risk Management. Dispense information and present a thorough explanation of Information, Data Breach Impacting, Customer Loyalty using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty
Information System Security And Risk Administration Information And Data Breach Impacting Customer LoyaltyDeliver an outstanding presentation on the topic using this Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty. Dispense information and present a thorough explanation of Business, Financial Data, Data Breach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information System Security And Risk Administration Plandashboard For Data Security Risk Management
Information System Security And Risk Administration Plandashboard For Data Security Risk ManagementThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Present the topic in a bit more detail with this Information System Security And Risk Administration Plandashboard For Data Security Risk Management. Use it as a tool for discussion and navigation on Enterprise Risk, Risks By Objectives, Data Protection Findings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
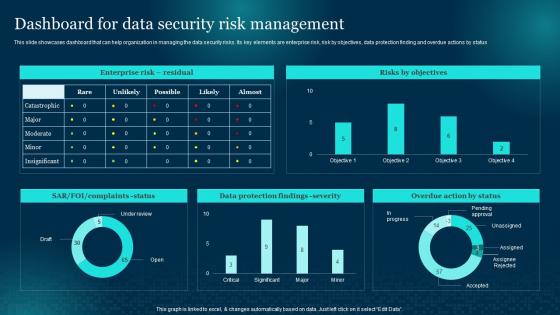 Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan
Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Present the topic in a bit more detail with this Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Dashboard, Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security
Consequences Of Data Breaches Faced By Organization Development And Implementation Of SecurityThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security. Dispense information and present a thorough explanation of Payment Card Fraud, Physical Loss, Insider Leak using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Top Vulnerable Industries To Cyber Security Threats And Data Breaches
Top Vulnerable Industries To Cyber Security Threats And Data BreachesThis slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Introducing our Top Vulnerable Industries To Cyber Security Threats And Data Breaches set of slides. The topics discussed in these slides are Government, Department. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Business Data Security And Privacy Assessment Survey Form Survey SS
Business Data Security And Privacy Assessment Survey Form Survey SSFollowing slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Introducing our Business Data Security And Privacy Assessment Survey Form Survey SS set of slides. The topics discussed in these slides are Security Tools Used, Allocated For Tools, Security Software Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon showcasing data availability security against risks and threats
Icon showcasing data availability security against risks and threatsPresenting our set of slides with Icon Showcasing Data Availability Security Against Risks And Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Showcasing Data Availability Security Against Risks And Threats.
-
 Addressing internal and external sources of threat data corporate security management
Addressing internal and external sources of threat data corporate security managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Introducing Addressing Internal And External Sources Of Threat Data Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, using this template. Grab it now to reap its full benefits.
-
 Agenda for advanced security monitoring plan to remove cybersecurity threat and data infraction
Agenda for advanced security monitoring plan to remove cybersecurity threat and data infractionIncrease audience engagement and knowledge by dispensing information using Agenda For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. This template helps you present information on seven stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infraction
Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infractionIntroducing our well researched set of slides titled Icons Slide For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table of contents advanced security monitoring plan to remove cybersecurity threat and data infraction
Table of contents advanced security monitoring plan to remove cybersecurity threat and data infractionPresent the topic in a bit more detail with this Table Of Contents Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Tools To Be Implemented, Essential Elements Of Security Monitoring Plan, Cybersecurity Monitoring Best Practices To Be Followed By The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways through which security data can be compromised and measures to deal with them
Ways through which security data can be compromised and measures to deal with themThis slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Present the topic in a bit more detail with this Ways Through Which Security Data Can Be Compromised And Measures To Deal With Them. Use it as a tool for discussion and navigation on Supply Chain Attacks, Insider Attacks, External Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Dispose Data And Equipment Properly
Information Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Increase audience engagement and knowledge by dispensing information using Information Security Dispose Data And Equipment Properly. This template helps you present information on three stages. You can also present information on Dispose Data And Equipment Properly using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data center security and safety data center it ppt powerpoint presentation infographic template
Data center security and safety data center it ppt powerpoint presentation infographic templateThis slide represents the data center security and safety that includes physical security, climate control system, data backup system, data backup system, and backup power generator. Deliver an outstanding presentation on the topic using this Data Center Security And Safety Data Center It Ppt Powerpoint Presentation Infographic Template. Dispense information and present a thorough explanation of Control System, Physical Security, Network Operations Center, Client Privacy, Prevention System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing internal and external sources data cyber security risk management
Addressing internal and external sources data cyber security risk managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Data Cyber Security Risk Management. Dispense information and present a thorough explanation of Internal Sources, External Sources, Targeted Intelligence, Malware Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Dispose Data And Equipment Properly
Network Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Introducing Network Security Dispose Data And Equipment Properly to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Dispose Data And Equipment Properly, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Dispose Data And Equipment Properly
Information Technology Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Introducing Information Technology Security Dispose Data And Equipment Properly to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Dispose Data And Equipment Properly, using this template. Grab it now to reap its full benefits.
-
 Planning And Implementation Of Crm Software Securing Our Data With Crm
Planning And Implementation Of Crm Software Securing Our Data With CrmThis slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. Deliver an outstanding presentation on the topic using this Planning And Implementation Of Crm Software Securing Our Data With Crm. Dispense information and present a thorough explanation of User Role Based Security, Profile Based Security, Record Sharing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Our Data With Crm Planning And Implementation Of Crm Software
Securing Our Data With Crm Planning And Implementation Of Crm SoftwareThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Present the topic in a bit more detail with this Securing Our Data With Crm Planning And Implementation Of Crm Software. Use it as a tool for discussion and navigation on Securing Our Data With CRM. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Distributed computing security of data and networks in distributed computing
Distributed computing security of data and networks in distributed computingThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Present the topic in a bit more detail with this Distributed Computing Security Of Data And Networks In Distributed Computing. Use it as a tool for discussion and navigation on Element, Computing, Protection, System, Network, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Of Data And Networks In Edge Computing Distributed Information Technology
Security Of Data And Networks In Edge Computing Distributed Information TechnologyThis slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Deliver an outstanding presentation on the topic using this Security Of Data And Networks In Edge Computing Distributed Information Technology. Dispense information and present a thorough explanation of Security Of Data And Networks In Edge Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Information Security
Cloud Security Checklist Backup And Data Recovery Cloud Information SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Information Security This template helps you present information on five stages. You can also present information on Sensitive Information, Encode Sensitive, Encrypted Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Hybrid Blockchain Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Hybrid Blockchain Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Hybrid blockchain data security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Hybrid Blockchain Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Hybrid Blockchain Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Hybrid blockchain data security monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Mobile Data Security Authentication Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Data Security Authentication Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Mobile data security authentication colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Mobile Data Security Authentication Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Data Security Authentication Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Mobile data security authentication monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cloud Computing Security How Does Cloud Security Work Data Retention And Business
Cloud Computing Security How Does Cloud Security Work Data Retention And BusinessThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Data Retention And Business. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Testing And Maintenance, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Computing Security
Cloud Security Checklist Backup And Data Recovery Cloud Computing SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Computing Security. This template helps you present information on three stages. You can also present information on Cyber Attacks, Physical Location, Backup And Recovery Plans using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation gallery
Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation galleryThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Increase audience engagement and knowledge by dispensing information using Big Data And Its Types Security Of Information In Big Data Ppt PowerPoint Presentation gallery. This template helps you present information on two stages. You can also present information on Challenges, Solution, Data Collections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cyber data security protocols colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cyber Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cyber data security protocols monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data security protocols colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data security protocols monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Lock Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Lock Data Security Protocols Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Lock data security protocols colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Lock Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Lock Data Security Protocols Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Lock data security protocols monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Building Data Analytics And Cyber Security Strategy Framework
Building Data Analytics And Cyber Security Strategy FrameworkThis slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Introducing our premium set of slides with Building Data Analytics And Cyber Security Strategy Framework. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Collection, Data Normalization, Expansion. So download instantly and tailor it with your information.
-
 Data Security With Lock Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security With Lock Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data security with lock colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Security With Lock Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security With Lock Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data security with lock monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Mobile Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Mobile data security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Mobile Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Mobile data security monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Risk Assessment And Management Plan For Information Security Current Information And Data Security
Risk Assessment And Management Plan For Information Security Current Information And Data SecurityThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating Present the topic in a bit more detail with this Risk Assessment And Management Plan For Information Security Current Information And Data Security. Use it as a tool for discussion and navigation on Information, Capabilities, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Central Authority And Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Central Authority And Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Central authority and data security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.





