Powerpoint Templates and Google slides for Data Aggression
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Advanced security monitoring plan to remove cybersecurity threat and data infraction complete deck
Advanced security monitoring plan to remove cybersecurity threat and data infraction complete deckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fourty six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Proper data management in healthcare company to reduce cyber threats complete deck
Proper data management in healthcare company to reduce cyber threats complete deckEnthrall your audience with this Proper Data Management In Healthcare Company To Reduce Cyber Threats Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Effective security monitoring plan to eliminate cyber threats and data breaches complete deck
Effective security monitoring plan to eliminate cyber threats and data breaches complete deckEnthrall your audience with this Effective Security Monitoring Plan To Eliminate Cyber Threats And Data Breaches Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Implementing security management plan to reduce threats and protect sensitive company data complete deck
Implementing security management plan to reduce threats and protect sensitive company data complete deckThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Implementing Security Management Plan To Reduce Threats And Protect Sensitive Company Data Complete Deck and has templates with professional background images and relevant content. This deck consists of total of fourty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Data security it dashboard snapshot for threat tracking in data security
Data security it dashboard snapshot for threat tracking in data securityThis slide depicts the dashboard snapshot for threat tracking in data security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Data Security IT Dashboard For Threat Tracking In Data Security. Dispense information and present a thorough explanation of Monthly Threat Status, Current Risk Status, Threats Based On Role, Threats Owners, Risk Threats, Threat Report using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threat Analysis With Data Encryption
Cyber Threat Analysis With Data EncryptionThe purpose of this slide is to highlight how cyber threat analysis with data encryption fortifies security. It offers proactive insights into potential threats, ensuring a robust defense, and safeguarding sensitive information in the evolving landscape of cyber threats. Introducing our Cyber Threat Analysis With Data Encryption set of slides. The topics discussed in these slides are Cybersecurity Threat, Budget Constraints, Inadequate Training And Awareness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
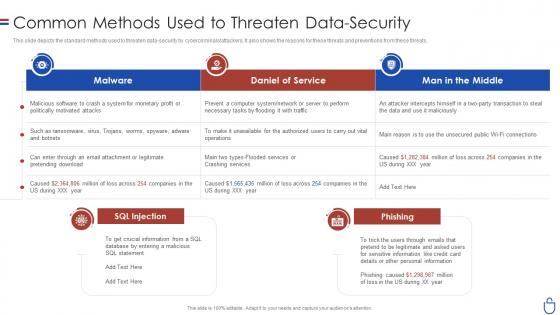 Data security it common methods used to threaten data security
Data security it common methods used to threaten data securityThis slide depicts the standard methods used to threaten data-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Present the topic in a bit more detail with this Data Security IT Common Methods Used To Threaten Data Security. Use it as a tool for discussion and navigation on Malware, Daniel Service, Man Middle, SQL Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
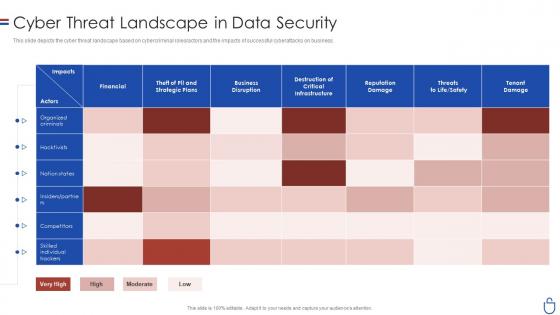 Data security it cyber threat landscape in data security
Data security it cyber threat landscape in data securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Data Security IT Cyber Threat Landscape In Data Security. Use it as a tool for discussion and navigation on Financial, Business Disruption, Reputation Damage, Tenant Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it latest threats in data security ppt slides background designs
Data security it latest threats in data security ppt slides background designsThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Increase audience engagement and knowledge by dispensing information using Data Security IT Latest Threats In Data Security Ppt Slides Background Designs. This template helps you present information on three stages. You can also present information on Dridex Malware, Romance Scams, Emotet Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data security it types of threats in data security ppt slides graphic tips
Data security it types of threats in data security ppt slides graphic tipsThis slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Increase audience engagement and knowledge by dispensing information using Data Security IT Types Of Threats In Data Security Ppt Slides Graphic Tips. This template helps you present information on three stages. You can also present information on Cyber Crime, Cyber Terrorism, Cyber Attack, Cause Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Preventive Measures For Data Theft Threats
Preventive Measures For Data Theft ThreatsThis slide covers security threats and preventive actions. The purpose of this template is to educate on various data theft methods and provide actionable steps to mitigate risks. It includes thumb sucking, data leakage, phishing attacks, data interception, and insider data theft. Presenting our set of slides with Preventive Measures For Data Theft Threats. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing, Interception, Data.
-
 Managing Information Security Threats To Enhance Data Protection
Managing Information Security Threats To Enhance Data ProtectionThis slide represents strategies that help businesses mitigate threats of information security management and reduce data loss incidents. It includes various threats such as social media attacks, social engineering, lack of encryption, etc. Presenting our well structured Managing Information Security Threats To Enhance Data Protection. The topics discussed in this slide are Social Media Attacks, Social Engineering, Malware On Endpoints. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Gathering And Analyzing Threat Intelligence Data Through ChatGPT Leveraging ChatGPT AI SS V
Gathering And Analyzing Threat Intelligence Data Through ChatGPT Leveraging ChatGPT AI SS VThis slide showcases various data sources that are leveraged by ChatGPT for threat intelligence to tack cyber attack on organization. Various data sources for threat intelligence are security blogs, social media and security forums. Introducing Gathering And Analyzing Threat Intelligence Data Through ChatGPT Leveraging ChatGPT AI SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Security Blogs, Security Forums, Social Media using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS V
Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS VThe following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Introducing Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Regularly Backup, Automated Backup, Track Backup using this template. Grab it now to reap its full benefits.
-
 Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats
Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates various methods to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Deliver an outstanding presentation on the topic using this Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Network Attached Storage, Cloud Storage Services, Flat Backup System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats
Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Increase audience engagement and knowledge by dispensing information using Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Time Consuming Process, Speedy Process, Incremental Backup using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 External Threats To Data Security Management With Solutions
External Threats To Data Security Management With SolutionsThis slide showcases various external threats that affect the data security management of businesses with solutions to mitigate those risks. It includes various threats such as SQL injection, ransomware, phishing, and accidental exposure. Introducing our premium set of slides with External Threats To Data Security Management With Solutions. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Accidental Exposure, Unwanted Operations, Secure Mechanism. So download instantly and tailor it with your information.
-
 Security Management Policies To Mitigate Internal Data Threats
Security Management Policies To Mitigate Internal Data ThreatsThis slide focuses on the policies for security management helping companies to mitigate internal data threats efficiently. It includes policies for metadata, backup, internal protocol, emails, etc. Introducing our premium set of slides with Security Management Policies To Mitigate Internal Data Threats. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protocol For Visitors, Internet Protocol, Security Audit. So download instantly and tailor it with your information.
-
 Cybersecurity Data Threat Detection Icon
Cybersecurity Data Threat Detection IconPresenting our well structured Cybersecurity Data Threat Detection Icon. The topics discussed in this slide are Cybersecurity Data, Threat Detection, Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Our Threats Data Analytics And Storage Company Profile CP SS V
Our Threats Data Analytics And Storage Company Profile CP SS VThe following slide showcases the threats to Snowflake company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as market competition market competition and technology disruptions. Introducing Our Threats Data Analytics And Storage Company Profile CP SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Weakness, Opportunities using this template. Grab it now to reap its full benefits.
-
 Our Threats Data Warehouse Service Company CP SS V
Our Threats Data Warehouse Service Company CP SS VThe following slide showcases the threats to Snowflake company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as market competition market competition and technology disruptions. Increase audience engagement and knowledge by dispensing information using Our Threats Data Warehouse Service Company CP SS V This template helps you present information on four stages. You can also present information on Opportunities, Strategic Collaboration, Industry Growth using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Bfsi Sector Cybersecurity Threats In Big Data Analytics
Bfsi Sector Cybersecurity Threats In Big Data AnalyticsThis slide highlights cybersecurity in BFSI sector big data analytics threats. This includes phishing attacks, cyber physical attacks, internet of things attacks and threats by third party involved. Introducing our premium set of slides with name Bfsi Sector Cybersecurity Threats In Big Data Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Physical Attacks, Internet Of Things Attacks, Threats By Third Party Involved. So download instantly and tailor it with your information.
-
 Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to data breach recovery. It includes key elements such as incident date, challenges faced, LinkedIn response plan, and results. Deliver an outstanding presentation on the topic using this Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Regain Customer Trust, Rebuilding Business Reputation, Linkedin Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat
Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information leveraging multifactor authentication to increase cyber security. It includes key points such as failed login, geographic location, time of login, operating system, IP address, etc. Deliver an outstanding presentation on the topic using this Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Time Of Login Attempt, Operating System, Source Of IP Address using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining Data Loss Impact Due To Cyber Threat Safeguarding Business With Data Loss Cybersecurity SS
Determining Data Loss Impact Due To Cyber Threat Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding impact of data loss due to threat agents such as insider threat, social engineering, malware, specific enterprise cyber threats, etc.Present the topic in a bit more detail with this Determining Data Loss Impact Due To Cyber Threat Safeguarding Business With Data Loss Cybersecurity SS. Use it as a tool for discussion and navigation on Insider Threat, Social Engineering, Maintenance Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Insider Threats Management Case Study Aspire Safeguarding Business With Data Loss Cybersecurity SS
Insider Threats Management Case Study Aspire Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding case study highlighting insider threat management at a pharmaceutical company to secure clients sensitive data, track employees activities, etc.Introducing Insider Threats Management Case Study Aspire Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Challenge, Solution, Impact, Objective, Industry Healthcare, using this template. Grab it now to reap its full benefits.
-
 Introduction Of Cyber Threat Intelligence For Data Security
Introduction Of Cyber Threat Intelligence For Data SecurityThis slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Introducing Introduction Of Cyber Threat Intelligence For Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Evolving Threats Demand Intelligence, Vital For Security Architecture, Proactively Blocks Attacks, using this template. Grab it now to reap its full benefits.
-
 Mitigating Cybersecurity Threats With Data Loss Prevention Solutions
Mitigating Cybersecurity Threats With Data Loss Prevention SolutionsThis slide represents various data loss prevention strategies that assist companies in mitigating multiple cybersecurity threats to enhance information protection. It includes threats such as extrusion, insider threats, and unintended exposure. Introducing our Mitigating Cybersecurity Threats With Data Loss Prevention Solutions set of slides. The topics discussed in these slides are Extrusion, Insider Threats, Unintended Exposure. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatSecure your digital assets with our Cloud-based endpoint cyber security icon for PowerPoint. Featuring a bold and vibrant design, this icon represents the protection and peace of mind offered by our cutting-edge security solutions. Perfect for presentations on cloud security, data protection, and cyber threats. Download now and enhance your slides.
-
 Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents a cloud-based endpoint cyber security solution. It is designed to protect your digital assets from external threats, providing real-time monitoring and threat detection. With its user-friendly interface and advanced features, it offers a comprehensive and reliable solution for safeguarding your data and devices.
-
 Mdr Cybersecurity Icon To Detect Data Threats
Mdr Cybersecurity Icon To Detect Data ThreatsPresenting our well structured Mdr Cybersecurity Icon To Detect Data Threats. The topics discussed in this slide are Cybersecurity, Data Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Protecting Sensitive Data From Network Security Threats
Protecting Sensitive Data From Network Security ThreatsThis slide highlights network security threats to protect from unauthorized access including trojan viruses, malware, and computer worms. Introducing our premium set of slides with name Protecting Sensitive Data From Network Security Threats. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trojan Virus, Malware, Computer Worms. So download instantly and tailor it with your information.
-
 Statistical Data Showcasing Key Elements Of Cyber Terrorism
Statistical Data Showcasing Key Elements Of Cyber TerrorismThis slide represents the statistics related to the key elements of the cyber terrorism. It includes elements such as fear as an outcome, civilian targets, criminality or illegality, digital means or target. Presenting our well structured Statistical Data Showcasing Key Elements Of Cyber Terrorism. The topics discussed in this slide are Statistical Data Showcasing Key Elements Of Cyber Terrorism. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Breakdown Of Malicious Data Breach Risk Root Cause By Threat
Breakdown Of Malicious Data Breach Risk Root Cause By ThreatThis slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Introducing our Breakdown Of Malicious Data Breach Risk Root Cause By Threat set of slides. The topics discussed in these slides are Social Engineering, Business Email Compromise, Malicious Insider. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Depicting Effects Of Cyber Bullying On Children
Data Depicting Effects Of Cyber Bullying On ChildrenThis slide showcases statistical data regarding childrens problems caused by cyberbullying to understand its effect and apply effective measures. It also includes the frequency of issues such as drug abuse, self harm, etc. Introducing our Data Depicting Effects Of Cyber Bullying On Children set of slides. The topics discussed in these slides are Experienced, Cyberbullying, Spreading. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Top Vulnerable Industries To Cyber Security Threats And Data Breaches
Top Vulnerable Industries To Cyber Security Threats And Data BreachesThis slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Introducing our Top Vulnerable Industries To Cyber Security Threats And Data Breaches set of slides. The topics discussed in these slides are Government, Department. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon showcasing data availability security against risks and threats
Icon showcasing data availability security against risks and threatsPresenting our set of slides with Icon Showcasing Data Availability Security Against Risks And Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Showcasing Data Availability Security Against Risks And Threats.
-
 Addressing internal and external sources of threat data corporate security management
Addressing internal and external sources of threat data corporate security managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Introducing Addressing Internal And External Sources Of Threat Data Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, using this template. Grab it now to reap its full benefits.
-
 Agenda for advanced security monitoring plan to remove cybersecurity threat and data infraction
Agenda for advanced security monitoring plan to remove cybersecurity threat and data infractionIncrease audience engagement and knowledge by dispensing information using Agenda For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. This template helps you present information on seven stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infraction
Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infractionIntroducing our well researched set of slides titled Icons Slide For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table of contents advanced security monitoring plan to remove cybersecurity threat and data infraction
Table of contents advanced security monitoring plan to remove cybersecurity threat and data infractionPresent the topic in a bit more detail with this Table Of Contents Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Tools To Be Implemented, Essential Elements Of Security Monitoring Plan, Cybersecurity Monitoring Best Practices To Be Followed By The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management for organization critical addressing internal and external sources of threat data gathering
Threat management for organization critical addressing internal and external sources of threat data gatheringThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Present the topic in a bit more detail with this Threat Management For Organization Critical Addressing Internal And External Sources Of Threat Data Gathering. Use it as a tool for discussion and navigation on Targeted Intelligence, Malware Intelligence, Reputation Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace A Internal And External Sources Threat Data Gathering
Vulnerability Administration At Workplace A Internal And External Sources Threat Data GatheringThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Present the topic in a bit more detail with this Vulnerability Administration At Workplace A Internal And External Sources Threat Data Gathering. Use it as a tool for discussion and navigation on Sources, Intelligence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Data Should Be Backup Cyber Terrorism Attacks
Confidential Data Should Be Backup Cyber Terrorism AttacksThis slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Introducing Confidential Data Should Be Backup Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Unanticipated, Occurrence, Recovered, Business, Assurance, using this template. Grab it now to reap its full benefits.
-
 Qualitative Analysis Of Collected Cyber Terrorism Primary Data
Qualitative Analysis Of Collected Cyber Terrorism Primary DataThis slide represents the analysis of the collected cyber terrorism data. It includes details related to victims of cyber terrorism, increase of terrorism online presence, regulation and stakeholder understanding and defining cyber terrorism. Introducing our premium set of slides with name Qualitative Analysis Of Collected Cyber Terrorism Primary Data. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulation And Stakeholder Understanding, Defining Cyber Terrorism, Terrorism Online Presence. So download instantly and tailor it with your information.
-
 Cloud Security Threats Loss Of Data Cloud Information Security
Cloud Security Threats Loss Of Data Cloud Information SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Information Security This template helps you present information on four stages. You can also present information on Cloud Administrations, Protection Frameworks, Technology Advances using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Loss Of Data Cloud Computing Security
Cloud Security Threats Loss Of Data Cloud Computing SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Computing Security. This template helps you present information on four stages. You can also present information on Service Providers, Organization, Backup Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Threat Assessment Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Threat Assessment Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data threat assessment colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Threat Assessment Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Threat Assessment Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data threat assessment monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Threat Password Attack Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Threat Password Attack Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data threat password attack colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Threat Password Attack Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Threat Password Attack Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data threat password attack monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Threat With Bug Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Threat With Bug Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data threat with bug colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Threat With Bug Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Threat With Bug Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data threat with bug monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Spoofing And Data Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Spoofing And Data Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Spoofing and data threat colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Spoofing And Data Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Spoofing And Data Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Spoofing and data threat monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cloud Security Risks Or Threats Cloud Data Protection
Cloud Security Risks Or Threats Cloud Data ProtectionThis slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Increase audience engagement and knowledge by dispensing information using Cloud Security Risks Or Threats Cloud Data Protection. This template helps you present information on eight stages. You can also present information on Revenue Losses, Compliance Violations, Loss Of Data using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats Compliance Violations Cloud Data Protection
Cloud Security Threats Compliance Violations Cloud Data ProtectionThis slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. Introducing Cloud Security Threats Compliance Violations Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Authentication Procedures, Business, Organizations, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Contract Breaches With Clients Cloud Data Protection
Cloud Security Threats Contract Breaches With Clients Cloud Data ProtectionThis slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Contract Breaches With Clients Cloud Data Protection. This template helps you present information on four stages. You can also present information on Business Partners, Organization, Cloud using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats End User Control Cloud Data Protection
Cloud Security Threats End User Control Cloud Data ProtectionThis slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. Introducing Cloud Security Threats End User Control Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Business Data, Customers, Centralized Data, using this template. Grab it now to reap its full benefits.




