Powerpoint Templates and Google slides for Cybersecurity Tools
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Anti Spyware Tools In Cybersecurity Training Ppt
Anti Spyware Tools In Cybersecurity Training PptPresenting Anti Spyware Tools in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Threat Technology Security Displaying Cybersecurity Companies
Threat Technology Security Displaying Cybersecurity CompaniesIntroduce your topic and host expert discussion sessions with this Threat Technology Security Displaying Cybersecurity Companies. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Introduction To Cybersecurity Using Decoding The Future Of Blockchain Technology BCT SS
Introduction To Cybersecurity Using Decoding The Future Of Blockchain Technology BCT SSThis slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Deliver an outstanding presentation on the topic using this Introduction To Cybersecurity Using Decoding The Future Of Blockchain Technology BCT SS. Dispense information and present a thorough explanation of Reducing Identity Theft Risks, Cybersecurity, Cybersecurity Using Blockchain using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity And Crisis Management Technology Adoption Trends
Cybersecurity And Crisis Management Technology Adoption TrendsThe purpose of this slide is to highlight how cybersecurity and crisis management technology adoption trends enable organizations to stay ahead by identifying and adopting emerging technologies, enhancing resilience against cyber threats and crises. Introducing our Cybersecurity And Crisis Management Technology Adoption Trends set of slides. The topics discussed in these slides are Cybersecurity, Crisis Management Technology, Adoption Trends. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS
Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SSThis slide demonstrates the positive impact of implementing network vulnerability management solutions on returns on investments. The graph depicts an increase in ROI and savings over time..Deliver an outstanding presentation on the topic using this Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS. Dispense information and present a thorough explanation of Key Insights, Improved Compliance, Password Hacking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tools To Address Supply Chain Cybersecurity Attacks For Data Protection
Tools To Address Supply Chain Cybersecurity Attacks For Data ProtectionThis slide graphically represents use of various tools and approaches that assist companies in addressing various supply chain cybersecurity attacks and optimizing data protection. It includes tools such as IT vendor risk management tools, supply chain risk management tools, etc. Presenting our well structured Tools To Address Supply Chain Cybersecurity Attacks For Data Protection. The topics discussed in this slide are Audits Of Suppliers, Manufacturers, Logistics Partners. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Features Of OpenAI ChatGPT Tool How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Key Features Of OpenAI ChatGPT Tool How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcase various features of OpenAI ChatGPT tool. Features include multi language support, text generation, question answering, customization, conversational AI, integration within web application, batching, scaling etc. Introducing Key Features Of OpenAI ChatGPT Tool How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Generation, Support, Customization, using this template. Grab it now to reap its full benefits.
-
 PentestGPT Penetration Testing Tool How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
PentestGPT Penetration Testing Tool How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases overview of PentestGPT tool that can help organization in penetration testing and reduce cyber attacks in organization. It also highlights various capabilities and modules of PentestGPT tool. Introducing PentestGPT Penetration Testing Tool How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Generation, Reasoning, Module, using this template. Grab it now to reap its full benefits.
-
 Overview Of Active Risk Manager Tools For Cybersecurity Risk Supplier Risk Management
Overview Of Active Risk Manager Tools For Cybersecurity Risk Supplier Risk ManagementThis slide showcases benefits of using Active Risk Manager tools for cybersecurity risk. This template includes elements such as quantitative risk assessments and analysis, risk normalization and aggregation etc. Present the topic in a bit more detail with this Overview Of Active Risk Manager Tools For Cybersecurity Risk Supplier Risk Management. Use it as a tool for discussion and navigation on Platforms Supported, Popular Features, Overall Rating, Security Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Selection Of Cybersecurity Risk Management Tools Supplier Risk Management
Selection Of Cybersecurity Risk Management Tools Supplier Risk ManagementThis slide showcases cybersecurity risk management tools comparison to choose best software to reduce risk. This template includes tools such as ZenGRC, Active Risk Manager, Cloud GRC, Pathlock etc. Increase audience engagement and knowledge by dispensing information using Selection Of Cybersecurity Risk Management Tools Supplier Risk Management. This template helps you present information on five stages. You can also present information on Active Risk Manager, Contract Management, Security Risk Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Cybersecurity Technology Deployment Plan To Improve Organizations
Best Practices For Cybersecurity Technology Deployment Plan To Improve OrganizationsThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Introducing Best Practices For Cybersecurity Technology Deployment Plan To Improve Organizations to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Management, Process, Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Overview And Key Benefits Of Cybersecurity In Business Unlocking The Impact Of Technology
Overview And Key Benefits Of Cybersecurity In Business Unlocking The Impact Of TechnologyThis slide showcases introduction to cybersecurity. This template focuses on confidentiality, integrity and availability of data in an organisation. It includes information related to maintaining employee trust, protecting personal information, etc. Introducing Overview And Key Benefits Of Cybersecurity In Business Unlocking The Impact Of Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Servers From Malicious Attacks, Applications From External Attacks, Maintains Employee Trust, Safeguards Business Operations, using this template. Grab it now to reap its full benefits.
-
 Success Metrics For Measuring Cybersecurity Unlocking The Impact Of Technology
Success Metrics For Measuring Cybersecurity Unlocking The Impact Of TechnologyThis slide showcases key performance indicators to measure cybersecurity performance. This template focuses on providing stats used to ensure security of current application in use. It includes information related to security incidents, mean time to detect, etc. Increase audience engagement and knowledge by dispensing information using Success Metrics For Measuring Cybersecurity Unlocking The Impact Of Technology. This template helps you present information on one stages. You can also present information on Regular Data Backup And Recovery, Educating Employees, Cybersecurity Performance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity Techniques
Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity TechniquesThis slide showcases best practices required for securing data. This template focuses on maintaining continuity of operations and minimizing potential for costly interruptions. It covers aspects related to threat detection, firewall, antivirus software, etc. Increase audience engagement and knowledge by dispensing information using Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity Techniques. This template helps you present information on four stages. You can also present information on Threat Detection And Prevention, Antivirus Software, Two Factor Authentication, Cybersecurity Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unlocking The Impact Of Technology Current Cybersecurity Trends Followed By Organisations
Unlocking The Impact Of Technology Current Cybersecurity Trends Followed By OrganisationsThis slide showcases trends followed by organisations related to cybersecurity. This template focuses on improving detection and response capabilities and building more digitally immune identity ecosystems. It includes information related to Chrome, microphones, etc. Increase audience engagement and knowledge by dispensing information using Unlocking The Impact Of Technology Current Cybersecurity Trends Followed By Organisations. This template helps you present information on five stages. You can also present information on Current Cybersecurity Trends, Microphones, Digitally Immune, Identity Ecosystems using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unlocking The Impact Of Technology Cybersecurity Architecture Framework To Protect Organisations
Unlocking The Impact Of Technology Cybersecurity Architecture Framework To Protect OrganisationsThis This slide showcases framework for cybersecurity in organisations. This template focuses on reducing cyber breaches and protecting assets from digital harm. It includes information related to enterprise goals, creating safety solution, etc. Present the topic in a bit more detail with this Unlocking The Impact Of Technology Cybersecurity Architecture Framework To Protect Organisations. Use it as a tool for discussion and navigation on Cybersecurity Architecture, Framework To Protect Organisations, Assets From Digital Harm, Enterprise Goals. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unlocking The Impact Of Technology Steps For Building Business Cybersecurity Strategy
Unlocking The Impact Of Technology Steps For Building Business Cybersecurity StrategyThis slide showcases process for creating cybersecurity strategy. This template focuses on measuring protection against cyberthreats which disrupts employee productivity. It includes information related to assessing maturity, documenting strategy, etc. Introducing Unlocking The Impact Of Technology Steps For Building Business Cybersecurity Strategy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Understand Cybersecurity Threat, Assess Maturity, Cybersecurity Awareness, Training Initiatives, using this template. Grab it now to reap its full benefits.
-
 Unlocking The Impact Of Technology Use Cases Of Cybersecurity For Different Enterprises
Unlocking The Impact Of Technology Use Cases Of Cybersecurity For Different EnterprisesThis slide showcases use cases of cybersecurity in different enterprises. This template focuses on safeguarding personal data and privacy. It includes information related to detecting insider threats, investigating cyber attacks and monitoring privileged accounts. Increase audience engagement and knowledge by dispensing information using Unlocking The Impact Of Technology Use Cases Of Cybersecurity For Different Enterprises. This template helps you present information on three stages. You can also present information on Detecting Insider Threats, Monitoring Privileged Account Access, Investigating Attacks, Cybersecurity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Plan With Effective Healthcare Tools
Cybersecurity Plan With Effective Healthcare ToolsThis slide presents healthcare cybersecurity plan, helpful in identifying nature of threats and using tools to protect system from malicious practices. It includes affected components such as patient, privacy protection, healthcare legacy system and tools such as Microsoft EMET and Exact Trak Introducing our Cybersecurity Plan With Effective Healthcare Tools set of slides. The topics discussed in these slides are Cybersecurity Key Components, Cybersecurity Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Big Data Analytics Cybersecurity Tools
Big Data Analytics Cybersecurity ToolsThe following slide highlights resources like EPP, SIEM, threat intelligence software, fraud detection, predictive modeling, and anti malware sandboxes to show big data analytics cybersecurity tools. It helps organizations to bolster their cyber defense capabilities and safeguard against a wide range of threats. Introducing our premium set of slides with Big Data Analytics Cybersecurity Tools. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protection, Management, Intelligence. So download instantly and tailor it with your information.
-
 Users Of IoT Security Software Tool Improving IoT Device Cybersecurity IoT SS
Users Of IoT Security Software Tool Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase clients of Internet of Things IoT security software. The classification is done on the basis of companies, industrial enterprises, healthcare providers, and financial services companies. Introducing Users Of IoT Security Software Tool Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Providers, Services, Enterprises, using this template. Grab it now to reap its full benefits.
-
 Various Types Of IoT Security Tools Improving IoT Device Cybersecurity IoT SS
Various Types Of IoT Security Tools Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase different types of Internet of Things IoT security software. Identity and access management, antivirus software, firewall software, intrusion detection system, and data loss prevention are some of the major tools which are outlined in slide. Introducing Various Types Of IoT Security Tools Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Management, Software, System, using this template. Grab it now to reap its full benefits.
-
 Technology Cybersecurity In Powerpoint And Google Slides Cpb
Technology Cybersecurity In Powerpoint And Google Slides CpbPresenting our Technology Cybersecurity In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Technology Cybersecurity This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Introducing Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Decentralized Architecture, Public Key Cryptography, Smart Contracts, using this template. Grab it now to reap its full benefits.
-
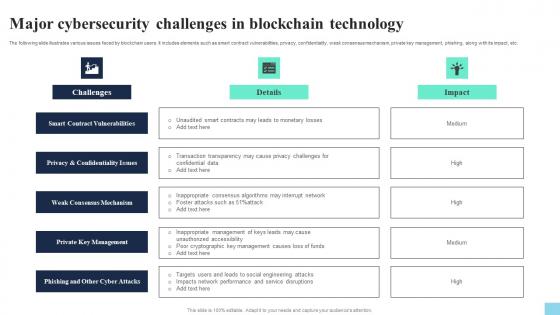 Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Introducing Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Smart Contract Vulnerabilities, Weak Consensus Mechanism, Private Key Management, using this template. Grab it now to reap its full benefits.
-
 Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Increase audience engagement and knowledge by dispensing information using Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V. This template helps you present information on seven stages. You can also present information on Transaction Requested, Created Transaction, Existing Blockchain using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
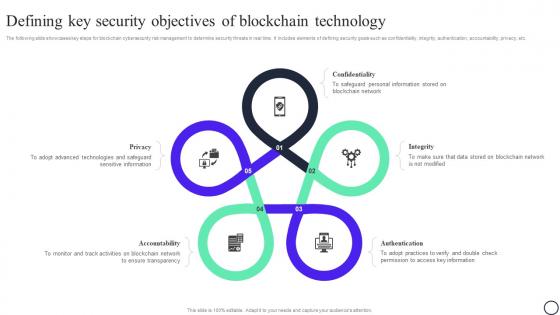 Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V
Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V This template helps you present information on Five stages. You can also present information on Privacy, Confidentiality, Integrity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity How Hackers Attack Blockchain Technology BCT SS V
Blockchain And Cybersecurity How Hackers Attack Blockchain Technology BCT SS VThe following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. Introducing Blockchain And Cybersecurity How Hackers Attack Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Technology, Modify Data, Swindles Private Keys using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Importance Of Cybersecurity In Blockchain Technology BCT SS V
Blockchain And Cybersecurity Importance Of Cybersecurity In Blockchain Technology BCT SS VThe following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Importance Of Cybersecurity In Blockchain Technology BCT SS V This template helps you present information on Four stages. You can also present information on Decentralized Architecture, Public Key Cryptography, Smart Contracts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Major Cybersecurity Challenges In Blockchain Technology BCT SS V
Blockchain And Cybersecurity Major Cybersecurity Challenges In Blockchain Technology BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Major Cybersecurity Challenges In Blockchain Technology BCT SS V Use it as a tool for discussion and navigation on The following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V
Blockchain And Cybersecurity Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Introducing Blockchain And Cybersecurity Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Works, Created Transaction, Node In Transaction using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Overview Of Phishing Attack In Blockchain Technology BCT SS V
Blockchain And Cybersecurity Overview Of Phishing Attack In Blockchain Technology BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Blockchain And Cybersecurity Overview Of Phishing Attack In Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Attached Fake Links, Investment Opportunities, Fake Website using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS V
Blockchain And Cybersecurity Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS VThe following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS V Use it as a tool for discussion and navigation on Astra Security, Intruder, Features, Reviews This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon Highlighting Technology Innovation For Ensuring Cybersecurity
Icon Highlighting Technology Innovation For Ensuring CybersecurityIntroducing our premium set of slides with Icon Highlighting Technology Innovation For Ensuring Cybersecurity Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Highlighting, Technology Innovation, Ensuring Cybersecurity So download instantly and tailor it with your information.
-
 Cyber Threats In Blockchain Importance Of Cybersecurity In Blockchain Technology BCT SS V
Cyber Threats In Blockchain Importance Of Cybersecurity In Blockchain Technology BCT SS VThe following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Importance Of Cybersecurity In Blockchain Technology BCT SS V This template helps you present information on Four stages. You can also present information on Decentralized Architecture, Public Key Cryptography, Smart Contracts using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS V
Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS V Use it as a tool for discussion and navigation on Challenges, Details, Impact This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V
Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V This template helps you present information on One stages. You can also present information on Node Validates Transaction, Existing Blockchain, Transaction Completed using this PPT design. This layout is completely editable so personaize it now
-
 Best Practices For 5G Cybersecurity Technology
Best Practices For 5G Cybersecurity TechnologyThis slide showcases the best practices to be followed during the installation of 5G cybersecurity. The purpose of this slide is to help establish a secure 5 G network through the use of practice such as building security into network design, real time monitoring and analysis of traffic, etc. Presenting our set of slides with Best Practices For 5G Cybersecurity Technology. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Monitoring, Assessment.
-
 Importance Of Cybersecurity In Blockchain Technology Guide For Blockchain BCT SS V
Importance Of Cybersecurity In Blockchain Technology Guide For Blockchain BCT SS VThe following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Introducing Importance Of Cybersecurity In Blockchain Technology Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Decentralized Architecture, Key Cryptography, Smart Contracts using this template. Grab it now to reap its full benefits.
-
 Major Cybersecurity Challenges In Blockchain Technology Guide For Blockchain BCT SS V
Major Cybersecurity Challenges In Blockchain Technology Guide For Blockchain BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Present the topic in a bit more detail with this Major Cybersecurity Challenges In Blockchain Technology Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Contract Vulnerabilities, Confidentiality Issues, Consensus Mechanism This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Workflow Of Blockchain Cybersecurity Technology Guide For Blockchain BCT SS V
Overview And Workflow Of Blockchain Cybersecurity Technology Guide For Blockchain BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Introducing Overview And Workflow Of Blockchain Cybersecurity Technology Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Blockchain Works, Transaction Completed using this template. Grab it now to reap its full benefits.
-
 Mitigate EDR Incidents Icon Using Cybersecurity Technology
Mitigate EDR Incidents Icon Using Cybersecurity TechnologyPresenting our set of slides with name Mitigate EDR Incidents Icon Using Cybersecurity Technology. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mitigate EDR Incidents, Icon Using Cybersecurity Technology.
-
 Cybersecurity Incident Response Tools Comparison
Cybersecurity Incident Response Tools ComparisonThis slide guides optimal tool selection for cybersecurity incident response through a concise comparison, empowering organizations to enhance their capabilities and strengthen overall cybersecurity resilience. Presenting our well structured Cybersecurity Incident Response Tools Comparison. The topics discussed in this slide are Security Information, Event Management, Antivirus, Endpoint Protection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Cybersecurity Monitoring Tools
Comparative Analysis Cybersecurity Monitoring ToolsFollowing slide represents cyber security inhouse data monitoring tools for comparative analysis for choosing best option to enhance data protection. It further covers tools, pricing, free trial, reviews and features such as risk mitigation, smart recon, data visualization, etc. Introducing our Comparative Analysis Cybersecurity Monitoring Tools set of slides. The topics discussed in these slides are Manage Engine, Monitoring Tools, Comparative Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Use Cases Of Blockchain In Cybersecurity Decoding The Future Of Blockchain Technology BCT SS
Use Cases Of Blockchain In Cybersecurity Decoding The Future Of Blockchain Technology BCT SSThis slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems. Increase audience engagement and knowledge by dispensing information using Use Cases Of Blockchain In Cybersecurity Decoding The Future Of Blockchain Technology BCT SS. This template helps you present information on five stages. You can also present information on Protected Edge Computing With Authentication, Advanced Confidentiality And Data Integrity, Secured Private Messaging using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Tools To Enhance Data Protection
Cybersecurity Tools To Enhance Data ProtectionThe highlighted slide details essential aspects such as tools, descriptions, use cases, platforms, and licenses, presenting cybersecurity tools designed to enhance data protection. This information aids in selecting and implementing the right tools to bolster the security infrastructure and safeguard sensitive data effectively. Presenting our well structured Cybersecurity Tools To Enhance Data Protection. The topics discussed in this slide are Intrusion Detection And Prevention, Penetration Testing, Ethical Hacking. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of SCADA Cybersecurity Tools For Data Protection
Applications Of SCADA Cybersecurity Tools For Data ProtectionThis slide represents various applications of SCADA cybersecurity tools that assist IT companies to enhance their data protection effectively. It includes various applications such as data encryption, vulnerability assessment, etc. Introducing our premium set of slides with Applications Of SCADA Cybersecurity Tools For Data Protection Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Detection Systems, Firewalls And Network Segmentation, Encryption And Secure Protocols. So download instantly and tailor it with your information.
-
 Comparative Analysis Of Cybersecurity Mesh Tools
Comparative Analysis Of Cybersecurity Mesh ToolsThe following slide highlights key points such as network security, endpoint security, access management, cloud security, and SIEM. This aids in conducting a comparative analysis of cybersecurity mesh tools, facilitating informed tool selection for comprehensive security solutions. Introducing our Comparative Analysis Of Cybersecurity Mesh Tools set of slides. The topics discussed in these slides are Network Security, Endpoint Security, Cloud Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Assessment Of Cybersecurity Tools In Retail Industry
Comparative Assessment Of Cybersecurity Tools In Retail IndustryThis slide highlights comparison of retail cyber security platforms. The purpose of this template is to aid managers in evaluating and selecting the most effective tools tailored for optimizing defence mechanisms. It includes elements such as advanced threat detection, data encryption, etc. Introducing our Comparative Assessment Of Cybersecurity Tools In Retail Industry set of slides. The topics discussed in these slides are Symantec Endpoint Protection, Crowdstrike Falcon This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Tools To Safeguard Educational Institutes
Cybersecurity Tools To Safeguard Educational InstitutesThis slide depicts the cybersecurity tools to safeguard educational institutes. The purpose of this slide is to help the business ensure suitable cybersecurity measures are implemented to prevent cyberattacks. It includes tools such as packet sniffers, firewalls, etc. Presenting our set of slides with Cybersecurity Tools To Safeguard Educational Institutes. This exhibits information on Ten stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cybersecurity Tools, Penetrating Tests, Encryption Tools
-
 Cybersecurity Technology To Protect NGOs Data
Cybersecurity Technology To Protect NGOs DataThe purpose of this slide is to highlight how cybersecurity technology protects NGOs data by preventing unauthorized access, ensuring integrity, and fortifying against cyber threats and breaches. Introducing our premium set of slides with Cybersecurity Technology To Protect NGOs Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Breaches And Hacking, Phishing And Social Engineering, Outdated Software And Systems, Data Privacy Compliance. So download instantly and tailor it with your information.
-
 Cybersecurity Challenges For Cloud Computing And Technology
Cybersecurity Challenges For Cloud Computing And TechnologyThis slide illustrates cloud computing cybersecurity challenges by establishing secure and resilient digital environment for users. It includes challenges such as security issues, lack of resources and expertise, compliance, and performance. Presenting our well structured Cybersecurity Challenges For Cloud Computing And Technology The topics discussed in this slide are Security Issues, Compliance, Performance This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Challenges In Blockchain Technology For Security Enhancement
Cybersecurity Challenges In Blockchain Technology For Security EnhancementThis slide highlights cybersecurity challenges for working together to enhance security posture of blockchain community by developers and users.It includes issues such as scalability challenges, lack of governance, blockchain literacy, and reliance on private keys. Presenting our set of slides with Cybersecurity Challenges In Blockchain Technology For Security Enhancement This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scalability Challenges, Blockchain Literacy, Lack Of Governance
-
 Emerging Cybersecurity Challenges In Information Technology
Emerging Cybersecurity Challenges In Information TechnologyThis slide represents cybersecurity challenges in information technology for adapting to dynamic landscapes, strengthening defenses, and ensuring resilience of systems. It includes issues such as cloud, ransomware, IoT, phishing, and insider attacks. Introducing our premium set of slides with Emerging Cybersecurity Challenges In Information Technology Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Attacks, Iot Attacks, Insider Attacks So download instantly and tailor it with your information.
-
 Comparison Of Cybersecurity Apps For Threat Detection
Comparison Of Cybersecurity Apps For Threat DetectionThis slide represents comparison table for cybersecurity applications for online risk mitigation including Wireshark, Metasploit, and Entersoft apps. Introducing our premium set of slides with Comparison Of Cybersecurity Apps For Threat Detection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Protocol Analysis, Security Assessment, Infrastructure Security Analysis. So download instantly and tailor it with your information.
-
 Technology Integration Of AI And ML For Ensuring Global Cybersecurity
Technology Integration Of AI And ML For Ensuring Global CybersecurityThis slide shows advancements in the field of cybersecurity achieved through the technological integration of artificial intelligence and machine learning algorithms. It covers various cybersecurity practices such as preventing cyberattacks, identifies suspicious activities, detects malware and spam. Presenting our set of slides with Technology Integration Of AI And ML For Ensuring Global Cybersecurity. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prevents Cyberattacks, Detects Malware, Identifies Suspicious Activities.
-
 Big Data Analytics Tools For Efficient Cybersecurity
Big Data Analytics Tools For Efficient CybersecurityThis slide represents efficient cybersecurity tools for big data analytics. This includes tools, features, free trials, price, reviews along with features such as free to use, efficient storage solution, data storage system. Presenting our well structured Big Data Analytics Tools For Efficient Cybersecurity. The topics discussed in this slide are Big Data Analytics Tools, Efficient Cybersecurity, Data Storage Flexibility. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Automation Tools To Enhance Data Protection
Cybersecurity Automation Tools To Enhance Data ProtectionThis slide represents various cybersecurity automation tools that help companies to enhance data protection from threats and vulnerabilities. It includes various tools such as sprint, quals, splunk, logpoint, etc. Introducing our premium set of slides with Cybersecurity Automation Tools To Enhance Data Protection Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Features, Cybersecurity Automation, Data Protection So download instantly and tailor it with your information.
-
 Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SS
Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SSThis slide showcases comparative analysis of major encryption software, helping companies choose according to their needs. It provides details about platform, integration, cost, user experience, etc. Present the topic in a bit more detail with this Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SS. Use it as a tool for discussion and navigation on Encryption Type, Platform, Integration, User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SS
Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SSThis slide showcases general overview of encryption technology process, focused on improving data privacy. It provides details about plaintext, ciphertext, decryption, etc. Introducing Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SS to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Plaintext Becomes Ciphertext, Encryption Keys And Algorithms Used, Ciphertext Sent Though Insecure Channels, using this template. Grab it now to reap its full benefits.




