Powerpoint Templates and Google slides for Cybersecurity Threats Vulnerabilities
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb
Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides CpbPresenting Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cybersecurity Threats Vulnerabilities. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cybersecurity Tips While Using Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Cybersecurity Tips While Using Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various cybersecurity tips that can be used while using ChatGPT for generating responses. Its key elements are avoid inserting sensitive data, awareness of potential bias and beware of fake applications Increase audience engagement and knowledge by dispensing information using Cybersecurity Tips While Using Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. This template helps you present information on three stages. You can also present information on Avoid Inserting Sensitive Data, Awareness Of Potential Bias, Beware Of Fake Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How In Cybersecurity Penetration Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
How In Cybersecurity Penetration Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various ChatGPT use cases for penetration testing which can help to prevent cyber attacks in organization. Its key elements are establish penetration testing environment, gain knowledge about testing tools, writing code for testing etc. Introducing How In Cybersecurity Penetration Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Penetration, Testing Environment, Penetration, using this template. Grab it now to reap its full benefits.
-
 Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various statistics that highlights the importance of cybersecurity in organization. It highlights stats related to malware attacks, DDos attacks, cybersecurity spending, ransomware attacks, malicious mining software etc. Present the topic in a bit more detail with this Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Use it as a tool for discussion and navigation on Cybersecurity, Statistics, Importance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Overview And Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases cybersecurity overview that can help organization to safeguard data from different types of cyber attacks. It also highlights various benefits of cybersecurity such as safeguard data, timely incident response, reduce monetary damage etc. Deliver an outstanding presentation on the topic using this Overview And Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Dispense information and present a thorough explanation of Organization, Cybersecurity, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Cybersecurity Incident Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Overview Cybersecurity Incident Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases overview of incident management that can help organization in tackling cyber attacks. It also highlights various importance of incident management that are reduction in cyber attacks, decrease in system downtime, improved incident response etc. Present the topic in a bit more detail with this Overview Cybersecurity Incident Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Use it as a tool for discussion and navigation on Management, Overview, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
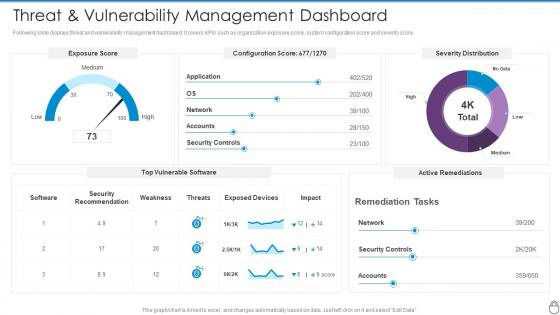 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix
Information Security Program Cybersecurity Management Threat Vulnerability Asset MatrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
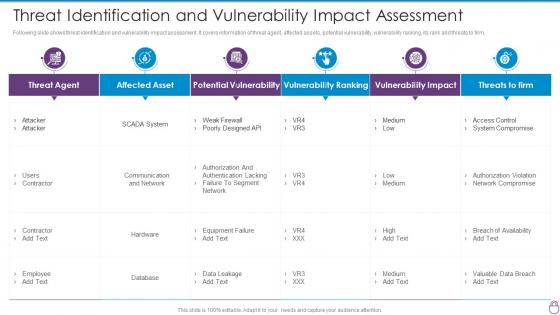 Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact
Cybersecurity Risk Management Framework Threat Identification And Vulnerability ImpactFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact. Dispense information and present a thorough explanation of Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
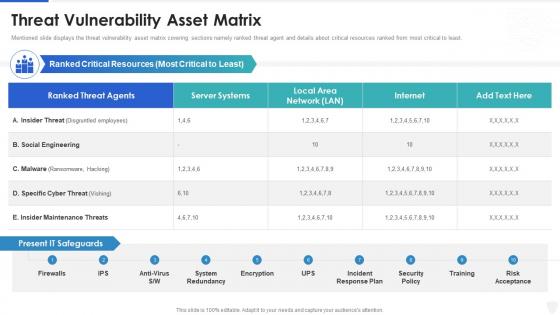 Cybersecurity and digital business risk management threat vulnerability asset matrix
Cybersecurity and digital business risk management threat vulnerability asset matrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan
Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity PlanThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Risk Assessment Matrix, Vulnerability Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan
Threat Identification And Vulnerability Assessment Formulating Cybersecurity PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Vulnerability Severity, Threat Source, Likelihood. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And Vulnerability
Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And VulnerabilityFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Introducing Checklist To Ensure Asset Protection From Internal Threats Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Email, Mobile Devices, using this template. Grab it now to reap its full benefits.
-
 Cyber Threat Facts Figures And Statistics Cybersecurity Incident And Vulnerability
Cyber Threat Facts Figures And Statistics Cybersecurity Incident And VulnerabilityThis slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Increase audience engagement and knowledge by dispensing information using Cyber Threat Facts Figures And Statistics Cybersecurity Incident And Vulnerability. This template helps you present information on six stages. You can also present information on Data Breach, Cost, Security Professionals using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.



