Powerpoint Templates and Google slides for Cybersecurity Threat Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
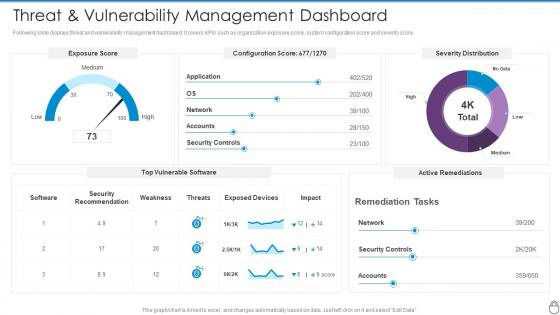 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview
Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Present the topic in a bit more detail with this Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Cybersecurity, Management, Tracking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Cybersecurity Technology Threat Management
IoT Cybersecurity Technology Threat ManagementThe below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Presenting our well structured IoT Cybersecurity Technology Threat Management. The topics discussed in this slide are Cybersecurity, Technology, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix
Information Security Program Cybersecurity Management Threat Vulnerability Asset MatrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Management Framework Mitigation Plan For Resolving Encountered Threat
Cybersecurity Risk Management Framework Mitigation Plan For Resolving Encountered ThreatMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Mitigation Plan For Resolving Encountered Threat. Dispense information and present a thorough explanation of Security Breach, Data Backup Team, Asset Manager, Operational Downtime using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
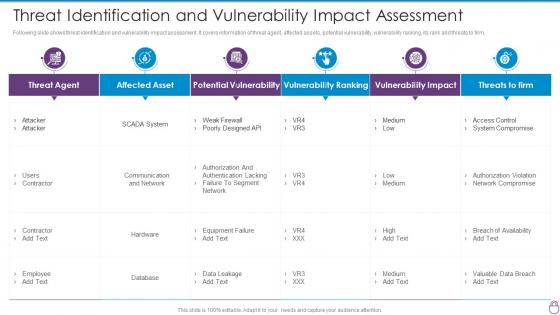 Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact
Cybersecurity Risk Management Framework Threat Identification And Vulnerability ImpactFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact. Dispense information and present a thorough explanation of Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
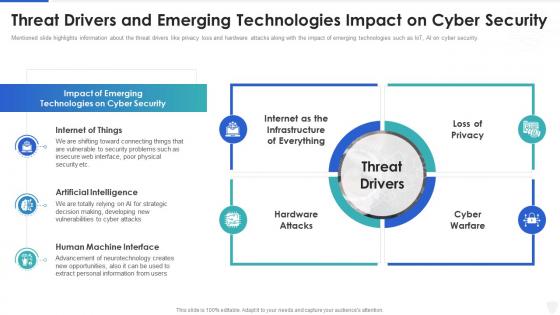 Cybersecurity and digital business risk management threat drivers and emerging technologies
Cybersecurity and digital business risk management threat drivers and emerging technologiesMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Drivers And Emerging Technologies. Dispense information and present a thorough explanation of Internet Of Things, Artificial Intelligence, Human Machine Interface using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
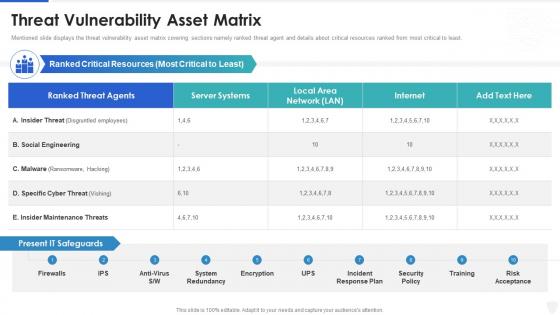 Cybersecurity and digital business risk management threat vulnerability asset matrix
Cybersecurity and digital business risk management threat vulnerability asset matrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Five Step Cybersecurity Threat Management Roadmap
Five Step Cybersecurity Threat Management RoadmapThis slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk. Presenting our set of slides with name Five Step Cybersecurity Threat Management Roadmap. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyzing, Identification, Responding, Monitoring, Evaluation.
-
 Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats
Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security ThreatsPresent the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats. Use it as a tool for discussion and navigation on Analysing, Organization, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered Threat
Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered ThreatMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered Threat. Dispense information and present a thorough explanation of Encountered Threat, Description, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan
Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management PlanThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization Present the topic in a bit more detail with this Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Identifying, Information, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management Plan
Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack Present the topic in a bit more detail with this Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Management, Solution, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan
Matrix For Threat Solution And Risk Management Formulating Cybersecurity PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Deliver an outstanding presentation on the topic using this Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Block Malicious, Monitor Database Activity, Validate Database Protocols using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace Overview
Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace OverviewThis slide provides details regarding best practices to enable cybersecurity at workplace in terms of data backup, enable compliance, phishing simulations, employees training, etc. Introducing Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Develop, Security, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace Overview
Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace OverviewThis slide provides details regarding roadmap to track cybersecurity activities across firm on monthly basis in terms of security and compliance, backups, staff training. Deliver an outstanding presentation on the topic using this Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Security, Backups, Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace Overview
Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace OverviewThis slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. Increase audience engagement and knowledge by dispensing information using Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace Overview. This template helps you present information on eight stages. You can also present information on Cybersecurity, Confidentiality, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace Overview
Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity trends existing across globe in terms of rise in automotive hacking, IoT with 5G, cloud platform as potential vulnerable, etc. Introducing Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Automotive, Artificial, Potential, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Framework Checklist To Manage Threats
Cybersecurity Framework Checklist To Manage ThreatsMentioned slide depicts the comparison of cybersecurity framework tools such as nikto,cain and abel,nmap,acunetix,metasploit. It compare differences on the basis of tool category, features and cost etc. Introducing our Cybersecurity Framework Checklist To Manage Threats set of slides. The topics discussed in these slides are Identify, Protect, Respond. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
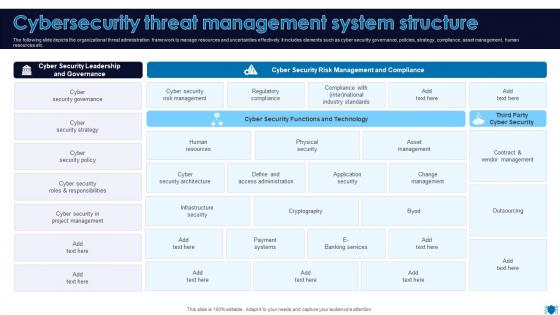 Cybersecurity Threat Management System Structure
Cybersecurity Threat Management System StructureThe following slide depicts the organizational threat administration framework to manage resources and uncertainties effectively. It includes elements such as cyber security governance, policies, strategy, compliance, asset management, human resources etc. Presenting our well structured Cybersecurity Threat Management System Structure. The topics discussed in this slide are Cyber Security Governance, Cyber Security Strategy, Cyber Security Policy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Unified Threat Management For Cybersecurity Icon
Unified Threat Management For Cybersecurity IconIntroducing our premium set of slides with Unified Threat Management For Cybersecurity Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Unified Threat Management, Cybersecurity Icon So download instantly and tailor it with your information.



