Powerpoint Templates and Google slides for Cybersecurity Monitoring
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Advanced security monitoring plan to remove cybersecurity threat and data infraction complete deck
Advanced security monitoring plan to remove cybersecurity threat and data infraction complete deckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fourty six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Ways to set up an advanced cybersecurity monitoring plan powerpoint presentation slides
Ways to set up an advanced cybersecurity monitoring plan powerpoint presentation slidesEnthrall your audience with this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SS
Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SSThis slide showcases endpoint encryption progress monitoring dashboard focused on tracking protection status of organizations computers. It provides details about warning period, managed, decrypted drives, etc. Present the topic in a bit more detail with this Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SS. Use it as a tool for discussion and navigation on Decrypting, Managed Computers, Non-Reporting Computers, Computer With Decrypted Drives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SS
Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding monitoring of risk reduction outcomes for successful data loss prevention execution. It includes tracking of data loss likelihood across platforms such as web, email, etc.Deliver an outstanding presentation on the topic using this Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Marker Legend, Goals, Data Loss Likelihood using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 AUP Cybersecurity Components For Network Monitoring
AUP Cybersecurity Components For Network MonitoringThis slide highlights AUP cybersecurity elements for accessing restricted information and using organizations IT security policies. It includes components such as authorized users, permitted uses, data security and network usage. Presenting our set of slides with AUP Cybersecurity Components For Network Monitoring This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authorized Users, Data Security, Permitted Uses
-
 AUP Cybersecurity Principles For Monitoring Network Traffic
AUP Cybersecurity Principles For Monitoring Network TrafficThis slide represents AUP cybersecurity guidelines for governing appropriate use of information technology resources and its security. It includes rules such as confidentiality, access codes, physical security, equipment and software, etc. Presenting our set of slides with AUP Cybersecurity Principles For Monitoring Network Traffic This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Confidentiality, Equipment And Software, Physical Security
-
 Enforcing AUP Cybersecurity Strategies For Network Monitoring
Enforcing AUP Cybersecurity Strategies For Network MonitoringThis slide covers AUP cybersecurity ways for providing clear expectations for using technology safely and appropriately in organization. It includes strategies such as understandable policies, corrective action plan, employee monitoring software, etc. Introducing our premium set of slides with Enforcing AUP Cybersecurity Strategies For Network Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understandable Policies, Corrective Action Plan So download instantly and tailor it with your information.
-
 Comparative Analysis Cybersecurity Monitoring Tools
Comparative Analysis Cybersecurity Monitoring ToolsFollowing slide represents cyber security inhouse data monitoring tools for comparative analysis for choosing best option to enhance data protection. It further covers tools, pricing, free trial, reviews and features such as risk mitigation, smart recon, data visualization, etc. Introducing our Comparative Analysis Cybersecurity Monitoring Tools set of slides. The topics discussed in these slides are Manage Engine, Monitoring Tools, Comparative Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 CRM Software Features To Monitor Cybersecurity Threat
CRM Software Features To Monitor Cybersecurity ThreatFollowing slide showcases monitoring cybersecurity threat CRM software features for network performance optimization. It further covers security monitoring, respond to suspicious activity and stay compliant. Introducing our premium set of slides with CRM Software Features To Monitor Cybersecurity Threat Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Monitoring, Suspicious Activity, Stay Compliant. So download instantly and tailor it with your information.
-
 Cybersecurity Alert Monitoring Priority Matrix
Cybersecurity Alert Monitoring Priority MatrixFollowing slide represents alert priority matrix for monitoring network cybersecurity to maintain regulatory compliance. It further covers characteristics, description and alert priority rating such as high, medium, low etc. Presenting our well structured Cybersecurity Alert Monitoring Priority Matrix The topics discussed in this slide are Alert Priority Rating, Priority Matrix, Intelligence System. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Maturity Model For Monitoring SCADA Cybersecurity Implementation
Maturity Model For Monitoring SCADA Cybersecurity ImplementationThis slide represents maturity model that assist IT companies to track implementation of SCADA cybersecurity for optimizing data protection. It includes various phases such as defining standards, increasing awareness, deploying solutions, etc. Introducing our premium set of slides with Maturity Model For Monitoring SCADA Cybersecurity Implementation Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Objectives, Operate And Maintain, Actions Required, Cybersecurity Implementation. So download instantly and tailor it with your information.
-
 Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS
Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of auditing and monitoring for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about response plan, etc. Increase audience engagement and knowledge by dispensing information using Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Auditing And Reporting, Incident Response Planning, Record Of Security Actions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phase 3 Of Dlp Success Execute Monitoring Program Safeguarding Business With Data Loss Cybersecurity SS
Phase 3 Of Dlp Success Execute Monitoring Program Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding execution of a monitoring program for successful data loss prevention execution. Essential roles to manage DLP integrity include technical administrator, forensics investigator, etc.Introducing Phase 3 Of Dlp Success Execute Monitoring Program Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Objective, Initiative, Forensics Investigator, Technical Administrator, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS
Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SSThis slide covers details related to real-time monitoring of system alerts provided by deployed network security tool that monitors networks for preventing, reporting and blocking malicious activities. Introducing Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Pattern Recognition, Automated Response, Behavioral Analysis, using this template. Grab it now to reap its full benefits.
-
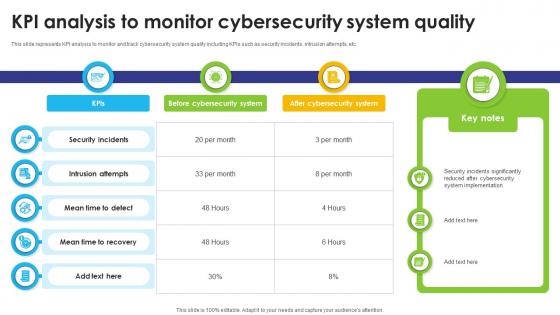 KPI Analysis To Monitor Cybersecurity System Quality
KPI Analysis To Monitor Cybersecurity System QualityThis slide represents KPI analysis to monitor and track cybersecurity system quality including KPIs such as security incidents, intrusion attempts, etc. Presenting our well structured KPI Analysis To Monitor Cybersecurity System Quality The topics discussed in this slide are Before Cybersecurity System, After Cybersecurity SystemThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents
Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attack Incidents, Vulnerabilities, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways to set up an advanced cybersecurity monitoring plan cybersecurity monitoring tools to be implemented
Ways to set up an advanced cybersecurity monitoring plan cybersecurity monitoring tools to be implementedThis slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Present the topic in a bit more detail with this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Cybersecurity Monitoring Tools To Be Implemented. Use it as a tool for discussion and navigation on Tool Category, Tool Description, Tool Implementation Costs, Tool Implementation Time. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways to set up an advanced cybersecurity monitoring plan estimated security monitoring key performance
Ways to set up an advanced cybersecurity monitoring plan estimated security monitoring key performanceThis slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an outstanding presentation on the topic using this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Estimated Security Monitoring Key Performance. Dispense information and present a thorough explanation of Security Monitoring KPIs, Costs Per Security Incident, Security Monitoring Incidents Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ways to set up an advanced cybersecurity monitoring plan major reasons for poor security monitoring
Ways to set up an advanced cybersecurity monitoring plan major reasons for poor security monitoringThis slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Present the topic in a bit more detail with this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Major Reasons For Poor Security Monitoring. Use it as a tool for discussion and navigation on Reasons Poor Security Monitoring, Reason Description, Improper Security Maintenance, Effects Ransomware, Evolving Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways to set up an advanced cybersecurity monitoring plan measures and ways to mitigate security
Ways to set up an advanced cybersecurity monitoring plan measures and ways to mitigate securityThis slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an outstanding presentation on the topic using this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Measures And Ways To Mitigate Security. Dispense information and present a thorough explanation of Malware Attacks, Pnishing Attacks, Lot Centric Breaches, Employee Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ways to set up an advanced cybersecurity monitoring plan ways through which security data
Ways to set up an advanced cybersecurity monitoring plan ways through which security dataThis slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Present the topic in a bit more detail with this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Ways Through Which Security Data. Use it as a tool for discussion and navigation on Attack Description, Ways To Mitigate Attack, External Attacks, Insider Attacks, Supply Chain Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Advanced security monitoring plan cybersecurity monitoring plan steps in detail
Advanced security monitoring plan cybersecurity monitoring plan steps in detailThis slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Introducing Advanced Security Monitoring Plan Cybersecurity Monitoring Plan Steps In Detail to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Logging, Incident Categorization, Incident Prioritization, Incident Assignment, Task Creation And Management, using this template. Grab it now to reap its full benefits.
-
 Agenda for advanced security monitoring plan to remove cybersecurity threat and data infraction
Agenda for advanced security monitoring plan to remove cybersecurity threat and data infractionIncrease audience engagement and knowledge by dispensing information using Agenda For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. This template helps you present information on seven stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity monitoring best practices to be followed by the company
Cybersecurity monitoring best practices to be followed by the companyThis slide provides information about some of the best practices related to security monitoring that must be followed by the company. Present the topic in a bit more detail with this Cybersecurity Monitoring Best Practices To Be Followed By The Company. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Best Practices To Be Followed By The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity monitoring plan steps advanced security monitoring plan
Cybersecurity monitoring plan steps advanced security monitoring planThis slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies Increase audience engagement and knowledge by dispensing information using Cybersecurity Monitoring Plan Steps Advanced Security Monitoring Plan. This template helps you present information on six stages. You can also present information on Business Needs, Risk Assessment, Monitoring Plan, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity monitoring plan steps in detail fine tune monitoring system
Cybersecurity monitoring plan steps in detail fine tune monitoring systemThis slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine Tune Monitoring System. Introducing Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Monitoring Plan, using this template. Grab it now to reap its full benefits.
-
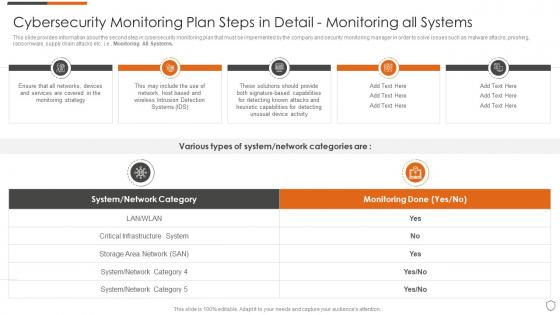 Cybersecurity monitoring plan steps in detail monitoring all systems
Cybersecurity monitoring plan steps in detail monitoring all systemsThis slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Increase audience engagement and knowledge by dispensing information using Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems. This template helps you present information on five stages. You can also present information on Critical Infrastructure System, Storage Area Network, System Network Category using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity monitoring plan steps in detail monitoring network traffic
Cybersecurity monitoring plan steps in detail monitoring network trafficThis slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Introducing Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Traffic Monitoring Tools, Tool Implementation Costs Per Year, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity monitoring plan steps in detail monitoring user activity
Cybersecurity monitoring plan steps in detail monitoring user activityThis slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Increase audience engagement and knowledge by dispensing information using Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity. This template helps you present information on three stages. You can also present information on Action Information, User Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity monitoring plan steps in detail providing resilient and synchronized timing
Cybersecurity monitoring plan steps in detail providing resilient and synchronized timingThis slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Present the topic in a bit more detail with this Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing. Use it as a tool for discussion and navigation on Asset Management, Cybersecurity, Compliance, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity monitoring plan steps in detail review and risk analysis
Cybersecurity monitoring plan steps in detail review and risk analysisThis slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Increase audience engagement and knowledge by dispensing information using Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis. This template helps you present information on four stages. You can also present information on Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability
Cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capabilityThis slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. Introducing Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Analysis Capability to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Monitoring Plan Steps, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity monitoring tools to be implemented ppt powerpoint presentation file gallery
Cybersecurity monitoring tools to be implemented ppt powerpoint presentation file galleryThis slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Present the topic in a bit more detail with this Cybersecurity Monitoring Tools To Be Implemented Ppt Powerpoint Presentation File Gallery. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Tools To Be Implemented. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infraction
Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infractionIntroducing our well researched set of slides titled Icons Slide For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table of contents advanced security monitoring plan to remove cybersecurity threat and data infraction
Table of contents advanced security monitoring plan to remove cybersecurity threat and data infractionPresent the topic in a bit more detail with this Table Of Contents Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Tools To Be Implemented, Essential Elements Of Security Monitoring Plan, Cybersecurity Monitoring Best Practices To Be Followed By The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan
Way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring planThis slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge or problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. Increase audience engagement and knowledge by dispensing information using Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Monitoring Plan. This template helps you present information on nine stages. You can also present information on Monitoring All Systems, Monitoring Network Traffic, Review And Risk Analysis, Fine Tune Monitoring System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity breakdown facebook advertising surplus biotechnology risk monitor cpb
Cybersecurity breakdown facebook advertising surplus biotechnology risk monitor cpbPresenting this set of slides with name - Cybersecurity Breakdown Facebook Advertising Surplus Biotechnology Risk Monitor Cpb. This is an editable three stages graphic that deals with topics like Cybersecurity, Breakdown, Facebook Advertising, Surplus, Biotechnology, Risk Monitor to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cybersecurity maintenance checklist monitoring ppt powerpoint gallery
Cybersecurity maintenance checklist monitoring ppt powerpoint galleryThis slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily weekly monthly or quarterly basis. Presenting this set of slides with name Cybersecurity Maintenance Checklist Monitoring Ppt Powerpoint Gallery. The topics discussed in these slides are Security Patches, Virus Scanning, Preventive Maintenance, Backup Monitoring, Disk Error Checking . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Optimizing cybersecurity framework roadmap logging monitoring ppt gallery
Optimizing cybersecurity framework roadmap logging monitoring ppt galleryThis slide portrays information regarding optimization of current cybersecurity framework. The IT department will require to fulfill crucial activities in specific timeframe. Presenting this set of slides with name Optimizing Cybersecurity Framework Roadmap Logging Monitoring Ppt Gallery. The topics discussed in these slides are Optimizing Cybersecurity, Framework Roadmap, Logging Monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cybersecurity monitoring company effective security monitoring plan ppt ideas tips
Cybersecurity monitoring company effective security monitoring plan ppt ideas tipsThis slide provides information about some of the best practices related to security monitoring that must be followed by the company. Present the topic in a bit more detail with this Cybersecurity Monitoring Company Effective Security Monitoring Plan Ppt Ideas Tips. Use it as a tool for discussion and navigation on Network, Performance, Practice. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity monitoring plan effective security monitoring plan ppt inspiration icons
Cybersecurity monitoring plan effective security monitoring plan ppt inspiration iconsThis slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Increase audience engagement and knowledge by dispensing information using Cybersecurity Monitoring Plan Effective Security Monitoring Plan Ppt Inspiration Icons. This template helps you present information on five stages. You can also present information on Plan, Management, Assignment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity monitoring system effective security monitoring plan ppt outline outfit
Cybersecurity monitoring system effective security monitoring plan ppt outline outfitThis slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine Tune Monitoring System. Introducing Cybersecurity Monitoring System Effective Security Monitoring Plan Ppt Outline Outfit to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Systems, Generate, Changes, Monitoring, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity risk analysis effective security monitoring plan ppt pictures graphics
Cybersecurity risk analysis effective security monitoring plan ppt pictures graphicsThis slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis Effective Security Monitoring Plan Ppt Pictures Graphics. Dispense information and present a thorough explanation of Potential Consequence, Security, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity synchronized timing effective security monitoring plan ppt microsoft
Cybersecurity synchronized timing effective security monitoring plan ppt microsoftThis slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Present the topic in a bit more detail with this Cybersecurity Synchronized Timing Effective Security Monitoring Plan Ppt Microsoft. Use it as a tool for discussion and navigation on Tracking And Security, Cybersecurity, Asset Management, Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective security monitoring plan cybersecurity monitoring activity ppt slides clipart images
Effective security monitoring plan cybersecurity monitoring activity ppt slides clipart imagesThis slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an outstanding presentation on the topic using this Effective Security Monitoring Plan Cybersecurity Monitoring Activity Ppt Slides Clipart Images. Dispense information and present a thorough explanation of Monitoring, Internal Customer, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective security monitoring plan cybersecurity monitoring implemented ppt example
Effective security monitoring plan cybersecurity monitoring implemented ppt exampleThis slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Present the topic in a bit more detail with this Effective Security Monitoring Plan Cybersecurity Monitoring Implemented Ppt Example. Use it as a tool for discussion and navigation on Network Security, Utilization, Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective security monitoring plan cybersecurity monitoring strategy ppt pictures
Effective security monitoring plan cybersecurity monitoring strategy ppt picturesThis slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies Increase audience engagement and knowledge by dispensing information using Effective Security Monitoring Plan Cybersecurity Monitoring Strategy Ppt Pictures. This template helps you present information on six stages. You can also present information on Strategy, Training, Monitoring, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective security monitoring plan cybersecurity monitoring traffic ppt model diagrams
Effective security monitoring plan cybersecurity monitoring traffic ppt model diagramsThis slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Deliver an outstanding presentation on the topic using this Effective Security Monitoring Plan Cybersecurity Monitoring Traffic Ppt Model Diagrams. Dispense information and present a thorough explanation of Implementation, Network Traffic, Investigation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



