Powerpoint Templates and Google slides for Cybersecurity Key
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Key Takeaways From Cybersecurity Training Sessions Training Ppt
Key Takeaways From Cybersecurity Training Sessions Training PptPresenting Key Takeaways from Cybersecurity Training Sessions. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Key Statistics Highlighting Importance Of How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Key Statistics Highlighting Importance Of How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various statistics that highlights the importance of cybersecurity in organization. It highlights stats related to malware attacks, DDos attacks, cybersecurity spending, ransomware attacks, malicious mining software etc. Increase audience engagement and knowledge by dispensing information using Key Statistics Highlighting Importance Of How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. This template helps you present information on seven stages. You can also present information on Cybersecurity, Email, Reported using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Key Benefits Of Cybersecurity In Business Unlocking The Impact Of Technology
Overview And Key Benefits Of Cybersecurity In Business Unlocking The Impact Of TechnologyThis slide showcases introduction to cybersecurity. This template focuses on confidentiality, integrity and availability of data in an organisation. It includes information related to maintaining employee trust, protecting personal information, etc. Introducing Overview And Key Benefits Of Cybersecurity In Business Unlocking The Impact Of Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Servers From Malicious Attacks, Applications From External Attacks, Maintains Employee Trust, Safeguards Business Operations, using this template. Grab it now to reap its full benefits.
-
 Benefits Of Using Cybersecurity Key Performance Indicators
Benefits Of Using Cybersecurity Key Performance IndicatorsThis slide showcases the benefits of using cybersecurity key performance indicators which help an organization to provide a snapshot to its relevant stakeholders, managers. It include details such as removes unknown devices on an organizations network, etc. Introducing our Benefits Of Using Cybersecurity Key Performance Indicators set of slides. The topics discussed in these slides are Removes Unknown, Calculates Open Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Key Performance Indicator And Padlock Icon
Cybersecurity Key Performance Indicator And Padlock IconIntroducing our Cybersecurity Key Performance Indicator And Padlock Icon set of slides. The topics discussed in these slides are Cybersecurity Key, Performance Indicator. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Key Performance Indicators With Applications
Cybersecurity Key Performance Indicators With ApplicationsThis slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc. Presenting our well structured Cybersecurity Key Performance Indicators With Applications. The topics discussed in this slide are Security Policies, Identify Weaknesses.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Essential Cybersecurity Key Performance Indicators
Essential Cybersecurity Key Performance IndicatorsThis slide showcases the essential cybersecurity key performance indicators which helps an organization to easily detect and response threats on time. It include details such as level of preparedness, unidentified devices on internal networks, etc. Presenting our well structured Essential Cybersecurity Key Performance Indicators. The topics discussed in this slide are Level Of Preparedness, Intrusion Attempts.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Market Drivers For Cybersecurity FIO SS
Key Market Drivers For Cybersecurity FIO SSFollowing slide showcases key market drivers associate in cybersecurity. It includes pointers such as adoption of IoT and cloud computing, awareness of data privacy, integration of AI and machine learning, etc.Introducing our premium set of slides with Key Market Drivers For Cybersecurity FIO SS. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Computing, Complex Networks, Online Transaction. So download instantly and tailor it with your information.
-
 Overview Of Cybersecurity With Major Segments And Key Players FIO SS
Overview Of Cybersecurity With Major Segments And Key Players FIO SSFollowing slide shows a comprehensive overview of cybersecurity to understand current market position. It includes elements such as introduction, market segmentation, top producers and key players.Introducing our premium set of slides with Overview Of Cybersecurity With Major Segments And Key Players FIO SS. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Increasing Cyberattacks, Telecommunication Retail, Enterprises Size. So download instantly and tailor it with your information.
-
 Key Statistics Associated With IoT Botnet Improving IoT Device Cybersecurity IoT SS
Key Statistics Associated With IoT Botnet Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase major statistics which are associated with Internet of Things IoT botnet attack. It covers information about total activities which are associated with gaining unauthorized access, financial loss caused by IoT botnet attack, etc. Introducing Key Statistics Associated With IoT Botnet Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Access, Increased, Significant, using this template. Grab it now to reap its full benefits.
-
 Key Statistics Associated With IoT Password Improving IoT Device Cybersecurity IoT SS
Key Statistics Associated With IoT Password Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline major statistics associated with Internet of Things IoT password attack. Information covered in this slide is related to most default password used, use of poor password, default username and password, etc. Increase audience engagement and knowledge by dispensing information using Key Statistics Associated With IoT Password Improving IoT Device Cybersecurity IoT SS. This template helps you present information on five stages. You can also present information on Generator, Devices, Reported using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Issues Overview And Key Statistics Strategic Guide For Web Design Company
Cybersecurity Issues Overview And Key Statistics Strategic Guide For Web Design CompanyMentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Present the topic in a bit more detail with this Cybersecurity Issues Overview And Key Statistics Strategic Guide For Web Design Company. Use it as a tool for discussion and navigation on Service, Authentication, Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
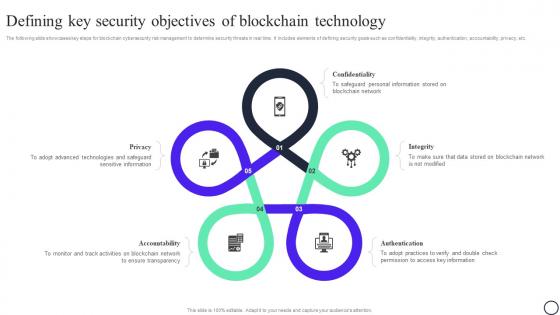 Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V
Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V This template helps you present information on Five stages. You can also present information on Privacy, Confidentiality, Integrity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Functional Testing Checklist To Review Key Components BCT SS V
Blockchain And Cybersecurity Functional Testing Checklist To Review Key Components BCT SS VThe following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Functional Testing Checklist To Review Key Components BCT SS V This template helps you present information on Three stages. You can also present information on Parameters, Description, Status using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Key Approaches To Protect From Honeypot Scams BCT SS V
Blockchain And Cybersecurity Key Approaches To Protect From Honeypot Scams BCT SS VThe following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. Introducing Blockchain And Cybersecurity Key Approaches To Protect From Honeypot Scams BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Audits, No Dead Coins, Scrutinize Website using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Key Scenarios Of Sybil Attack On Blockchain Network BCT SS V
Blockchain And Cybersecurity Key Scenarios Of Sybil Attack On Blockchain Network BCT SS VThe following slide showcases major scenarios of Sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer-to-peer model, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Key Scenarios Of Sybil Attack On Blockchain Network BCT SS V This template helps you present information on Two stages. You can also present information on Bitcoin Network, Attack On Tor Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Key Statistics Associated With Blockchain Scams BCT SS V
Blockchain And Cybersecurity Key Statistics Associated With Blockchain Scams BCT SS VThe following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Key Statistics Associated With Blockchain Scams BCT SS V This template helps you present information on Six stages. You can also present information on Digital Assets, Stolen Through Frauds using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Overview And Key Levels Of Honeypot Crypto Frauds BCT SS V
Blockchain And Cybersecurity Overview And Key Levels Of Honeypot Crypto Frauds BCT SS VThe following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Overview And Key Levels Of Honeypot Crypto Frauds BCT SS V This template helps you present information on Three stages. You can also present information on Solidity Compiler, Etherscan Blockchain Explorer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Statistics Highlighting Importance Of Cybersecurity Leveraging ChatGPT AI SS V
Key Statistics Highlighting Importance Of Cybersecurity Leveraging ChatGPT AI SS VThis slide showcases various statistics that highlights the importance of cybersecurity in organization. It highlights stats related to malware attacks, DDos attacks, cybersecurity spending, ransomware attacks, malicious mining software etc. Introducing Key Statistics Highlighting Importance Of Cybersecurity Leveraging ChatGPT AI SS V to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Mining, Alware Was Delivered, Companies Reported Ransomware using this template. Grab it now to reap its full benefits.
-
 Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various statistics that highlights the importance of cybersecurity in organization. It highlights stats related to malware attacks, DDos attacks, cybersecurity spending, ransomware attacks, malicious mining software etc. Present the topic in a bit more detail with this Key Importance Of Cybersecurity Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Use it as a tool for discussion and navigation on Cybersecurity, Statistics, Importance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Practices For Implementation Of Opsec Cybersecurity
Key Practices For Implementation Of Opsec CybersecurityThis slide depicts the key practices for opsec cybersecurity implementation. This slide aims to help the business leverage opsec through practices such as implementation of relevant processes, selection of suitable providers, restriction of access to networks, etc. Introducing our premium set of slides with Key Practices For Implementation Of Opsec Cybersecurity. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Practices, Description, Networks And Devices. So download instantly and tailor it with your information.
-
 Key Role Played By Firewalls In Cybersecurity
Key Role Played By Firewalls In CybersecurityThis slide showcases the crucial role played by firewalls in cybersecurity which helps an organization to provide protection against attacks by shielding network from unnecessary activities. It include details such as tracks unwanted traffic, acts as traffic controller, etc. Presenting our well structured Key Role Played By Firewalls In Cybersecurity. The topics discussed in this slide are Cybersecurity, Organization, Protection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Components Of Maritime Cybersecurity System
Key Components Of Maritime Cybersecurity SystemThis slide showcases major components of maritime. The main purpose of this template is to develop cargo management. This includes cybersecurity infrastructure, supply chain integration, environmental monitoring, etc. Presenting our set of slides with Key Components Of Maritime Cybersecurity System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cybersecurity Infrastructure, Environmental Monitoring, Supply Chain Integration.
-
 Key Cybersecurity Awareness Topics For Employees Training
Key Cybersecurity Awareness Topics For Employees TrainingThis slide highlights strategies for educating retail personnel on cyber security. The purpose of this template is to aid businesses in eliminating evolving digital threats effectively. It includes elements such as email scam, password security, removable media, etc. Presenting our set of slides with Key Cybersecurity Awareness Topics For Employees Training This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Password Security, Safe Internet Habits, Removable Media
-
 IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SS
IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security introduction with its major benefits, referable for companies dealing with related vulnerabilities. It provides details about security protocols, device protection, encryption, etc. Increase audience engagement and knowledge by dispensing information using IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on two stages. You can also present information on Protection Of Devices, Encryption Of Networks, Secured Data Handling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Considerations Assumptions Of Cybersecurity Industry Report Global Cybersecurity Industry Outlook
Key Considerations Assumptions Of Cybersecurity Industry Report Global Cybersecurity Industry OutlookThe slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Introducing Key Considerations Assumptions Of Cybersecurity Industry Report Global Cybersecurity Industry Outlook to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Historical Trends, Government Publications, Market Share, using this template. Grab it now to reap its full benefits.
-
 Key Statistics Highlighting Importance Of Cybersecurity Impact Of Generative AI SS V
Key Statistics Highlighting Importance Of Cybersecurity Impact Of Generative AI SS VThis slide showcases various statistics that highlights the importance of cybersecurity in organization. It highlights stats related to malware attacks, DDos attacks, cybersecurity spending, ransomware attacks, malicious mining software etc. Introducing Key Statistics Highlighting Importance Of Cybersecurity Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Mining Software, Reported Ransomware, Faced Per Day, using this template. Grab it now to reap its full benefits.
-
 Key Strategies For Cybersecurity Risk Management
Key Strategies For Cybersecurity Risk ManagementFollowing slide highlights various risk management strategies to boost cyber security and sensitive data protection. It further covers capability assessments, program design, strategy, risk management, compliance, etc. Introducing our premium set of slides with Key Strategies For Cybersecurity Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party Risk Management, Capability Assessments, Risk Management. So download instantly and tailor it with your information.
-
 Encryption For Data Encryption Key Management Best Practices Cybersecurity SS
Encryption For Data Encryption Key Management Best Practices Cybersecurity SSThis slide showcases encryption key management best practices which can help companies increase security. It provides details about secure key stores, access, backup, recovery, etc. Present the topic in a bit more detail with this Encryption For Data Encryption Key Management Best Practices Cybersecurity SS. Use it as a tool for discussion and navigation on Secure Key Stores, Access To Key Stores, Key Backup And Recoverability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS
Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SSThis slide showcases key management protocols which can help companies increase efficiency and generation time. It provides details about hash functions, authentication, symmetric, etc. Introducing Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Cryptographic Hash Functions, Symmetric-Key Algorithms, Asymmetric-Key Algorithms, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SS
Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SSThis slide showcases key management and strength improvement techniques which can help companies increase security. It provides details about elliptic, organization strategy, data exposure, etc. Introducing Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Establishing Key Strength, Encrypting Keys Securely, Elliptic Curve Algorithms, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS
Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS. Use it as a tool for discussion and navigation on Potential Impact, Increased Speed, Improved User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Parameters Of Company Cybersecurity Policy
Key Parameters Of Company Cybersecurity PolicyThis slide showcases the major components of company cybersecurity policy which helps an organization to follow procedures that transfer data and ensure security and prevent unauthorized access. It include details such as confidential data, company devices protection, etc. Presenting our set of slides with Key Parameters Of Company Cybersecurity Policy This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Confidential Data, Company Devices Protection, Email Protection
-
 Key Considerations To Select Pam Vendor For Effective Cybersecurity
Key Considerations To Select Pam Vendor For Effective CybersecurityThis slide represents various considerations that assist companies to select best PAM vendor to enhance their data protection and cybersecurity effectively. It includes various factors such as price transparency, easy management, user onboarding, etc. Presenting our well structured Key Considerations To Select Pam Vendor For Effective Cybersecurity. The topics discussed in this slide are Easy Management, Price Transparency, Innovation And Updates. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SSIntroducing Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Gather Information, Choose Security Solutions, Implement Chosen Solutions, using this template. Grab it now to reap its full benefits.
-
 Key Considerations For Building Cybersecurity Strategies
Key Considerations For Building Cybersecurity StrategiesThis slide showcases the major considerations for developing cybersecurity strategies which helps an organization to decrease attacks and data breaches by offering quick response time. It include details such as protect perimeter less technology,support zero trust,etc. Introducing our premium set of slides with Key Considerations For Building Cybersecurity Strategies. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Support Zero Trust,Provide Awareness Programs,Offer Security Knowledge. So download instantly and tailor it with your information.
-
 Key Considerations To Select Mdr Vendor For Effective Cybersecurity
Key Considerations To Select Mdr Vendor For Effective CybersecurityThis slide represents various considerations that assist companies to select best MDR vendor to enhance their data protection and cybersecurity effectively. It includes various considerations such as expertise, facilities, and methodology. Introducing our Key Considerations To Select Mdr Vendor For Effective Cybersecurity set of slides. The topics discussed in these slides are Key Considerations, Cybersecurity, Methodology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SS
Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SSThis slide represents challenges faced by enterprise as a result of network vulnerabilities leading to issues such as lack of privacy, compliance and security and data leakage etc.Introducing Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Security, Personal Devices, Software Encryption, using this template. Grab it now to reap its full benefits.
-
 Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SS
Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SSThis dashboard tracks and manages the organizations network vulnerabilities. It includes KPIs such as data access vulnerabilities and exploitable vulnerabilities and a summary of vulnerabilities by severity.Deliver an outstanding presentation on the topic using this Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SS. Dispense information and present a thorough explanation of Unmitigated, Mitigated, Exploitable, Exploitable Hosts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred
Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cyber Attacks Occurred, Financial Loss, Cyber Attack Origins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways to set up an advanced cybersecurity monitoring plan estimated security monitoring key performance
Ways to set up an advanced cybersecurity monitoring plan estimated security monitoring key performanceThis slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an outstanding presentation on the topic using this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Estimated Security Monitoring Key Performance. Dispense information and present a thorough explanation of Security Monitoring KPIs, Costs Per Security Incident, Security Monitoring Incidents Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity and digital business risk management key security controls to be addressed
Cybersecurity and digital business risk management key security controls to be addressedPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Increase audience engagement and knowledge by dispensing information using Cybersecurity And Digital Business Risk Management Key Security Controls To Be Addressed. This template helps you present information on three stages. You can also present information on Framework, Authentification, Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
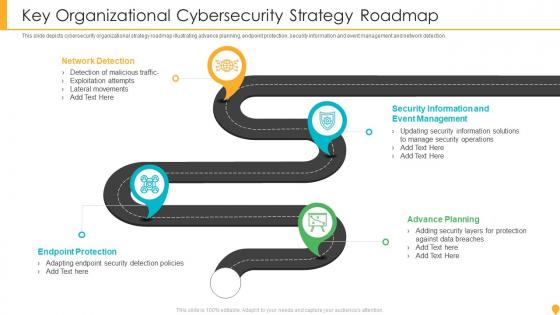 Key Organizational Cybersecurity Strategy Roadmap
Key Organizational Cybersecurity Strategy RoadmapThis slide depicts cybersecurity organizational strategy roadmap illustrating advance planning, endpoint protection, security information and event management and network detection. Presenting our set of slides with name Key Organizational Cybersecurity Strategy Roadmap. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Detection, Endpoint Protection, Advance Planning, Security Information.
-
 Key Issues Faced By Organization Due To Cybersecurity Incidents Ppt Template
Key Issues Faced By Organization Due To Cybersecurity Incidents Ppt TemplateThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Increase audience engagement and knowledge by dispensing information using Key Issues Faced By Organization Due To Cybersecurity Incidents Ppt Template. This template helps you present information on five stages. You can also present information on Organization, Cybersecurity Incidents, Comparison using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Elements Of Cybersecurity Awareness Training Program
Key Elements Of Cybersecurity Awareness Training ProgramThis slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Introducing our premium set of slides with Key Elements Of Cybersecurity Awareness Training Program. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Make Message Relevant, Use Examples, Use Common Language, Present Small Messages . So download instantly and tailor it with your information.
-
 Key Services Analysis For Cybersecurity Risk Management Company
Key Services Analysis For Cybersecurity Risk Management CompanyThe following slide explains various services provided by cybersecurity risk management company. It further includes details such as capability assessment, regulatory response and compliance, etc. Presenting our set of slides with name Key Services Analysis For Cybersecurity Risk Management Company. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Capability Assessments, Risk Management, Strategy Program Design.
-
 Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity Incidents
Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity IncidentsThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Introducing Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity Incidents to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Faced By Organization Due, Cybersecurity Incidents, Confidential Information , using this template. Grab it now to reap its full benefits.
-
 Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity Incidents
Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity IncidentsThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Introducing Development And Implementation Of Security Key Issues Faced By Organization Due To Cybersecurity Incidents to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Privacy, Compliance, Security, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks
Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Control Accounts Access, Multifactor Authentication, Track Network Intrusions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Challenges To Healthcare Cybersecurity Performance
Key Challenges To Healthcare Cybersecurity PerformanceThis slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness. Presenting our set of slides with Key Challenges To Healthcare Cybersecurity Performance This exhibits information on sixstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Breaches, Insider Threats, Cloud Threats, Lack Of Cyber Awareness.
-
 Key Threats In Healthcare Cloud Cybersecurity
Key Threats In Healthcare Cloud CybersecurityThis slide presents main threats to cloud cybersecurity in healthcare helpful for organizations to check potential risks and work towards eliminating them. It includes threats such as natural phenomenon, supply chain failure, human errors and malicious action that should be checked upon from time to time. Introducing our Key Threats In Healthcare Cloud Cybersecurity set of slides. The topics discussed in these slides are Threat Level, Threat, Description This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key principles cybersecurity ppt powerpoint presentation inspiration slideshow cpb
Key principles cybersecurity ppt powerpoint presentation inspiration slideshow cpbPresenting Key Principles Cybersecurity Ppt Powerpoint Presentation Inspiration Slideshow Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Key Principles Cybersecurity. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cybersecurity threat landscape with key trends
Cybersecurity threat landscape with key trendsIntroducing our Cybersecurity Threat Landscape With Key Trends set of slides. The topics discussed in these slides are Cybersecurity Threat Landscape With Key Trends. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Elements Of Comprehensive Cybersecurity Audit
Key Elements Of Comprehensive Cybersecurity AuditThe following slide covers vital elements, including manual specifications, documentation review, automated testing, static analysis, fuzzing, symbolic verification, formal and manual analysis, in a comprehensive cybersecurity audit. This provides a holistic approach to assessing and fortifying security measures. Introducing our premium set of slides with Key Elements Of Comprehensive Cybersecurity Audit Ellicudate the Eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Operational Security, Network Security, System Security. So download instantly and tailor it with your information.



