Powerpoint Templates and Google slides for Cybersecurity Computing
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cybersecurity Risks Mitigation With Serverless Computing V2
Cybersecurity Risks Mitigation With Serverless Computing V2This slide talks about some ways that a serverless system can help reduce the attack surface by minimizing the number of attack vectors. These include reduced infrastructure, access control restrictions, stateless computing, and auto-scaling. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risks Mitigation With Serverless Computing V2. This template helps you present information on four stages. You can also present information on Reduced Infrastructure, Access Control Restrictions, Stateless Computing, Serverless Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Challenges For Cloud Computing And Technology
Cybersecurity Challenges For Cloud Computing And TechnologyThis slide illustrates cloud computing cybersecurity challenges by establishing secure and resilient digital environment for users. It includes challenges such as security issues, lack of resources and expertise, compliance, and performance. Presenting our well structured Cybersecurity Challenges For Cloud Computing And Technology The topics discussed in this slide are Security Issues, Compliance, Performance This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Computer Ransomware Cybersecurity Icon With Big Data Analytics
Computer Ransomware Cybersecurity Icon With Big Data AnalyticsPresenting our set of slides with name Computer Ransomware Cybersecurity Icon With Big Data Analytics. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Computer Ransomware, Cybersecurity Icon, Big Data Analytics.
-
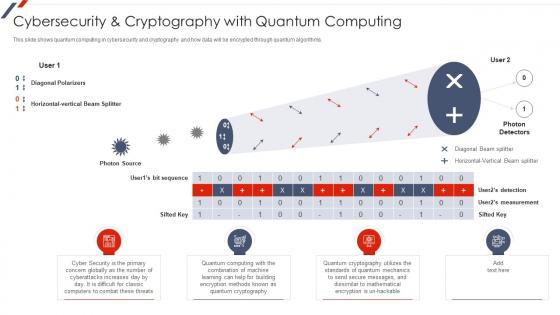 Quantum Mechanics Cybersecurity And Cryptography With Quantum Computing
Quantum Mechanics Cybersecurity And Cryptography With Quantum ComputingThis slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms. Deliver an outstanding presentation on the topic using this Quantum Mechanics Cybersecurity And Cryptography With Quantum Computing. Dispense information and present a thorough explanation of Diagonal Polarizers, Horizontal Vertical Beam Splitter, Photon Source, Sifted Key using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
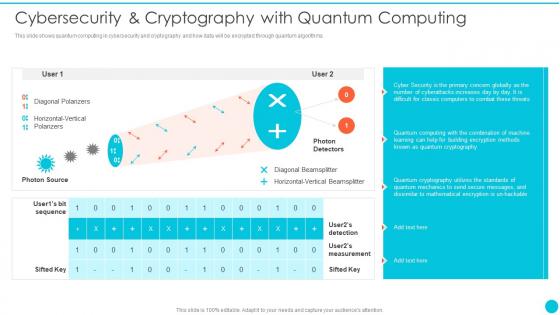 Cybersecurity And Cryptography With Quantum Computing Quantum Cryptography
Cybersecurity And Cryptography With Quantum Computing Quantum CryptographyThis slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms.Present the topic in a bit more detail with this Cybersecurity And Cryptography With Quantum Computing Quantum Cryptography Use it as a tool for discussion and navigation on Diagonal Polarizers, Diagonal Beamsplitter, Quantum Computing This template is free to edit as deemed fit for your organization. Therefore download it now.
-
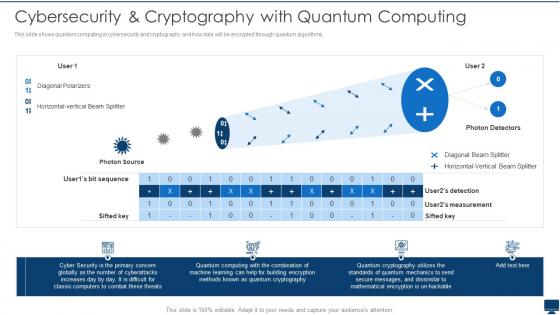 Cybersecurity And Cryptography With Quantum Computing Quantum Computation
Cybersecurity And Cryptography With Quantum Computing Quantum ComputationThis slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms. Deliver an outstanding presentation on the topic using this Cybersecurity And Cryptography With Quantum Computing Quantum Computation. Dispense information and present a thorough explanation of Cybersecurity, Cryptography, Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Serverless Computing Cybersecurity Risks Mitigation With Serverless Computing
Serverless Computing Cybersecurity Risks Mitigation With Serverless ComputingThis slide talks about some ways that a serverless system can help reduce the attack surface by minimizing the number of attack vectors. These include reduced infrastructure, access control restrictions, stateless computing, and auto-scaling. Increase audience engagement and knowledge by dispensing information using Serverless Computing Cybersecurity Risks Mitigation With Serverless Computing. This template helps you present information on five stages. You can also present information on Reduced Infrastructure, Access Control Restrictions, Stateless Computing, Auto Scaling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Cybersecurity Incident Management Deploying Computer Security Incident
Best Practices For Cybersecurity Incident Management Deploying Computer Security IncidentThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc.Increase audience engagement and knowledge by dispensing information using Best Practices For Cybersecurity Incident Management Deploying Computer Security Incident. This template helps you present information on five stages. You can also present information on Incident Management, Management Process, Responsibilities Members using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident Management
Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc.Introducing Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sharing Information, Establish Policies, Response Process, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident Management
Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc.Increase audience engagement and knowledge by dispensing information using Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident Management. This template helps you present information on five stages. You can also present information on Increased Costs, Operational Disruption, Reputational Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis Of Cybersecurity And Cloud Computing Security
Comparative Analysis Of Cybersecurity And Cloud Computing SecurityThe purpose of the slide is to showcase the significant differences between cyber security and cloud security. It provides a comparative matrix with differentiating aspects like definition, maintenance of personal information security, liability of security breach, access to data and security threat detection. Presenting our well structured Comparative Analysis Of Cybersecurity And Cloud Computing Security. The topics discussed in this slide are Aspects, Cloud Security, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comprehensive Cybersecurity Checklist For Cloud Computing
Comprehensive Cybersecurity Checklist For Cloud ComputingThe slide showcases an inclusive cybersecurity checklist for cloud. It covers identity and access management, data protection, visibility and intelligence, network security, application security and workloads centric. Introducing our premium set of slides with Comprehensive Cybersecurity Checklist For Cloud Computing. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Visibility And Intelligence, Workloads Centric, Network Security. So download instantly and tailor it with your information.
-
 IoT Cloud Computing Cybersecurity Technology Components
IoT Cloud Computing Cybersecurity Technology ComponentsThis slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Presenting our set of slides with IoT Cloud Computing Cybersecurity Technology Components. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Control, Management, Hardware.
-
 Internet cybersecurity protection icon for personal computer
Internet cybersecurity protection icon for personal computerPresenting our set of slides with Internet Cybersecurity Protection Icon For Personal Computer. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Internet Cybersecurity Protection Icon For Personal Computer.
-
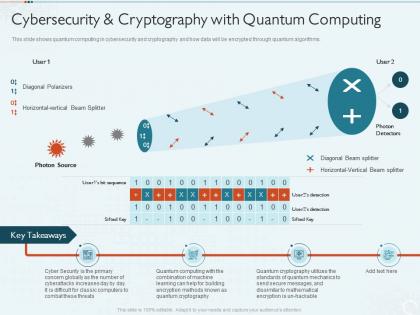 Quantum computing it cybersecurity and cryptography with quantum computing ppt skills
Quantum computing it cybersecurity and cryptography with quantum computing ppt skillsThis slide shows quantum computing in cybersecurity and cryptography and how data will be encrypted through quantum algorithms. Deliver an outstanding presentation on the topic using this Quantum Computing IT Cybersecurity And Cryptography With Quantum Computing Ppt Skills. Dispense information and present a thorough explanation of Cryptography, Quantum Computing, Cyberattacks, Globally using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



